A Deep Dive Into The Cloud & Application Security Ecosystem
Discussion on various market segments, emerging trends, leading vendors, and defining what differentiates the leaders.
Software has become the backbone of our digital lives today. As more enterprises have adopted cloud-native microservices and applications, their attack surface has broadened. This has heightened the need for robust cloud/application security tools and practices. As a result, cloud and app security continues to be one of the fastest-growing cybersecurity markets in 2024. However, there is a big question around which pockets are seeing real growth vs. fad? what does a platform look like in this category?
In my beginner’s guide to cybersecurity, I provided a framework for understanding the entire sector, but today, my goal shifts towards dissecting the cloud and application security ecosystem more intricately. This is both an educational piece, but one that touches on emerging trends. Over the next few weeks, I’ll be diving deeper into parts of the AppSec, Cloud and Software supply chain space using some vendors to illustrate these examples. The goal will be trying to define what makes a platform in software security. Also, expect some insights into identity security and next-gen SIEM technologies. My goal is to clarify some of the misconceptions about this market and help operators put some structure around this category
Actionable Summary
Cloud and app security continues to be top major priority for enterprises coming into 2024. The 2024 Crowdstrike Global Threat Report highlights a significant escalation in cloud security challenges, with a 110% upsurge in cloud-conscious incidents and a 75% rise in cloud intrusions. The deployment of Generative AI by threat actors like Scattered Spider to orchestrate complex attacks against enterprise cloud environments underscores the critical role security continues to play in the cloud and application development domains.
Shift left and shift right: One way to understand the cloud and app security industry is to consider the security solutions that are required during the pre-deploy and post-deploy phase of software development. Your shift left categories are software composition analysis (SCA), software supply-chain security (SSCS) and application security testing tools (AST). The shift-right has to do with solutions closer to/in deployment for production environments. These include cloud security vendors, application runtime security (ARS), SaaS Security and vulnerability management solutions.
Cloud and application security challenges: Securing cloud environments requires addressing the dynamic, ephemeral, and scalable nature of these platforms. Maintaining visibility across cloud workloads is a critical concern. The evolution of application development, marked by increased use of open-source tools by software teams, adds to these challenges. Recently, a significant focus has been on closing the gap between code scanning and runtime environments in the cloud, ensuring developers have clear insights into the health of their applications in deployment.
The battle for the Code-to-Cloud Platform: Numerous software security companies are vying to establish themselves as comprehensive software security platforms. Code scanning and software supply chain services are seeking to integrate cloud security and runtime capabilities. Concurrently, cloud security providers are aiming to enhance their offerings with code security and Application Security Posture Management (ASPM) products. While no vendor currently offers a fully mature solution across all these domains, the evolving landscape promises interesting developments.
The Major Cloud & App Security Categories
This market map highlights the major categories of the cloud and app ecosystem. There are a few sub-sectors and vendors that I haven’t discussed for simplicity's sake, but these are the most important categories for any operator wanting to understand the space. To learn more about other vendors within this ecosystem, I recommend visiting Cypher to learn more about a variety of categories and players and their different solutions.
The Cloud & App Security Delineation
At its core, software acts as the intermediary that enables interaction between hardware and users within an enterprise's network. The process of creating and deploying applications, whether for on-premise or cloud environments, involves developers navigating through the software development lifecycle.
The landscape of software security has seen the emergence of numerous new categories only in recent years, largely due to the proliferation of cloud-native applications. This boom has subsequently led to a surge in security breaches, as attackers increasingly recognize developers working in cloud environments as prime, vulnerable targets. Such vulnerabilities present significant opportunities for attackers to inflict substantial damage on an organization. Wiz revealed that enterprises have, on average, 200 critical cloud issues that could cause a breach if exploited.
Many of the major software-related risks include open-source supply chain attacks that target the software development process, such as the embedding of malicious code at its source. This tactic distributes the code across multiple enterprises that use the software, as seen in incidents like the SolarWinds attack. We’ve also seen data breaches into cloud environments, cloud misconfiguration, insecure APIs being exploited, and Distributed Denial of Service (DDoS) attacks disrupt enterprises.
Software Security Solutions Step In:
As a result, we’ve seen cybersecurity companies evolve to protect both the developer and the infrastructure used to build these applications. The software security category has evolved from purely securing applications to more emphasis on securing the software development stages.
Securing software development stages (shift-left): These solutions are built to secure the earliest stages of software development. They are primarily scanners that scan source code and secure aspects of the build and deploy phases. They involve code-level scanning, software supply chain (SSC), application security testing (AST), threat modelling, and more.
Securing Open-Source: Software Supply Chain (SSCS) and Software Composition Analysis (SCA) security solutions
Code Scanners & Application Security Testing (AST)
SAST: Static Application Security Testing,
DAST: Dynamic Application Security Testing & Web App Scanner
IAST: Interactive Application Security Testing
Securing applications (shift-right): These are solutions built to protect against cyber-attacks after an application has been built and deployed. It involves categories:
Cloud Infrastructure Security
CNAPP: Cloud-Native Application Protection Platforms (CWPP - CIEM - CSPM - Compliance).
