The Evolution of the Privileged Access Management (PAM) Market & The New Competitive Landscape
The Future of PAM post PANW & CyberArk; How Zero standing Privileges, Cloud, and Agentic AI Are Redefining the Privileged Identity Access Control Plane
Introductory Blurb
As Identity becomes central to agentic security, Privileged Access Management (PAM) is undergoing a structural shift. It is currently an underlooked category which deserves more attention as we prepare for an identity centric agentic stack.
Our opinion is that privileged access will be central to how human, agents and machines (NHIs) evolve within the future identity stack. The acquisitions we have witnessed over the past 12 months have been reinforced by decisive market activity. Palo Alto Networks’ $25B acquisition of CyberArk reflects a clear recognition that identity and privilege are now foundational to platform agentic security. Palo Alto Networks had many opportunities across this ecosystem, but chose to go with the PAM route.
Subsequently, we’ve seen other minor acquisitions such as Okta’s acquisition of Axiom. We also saw Delinea’s acquisition of StrongDM two weeks ago signal a move toward just-in-time, runtime-aware access for cloud and developer environments. We’ve recently seen vendors such as Silverfort (PAS), 1Password vaulting and Keeper PAS continue to push for more privilege access products.
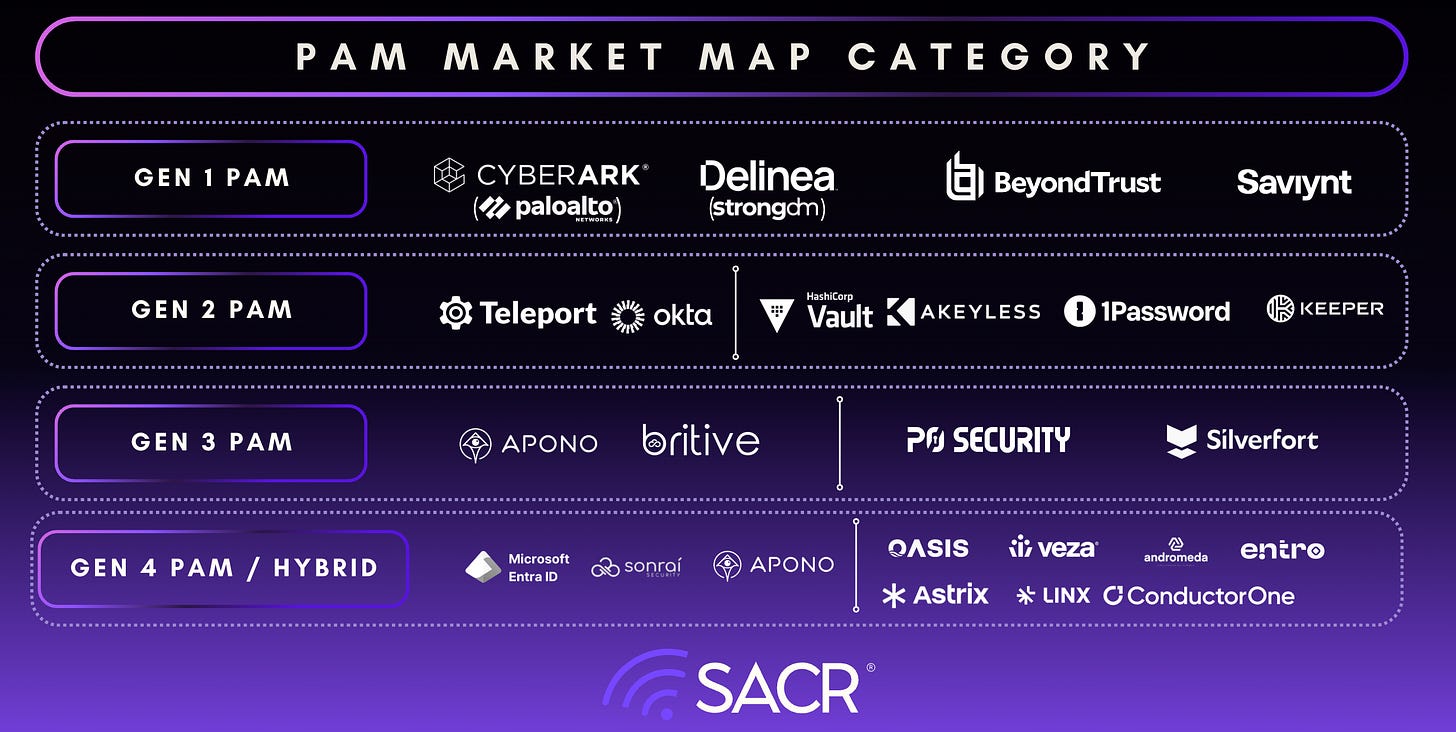
See market breakdown below:
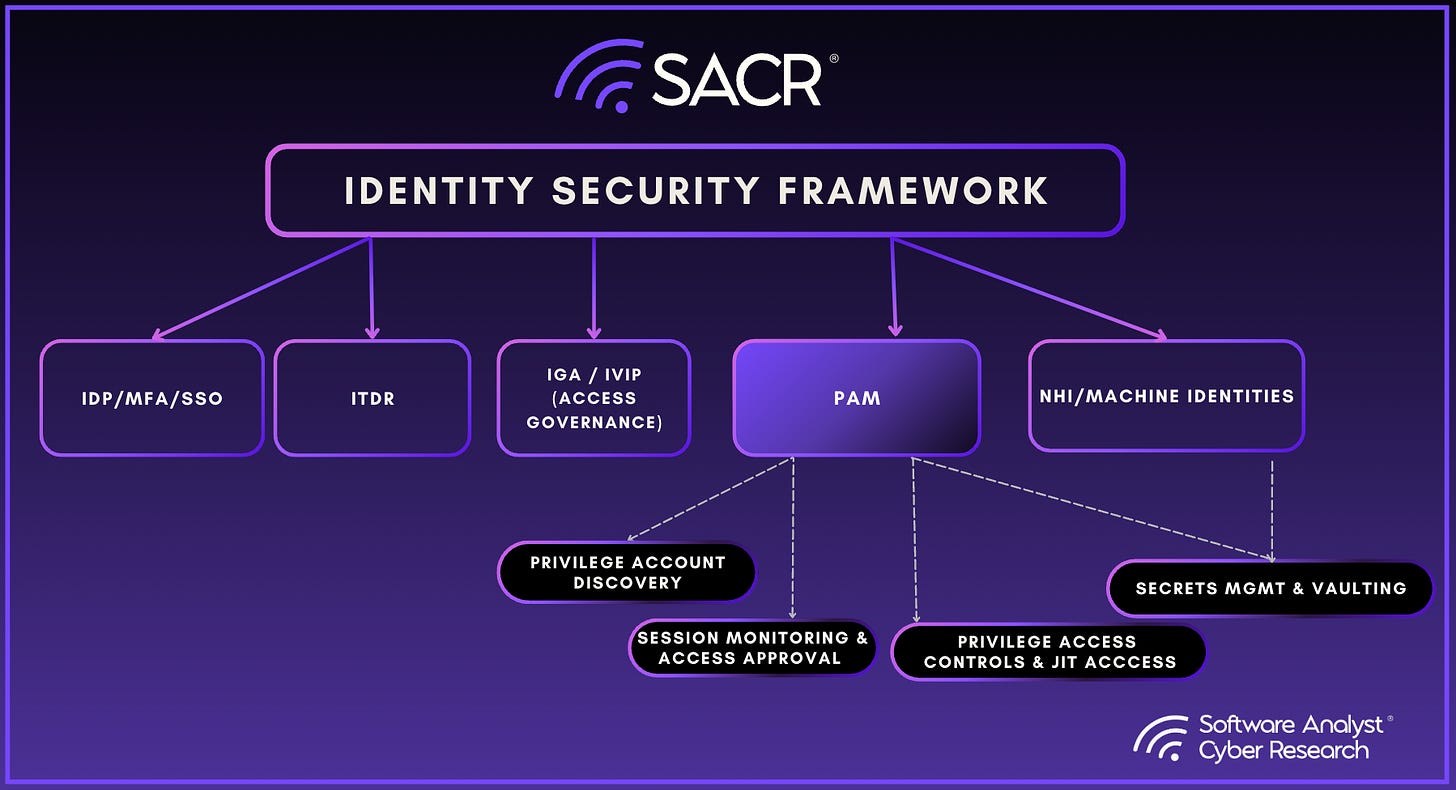
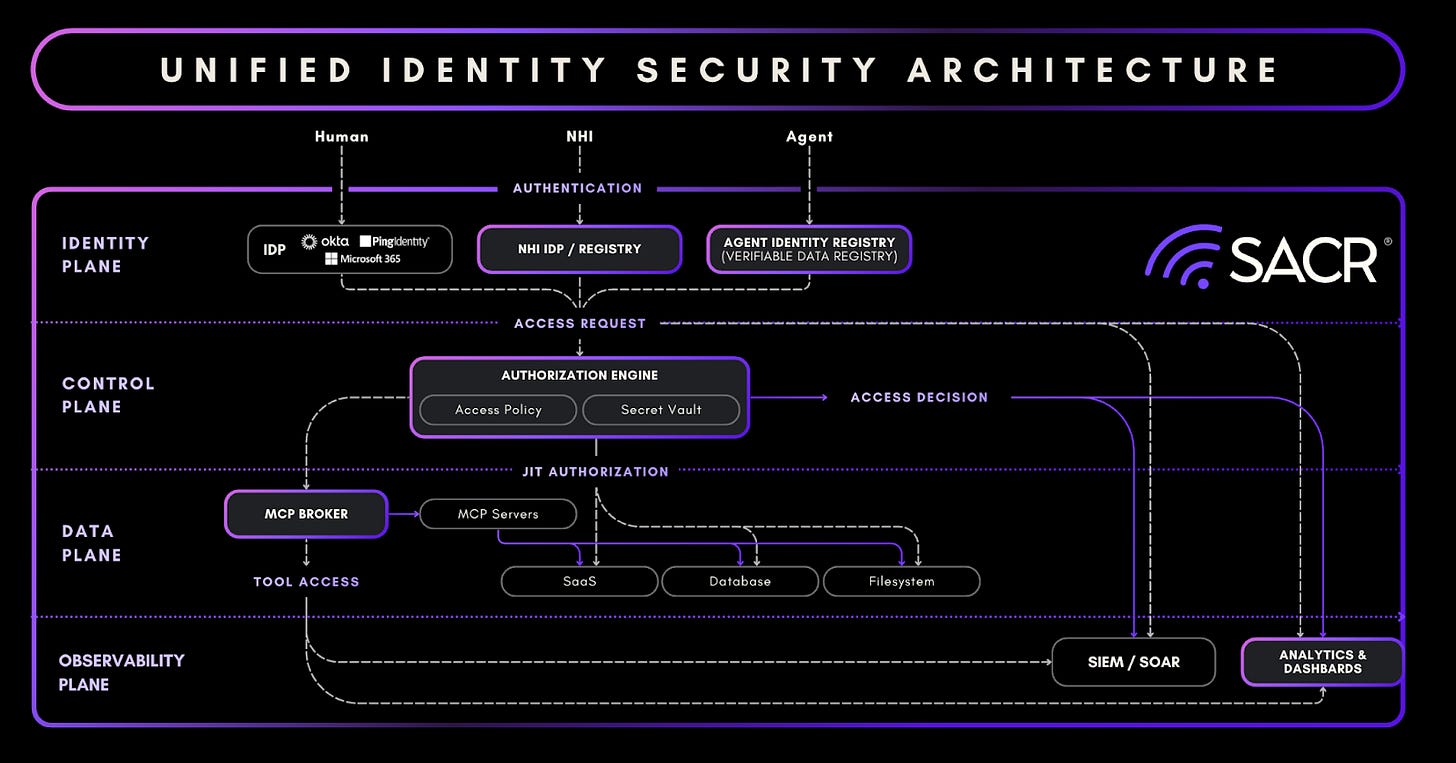
SACR’s View Of The Modern Identity Security Stack
To better understand this framework, it’s crucial to understand how SACR thinks about the identity ecosystem. In today’s cloud-first and identity-driven environments, identity security has become the new perimeter. The image below outlines the core pillars of a modern Identity Security Framework, illustrating how organizations must govern access across both human and machine users.
