An In-Depth Overview: The Future of Cloud-Native Identity Security
Exploring The Path ahead for cloud-native Identity security, major trends and Predictions.
Welcome to all the software analyst readers!
This is a comprehensive research report that delves into the Identity security ecosystem, one of the largest and most foundational cybersecurity markets. It is an intensive report (so please open it on your browser). The first section provides a summary of the report, and the latter half goes into depth. I hope you enjoy it!
About the Authors
Francis Odum, Founder and CEO, Software Analyst Cybersecurity Research. I explore in-depth emerging trends reshaping the Cybersecurity industry [Acknowledgements to P0 security, an RSA sandbox finalist and Veza for supporting this research]
Alex Krongold, SentinelOne / S Ventures, Manager, Corporate Development & Ventures, investing in the next generation of category-defining security, data, and AI companies
Daniel Bartus, Felicis, Partner / Head of Research, investing in early-stage companies reinventing core markets and creating frontier ones in security, AI, defense, infrastructure, health, and more
Intro & Key Takeaways
This comprehensive primer on Identity Security aims to provide both an introduction and a deeper analysis of the identity market, including its history, current landscape, and challenges faced by the industry. Our goal is to provide a thorough understanding of the identity ecosystem, mainly workforce identity. We'll also explore the evolution of the identity TAM, market segmentation, and strategic market activity. This report is the result of extensive research and discussions with industry leaders and experts.
Why identity security and why now? First, we recognized that identity security is an increasingly critical area of focus for organizations of all sizes, given its central role in protecting systems and data - one could argue it is the perimeter of most importance. Second, there is a trend of consolidation among legacy solutions paired with existing technologies becoming commoditized - signs that the market is ripe for disruption.
Now that the authentication problem has been mostly solved, what comes next? We expect a pivot to focus on expanding functionality in Identity Governance & Administration (IGA) and Privilege Access Management (PAM), characterized by Zero Trust principles, fine-grained access management, and improved cross-environment visibility.
Identity is one of the most common attack vectors, and the challenges facing the sector now with the growth of GenAI are vast, especially in a world where more systems interact with each other autonomously, with increasingly less human involvement than before.
There has been a lot of strategic market activity across the identity market that signals its importance and prominence over the next few years. We provide a breakdown on the key M&As & financings below.
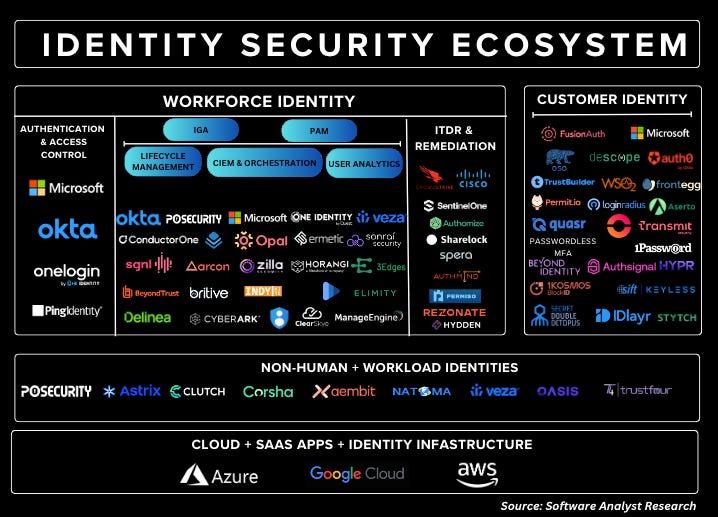
The Identity Security Market Ecosystem
The Identity Security Ecosystem is highly fragmented, with many vendors. There are over 200+ vendors. For a full list, please visit platforms like Cypher to see a full vendor list. Based on our extensive research, this is how we decided to segment the market into the following major categories:
Identity Security Market Activity
Mergers & acquisitions
From the selected data provided below, recent acquisitions in identity have been dominated by financial sponsors and their platform companies (10 of 18) - a move to consolidate different parts of the identity stack and a signal that the category is aging and ripe for disruption. According to the Cybersecurity Year in Review for 2023 published by Altitude Cyber, IAM was the top sector by deal volume in 2022 at $12.7B across 37 deals (#2 by deal count), then plummeted to the last position in 2023 with only $675M across 29 deals (#4 by deal count). Granted, 2022 was an anomaly with Thoma Bravo scooping up $12B+ worth of identity assets with SailPoint, Ping Identity, and ForgeRock.
For Q1-24, IAM reclaimed its top spot (alongside SecOps/IR/TI) as the most active by deal count (7 transactions) if we exclude the non-software Security Consulting category.
ITDR stands out as a recent important area for established vendors to acquire given it requires both posture management and response capabilities, both difficult to build. We suspect this activity will create more opportunities for startups to innovate.