IaC Security: Container/Kubernetes security, Secrets Scanning
Runtime Security: Cloud detection and response (CDR)
Application Runtime Security (ARS)
ASPM: Application Security Posture Management
RASP: Runtime application self-protection
API: Application Programming Interface Security
WAF: Web Application Firewall
SaaS Security
SSPM: SaaS security posture management
CASB: Cloud access security broker
Cloud Vulnerability Management (VM)
Vulnerability scanners and assessment solutions.
Today’s Partner: Probely Security
(Partners like probely allow me to make this report free.) Probely is a web application and API vulnerability scanning solution designed for agile teams. Probely is able to provide a comprehensive analysis of modern web applications and APIs, and detect vulnerabilities in real-time. Probley offers proactive support, leveraging visibility into the scanning process to notify users of potential issues during scans. Their solution effectively scans modern web applications and APIs, especially those with intricate architectures and extensive use of JavaScript. Visit probely security.com
Diving Deeper Into The Major Categories:
These are three major categories that I will use to discuss security for cloud-native applications. Everything begins from the control plane (which is the brain of the system) and then flows through the data plane. Security teams need to ensure they do their jobs correctly on the App Security development components (SAST, DAST, SCA, API Scans, and IaC Scan) before deployment.
Cloud Infrastructure Security (CNAPP, CWPP, CSPM)
Code Scanner & Application Security Solutions (SCA, SAST, DAST, IaC, Secrets)
Runtime Protection Security (VM, Application Runtime Security, SaaS Security)
I’ll explain each of these categories but begin with the cloud workloads.
1) Cloud Infrastructure Security
The history of cloud security dates to the early 2010s with the rise of hyperscalers. Initially, cloud adoption was viewed with skepticism due to security concerns. However, advancements in encryption and the ability to secure data and detect vulnerabilities in workloads allayed these fears. The establishment of standards and frameworks, such as the Cloud Security Alliance (CSA) guidelines and ISO/IEC 27017, reinforced best practices.
Although progress has been made in securing the cloud good things have evolved, the unfortunate part is the rise of cloud breaches have occurred over the years. Most of these happen due to cloud misconfigurations, poorly configured cloud buckets, poor security practices, weak cloud security posture, and more. AWS developed the shared responsibility model to distinguish between the cloud provider and the customer. It entails that AWS’ responsibility is the ‘security of the cloud’ and its infrastructure. The cloud provider is responsible for protecting the infrastructure (hardware, networking and facilities) that runs all cloud services.
Meanwhile, the customer has a responsibility to secure ‘what is in the cloud’—this includes securing the operating system, the application, data, and runtime. Depending on the cloud service and consumption model being used, security responsibility is shared. This shared responsibility has led to the creation of cloud security providers, including key vendors like Wiz, Datadog, and Palo Alto Networks Prisma Cloud.
Using the industry standard from Gartner on Cloud Native Application Protection Platform (CNAPP), Cloud security can be categorized into the following key areas:
CWPP (Cloud Workload Protection Platforms (CWPP): These are technologies that utilize agents to provide consistent visibility into and control over physical machines, virtual machines, containers, and serverless deployments within cloud environments.
Cloud Security Posture Management (CSPM): These are technologies for protecting and enforcing policies, standards, and compliance on the cloud. Important to note that CSPM tools are designed to identify misconfiguration issues or gaps in security policy enforcement by comparing cloud environments
against a predefined set of best practices or security policies by a component.
Sub-Categories of Cloud Infrastructure Security:
CWPP and CSPM are two technologies that are the cornerstones of effective cloud security solutions. There are a number of other categories that play a critical role in providing comprehensive breadth to security of cloud workloads:
Cloud Infrastructure Entitlements Management (CIEM)
These are technologies for helping companies manage identities, permissions, and access control in the cloud. It ensures companies have clear visibility to privileged cloud admin and their access to sensitive data.
Container Security & IaC Scanning
Containers, referred to as a "cloud within a cloud", have become pivotal for streamlining application development. Platforms like Docker offer all the necessary elements for developers to deploy portable and self-contained applications, yet they present certain risks. Container environments necessitate a comprehensive cybersecurity strategy. This includes securing images, containers, hosts, runtimes, registries, and orchestration platforms. The complexity of container security is exacerbated by the high volume of containers organizations manage and the regular updates they undergo. Container security involves protecting the container, its system libraries, runtime, and orchestrators from cyber threats. Methods such as container image scanning have become popular for identifying vulnerabilities.
Additionally, security solutions exist that scan Infrastructure as Code (IaC) templates like Terraform for vulnerabilities and misconfigurations. Kubernetes, the leading open-source container orchestration platform, has an increasing array of security tools built around it. It's worth noting that container security spans the entire application development and deployment lifecycle. IaC scanning plays a pivotal role in security: if a scanner identifies a security flaw in an IaC pipeline like AWS CloudFormation, Azure Resource Manager, or Terraform, it can halt the deployment process, prompting DevOps to rectify the IaC misconfiguration.