At the center is Privileged Access Management (PAM). Its the hardest capability to build in identity security relative to others. We believe PAM will be central to managing agent identity. The function responsible for securing the most sensitive and high-impact permissions across your environment. Surrounding PAM are adjacent pillars:
IDP/MFA/SSO, which authenticate users and enable secure logins.
ITDR (Identity Threat Detection & Response), focused on detecting identity-based threats in real time,
IGA/IVIP, which handles visibility into all identities (IVIP) and IGA focuses on governance, access reviews, and joiner/mover/leaver flows.
NHI (Non-Human Identities), which includes service accounts, workloads, bots, and API keys. It is important to realize there is a separation or distinction of NHIs vs agents.
Within PAM itself, we break SACR down into four essential components:
Privileged Account Discovery: Find what powerful access exists
Secrets Management & Vaulting: Store credentials safely
Privileged Access Controls & JIT Access: Enforce who gets access, when, and how
Session Monitoring & Access Approval: Observe usage and add checks before granting access
These building blocks work together to enforce least privilege, prevent unauthorized escalation, and contain the blast radius of breaches. The rest of this report will dive deeper into this PAM pillar and, hopefully, provide context for all readers. I provide a foundation breakdown much more in the report.
Defining Privileged Access Management (PAM) in the Modern Enterprise
Privileged Access Management is the identity security discipline focused on protecting, governing, and monitoring access to the most sensitive systems and actions within an environment.
A privileged account is any account that can
Change systems
Access sensitive data
Create or delete users
Shut things down
Override security controls
Privileged accounts span
Domain controllers and directory services
Administrative access to databases, applications, and operating systems
Public and private cloud IAM permissions
Network and infrastructure devices
DevOps secrets, API keys, tokens, and service accounts
Historically, PAM was synonymous with IT administrators and shared root credentials. Today, privilege has expanded dramatically in breadth (more identities) and depth (more powerful actions). Broadly, the move to the cloud has expanded access across the enterprise. We have seen an expansion in developers becoming more admins of critical infrastructure.
Foundational components
The core components of a PAM suite
Privileged Account Discovery: The goal is to identify all privileged accounts across systems, networks, applications, and cloud platforms. There is also another audit logging and compliance where before you can protect privileged access, you need to find it and track it. This pillar handles account discovery, continuous inventory, detailed activity logs, and compliance reporting. It ensures that security teams have the insights to detect risks and prove controls are working.
Credential Vaulting / Rotation: It stores privileged credentials in a secure and encrypted vault accessible only to authorized users or systems. This pillar focuses on protecting the actual secrets: passwords, SSH keys, tokens, and certificates. Credentials are stored in secure vaults, rotated frequently, and retrieved securely without exposing them to users. This reduces the risk of theft, reuse, or unmanaged sprawl.
Access Control & Least Privilege: This category covers Access control, Just-in-Time (JIT) Access and Approval Workflows. It enforce who gets access, when, and under what conditions. The goal is to eliminate standing privileges and instead issue temporary access based on need and context, often requiring manager or peer approval. It’s the core of Zero Trust and minimizes exposure.
Session Management and Monitoring: Once privileged access is granted, this pillar ensures real-time visibility and oversight of what users do with that power. This includes logging, monitoring, session recording, and if needed termination of live sessions. It’s crucial for incident response and auditability.
Core Actionable Summary For Readers
Setting the context for PAM, if you only had a few minutes to read the report. Here are the core takeaways:
Consolidation Has Made Privileged Access a Board-Level Control, not a Point Solution. We highlighted this in our report last year. Palo Alto Networks’ acquisition of CyberArk is not simply another large security deal; it is a signal that privileged access has moved to a foundational layer of enterprise security architecture. Platform security vendors do not spend $25B to fill feature gaps, they do it to control a control plane. By embedding privileged identity telemetry into network, endpoint, and SOC workflows, Palo Alto is effectively asserting that identity-driven privilege enforcement must operate at the same level of priority as threat detection and response. For CISOs, the implication is clear: privileged access is no longer a standalone IAM decision or a compliance checkbox. It is becoming inseparable from how organizations detect, contain, and respond to breaches. This acquisition has created a gap, opening the door for new vendors like Britive, Apono, Teleport and P0 Security.
Machine and Agentic Identities Are Now the Fastest-Growing Privileged Users and the Least Governed: The definition of identities is expanding more and more. The most significant expansion of privilege in modern environments is no longer human administrators, but non-human identities: service accounts, API keys, workloads, automation, and increasingly autonomous AI agents. These identities already outnumber humans by orders of magnitude, and unlike people, they operate continuously, at machine speed, and often with broad, implicit permissions. AI agents amplify this risk further by introducing non-deterministic behavior, an agent granted access to “optimize infrastructure” may legitimately modify or delete production systems if guardrails are weak or misinterpreted.
The Evolution of Privileged Identity: Enterprise security has undergone a structural inversion over the last two decades. Where trust was once anchored to a hardened network perimeter, modern environments have dissolved those boundaries through cloud computing, SaaS adoption, automation scripts, and an API-driven infrastructure. The perimeter no longer meaningfully exists. Identity is now the only consistent boundary. Across any organization, certain users and accounts hold elevated permissions over systems, infrastructure, data, and configurations effectively the “keys to the kingdom.” These privileged identities now include not only IT administrators, but developers, cloud engineers, service accounts, APIs, workloads, and increasingly, autonomous AI agents. This is a crucial contrast that is changing PAM
Cloud and Ephemeral Infrastructure Have Made Standing Privilege Structurally Unsustainable: Cloud has fundamentally broken the assumptions that traditional PAM was built on. Infrastructure is now created and destroyed in minutes, access requirements change continuously, and policy defined through static roles cannot keep pace without creating excessive risk or operational drag. Standing privilege like long-lived permissions granted has become one of the most common root causes of cloud security incidents. In this environment, the question is no longer whether an organization will experience privilege misuse, but whether it can limit the blast radius when it happens. Modern PAM is shifting from credential storage to real-time authorization: provisioning access only when needed, enforcing it in context, and revoking it automatically. Organizations that fail to make this transition are not merely behind the curve; they are operating with an access model that is incompatible with the speed and volatility of their own infrastructure.
How PAM Is Slowly Evolving In 2026
This new parameter shift, where identity security becomes the “parameter, “ is new for many practitioners. What was once a discipline centred on on-prem session control and credential vaulting is now evolving into a core access control layer responsible for enforcing contextual access decisions, continuous verification, and eliminating standing privileges across increasingly dynamic environments.
As a result, the baseline for PAM has materially changed. Just-in-time (JIT) access, remote privileged access, secrets management, and automation are no longer differentiators; they have become stakes. Buyers are increasingly evaluating PAM platforms based on their ability to enforce least privilege in real time, integrate with identity and infrastructure signals, and operate effectively across hybrid, cloud-native, and SaaS environments.
However, the most consequential force reshaping PAM is not cloud adoption or Zero Trust alone, as we’ve seen in recent years. Agentic AI is now redefining the nature of privileged access itself. The scope of identity has expanded well beyond human administrators to include non-human identities like service accounts and agents that operate with elevated permissions. This expansion in identities and privileged access is exposing a critical gap. Traditional PAM architectures, which were designed for human-centric access and static infrastructure, are increasingly misaligned with these new identities.
For CISOs and investors alike, the next phase of PAM will be determined by which platforms can govern human, machine, and AI identities at runtime, enforce privilege dynamically, and scale trust decisions in systems where access is transient and constantly changing.
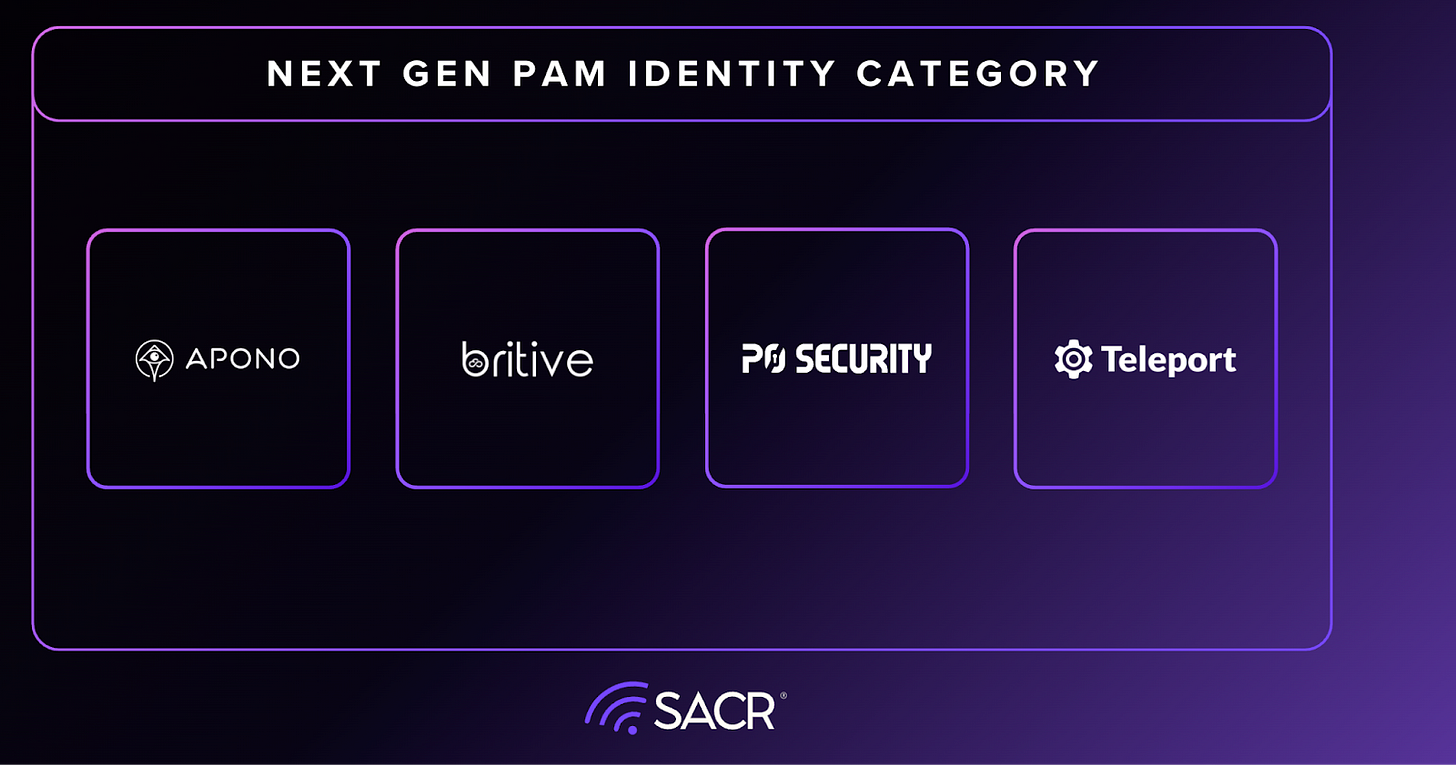
This report examines how the evolving PAM market has hit an inflection point for 2026, what it signals about the future of identity security, and which architectural approaches are likely to define the next generation of privileged access control. We selected the following players based on their next-gen PAM criterion and partnered with them to produce this research report for the community. The four vendors do not represent the entire market for next-gen players but they have representative key use-cases that help us illustrate how PAM is evolving for the cloud and agentic world.