Select Identity Acquisitions
Financings
Referencing the same annual cyber report from above, identity-related fundraising activity remains strong, with $2.9B invested across 128 deals and $1.1B across 78 deals during 2022 and 2023, respectively. We expect to continue to see more dollars poured into the IAM category as there is a large opportunity to displace legacy incumbents.
Q1-24 financings came in at 18 deals, fourth to Risk & Compliance (38), Data Security (32), and SecOps/IR/TI (25)
Select identity financings
Components of a Next-gen Identity Platform
It’s no secret that the broader cybersecurity market is fragmented, with many point solutions, each addressing a part of the problem. As an output of this report, we thought it was important to outline what a holistic, forward-looking view of an identity platform should look like - we call it a cloud-native identity management platform.
Overview of the Identity Ecosystem
Introduction
It’s difficult to understand the evolution of identity security without remembering how things used to get done. To orient the discussion, let’s think back to how people used to work in the age of computers and the internet. Typically, new employees were using stationary, desktop computers that were already connected to a private network that was physically located at the work site and which had the necessary software programs pre-installed. There really wasn’t a need for the concept of an identity - basically, if you could gain access to the building, get on a computer that was your identity security (and maybe a username and password). With the advent of more scalable and efficient application delivery methods (delivering and updating software-as-a-service) and software hosting methods (utilize third-party infrastructure-as-a-service), the control perimeter and complexity of managing identities and access exploded.
Now that we are well into the cloud era and beginning the age of GenAI, it’s a good time to take a step back and examine the history of identity security, where the industry is heading, and how startups are thinking about solving some of the industry's biggest pain points.
Definition
At its core, identity and access management (IAM) is about knowing who (or what) is taking what actions on which resources so people and processes can be productive while remaining secure—this is known as Workforce Identity. Workforce identity makes up most of the market today and will be the focus of this report.

Components of Workforce Identity
Access Management (AM) solutions are focused on delivering real-time access control to applications and data through user authentication.
Identity Governance and Administration (IGA) is a set of security solutions responsible for aggregating and managing digital identities, roles and access rights across enterprise systems.
Privileged Access & Management (PAM) is a set of security solutions that protects privileged accounts, often defined as those with extensive access across an enterprise.
Cloud Infrastructure Entitlements Management (CIEM) is a new category that has emerged to manage identity access, cloud entitlements and security risks in cloud environments. It draws upon some of the core components of PAM/IGA to secure IaaS entitlements on the cloud.
Identity Threat and Detection Response (ITDR) is a security procedure for identifying, reducing, and responding to identity-based threats and attacks.
Non-human Identity (NHI) deals with AM for non-human entities such as bots, workloads (including virtual machines and containers), and Internet of Things (IoT) devices, including service accounts.
Identity Security Posture Management (ISPM) is more of a framework used to strengthen and maintain the security posture of an organization’s identity infrastructure to prevent breaches.
Brief Overview of Customer Identity
Although this report primarily focuses on workforce identity, it's important to recognize that another major category of identity exists for organizations looking to create secure and seamless customer experiences within their public customer-facing applications. Customer Identity and Access Management (CIAM) has emerged as a new category focused on organizations that need secure identity solutions for a large number of external-facing users (non-employees, customers, etc.).
Identity Challenges & Industry Pain Points Today
To better understand the identity security industry's current state, the top issues plaguing security practitioners, and its future, we sat down to speak with founders and operators of identity security businesses and security professionals at large enterprises. Below is a summary of our findings.
Visibility is lacking
It's really where all security starts and the only way to make informed critical decisions. Knowing all the identities in a given environment and what they are doing, then associating related identities and actions across all environments is still an issue for most organizations. Between having multiple Active Directories, both cloud and on-premises workloads and databases, hundreds of SaaS applications, GenAI apps, and non-human identities there is still a big need to discover, catalog, visualize, and query all identities. What seems to be missing is an identity fabric, a layer abstracted from point solutions that acts as a command post, a neutral observer of identities that integrates with any and all other relevant systems and tools. We’ve seen a flurry of recent M&A activity from established identity vendors to address this concern: Cisco’s acquisition of Oort, Okta’s acquisition of Spera, and Delinea’s acquisition of Authomize. Some interesting startups working on this issue include Strata, ConductorOne, Veza Rezonate, and AuthMind.
Access management (authorization) is difficult
Once you are authenticated, now what? Answering key questions like who should have access to what resources and data, how long access should persist, and under what circumstances should access be granted are still difficult questions for an organization to answer. Pair it with the need to continuously update and assess these decisions, and this becomes a big headache. As the industry moves to least privileged principals, how do you set up effective workflows and obtain the proper context necessary for seamless access to any resource, continually assess and augment policies, and minimize access exposure without disrupting the business?