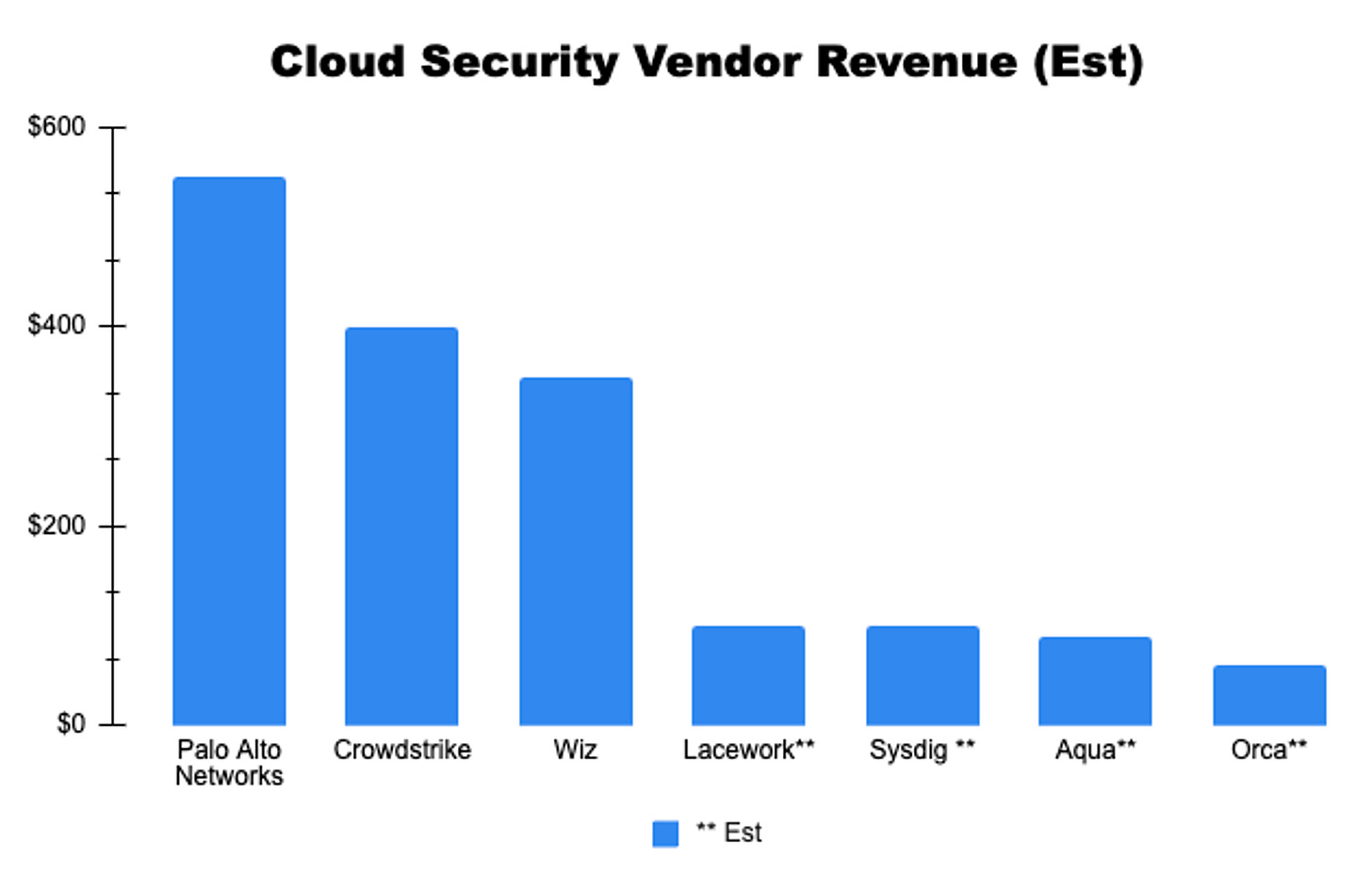
The Major Cloud Security Vendors
Source: Author’s & Wall Street Estimates
Wiz Security
Wiz offers a holistic security solution tailored for cloud environments, leveraging an agentless scanning that utilizes APIs and log data to map out intricate relationships within cloud workloads. This includes everything from visibility into VM/containers, secrets to vulnerability assessment across multi-cloud workloads. At the heart of Wiz's technology is an advanced graph database, enhancing the platform's capability to monitor a diverse array of cloud events comprehensively.
Wiz also simplifies compliance management with its intuitive CSPM templates and the user interface into visibility across cloud workloads. The agentless approach that utilizes API logs to the CSPs allow Wiz’ solution to be very quickly deployed within an enterprise. Their solution shortens the time to investigate and remediate incidents and companies can see ROI fairly quickly. Beyond quick deployment, Wiz’s core focus on enterprises early on in their story and nailing down the GTM (including leverage CSP sales rep and channel partner) was another key to their success.