Apono
Britive
P0 Security
Teleport
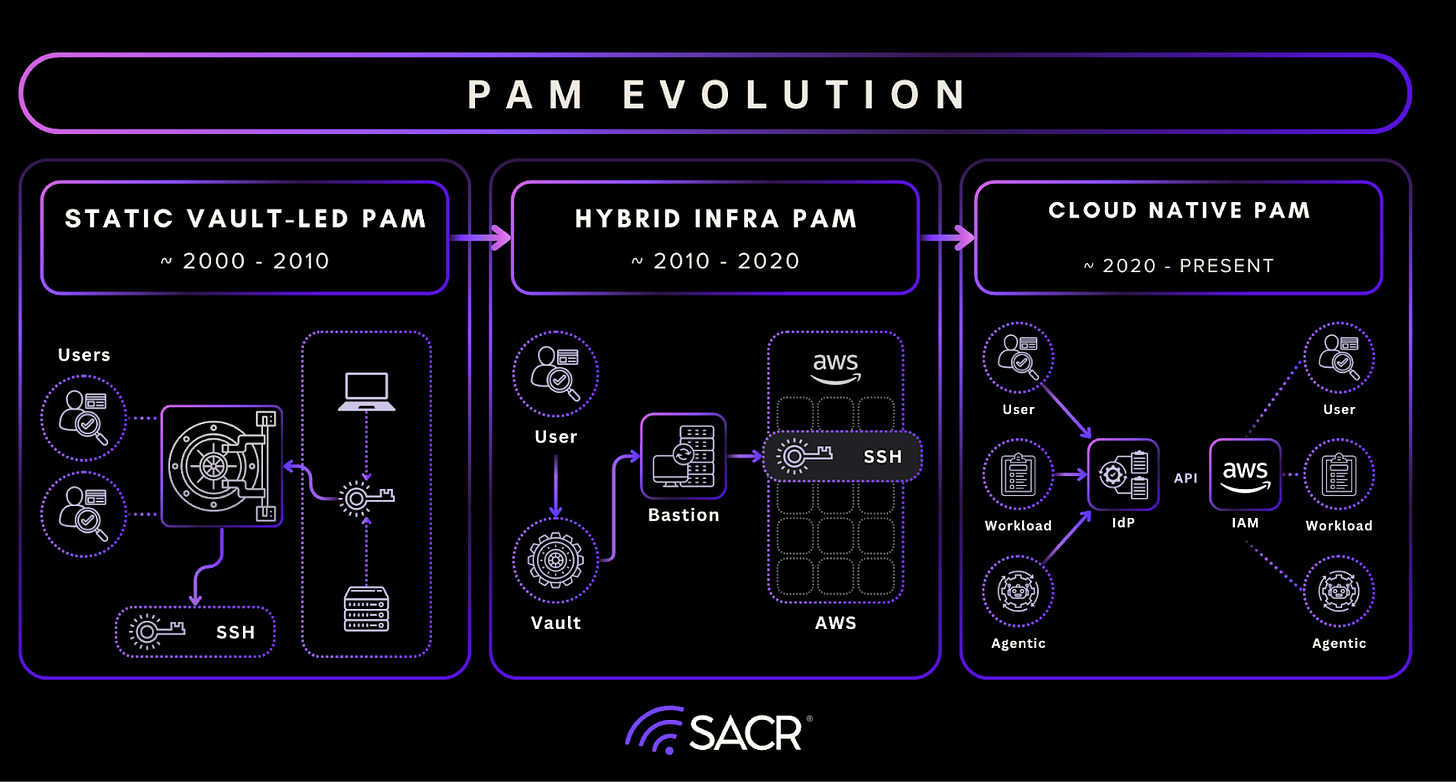
The History & Evolution of PAM
PAM suites then evolved over the years as more applications and infrastructure shifted from on-premise environments to public cloud environments. As we think about PAM, it has changed over the years from an on-prem centric ecosystem to cloud-centric view. More readings can be found here.
Phase 1: The Vault-Centric Era (Static Infrastructure, Static Secrets)
The PAM market emerged in the early 2000s alongside large on-premise data centers. Infrastructure was static, credentials were long-lived, and administrative access was often shared and poorly documented.
High-profile breaches exposed the fragility of this model. The 2014 Sony Pictures breach where attackers discovered a literal folder named “Passwords” containing privileged credentials became a defining moment for the category. Adoption accelerated rapidly, coinciding with CyberArk’s IPO and the market’s transition from niche to mission-critical.
Core architectural components of this era included:
Secure password vaults
Privileged session management and recording
Application identity and service account credential storage
Threat analytics focused on anomalous privileged behavior
This model dramatically reduced risk in static environments but introduced friction. Manual password checkout workflows often failed to scale, leading to shadow accounts and policy bypasses.
Phase 2: The Hybrid Cloud PAM Era (Session Governance at Scale)
As enterprises migrated to public cloud and virtualized infrastructure, the assumptions underlying vault-centric PAM began to break down. Ephemeral virtual machines, autoscaling workloads, CI/CD pipelines, and SaaS platforms caused an explosion in privileged credentials which many teams refer to as secret sprawl.
PAM platforms expanded to address this hybrid reality:
DevOps and secrets management
Endpoint privilege management
Cloud privilege and entitlement management
Bastion-based session mediation for SSH, RDP, and web access
Despite architectural change, market leadership remained stable. CyberArk and BeyondTrust retained dominance, while Centrify and Thycotic merged to form Delinea. At the same time, DevOps-native players like HashiCorp carved out a strong position around secrets management. The core limitation persisted: static roles and long-lived permissions do not align with infrastructure that changes by the minute.
Cloud Introduced Complexities Around Managing Ephemeral and Dynamic Privileged Access
The scale and volatility of modern cloud environments have fundamentally changed the requirements for privileged access management. Infrastructure is no longer composed of long-lived assets with predictable access patterns; instead, thousands of resources, virtual machines, containers, serverless functions, and cloud services are created, modified, and destroyed on a continuous basis.
In this context, access models built on static roles and pre-defined permissions become operationally unmanageable. Roles require constant updates, new resources must be manually onboarded, and permissions frequently lag behind the actual state of the environment, creating both security gaps and administrative overhead.
To be effective in cloud-native environments, privileged access must shift from static entitlement management to dynamic, context-aware authorization. This requires continuous, real-time discovery of infrastructure and identities, coupled with policies that evaluate access requests based on attributes such as workload context, environment, risk signals, and business intent at the time of use. Privilege must be provisioned just-in-time, scoped narrowly to the specific task or resource, and automatically revoked once the task is complete. Solutions that cannot adapt to infrastructure as it comes online without manual intervention; do not reduce risk; they simply introduce friction and complexity that teams will eventually work around.
As a result, defining privileged access policy through Infrastructure as Code (IaC) is becoming a practical requirement rather than a best practice for organizations operating at scale. Security and access controls must be versioned, automated, and deployed alongside infrastructure changes to remain effective. These requirements are increasingly driven not only by security teams, but also by platform, cloud, and DevOps engineers who are responsible for day-to-day operations and uptime. In environments where velocity is a competitive necessity, privileged access solutions must enforce control without impeding delivery: otherwise, they will be bypassed, undermining both security and governance.
Phase 3: The Zero Standing Privilege for AI Agents Era (Authorization Over Authentication)
The most significant shift underway is the transition from standing privilege to ephemeral, just-in-time authorization continuously in cloud environments and increasingly for AI agents.
In cloud-native environments, privileged access is less about logging into servers and more about executing API calls that mutate infrastructure state. Modern PAM architectures integrate directly with identity providers and cloud control planes, provisioning temporary credentials only when required and revoking them automatically upon task completion.
This Zero Standing Privilege (ZSP) model reduces blast radius, eliminates permanent secrets, and aligns access with real-time context. Newer entrants argue that managing secrets indefinitely is an anti-pattern, the real solution is eliminating the need for secrets altogether. Importantly, this is not yet the norm. Most enterprises remain hybrid, and vault-based PAM will remain essential for years. The market is not replacing legacy PAM, it is layering dynamic authorization on top of it.
The Expansion of Privilege From Humans to Machines
The complexity of human identity roles requires newer PAM solutions
The breadth and depth of access that engineers need to complete their work in the cloud have created a new attack surface for security teams to manage. This new class of privileged account presents two critical challenges for PAM: unprecedented scale, with exponentially more privileged accounts to manage; and heightened expectations regarding user experience. Unlike traditional privileged users, today’s developers represent a large population whose productivity directly impacts business outcomes, making friction intolerable.As a result, we regularly speak with CISOs who are as concerned with their team being viewed internally as business enablers as they are with addressing risk: an outcome that is often incompatible with traditional approaches to privileged access.We’ve also seen the scope of privileged access projects shift to include many stakeholders not typically associated with the category, including cloud security, platform security, DevOps, and even engineering leadership.These dynamics have redefined what organizations need and expect from PAM solutions: robust self-service capabilities, developer-friendly workflows, and the ability to secure access without impeding velocity.
Machines & Agents Evolving The Market
Identity security is increasingly bifurcated into human and non-human (machine) identities. While the number of human users has stabilized, machine identities: service accounts, API keys, tokens, certificates, workloads are growing exponentially. Most organizations already manage 40–50x more non-human identities than human ones, yet visibility and governance lag far behind. High-profile breaches at Okta, JumpCloud, and others have demonstrated that poorly managed machine identities represent a systemic risk. Machine identity security has evolved from SSH key management into a broader discipline encompassing:
Discovery and inventory
Lifecycle management
Secret rotation and certificate management
Behavioral detection and response
As PAM expanded into DevOps and secrets management, its boundaries increasingly overlapped with machine identity platforms such as Venafi and emerging startups focused exclusively on this problem.
The Future of PAM: The Rise of Agentic AI & the Redefinition of Privilege With Agents
AI agents represent a new class of privileged identity. When we compare them to traditional service accounts, agentic systems can reason, plan, and execute multi-step actions across domains. If compromised via prompt injection or model manipulation, these agents become high-speed insider threats. Organizations that have already operationalized just-in-time access, session auditing, and dynamic policy enforcement for humans are structurally better positioned to govern AI agents.
However, effective deployment of AI and agents require access to sensitive internal systems, data, and infrastructure, yet a majority of organizations remain uncertain about how to enable that access safely. Recent research indicates that a significant portion of IT leaders lack confidence in their ability to govern AI interactions with proprietary data, highlighting a growing gap between AI ambition and access control maturity. For many enterprises, even achieving zero standing privilege for human users remains an aspirational goal; extending privilege safely to non-deterministic AI agents introduces a materially higher level of risk.
Agentic identity is still an emerging domain, but customer sentiment is converging around a clear conclusion: privileged access maturity is a prerequisite for agentic AI adoption, not a downstream enhancement. AI agents operate continuously, execute multi-step actions, and can affect production environments at machine speed. Without just-in-time access, real-time authorization, session-level auditing, and anomaly detection, these agents effectively function as high-velocity privileged insiders. Organizations that have already operationalized these controls for human users are structurally better positioned to apply the same governance patterns to autonomous systems.
Additionally, AI co-pilots that inherit or “piggyback” on human access rights significantly expand the attack surface in environments with weak privilege boundaries. In such cases, compromise of a single identity can cascade across human and machine workflows.
Forward-looking CISOs are responding by treating PAM as a foundational control for AI readiness. We broadly believe that investing now in deep visibility into sensitive resources, enforcing automated and context-aware permissions, and aligning privileged access decisions with business intent. This groundwork will ultimately determine whether AI becomes a controlled force multiplier or an ungoverned source of systemic risk.
Future Themes To Watch
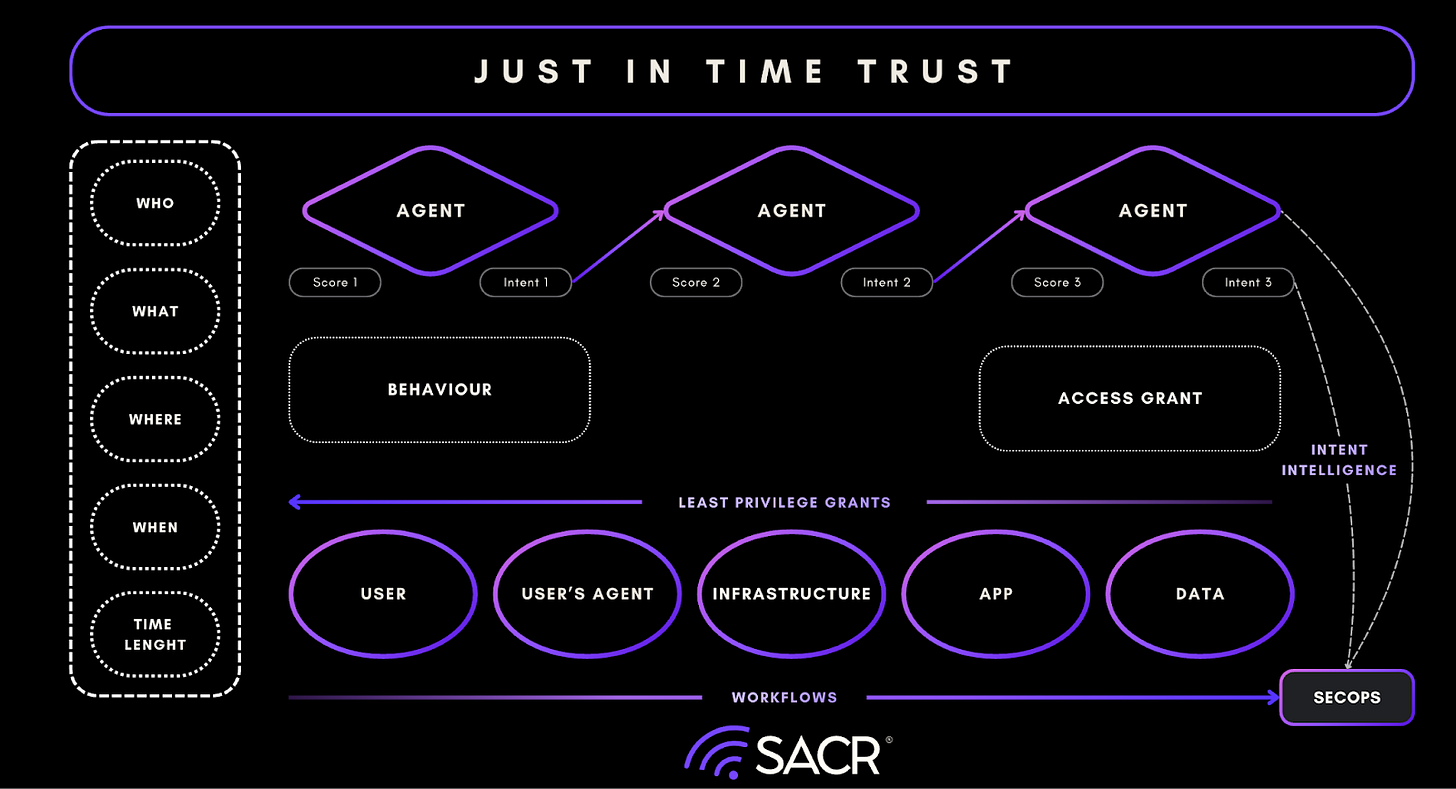
The Rise of Just-in-Time Trust (JIT Trust)
Just-in-Time Trust (JIT Trust) represents the next evolutionary step beyond Zero Trust Architecture (ZTA). It emerges as a unified identity control layer designed for the speed of modern threats and the rise of autonomous, agentic systems and AI agents. Where Zero Trust redefined who can access what, JIT Trust redefines how long, under what conditions, and for what exact purpose access exists. Unified identity systems, stronger authentication, and just-in-time access must be contextually aware of intent.
At its core, JIT Trust treats access as a continuously evaluated, ephemeral resource rather than a static entitlement. Long-lived credentials and standing privileges are replaced with temporary, self-destructing Ephemeral Access Grants (EAGs) and short-lived, certificate-based authentication. These grants are narrowly scoped to the precise resources and actions required for a specific human, machine, or agentic task.
JIT Trust moves beyond traditional authentication toward continuous authorization grounded in behavioral and intent-based signals. Rather than validating identity once at login, the system continuously monitors an entity’s intent and behavior: the digital signals generated through AI prompts, tool usage, API calls, and execution patterns to dynamically assess risk and derive trust in real time. When behavior deviates from an established baseline or intent shifts unexpectedly, the system initiates a graduated response: privileges can be reduced, entitlements constrained, or access suspended entirely.
This model establishes Continuous Adaptive Trust (CAT): a control framework where trust is not assumed, but continuously earned and recalibrated. The result is a dramatically reduced attack surface, tighter blast-radius containment, and an access model that aligns with environments defined by automation, ephemerality, and machine-speed execution.
PAM Market Ecosystem
This landscape illustrates a Privileged Access Management (PAM) market that has expanded well beyond its historical roots in password vaulting and session control. What was once a narrow category dominated by a handful of incumbents has evolved into a broad ecosystem spanning identity providers, secrets management, cloud-native access platforms, developer-centric tools, and emerging authorization layers.
The presence of legacy leaders such as CyberArk, Delinea, and BeyondTrust alongside newer cloud- and API-native players like Apono, Britive, Teleport, and StrongDM reflects a market in transition rather than replacement. Incumbents continue to anchor regulated and hybrid environments, while newer entrants are redefining PAM around just-in-time access, zero standing privilege, and runtime authorization aligned with cloud and DevOps workflows. At the same time, adjacent identity vendors including Okta, SailPoint, and One Identity underscore the growing convergence between PAM, IAM, IGA, and identity threat detection.
Collectively, this ecosystem signals that PAM is no longer a point solution but a foundational control layer within the modern identity stack. As non-human identities, automation, and agentic systems proliferate, the market is shifting toward platforms that can enforce privilege dynamically, at scale, and in context positioning PAM as a central pillar of enterprise security architecture heading into 2026.
Based on our extensive work, we want to dive into next-gen platform that are set to capitalize on the next evolution of cloud and agentic PAM architecture. They include:
Apono
Britive
P0 Security
Teleport.
Analyst Assessment
Apono
Executive Summary
Apono is one of the up-and-coming startups within the next generation of PAM solutions. They represent a new class of modern and cloud-native mPAM solutions built for cloud-native and engineering-led environments as discussed earlier in the report.
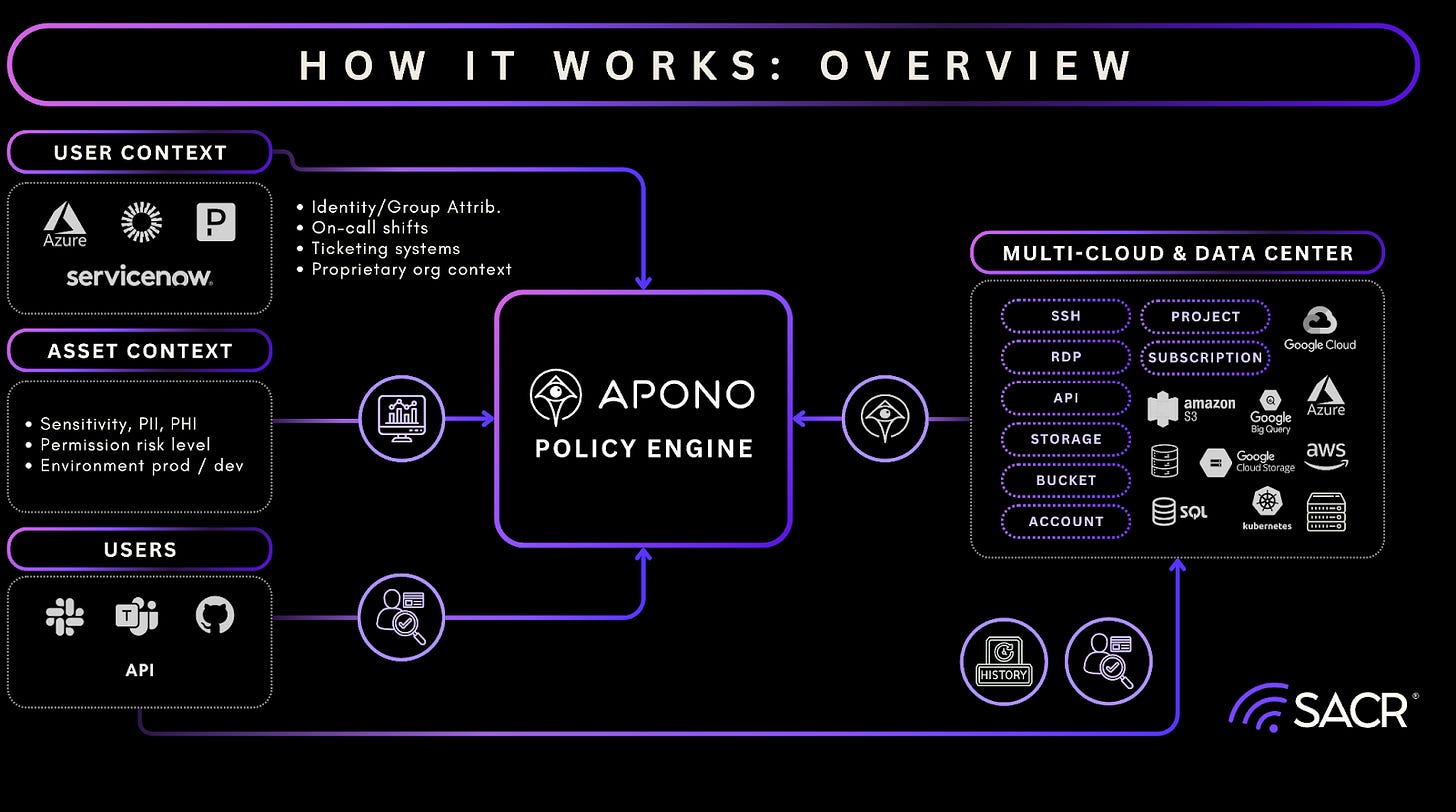
Apono has developed a modern architecture centered on Zero Standing Privilege (ZSP), Just-in-Time (JIT) permissioning, and real-time entitlement orchestration. The company’s core offering, ‘privileged cloud,’ is a cloud PAM solution that implements JIT controls to achieve ZSP. This is accomplished by dynamically granting access only when it is required, eliminating the need for permanent, elevated permissions. It utilizes an API-based approach (rather than an inline or proxy method) to create dynamic “access flows.” These flows provision permissions on-demand across various environments, including cloud platforms (AWS, Azure, GCP), on-premises infrastructure, and non-cloud native services.
Apono reports close to 100 customers of different sizes, with most using both Privileged Cloud and InfraGuard, their infrastructure protection and monitoring component that works alongside their JIT access capabilities.
A meaningful share of customers are large, regulated enterprises (financial institutions, airlines, and other highly regulated industries) with stringent regulatory requirements. Apono has demonstrated support for large-scale, cloud-native organizations, with documented use cases managing privileged access for 10,000+ engineers daily. Enterprises frequently deploy Apono alongside traditional PAM to modernize cloud and infrastructure access, achieving a 96% reduction in standing privileges and strong developer adoption within 30–60 days.
The platform is best understood not as a traditional PAM replacement, but as a cloud privilege orchestration layer that complements existing vault-based PAM for legacy systems while addressing gaps those tools were never designed to solve. For organizations with large engineering teams, dynamic cloud infrastructure, and heavy reliance on non-human identities, Apono offers a materially different operational and security model.