While Wiz excels in many aspects of cloud security, it has not focused intensively on code security and open-source vulnerabilities, nor has it made significant inroads into Application Security Posture Management (ASPM). According to Forrester’s cloud security report, areas such as administrative user Identity and Access Management (IAM) and reporting/auditing functionalities are yet to meet industry standards. Wiz has heavily relied on partnerships to ensure they provide the full spectrum of cloud security solutions and to fill in some gaps in some newer areas they plan on moving too. For example, we know Wiz will want to move into ASPM and be become better on code scanning capabilities. Wiz’s recent partnerships with Cycode and Splunk, both hint toward Wiz desire at become ingest data from multiple software assets (including CI/CD) and remediating cloud incidents. I wouldn’t also be surprised if they made an ASPM or AI security acquisition over the next few months.
CrowdStrike
Crowdstrike has extended its endpoint security capabilities to the cloud, using its agent technology for security scanning across cloud servers and infrastructure workloads.
Crowdstrike has developed a strong cloud workload protection (CWPP) product as a result of their strong agent used for detecting malware on windows operating systems. Research sources like Forester credits Crowdstrike for their strong agentless container runtime protection, IaC scanning capabilities and real-time event-based asset discovery. CrowdStrike's successful expansion into cloud security has been supported by upselling on their large Endpoint Detection and Response (EDR) customer base and their sales channel with AWS marketplace.
Their acquisitions of Bionic and Flow Security aim to enhance CrowdStrike's offerings in Application Security Posture Management (ASPM) and cloud data security, respectively. However, CrowdStrike's agentless Cloud Security Posture Management (CSPM) and Cloud Infrastructure Entitlement Management (CIEM) offerings are not as robust as some of the more established vendors in the space.
Palo Alto Networks
Prisma Cloud, part of Palo Alto Networks, is the largest player by revenue in the cloud security market, offering a wide array of cloud and code security solutions. Its product suite covers a broad spectrum but shows variation in the development stage across different components, particularly in code security areas.
The company expanded its portfolio through acquisitions, starting with CSPM technology via RedLock in 2018, and adding container and serverless application security with Twistlock and PureSec in 2019. In 2021, Prisma Cloud incorporated IaC scanning capabilities by acquiring Bridgecrew. These acquisitions have enabled Palo Alto Networks to provide CSPM and CWPP services, alongside features for container and IaC code scanning, Kubernetes Security Posture Management (KSPM), web application and API security, and some aspects of Cloud Infrastructure Entitlement Management (CIEM), positioning itself as a provider of CNAPP solutions. The planned acquisition of Cider Security in November 2022 aims to integrate application security orchestration and automation across the software development lifecycle.
Prisma Cloud has utilized agent technology from its endpoint products to enhance its cloud detection and response capabilities. Forrester recognizes its administrative IAM capabilities. The company has also utilized its customer base from network and security operations products to promote its cloud security solutions.
Despite these efforts, industry analysts, including Forrester, note that Prisma Cloud's CIEM, workload protection, and operational implementation capabilities need further development to meet market standards. Early cloud acquisitions have not been fully integrated, requiring customers to manually combine these solutions for full functionality. Unlike competitors such as CrowdStrike, Prisma Cloud has not consolidated its cloud security services under a single agent framework and has areas to improve in addressing open-source and compliance issues.
2) Software Supply Chain (SSCS) / Software Composition Analysis (SCA)
The software supply chain (SSC) is one of the fastest and most rapidly evolving categories in software security. I will be writing more about this category over the next few weeks and showing how vendors are differentiating themselves. The space has evolved in response to the need to secure open-source technologies, enable companies to comply with new regulatory requirements, and, frankly, enable visibility across all software components used in building applications. Today, over 90% of codebases use open-source software. Between 85% and 97% of enterprises also utilize open-source software. However, attackers have discovered ways to infiltrate open-source software and cause harm to organizations.
According to Sonatype research, they said that software supply chain attacks doubled in a year, and have tripled since 2019. There are over 245,000 malicious packages on the internet that people continue to download without awareness of the risks. Modern software development heavily relies on numerous open-source components, forming complex dependency trees. This complexity makes it harder to identify and manage vulnerabilities within all dependencies. Hence, the objective of Software Supply Chain Security (SSCS) and Software Composition Analysis (SCA) category is to ensure that before developers begin coding using these open source tools, they need to be able to verify the integrity of the software supply chain. This process includes examining third-party libraries and open-source components that will be integrated into your application.
Many open-source projects rely on volunteers and have limited resources for robust security audits and maintenance. This can leave them vulnerable to undiscovered vulnerabilities. However, one of the major objectives of this category is to use technologies like SCA and SSC to detect potential known or unknown vulnerabilities in open-source software. Key vendors include Snyk, Veracode, WhiteSource, Sonatype, Chainguard, Cloudsmith, Stackhawk, and others. See the initial parts of my report on the software supply chain here and here. Keep an eye out for more writing within this category.
3) Application Security Testing (AST)
Application Security Testing (AST) has evolved significantly from its early days, when the focus was mainly on manual code reviews and basic security testing techniques. With the rise of the internet and web applications in the late 1990s and early 2000s, there was a growing awareness of the need for more sophisticated security measures. This led to the development of automated tools for identifying vulnerabilities, such as SQL injection and cross-site scripting (XSS), which were prevalent in web applications. Over time, AST has expanded to include a variety of testing methods, to address the increasingly complex and dynamic nature of software development, particularly with the adoption of agile and DevOps practices. The three major categories of AST include:
Static Application Security Testing (SAST): They inspect and scan source code to find coding errors, lack of compliance with organizational standards, and validation issues. SAST tools generally provide a report on their findings to developers to fix any known issues before committing code to the next stage of development.
Interactive Application Security Testing (IAST): These are testing solutions that combine some elements of SAST (scanning source code) and DAST (scanning applications when deployed) to find vulnerabilities in applications. IAST can provide analytical results of issues in real time for developers.
Dynamic Application Security Testing (DAST): They are testing tools used when applications are deployed. DAST inspects an application in runtime to understand how it responds to security vulnerabilities. They can identify how the software will respond to unexpected user actions or potential hackers.
Today, AST is an integral part of the software development lifecycle (SDLC), aiming to identify and fix security vulnerabilities early in the development process to protect applications from potential attacks. AST solutions scan an application for vulnerabilities before, during and after the software development stage. They are used to discover and remediate known vulnerabilities within code. It’s important to note that there are other forms of security testing used by developers, including Fuzz testing (automated tests to discover coding errors) and penetration testing (simulates attacks to find vulnerabilities in the application software), but the three highlighted here are the major ones used across the sector.
More On Dynamic Application Security Testing (DAST)
Today’s applications run in increasingly complex environments (public cloud, hybrid/multi-cloud, containers, etc.) and are more architecturally complex and integrated (APIs, external dependencies, microservices, etc.). This complexity can introduce unforeseen challenges when applications are deployed in production environments.
Dynamic Application Security Testing (DAST) or web application scanning solutions are security testing solutions that tests a web application in its running state without knowledge of its underlying code or architecture. This approach seeks to find vulnerabilities that can be exploited in a real-world attack scenario, focusing on issues like input validation problems, session management vulnerabilities, and other runtime issues.
While other solutions like SAST scan the underlying code pre-production for potential vulnerabilities, they cannot detect vulnerabilities that surface when the various components of the deployment are put together. DAST solutions are able to detect vulnerabilities by simulating automated “real world” external attacks and test cases on complied code ready for release. Typical tested vulnerabilities include cross-site scripting, SQL injection, and path traversal. DAST tools also assess vulnerabilities in server or infrastructure configuration and authentication.
DAST Adoption and Web Application Scanners:
Web App scanners simulate potential real-world attacks on applications, often revealing how an attacker might exploit vulnerabilities in runtime. These scanners can be applied at scale and run continuously without needing access to an application's source code.
DAST tools can provide immediate feedback, making them useful for detecting and addressing vulnerabilities in rapidly changing environments. They also tend to have a lower rate of false positives compared to many other AppSec products. However, a notable drawback is their inability to provide developers with a complete remediation path if there's a problem with the source code. Since they lack some of the SAST capabilities, they might miss vulnerabilities that do not surface during the testing phase.
DAST solutions require upgrades and manual inputs to write and manage test conditions, considering various test approaches like development/runtime, open-source/proprietary code, etc. As a result, they can impact performance. Running DAST tools against a live application could disrupt users or services. Furthermore, DAST typically occurs later in the software development lifecycle, which means vulnerabilities are detected later, potentially increasing the cost and complexity of remediation.
DAST Vendor Review:
Probely is a web application and API vulnerability scanning solution. Probely effectively scans modern web applications and APIs, especially those with intricate architectures and extensive use of JavaScript. A key feature of Probely’s solution is its ability to provide detailed explanations of vulnerabilities once identified. It not only explains the impact but also offers remediation guidance. These comprehensive descriptions aim to educate developers on secure coding practices, adding value beyond simple vulnerability detection. Moreover, Probely maintains a low false positive rate, reducing the burden on security and development teams especially when compared to competitors where false positives are more common, as noted for Acunetix, Intruder, and Veracode.
Probely scans a web application in its running state to identify potential real-world attack vulnerabilities. The seamless integration of Probley with CI/CD pipelines and issue trackers like JIRA is designed to fit smoothly into development workflows, making it easier for teams to incorporate security scanning into their regular processes. This level of integration is particularly important for maintaining agility in DevOps environments. Uniquely, it supports complex authentication mechanisms, ensuring thorough scanning of authenticated areas of applications and APIs. Seamlessly integrating with CI/CD pipelines and issue trackers like JIRA, it easily fits into existing development workflows, facilitating the incorporation of security scanning into regular processes.
4) Application Runtime Security (ARS)
Once applications have been created, the next part is ensuring that these applications are secured during post-deployment. This involves real-time monitoring of an applications’ health and infrastructure once live. There are many components that make up a huge part of any security team’s application security infrastructure (especially in a cloud-native environment), but we’ll focus on just three of them here:
Web Application Firewall (WAF): They are web firewalls that sit between an application and its underlying infrastructure (servers) to monitor online threats and web traffic for applications. WAFs offer advantages like protection from a wide range of threats, flexibility in policy implementation, integration with other security tools, real-time monitoring, and data leakage prevention.