Scope and Positioning
Apono operates at the intersection of several identity security domains:
Access Management (IAM / RBAC / ABAC)
Privileged Access Management (PAM / JIT / ZSP)
Cloud Infrastructure Entitlement Management (CIEM)
Non-Human Identity (NHI) governance
While the company is often grouped under PAM, its architectural choices and feature emphasis align more closely with cloud-native privilege control than with traditional Privileged Access Security Management (PASM).
Detailed Capability Analysis
Based on our analysis of the company’s capabilities, these were some of the capabilities we were most impressed with:
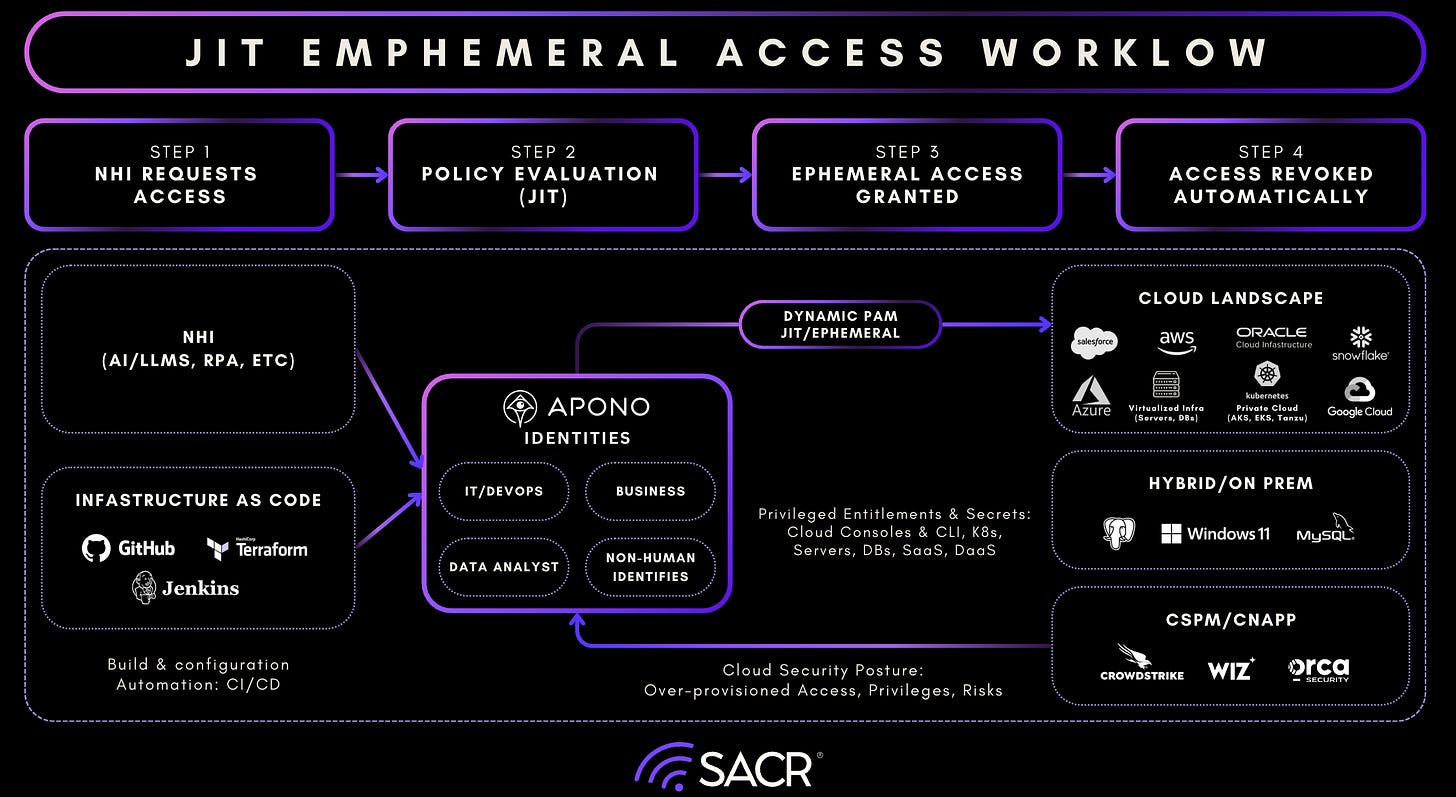
Just-In-Time Access and Zero Standing Privileges: At the core of Apono’s platform is a Just-in-Time (JIT) access model that eliminates standing privileges entirely. Privileged access is granted only when required, scoped precisely to the task at hand, and automatically revoked afterward. This model materially reduces the attack surface associated with always-on privileges or the risk of credential theft. Importantly, Apono applies this model not only to human users, but across databases, cloud services, compute resources, and automation workflows, enabling frictionless access without sacrificing control.
Visibility, Governance, and Anomaly Detection: Apono provides organization-wide visibility into privileged access across Cloud infrastructure (AWS, Azure, GCP), SaaS platforms and Servers, VMs, Kubernetes, and data stores. The platform identifies overprivileged users and service accounts, entitlement creep and risky access patterns. Alerting and anomaly detection are tightly coupled with enforcement, enabling security teams to move from passive visibility to active risk reduction rather than relying solely on reporting.
Cloud Infrastructure Entitlement Management (CIEM): Apono has built a core part of its capabilities around CIEM functionality. The platform continuously discovers cloud resources and identities and groups them into logical access scopes based on environment (prod / non-prod), sensitivity (PII, PCI, regulated data), and tags and metadata. A key insight is that as customer environments evolve, the dynamic nature of these access scopes significantly reduces policy maintenance over time. Apono has emphasized enforcing least-privilege access dynamically across multi-cloud environments. As CIEM increasingly becomes a core component of CNAPP strategies, Apono’s tight coupling of CIEM with real-time privilege enforcement stands out. This ensures security that keeps pace with development.
Non-Human Identity (NHI) Management: A key area of focus for Apono is managing non-human identities, including service accounts, automation tokens, and various workloads. To address this, they are prioritizing the beta release of its Agentic PAM solution to existing customers in January. his solution helps organizations achieve a Zero Standing Privilege (ZSP) environment by using an agent to perform real-time contextual validation of access requests, (implementing Just-in-Time and Just-Enough-Access principles).
Architecture and Deployment Model
Apono is API-driven and no-proxy by design. Instead of routing users through bastions or session proxies, it changes permissions directly on the target system at access time. This approach delivers faster deployment and higher developer acceptance. Users have direct system access once permissions are granted. By avoiding inline components, Apono also reduces failure points and scalability constraints common in proxy-based PAM architectures.
Legacy PAM Complementary
Apono is often deployed alongside CyberArk for traditional vault, mainframe, and legacy PAM use cases, which signals trust in demanding environments. Apono does not position itself as a primary vaulting solution. Instead, it integrates with existing vaults and session management platforms (e.g., CyberArk, BeyondTrust), particularly for on-premises environments, legacy systems, mainframes, and older databases.
One of the capabilities we were impressed with is its Policy and Access Model. This policy engine expresses access as risk-aware “access flows,” validating real-time context such as on-call status, ticket attributes, environment sensitivity, and MFA or approval requirements. We increasingly believe this approach will be more important in this space
Scale & Enterprise Readiness
Apono has demonstrated support for large-scale, cloud-native organizations, with documented use cases managing privileged access for 10,000+ engineers daily. Enterprises frequently deploy Apono alongside traditional PAM to modernize cloud and infrastructure access, achieving a 96% reduction in standing privileges and strong developer adoption within 30–60 days.
Apono represents the new generation of PAM: cloud-native, developer-centric, and built around Zero Standing Privilege. The company’s $34M Series B funding underscores market demand for alternatives to vault-centric models.
As PAM has evolved from vault- and bastion-centric models toward identity-native, API-driven control, organizations are increasingly prioritizing access velocity and operational efficiency alongside risk reduction. As one security leader noted:
“We’ve reduced the amount of time it takes people to get access to the things they need to do their job, and on top of that, we’re preventing tens of millions of dollars of potential data breach.”
— Drew O’Connor, Director of Security and Cloud Operations, Labelbox
The primary challenge for Apono will be displacement versus augmentation. In hybrid enterprises with deep legacy footprints, Apono is more likely to augment than replace incumbent PAM. Over time, however, its model aligns more closely with where cloud security architectures are heading. It is important to highlight that Apono differentiates itself through a cloud-first PAM architecture purpose-built for modern, fast-changing infrastructure, where constant resource discovery, dynamic permissioning, and Just-in-Time access are more practical than static role definitions. Its ability to automatically group cloud resources into logical access scopes, enforce granular and automated policies with minimal operational overhead, and manage both human and non-human identities at scale makes it particularly well suited for organizations where most engineers are effectively privileged users.
This resonates with customers operating under strict compliance and audit requirements, as one enterprise architect noted:
“We manage sensitive databases and various hybrid cloud data repositories, and it’s crucial for our engineering and data analysts to access this information securely and efficiently. We needed a solution that allowed them to access only what they needed, when they needed it, while also meeting the audit requirements of our Fortune 500 clients. Apono has been instrumental in achieving this. Their just-in-time and just-enough access solution has not only streamlined our processes but has also ensured robust access control and compliance. We can now provide the necessary access with confidence, knowing that our data remains secure and our clients are satisfied.”
— Avner Cohen, Architect, Workday
At the same time, Apono’s focus and status as an earlier-stage company introduce trade-offs. It lacks the decades-long brand recognition, regulator familiarity, and breach-tested history of incumbents like CyberArk, Delinea, and BeyondTrust. Its product breadth is narrower, prioritizing dynamic cloud access over deep vaulting, session recording, and legacy platform support, and its ecosystem of integrations, global services, and channel partnerships is still maturing. As a result, Apono is strongest as a modern privilege orchestration layer for cloud, databases, and Kubernetes-heavy environments, but will likely coexist with, rather than fully replace, established PAM platforms in enterprises with significant legacy or highly regulated infrastructure. It will be crucial for the company to continue maintaining its competitive advantage.
Conclusion
Apono fits best in environments where privileged access is driven by cloud infrastructure, large engineering teams, and a growing mix of human and non-human identities. Its architecture is designed around eliminating standing privileges through real-time, API-driven access rather than managing long-lived credentials. In practice, this makes Apono less of a traditional PAM replacement and more of a privilege orchestration layer that sits alongside existing vault-based systems, modernizing access where legacy tools struggle.
The platform has shown it can operate at meaningful scale, including in regulated enterprises, while maintaining strong developer adoption and measurable reductions in standing privilege. At the same time, Apono lacks the breadth and legacy platform depth of established PAM vendors, which makes coexistence more likely than displacement in hybrid environments. Where cloud-native infrastructure and dynamic access patterns dominate, Apono’s model aligns well with how privileged access is increasingly being enforced.