API Security: They primarily protects APIs but scans for risks and vulnerabilities during the software development stage against API threats when applications are deployed.
Runtime application self-protection (RASP): They monitor an applications’ internal state and behavior in runtime. RASP are capable of addressing threats by observing anomalous activity, including novel or “zero-day” attacks.
Its important to note that WAF and API are some of the most critical security tools used in the production phase of a cloud environment. In general, RASP technology tools enhance AST tools by monitoring the internal state of application execution, detecting vulnerabilities, and preventing attacks in real time. They preserve the application's design, address a wide range of threats and have a high accuracy due to its insight into application logic and configuration.
Observability and Application Performance Monitoring (APM): I’ll note that observability technologies and application performance monitoring platforms are installed for application monitoring, tracing, diagnostics, and performance. This domain can be complementary rather than a full cybersecurity solution.
5) SaaS Security
SaaS Security encompasses strategies and tools designed to protect user information, data and applications delivered as a service over the internet. SSPM offers visibility and control over the security settings and compliance status of SaaS applications. CASB, on the other hand, acts as a policy enforcement point between cloud service users and providers, offering deep visibility, compliance, data security, and threat protection for SaaS applications. Together, these elements form a comprehensive approach to securing SaaS environments.
Components of SaaS Security
SaaS security posture management (SSPM)
Cloud access security broker (CASB)
SaaS Security Posture Management (SSPM)
With the rise of SaaS applications within the enterprise due to the rise of the cloud, organizations are struggling to enforce strong security protocols around their apps. With 65% of sensitive or confidential data in the cloud being stored in SaaS applications, the need to secure this data becomes paramount, especially in industries subject to stringent regulatory requirements. To secure data stored in SaaS solutions, organizations need visibility into who can access their data in the SaaS solution, as well as who can make policy changes to provide access to data.
SSPM tools provide visibility and control over the security settings and compliance status of SaaS applications. They automate the identification of misconfigurations and inconsistencies in security policies across SaaS applications. SSPM solutions like ZScaler, Obsidian security provide continuous monitoring of SaaS applications to detect security misconfigurations and to automate compliance assessments against industry standards and regulations. These solutions are also good at identifying anomaly detection to identify unusual access patterns or data sharing practices that may indicate a security threat.
Some of the core components of SSPM include:
Application-Level Controls: SaaS security solutions provide fine-grained controls at the application level, including user access controls, data encryption, and activity monitoring specific to the SaaS application.
Identity and Access Management (IAM): Integration with IAM solutions that can provide both visibility into users’ access to data. These IAM solutions must be able to manage authentication and authorization for SaaS applications, ensuring only authorized users can access sensitive data.
Data Security: Emphasizes protecting data within the SaaS environment through encryption, data loss prevention (DLP), and classification schemes. Data encryption tools, usually native to SaaS apps themselves, encode data at rest (in storage) and in motion (moving to or from an endpoint or service) to protect it against unauthorized access.
Compliance Management: They help ensure that SaaS applications comply with relevant regulations and standards by enforcing policies and monitoring compliance posture using SaaS application configuration templates.
Cloud Access Security Broker (CASB)
CASB is a security policy enforcement point or an intermediary situated between enterprise users and cloud service providers ie once data leaves an organization’s environment. It acts as a gatekeeper providing deep visibility, compliance, data security, and threat protection into user activity on SaaS applications.
Its primary role is to enforce security policies and access controls across multiple cloud services, including SaaS, Platform as a Service (PaaS), and Infrastructure as a Service (IaaS). CASBs provide a centralized platform to gain visibility into all cloud services used within an organization. They enable the enforcement of consistent security policies across various cloud services, including access controls, threat prevention, and data security policies.
Types of CASB solutions:
Inline or Proxy-based CASB: The inline CASBs sit directly in the network path between users and cloud services inspecting traffic in real time, enforcing security policies before allowing or blocking access. They both operate in the data flow, providing visibility and control at the point of access .
Out-of-Line or API-based/Hybrid CASB: These providers interact directly with the cloud service APIs (not on the network path) to secure access data at the application level. They focus on data protection, encryption and access controls.
The difference between SaaS Security and CASB: It’s important to discusses this small but important difference. SaaS Security is specifically focused on individual SaaS applications. In contrast, CASBs provide a broader security perspective across multiple cloud services and platforms, including but not limited to SaaS. CASBs excel in providing visibility into cloud usage and risks across the organization, which is crucial for managing shadow IT and ensuring compliance. SaaS Security, however, is more focused on the granular monitoring and protection of data within specific SaaS applications.
6) Vulnerability Management (VM)
Vulnerability Management (VM) is primarily concerned with identifying, assessing, prioritizing and mitigating vulnerabilities within cloud environments without the need for deploying agents on each cloud resource. VM has been an industry primarily associated with on-prem environments. However, as more workloads have moved to the cloud, VM is always concerned with maintaining a secure posture within cloud environments, which cuts across IaaS, PaaS, and SaaS.