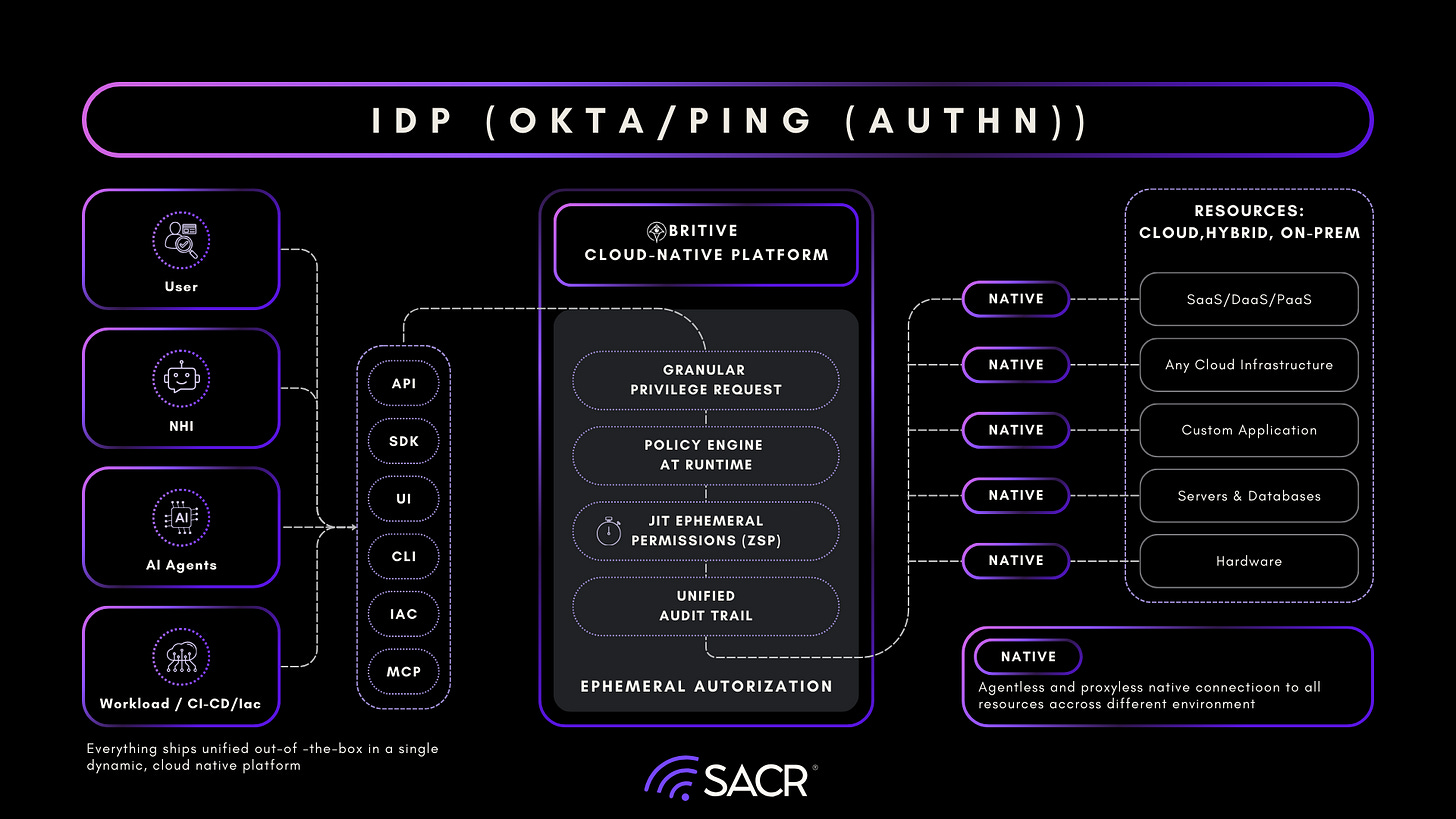
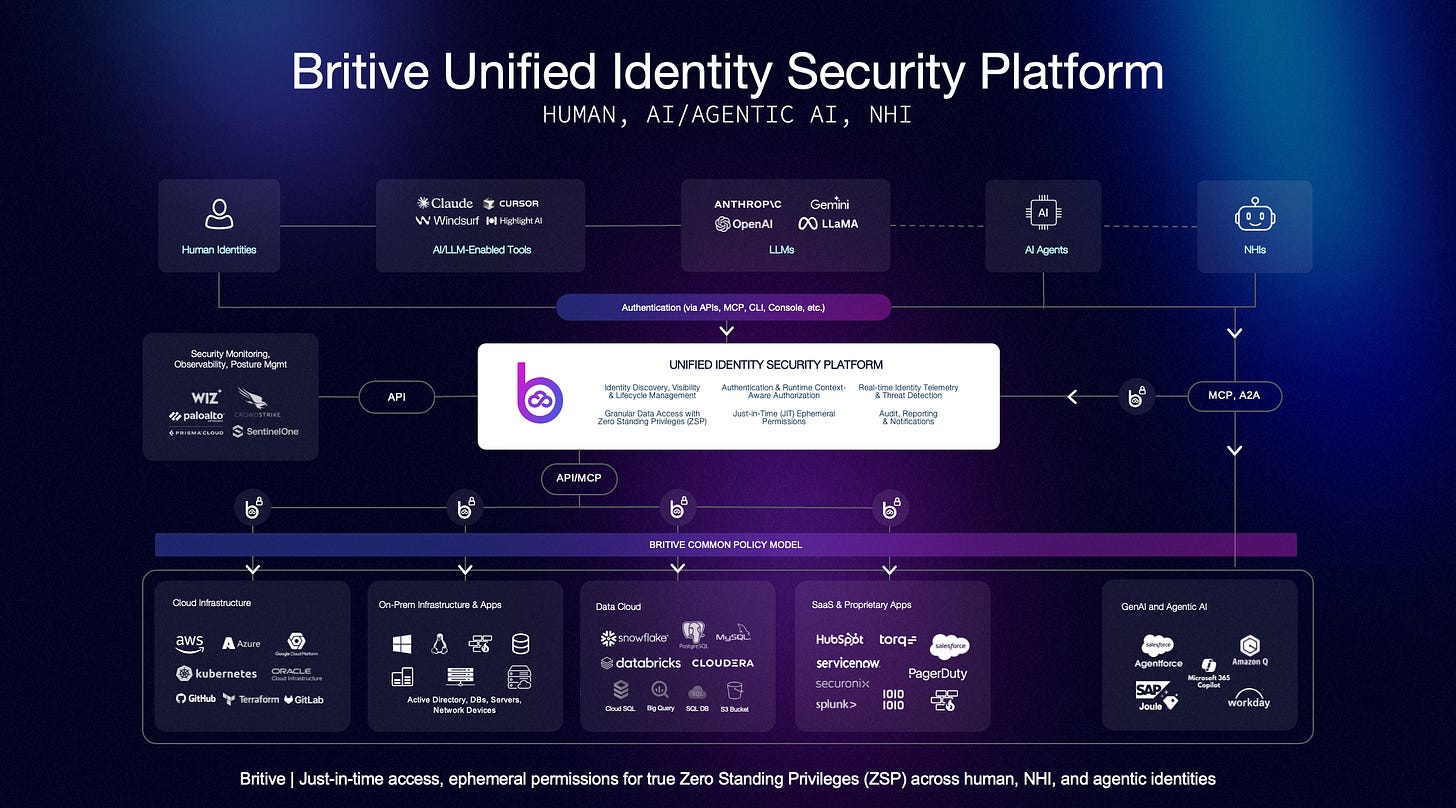
Britive
Executive Summary
Britive has emerged as a next-generation, cloud-native Privileged Access Management (PAM) platform architected around runtime-centric authorization rather than a vault-centric credential store. By enforcing access decisions at runtime using native control planes and APIs, the platform eliminates the need for persistent privileged accounts or credential checkout. This design enables a Zero Standing Privilege (ZSP) operating model, where permissions are created only when needed, scoped to the task, and automatically revoked once execution completes. In contrast, legacy Phase 1 PAM providers (e.g., CyberArk, Delinea) rely on persistent accounts and vaulted credentials that continue to exist even when access is not actively in use.
Broadly, Britive supports three distinct identity classes under a unified authorization model: human identities, non-human identities (NHIs) such as those used by workloads and pipelines, and agentic AI identities. In cloud-native environments, this model also extends to Kubernetes, where privileged access often spans clusters, namespaces, and platform services and benefits from the same time-boxed, policy-governed authorization approach.
Core Architectural Philosophy
From our analysis, Britive’s primary technical differentiator is its agentless and proxyless approach. While many modern competitors still utilize connectors or jump boxes to gate access, Britive integrates directly into the native identity control planes of major Cloud Service Providers (CSPs). We observed that, as a SaaS-native platform with an agentless, proxyless design for cloud-native targets, Britive can typically be stood up quickly without the overhead of deploying and maintaining proxy-heavy architectures. Onboarding can be accelerated through standard identity integrations, including SSO (SAML 2.0) and automated provisioning (SCIM 2.0), enabling teams to sync users and groups from providers such as Okta, Ping, and Microsoft Entra ID and begin building a common policy layer rapidly across environments.
Secondly, we believe Britive has a strong common policy model and access profiles system. We were impressed to see that Britive has an abstracted policy layer that spans all target systems, including cloud, SaaS, and on-premises environments (depending on system requirements). This provides unified security controls (MFA, ServiceNow integration, approval workflows) regardless of whether individual systems natively support them. This is an important differentiator that few vendors provide consistently across the ecosystem.
Britive’s architecture separates the authorization control plane from the underlying entitlement systems of target resources. Rather than simply placing users into native groups or roles for a fixed time window (the industry’s standard JIT model), Britive constructs access profiles as collections of permissions wrapped in a unified policy framework that applies consistently regardless of backend system capabilities.
Britive intentionally abstracts each target system’s entitlement model. This abstraction provides a common layer of security controls, including MFA challenges, approval workflows, ServiceNow integration, time-of-day restrictions, and IP constraints, that persist whether AWS supports those features natively or not, whether Google does or does not, or whether an on-premises Active Directory domain has step-up verification built in.
Traditional PAM models rely on a linear cost curve, as scaling privileged access security requires substantially more spend on vaults, agent- and proxy-based infrastructure, and operational headcount. However, by leveraging a cloud-native architecture managed via Infrastructure-as-Code (IaC) and Policy-as-Code (PaC), Britive decouples security enforcement from asset expansion.
This allows security teams to dynamically mint permissions at runtime for all identity types, maintaining consistent control across global environments without the compounding operational debt of vault-based systems that rely on static infrastructure.
Detailed Capability Analysis
Profiles as Portable Policy Containers
Britive’s capability goes beyond just defining a set of permissions for access. Each access profile is a reusable and portable construct that an administrator creates once and deploys across diverse environments, including cloud infrastructure, SaaS applications, and on-premise resources, without the need to rewrite entitlement logic for every system.
These profiles encapsulate the necessary permission set, such as:
S3 access for a specific account.
Elevated Kubernetes access restricted to a particular cluster and namespace.
Snowflake administrative roles limited to a certain warehouse and database/schema.
Temporary Salesforce admin privileges restricted to specific roles or permission sets.
Domain admin membership within Active Directory.
Furthermore, each profile includes a policy envelope, which incorporates:
Configurable expiration with an automatic forced check-in.
Requirements for human-in-the-loop approval.
Segmentation based on identity type (e.g., humans, service identities, AI agents).
Conditional controls.
This matters for hybrid and multi-cloud environments because, in enterprises spanning AWS, Azure, GCP, or legacy on-premises infrastructure, this model collapses operational complexity. A security team can enforce a single approval workflow for privileged access whether the target is an AWS IAM role, an Azure role assignment, a Google Cloud service account, a Kubernetes cluster, Snowflake, or a database behind the firewall.
The Access Broker technology extends the cloud-native Britive platform into private and on-premises zones, treating them as “resource profiles” governed by the same policy primitives. For example, a GitLab pipeline provisioning EC2, querying on-premises SQL, and writing to cloud-based MySQL illustrates how a single non-human identity can navigate the full stack through one authorization authority. Operationally, this model also benefits from rapid onboarding of target systems, enabling teams to bring cloud and application entitlements into scope and construct a common policy layer without deploying a complex network of connectors and session proxies.
Britive explicitly contrasts this approach with “basic just-in-time tools” that simply add a user to a group for a fixed duration and remove them afterward, with no intermediary policy layer or cross-system governance. Those tools inherit the limitations and inconsistencies of each target system. Britive’s abstraction compensates for these gaps while still honoring native constructs such as AWS role assumption or Azure PIM. The result is heterogeneous infrastructure managed through homogeneous policy and a control plane that scales with organizational complexity rather than multiplying it.
Developer-Centric CI/CD Integration
Britive addresses developer friction, a frequent byproduct of legacy PAM, by embedding security controls directly into the DevOps pipeline through its PyBritive CLI and SDK. The platform’s dynamic CLI tool is typically downloaded and executed as part of a CI/CD job and exists only for the duration of that job. The only setup required is configuring the pipeline to download PyBritive and execute the desired commands. The tool leverages OIDC and workload federation to authenticate without static API tokens or hardcoded secrets.