VMs scan servers, devices, and applications to discover vulnerabilities. VM technologies detect risky APIs, unencrypted data, misconfigurations, shadow IT, and providing broad visibility across your environments. VM is an integral and often mandatory part of most organization’s security posture.
There are two key components of VMs:
Vulnerability Scanners and Assessment: VM Scanning involves using agents, virtual machines, or APIs to conduct thorough scans of an enterprise's technology stack. The scans aim to detect misconfigurations, outdated software, and known vulnerabilities across both cloud infrastructure and applications. They perform tests on systems and networks to identify common weaknesses or flaws. Once vulnerabilities are identified, they need to be assessed to determine their nature, severity, and potential impact on the cloud environment. This assessment may involve comparing the vulnerabilities against known databases like the Common Vulnerabilities and Exposures (CVE) database, as well as utilizing risk assessment methodologies to prioritize them based on factors such as exploitability, impact, and the value of the affected asset.
Vulnerability prioritization technology (VPT): The VPT component ensures that all vulnerabilities discovered are prioritized based on severity, the sensitivity of the affected systems, and the potential impact of an exploit. VPT tools use data from various security testing technologies (such as VA, DAST, and SAST tools), web application testing, penetration testing, and network and endpoint security controls to identify and prioritize vulnerabilities. VPT solutions provide a centralized dashboard view for organizations that use standalone VA tools.
There are also other parts of VMs that allow companies to perform Breach and attack simulation (BAS) to stress test their environments with commonplace attack methods to identify weaknesses in their security defences. The VM market is dominated by Rapid7, Tenable, and Qualys which offer most of the features discussed above. However, cloud-native companies such as Crowdstrike and Wiz have VM as an additional module for their customers.
Emerging Trends & Categories To Watch
Cloud detection and response (CDR)
Cloud detection and response (CDR) is one of the latest new trend that has evolved over the last 3-years. CDR is all about identifying threats and mitigating security incidents in cloud environments through autoremediation or manual actions to mitigate their impact. It is generally not considered part of CNAPP, neither does it fit into your traditional XDR (Extended Detection and Response). However, its an extension of your typical CWPP platforms.
Alerts are a major challenge for security teams especially with their cloud security solutions. The high rates of false positives is still huge with SOC teams spending an average of 32% of their time on false incident investigations and validations. Using a CDR reduces how much time analyst need to spend investigating a report as its able to assess severity of every risk. One of the core differences compared to other D&R (Detection and response categories) in security is that CDR is primarily able to formulate optimal threat responses when it detects a threat on a cloud workload or multi-cloud environment.
There are three components to CDR’s. First, the higher fidelity ability to identify cloud risks. They offer vast visibility across the cloud, ingests and analyzes data from APIs, IAM tools, and cloud services to detect potential risks. They can also simulate and identify potential attack paths that threatens a company’s critical assets. Secondly, a core component to them is their ability to detect real-time risks and suspicious activities. Once a cloud risk has been identified, they assist with auto remediation or prioritize the most critical alerts to security teams. Another core part of their capabilities beyond reduced alerts, is their ability to provide lots of context and data to assist security teams in investing cloud events or forensics. They also have good remediation could include revoking access to a cloud resource or data, encryption, or restricting certain APIs.
Wiz has made a key move with their intended plan to acquire Gem security, a CDR player. Gem security is also an agentless security provider with good alerting and incident response. Their solution is heavily used by security operations team who might not good understanding of how the cloud environment works. The challenge here is truly understanding how unique these solutions are from CWPP. All the CSPs all provide CDR as a feature. For example, AWS GuardDuty focuses on this category, Microsoft Azure Security Center, or Google Cloud Security Command Center. There are also some emerging companies like Dazz security and DevOcean.
Cloud Runtime Security Companies
The cloud security market has progressed from basic Cloud Security Posture Management (CSPM) tools, aimed at identifying misconfigurations, to comprehensive CNAPP solutions. These solutions offer a unified approach to securing cloud-native applications by integrating security and compliance across development and production environments.
Initially, companies prioritized visibility into cloud configurations over runtime protection. However, the realization that configuration scanning often comes too late and is filled with false positives or minor vulnerabilities that are costly to fix has shifted the focus towards runtime protection. Runtime tools offer significant advantages by providing visibility into the actual compute layer, allowing security teams to detect and respond to real-time threats effectively. This focus on runtime security is seen as a better return on investment compared to traditional configuration scanning. Its crucial for detecting and mitigating threats that only manifest during application execution. Runtime tools are better suited to the dynamic and complex nature of cloud-native environments, especially those utilizing containers and Kubernetes, by offering precise and actionable insights into live application behavior. James Berthoty has a great article on this topic on his Sysdig blog post. Some examples of new companies emerging in this category include Upwind, ClearVector, Sweet, and Uptycs. For example, it is said that Upwind leverages previously unavailable runtime data to infuse security programs with runtime context, and delivers this capability in a wholistic CNAPP platform that leads to 10x fewer alerts and 10x faster risk identification and remediation.
Renaissance in API Security, DAST & Web Application Scanners
Historically, Software Composition Analysis (SCA) and Static Application Security Testing (SAST) tools have been closely aligned with developers due to their role in the early stages of the software development lifecycle. However, we’re now observing a closer integration between developers and Dynamic Application Security Testing (DAST) solutions. In organizations that implement full security protocols, it's common to combine DAST tools with SCA and SAST. DAST also complements Runtime Application Self-Protection (RASP) as a runtime tool. DAST is ideal for evaluating vulnerabilities pre-production, while RASP offers continuous vulnerability monitoring and remediation post-deployment.
With the advent of Microservices Architecture, with composable apps, and particularly after the emergence of the API Economy, DAST platforms have had to evolve to include better API vulnerability scanning capabilities. Most platforms still do not offer comprehensive coverage of OWASP's Top 10 API security risks, but those that strive to will change the landscape of the industry. All security risks related to logic and identifying its potential implications in exposing APIs to malicious actors are somewhat uncharted territory, and something that probably can only be achieved through the use of advanced heuristics or with the aid of Large Language Models (LLMs). Platforms that are able to harness the power of LLMs to assist in the identification of vulnerabilities will be differentiated due to the fact they'll actually be able to deliver on the promise of comprehensive API coverage.
But then, keeping track of the sprawl of APIs in an organization's portfolio is another one of the biggest challenges ahead, especially for larger companies, with development teams that may serve several lines of business and that may be scattered throughout the world. Platforms at the forefront of DAST have started incorporating External Attack Surface Management capabilities in order to help orgs cope with the sprawl, whether it's generated by dev teams or by citizen developers alike. Raising the inventories of the exposed surface, of those APIs and web apps, is just the first step, though.
Because the creation of new APIs and web apps occurs every single day, the process of finding them needs to be continuous. Due to their very nature, APIs have always been primed for being scanned as part of the SDLC, with the security testing of their running state being part of delivery pipelines. This process enables organizations to scale without impact from security testing, which is ever more important to help maintain the cadence of delivery that the business requires nowadays. Over time, we expect the application security vendors to expand their AST offerings further and add RASP for a more comprehensive toolset. Notable DAST vendors include Checkmarx, and emerging companies like Probely are playing a key role here including, Contrast Security, Detectify, Micro Focus, Qualys, Rapid7, Synopsys, StackHawk, Tenable, WhiteHat, and Veracode.
Application Security Posture Management (ASPM)
ASPM is envisioned as an all-encompassing platform that can handle all aspects of application security from application security testing (AST), scanning tools and all application logic to cloud. James from LatioTech has a great phrasing around it which emphasizes
A comprehensive ASPM solution should cover the entirety of an application's journey from code to cloud. Importantly, it should offer clear remediation guidance, integrate with other tools for enriched context, and prioritize fixes that address vulnerabilities effectively.
ASPM aim to manage application risk comprehensively by collecting, analyzing, and prioritizing security issues across the software lifecycle. The shift from Application Security Orchestration and Correlation (ASOC) ie. the coordinating of disparate tools to ASPM reflects a response to the sprawling complexity of using multiple, discrete security tools. Although, many companies would claim to be ASPM providers, the ASPM market is still evolving, with various vendors offering pieces of the ASPM puzzle.
AI Security Posture Management (AI-SPM)
This is an evolving category introduced by Wiz that is a solution aimed at securing AI and LLM infrastructure. Over 62% of organizations currently use at least one AI cloud service, with 67% planning to increase their investment in AI and data technologies. It offers full-stack visibility into AI pipelines, identifying and rectifying misconfigurations and safeguarding sensitive training data. It encompasses discovering risks across AI pipelines, enforcing secure configuration baselines, and analyzing potential attack paths. Additionally, AI-SPM provides an AI Bill of Materials (AI-BOM) for deeper insight into AI services and technologies. By integrating data security measures and empowering developers with a dedicated security dashboard, AI-SPM ensures AI deployments are secure, compliant, and resilient against threats. Interestingly, they are extending their Data Security Posture Management (DSPM) and attack path analysis to AI/LLM applications, ensuring the protection of sensitive AI training data.
There is an evolving trend leveraging AI-based agents that autonomously act as Product Security Engineers, auto-remediations autonomously and gain context from your source repos, allowing them to prioritize, select, and fix vulnerabilities on their own.
Concluding Words:
It's crucial to understand that we are still in the initial phases of actual CNAPP development and adoption among many vendors. No single vendor can currently provide a complete CNAPP solution that is truly capable of finding vulnerabilities from code inspection to runtime security. The process will be gradual, with tools like CSPM, CIEM, and CWPP gradually integrating with native ARS, RASP, and VM players to consolidate into a single runtime platform. ASPM will fully mature and incorporate all aspects of AST solutions and IaC scanning. This will eventually evolve into a comprehensive CNAPP that covers development to runtime security in a single major platform.
The ultimate battle will come down to who can become the centrepiece within the core control and data plane for modern software infrastructure. This mean the company that can natively integrate and provide all the core components of code scanning/application security testing tools, cloud configuration and runtime protection will become the ultimately winning platform for this industry.