This “secretless pipeline” approach ensures access exists only for the duration of a specific task, effectively enforcing Zero Standing Privilege (ZSP) for automated workflows. Furthermore, Britive provides branch-level scoping, allowing security teams to restrict permissions based on specific repositories or environments, preventing accidental or unauthorized production changes during development cycles.
Unified Identity Security for Hybrid Environments
A core architectural pillar of the Britive platform is its Common Policy Model, which establishes a consistent security control layer across heterogeneous cloud, SaaS, and on-premises environments. By abstracting platform-specific entitlements, such as those found in Snowflake, SQL Server, or Active Directory, into a single framework, the platform allows teams to define fine-grained policies once and enforce them universally. This model applies the same Just-in-Time (JIT) and ZSP rigor to non-human identities as it does to human users, an essential capability given that machine identities often outnumber human identities by a factor of 40 to 50. To bridge the gap with legacy systems, Britive utilizes access broker technology to extend modern API-driven privilege controls into traditional on-premises infrastructure.
Agentic AI Identity and Security
Britive has positioned itself as an early entrant in the emerging category of Agentic Identity and Security Platforms (AISP). The platform manages the full lifecycle of autonomous AI agents, treating them as distinct identities requiring intent-aware, context-sensitive authorization. Key governance features include impersonation controls that restrict an agent’s ability to act on a user’s behalf to specific matching profiles, thereby containing risk even in scenarios involving prompt injection. For high-risk operations, the platform supports human-in-the-loop (HITL) workflows, enabling administrators to intercept and approve actions prior to execution. To ensure accountability in multi-agent systems, Britive establishes agent provenance and agent-to-agent trust using verifiable identity standards such as SPIFFE.
Practitioner Assessment: Why Britive Matters
Blast Radius Reduction
By enforcing True ZSP, the platform ensures no privileged accounts exist to be compromised when not in use.
Native Role Assumption
Britive leverages native cloud constructs, such as role assumption in AWS, to grant ephemeral credentials. This ensures users do not maintain standing accounts or persistent “keys to the kingdom.” By using direct API functionality, Britive can administer native services across AWS, Azure, GCP, and OCI without the operational overhead of deploying middleware or agents for services such as Lambda or compute.
The agentless, proxyless design allows DevOps and SRE teams to maintain speed without altering core workflows.
Separation of AuthN and AuthZ
Britive allows organizations to use existing Identity Providers (e.g., Okta, Ping) for authentication (AuthN), while Britive manages the granular runtime authorization (AuthZ)
Agentic Readiness
Although still in early stages, Britive provides the runtime authorization framework needed to audit and govern agentic tasks.
Compliance & Audit
A single Unified Audit Trail provides a comprehensive record of all human, machine, and AI activities for audit and forensics.
Identity Intelligence and Analytics
Beyond raw logs, Britive provides reporting and analytics designed to turn identity and access data into measurable insight. This includes dashboards and reports to visualize privilege assignment and usage over time, detect potential identity and access risks, and track KPIs such as progress toward Zero Standing Privileges (ZSP), helping security teams produce cleaner audit evidence without manual data stitching.
Things To Watch
Britive’s architecture is optimized for API-driven role assumption and workload federation, such as OIDC. While Britive uses an Access Broker to extend controls to on-premises Windows and Linux servers and some databases, it does not offer the same exhaustive out-of-the-box support for the long tail of legacy enterprise hardware and niche industrial (OT/ICS) protocols found in CyberArk’s 350+ integrations. For organizations with a high percentage of non-cloud-native infrastructure that cannot support ephemeral access, Britive’s reliance on its Universal Secrets Manager may feel less robust than a specialized legacy vault.
Additionally, Britive’s session monitoring is runtime-centric and designed to be lightweight and frictionless for developers. However, it does not focus on endpoint PAM use cases, such as securing local administrator rights across thousands of corporate laptops, nor does it provide the same level of granular, keystroke-level isolation for RDP or SSH sessions that proxy-based PAM platforms like CyberArk deliver for maximum compliance.
Conclusion
For IT and identity security practitioners operating cloud- and developer-centric workflows, Britive represents a shift from static security to dynamic authorization. It is best suited for cloud-forward organizations where developer productivity and the rapid scaling of non-human and AI identities make traditional vault-based PAM a bottleneck. Britive should be viewed not just as a tool for securing administrators, but as a foundational control layer for modern identity infrastructure built on abstraction and runtime policy enforcement.
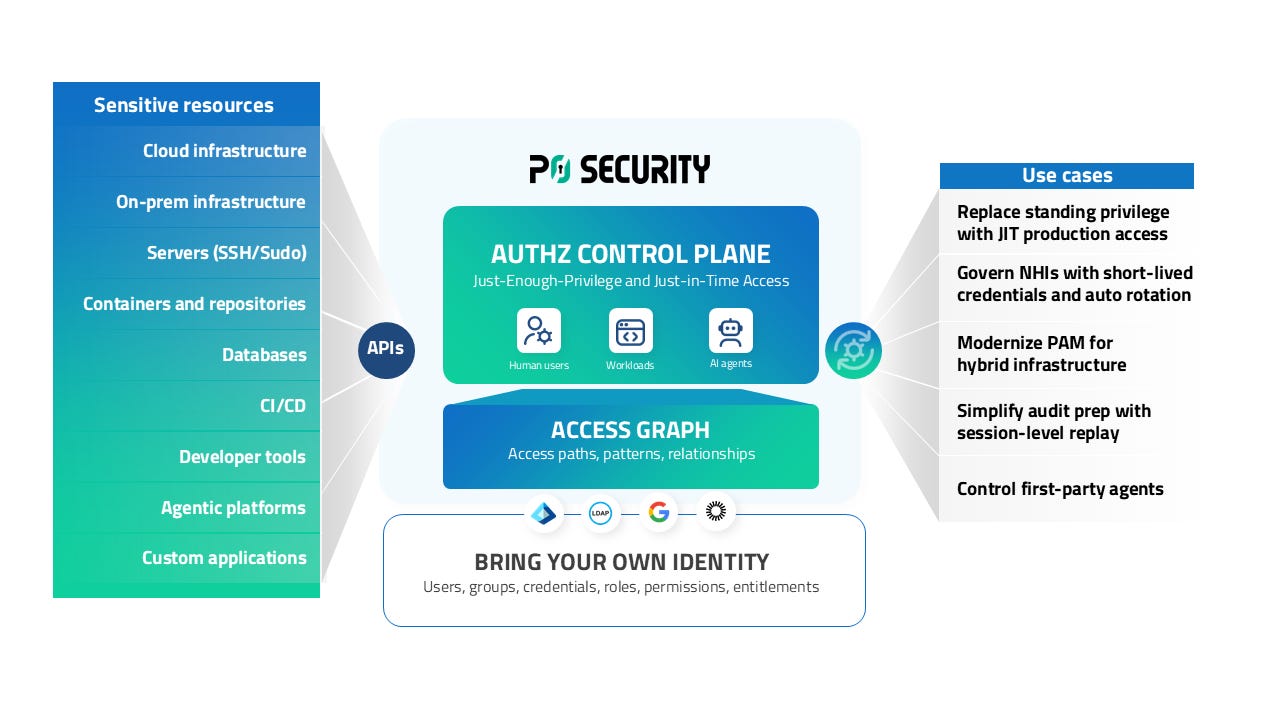
P0 Security
Executive Summary
P0 Security is a cloud-based Privileged Access Management (PAM) platform designed to address the challenges of hyper-fragmented, cloud-native environments by shifting the focus from credential vaulting to identity-native authorization. Although the company is much younger than many major PAM vendors in the space, the platform is notably modern compared to earlier traditional “heavy” PAM solutions that rely on bastions and vaults.
P0 Security utilizes an API-led orchestration layer to enforce Zero Standing Privilege (ZSP) at scale. By integrating directly with existing Identity Providers (IdPs) such as Okta or Entra ID, P0 provisions Just-in-Time (JIT) and Just-Enough Privilege (JEP) access for human users, workloads, and AI agents across multi-cloud and hybrid infrastructure.
Core Architectural Philosophy
Similar to other players discussed, P0 Security’s differentiation is rooted in its provisioning access and identity-centric approach, which aims to secure the business without interrupting developer velocity.
Based on our analysis, its core differentiation lies in SSH (Secure Shell) and RDP (Remote Desktop Protocol) access tied directly to corporate identity, both of which are commonly used to remotely control servers or computers.
Historically, accessing servers via SSH or RDP required:
Shared admin accounts (e.g., “root” or “Administrator”) used by multiple people
SSH keys or passwords managed separately from corporate identity
Static credentials stored in password vaults or shared across teams
These approaches created issues around traceability, credential sprawl, and security gaps. P0 Security’s approach removes shared accounts and static credentials, ensuring that every remote session is tied directly to an established corporate identity (the same identity used for Active Directory, Gmail, Slack, or Okta).
This capability continues to be central to the platform. Developers authenticate via corporate IdP credentials with no shared admin accounts, no SSH key management, and no secondary credentials. Every session is tied to an individual identity with full audit trails. This identity-native authorization method ensures every session is tied directly back to the corporate IdP identity rather than relying on shadow accounts or shared static credentials. The focus is more on removing friction for developers, governance overhead for security and the costs of heavy infrastructure maintenance.
Detailed Capability Analysis
The following analysis examines P0 Security’s technical capabilities, focusing on how their “Identity-Native” architecture addresses the “last mile” of privileged access in cloud-native and hybrid environments.
Just-Enough and Just-in-Time Server Access
A primary differentiator for P0 is its bastionless JIT SSH capability, which challenges the traditional vault-and-proxy model. By eliminating static credentials and shared admin accounts, the platform replaces long-lived SSH keys with short-lived, identity-based access tied directly to the corporate Identity Provider (IdP).
From a practitioner’s perspective, this removes a common bottleneck in legacy systems. Users request access through lightweight ChatOps workflows (Slack or Teams) or a CLI wrapper. Upon approval, P0 provisions a short-lived and tightly scoped IAM role or native entitlement. Sessions are automatically terminated upon expiry or manual revocation, ensuring no “shadow accounts” or standing privileges persist once the task is complete.
Granular Scoping for Code, Data Stores and Entitlements
P0 Security provides specialized depth for modern production stacks, particularly within Kubernetes (EKS, GKE, AKS) and high-scale data stores like Snowflake and Postgres. In Kubernetes environments, the platform moves beyond broad cluster-level access to allow “task-specific scoping” at the namespace or even individual pod level. This allows developers to “exec” into specific containers for troubleshooting without being granted cluster-wide permissions that could expand the blast radius. Similarly, for database resources, the platform can provision granular access down to the ability to run specific queries rather than granting broad, standing role permissions, effectively delivering “just-enough-privilege” (JEP) as the operational default.
The “Closed-Loop” Privilege Governance
To move an organization toward a Zero Standing Privilege (ZSP) target state, P0 includes a posture product designed to identify and quantify privilege-related risk in real time. This “closed-loop” system identifies unused or excessive privileges such as role bindings that have not been exercised in 90 days and provides security teams with actionable instructions or automated JIT policies to remediate those risks. Beyond a one-time cleanup, the platform performs continuous monitoring for “drift,” where access patterns deviate from defined guardrails. By surfacing these over-permissioned roles and automatically converting them into policy-driven, time-bound controls, P0 enables enterprises to transition from a reactive static defense to a dynamic, authorization-centric security model.
Analyst Perspective: Practitioner Considerations
Bring Your Own Identity (BYOI) Architecture: P0 emphasizes a pure authorization model with no infrastructure deployment. It leverages existing IdPs (Okta, Active Directory) and native cloud APIs to auto-discover resources and provision Just-in-Time access. No agents, proxies, or bastions are required. All activity ties directly back to corporate identity without cross-system correlation.
Access Graph: The platform builds a contextual visualization of all access paths, patterns, and relationships between users, machine identities, and resources. This allows security teams to identify risky “lurking” privileges that traditional tools often miss.
Proxy-Free Deployment: Because P0 operates as an orchestration layer outside the direct data path, it auto-discovers privileged resources via APIs without requiring the deployment of proxies or jump-hosts. This minimizes downtime risk and simplifies operations for hybrid enterprises.
Strengths
Policy-Based JIT Provisioning
P0 has good cloud-based JIT access scoping down to individual S3 bucket folders, specific database roles, or even single queries without broader role permissions. Configurable time windows, approval workflows (including auto-approval based on conditions like PagerDuty escalations), and dynamic IAM role creation with precise permissions.
Since P0 started with building cloud-based access governance controls, they have a good base of built-in cloud security posture management (CSPM) features that identifies unused standing privileges and role bindings (90+ days unused), then provides both remediation instructions and one-click conversion to JIT policies. This we believe helps customers achieve zero standing privileges by showing where unused access exists and automatically migrating identities to the JIT model.
Zero-Friction Developer UX: Native ChatOps (Slack/Teams) and CLI integrations drive high adoption among engineers.
Hybrid Maturity: While P0 announced hybrid/on-prem support (SSH/RDP) in late 2025, it remains a cloud-first platform compared to decades-old legacy incumbents.
Identity Lineage: Tying every action to a “real” IdP identity simplifies audits and removes the correlation overhead of shared accounts.
Direct Critical Path: P0 positions its API-led orchestration as being “outside the critical path” to reduce downtime risk, though it remains a critical control point.
Cost Efficiency: Eliminating the need for vaults, bastions, and shadow accounts reduces infrastructure and governance overhead.
Platform Consolidation: Organizations must decide if they prefer a specialized “AuthZ Control Plane” like P0 or a larger suite from consolidated vendors like Palo Alto Networks (post-CyberArk acquisition).
Things To Watch
For a “hybrid” enterprise with significant on-prem stacks, P0 lacks the decades of hardened connectors required to manage privilege for non-API-driven legacy hardware that cannot easily adopt a just-in-time (JIT) workflow. Legacy market leaders like CyberArk maintain a massive catalog of out-of-the-box integrations for “long-tail” infrastructure, including Mainframes, AS400, and Industrial Control Systems (OT/ICS).
P0 Security has an architecture that is predominantly API-led. While their historical focus has been on cloud servers and databases, recent months have seen an expansion of support to include traditional on-prem servers and databases. This deepening of capability will further extend to Active Directory in late 2025.
Broadly, compared to vendors like CyberArk’s Digital Vault, which provides policy-based rotation for nearly any credential type, P0 is a “authorization control plane” optimized for modern production stacks (K8s, Snowflake, AWS). However, we see P0 as being a strong complementary fit for large enterprises wanting a combination of both capabilities bolted into one stack.
Conclusion
In summary, P0 Security is a good choice for enterprises looking to modernize their PAM stack specifically for ephemeral clouds and Kubernetes environments where legacy tools often struggle. It is a complementary fit to vendors with strong on-prem systems. P0 shines very well for developer heavy, cloud environments that typically have strong and simple authentication controls around SSH and data store demos where teams can achieve total session auditability without shared keys or complex proxy infrastructure.
Teleport
Executive Summary
Teleport is one of the leading PAM vendors, with over 600 customers, more than $50M in ARR, and deployments across three of the top ten software firms, three major financial institutions, and three of the largest AI companies. Teleport has demonstrated breadth and maturity at enterprise scale, supporting complex environments where compliance and security cannot be compromised.
Teleport’s privileged access foundation is built around the concept of infrastructure identity. Rather than managing credentials through traditional vaults and proxies, Teleport eliminates the need for secrets entirely through a certificate-based, Zero Standing Privilege architecture that treats all identities (human, machine, workload, and AI agent) as first-class citizens under a unified control plane.
At its foundation, Teleport enforces Zero Standing Privilege (ZSP) by issuing ephemeral X.509 certificates tied to corporate identity providers such as Okta, Entra ID, and Active Directory. These certificates automatically expire within minutes to hours, ensuring that no long-lived credentials exist to be stolen or mismanaged.
The platform’s core thesis is that privileged access should not exist when work is not being performed. This security invariant eliminates attack surface while accelerating developer productivity. Teleport provides unified identity governance across servers (SSH/RDP), Kubernetes clusters, databases, internal applications, and cloud APIs. Access is provisioned just in time with granular policy enforcement, approval workflows, and automatic revocation upon expiration. By integrating capabilities traditionally siloed across IAM, IGA, PAM, and CIEM into a single cryptographic identity layer, Teleport enforces least-privilege access without the operational drag of credential vaulting, session proxies, or manual entitlement reviews.
Teleport operates at the convergence of multiple identity security domains. However, for this report, the core focus is on its Privileged Access Management (PAM) capabilities, specifically its just-in-time, certificate-based access to infrastructure. While often grouped under PAM, Teleport’s architecture and product philosophy align more closely with unified infrastructure identity than with traditional privileged credential management.
Detailed Capability Analysis
Certificate-Based, Vaultless Architecture
At the foundation of Teleport’s platform is a short-lived X.509 certificate model that replaces static credentials entirely. When a user or workload requests access, Teleport issues an ephemeral certificate tied directly to corporate identity, authenticated via Okta, Entra ID, Active Directory, or other IdPs. These certificates automatically rotate, typically within minutes to hours, ensuring that no long-lived secrets exist to be stolen, lost, or mismanaged.
This approach delivers Zero Standing Privilege (ZSP): when no work is being performed, no access exists. For organizations managing thousands of engineers or autonomous workloads, this eliminates credential sprawl, rotation burden, and vault maintenance overhead inherent to legacy PAM systems. Importantly, the certificates cannot be exfiltrated in a usable form; they are cryptographically bound to the requesting identity and expire automatically, rendering credential theft largely ineffective.
Just-in-Time Access with Policy Enforcement
Teleport provides granular, time-bound access across servers (SSH/RDP), Kubernetes clusters, databases, internal applications, and cloud APIs. Access requests are evaluated in real time against configurable policies that can include approval workflows, on-call status, compliance requirements, and device trust signals. Once approved, Teleport provisions the minimum necessary permissions for the defined task and duration, then automatically revokes access upon expiration.
This model addresses a core failure mode of traditional PAM: static role assignments that grant broad, persistent access “just in case.” By making least-privilege access the operational default, Teleport reduces blast radius while simultaneously improving developer experience, eliminating delays associated with credential issuance or complex vault checkout processes.
Session Recording, Monitoring, and Kill Switch
Session recording was once considered a legacy capability, but it remains a core requirement across modern platforms. Teleport captures full session recordings of privileged activity, including command-line input, database queries, and Kubernetes exec sessions. These recordings are indexed and searchable, enabling forensic investigation and compliance validation. Real-time monitoring allows security teams to observe active sessions, and a kill switch capability enables instant revocation of access across infrastructure when a compromised identity or policy violation is detected.
Importantly, Teleport’s architecture operates as an authorization control plane that provides native access directly through cloud APIs, reducing latency and eliminating single points of failure. Sessions are recorded and audited without forcing traffic through bottleneck infrastructure, a key differentiator from legacy bastion-based PAM architectures.
Architecture and Deployment Model
Teleport’s architecture is agentless, API-driven, and proxy-optional. The platform integrates with native cloud control planes (AWS IAM, Azure RBAC, GCP IAM), Kubernetes RBAC, database authentication layers, and application identity providers. Access is provisioned by dynamically creating short-lived roles or credentials through these native systems, ensuring that Teleport remains outside the critical data path for most operations.
For environments requiring session proxying, such as legacy SSH/RDP infrastructure or highly regulated environments mandating gateway controls, Teleport offers a bring-your-own-proxy model deployable as SaaS, self-hosted, or hybrid. Proxies can be deployed in customer VPCs or on premises, with control plane management handled by Teleport’s SaaS offering. This flexibility allows enterprises to balance operational simplicity with data residency and compliance requirements.
Teleport supports enterprise compliance frameworks including FedRAMP, SOC 2, DORA, PCI-DSS, and HIPAA, with granular audit logs, immutable session recordings, and policy-driven access controls that map directly to regulatory mandates.
Things To Watch
Competitive Pressure from Consolidation: Teleport must continue to differentiate on velocity, developer experience, and architectural simplicity. Some of field reports have suggested the need for them to further innovate their platform for the modern security stack.
Greenfield vs. Displacement: While Teleport displaces legacy PAM in cloud-native environments, hybrid enterprises may run Teleport alongside CyberArk or BeyondTrust for on-premises coverage, creating integration and operational complexity.
Legacy Infrastructure Coverage: While Teleport supports SSH/RDP for traditional servers, organizations with extensive mainframe, AS400, or industrial control system (ICS/OT) environments may require complementary solutions with deeper legacy protocol support.
Broadly, Teleport fit organizations where infrastructure is primarily cloud-native, and developer-centric. They have a full breadth of capabilities that offer a compelling alternative to vault-centric models that introduce friction, operational overhead, and architectural complexity. Teleport is a strong choice for CISOs seeking to evolve their PAM strategy, particularly as a primary access layer for cloud, Kubernetes, and data infrastructure. While it can complement existing PAM platforms in environments with substantial on-premises infrastructure, its simple architecture and high developer adoption often support gradual migration over time. The company’s focus on infrastructure identity and its traction among leading AI companies highlight its relevance as identity systems evolve from credential management toward governing access behavior and intent.
Conclusion
Privileged Access Management is shifting from a credential-centric control to a runtime authorization layer for modern identity security and increasingly, for agentic systems. Recent consolidation (most notably Palo Alto Networks’ acquisition of CyberArk) signals that privileged access is now viewed as a foundational control plane, not a standalone compliance product. Platform vendors are prioritizing privilege because it is where identity becomes enforceable and where breach containment is ultimately decided.
This transition is being driven by two structural forces.
First, cloud ephemerality has made standing privilege operationally and defensively unsustainable: infrastructure changes continuously, access needs are time-bound, and static roles cannot keep pace without creating excessive risk or friction.
Second, the fastest growth in privileged users is no longer human. Non-human identities already operate at machine scale, and agentic AI compounds the risk by introducing autonomous, multi-step execution that can amplify errors or adversarial manipulation at production speed. In this environment, privileged access maturity becomes a prerequisite for safe agentic adoption, not a downstream enhancement.
The vendor landscape highlighted in this report points to a clear direction of travel: modern PAM is moving toward Zero Standing Privilege (ZSP), policy-driven just-in-time access, and deeper integration with identity and infrastructure signals. Apono, Britive, P0 Security, and Teleport represent distinct architectural approaches to the same market requirement: privilege must be provisioned dynamically, scoped narrowly, verified continuously, and audited comprehensively across human, machine, and emerging agentic identities. Legacy vault-based PAM will remain durable in hybrid enterprises, but it is increasingly complemented by authorization-centric layers that better match cloud and automation realities.
Looking ahead, the outlook is constructive. As organizations modernize privileged access, they will not only reduce blast radius and credential sprawl, they will build the governance foundation required to safely unlock automation and agentic workflows. The next phase of identity security will be defined by how effectively enterprises can convert privilege from a static entitlement into a measurable, adaptive, and continuously enforced control system.
Our next report will focus on the next-gen IDP/SSO/Access control plane for agents. We will focus on how we need to rethink how agents will be authenticated in an agentic world where humans and machine become central. Keep up for more.




This is an excellent and deeply thoughtful piece. You do a great job showing why PAM is no longer a niche identity control, but a foundational layer for governing privileges across humans, machines, and increasingly, agents.
The stat about organizations managing 40-50x more non-human identities than human ones is alarming! The governance gap for service accounts, API keys, and now autonomous agents feels like the next major breach vector if we don't get ahead of it. Thanks for sharing this report.