Side note, there are two ways of looking at authorization software. One is building authorization natively into an application to allow a company to sell added security features to their customers. Oso and Permit are two good examples. The other way to look at it, is purchasing software that manages only employee access to internal company resources. The latter will be the focus of this section.
To get more specific with the shortcomings, let's dive into a few of the necessary components of managing access. Modeling is the act of collating and organizing data used for authorization decisions - like grouping users into roles to assign access levels (think RBAC, ABAC). Legacy models are static and too rigid to fit the myriad of use cases required by large organizations (e.g., access based on region) and manual. Other issues include a lack of data from other systems for decision-making, management and enforcement needing to occur in multiple places, and non-intuitive policy languages.
We think dynamic, context-aware authorization will need a few key components. Consistent and easy-to-understand interface for policy creation, management, and enforcement, automation to enable on-demand access decisions, integrations that bring all the necessary data to a decision process, the flexibility to enforce access from the broadest to the most granular layers, and AI for intelligent and continual assessment and improvement. This will enable organizations to adopt a zero/least standing privilege approach to access across the organization.
As we’ve seen with several high-profile breaches, authentication is not the end all, in fact, it should be seen as a necessary first line of defense that will be breached. Authorization is the true guardian that can protect and mitigate identity-based attacks. A few companies working on these issues include SGNL, Sonoma, Aserto, Permit, Opal, Oleria, and Oso.
Cloud identity sprawl
The fragmented, cloud-native development process gives every developer access to many environments/resources. What makes things even more complicated are the many more non-human identities (estimated 10-50x the number of human identities) that one could argue have higher privileges and are more difficult to track due to diversity (service accounts, application accounts, workloads, APIs), distribution across environments, and their ephemeral nature. Both access levels and number of identities have increased in the cloud era. Just one identity can hold enough permissions to take down an entire organization, meaning every cloud identity could be categorized as a privileged identity. More and more companies are realizing they need to right-size permissions and are using concepts like just-in-time (JIT) access and activity-based access revocation to lock down critical environments. This is a two-edged sword that could also lead to a loss in productivity.
A balanced approach incorporates limiting non-human identities to only the access required for their specific task, fine-grained policies that trigger access based on full context of the identity and action (e.g., geography, role, business justification, behavior signals, asset criticality), and intelligent, automated lifecycle management (credential rotation, decommissioning, vaulting, provisioning). A few companies like P0 Security, Clutch Security, Permiso, Veza, and Aembit are all startups working to wrangle cloud identities and workloads.
No Data Context
Access can be defined at different levels: network, infrastructure, applications, and data. Most access controls are focused on infrastructure (databases, data lakes, servers, cloud) and applications (Salesforce, Google Workspace) but a lot of times it makes sense to give access to an application while masking or removing access to data that should not be visible to that particular identity. This requires that the data itself have a type of identity, a classification as to whether its sensitive or not (credit cards, personal information, etc.). Data is also one of the key parameters when enabling context-based access. Companies like Veza, SGNL are looking to incorporate data when deciding on access.
Notable Startups Addressing Identity Challenges
Legacy IAM solutions are still broadly used and make up the majority of the install base today (SailPoint, ForgeRock / Ping, Microsoft, CyberArk, IBM, Cisco). We believe identity is beginning a new cycle of modernization that will include better visibility for modern, distributed architectures (access fabric), focus on access management and monitoring privileged accounts, and AI-first solutions that help with right-sizing access, detecting abnormal usage, and recommending policy to lock down environments.
Below are a few companies we are excited about, solving big pain points in identity:
Workforce Identity Security Deep-Dive
Components of Workforce Identity
Authentication: verifying that users are who they claim to be. We can think about it as the decision of who is allowed in the front door of your home. Traditionally, this has been accomplished with a username and password. In recent years authentication has expanded to include biometrics and devices with techniques including fingerprint matching, facial recognition, tokens, and multi-factor authentication.
Authorization: determining what resources an authenticated user can access. After someone is allowed in the front door, what rooms and sections can they access. This is accomplished through maintaining detailed lists and directories of all users and the resources they are authorized to access.
Below, we provide an in-depth breakdown of the authentication market. We further provide a breakdown of some of the major components of the workforce including:
Identity Governance & Administration (IGA)
Privileged Access Management (PAM)
Identity Threat Detection and Response (ITDR)
Non-Human Identity (NHI)
Authentication & Access Management (AM)
AM has been the cornerstone of the identity industry. While access management remains a central element in the IAM market, new tool categories have surfaced to address distinct, complex, and evolving enterprise needs.
Single-Sign-On (SSO) enables users to access all permitted applications through a central directory, using just one set of credentials, and eliminates the need to log in again when switching between applications; SSO relies heavily on Federated Identity Management (SAML, 0Auth, and OpenID). The IdP can either directly authenticate the user or can provide authentication services to third-party service providers (apps, websites, or other digital services). For example, the ability to use Google across other workflows. In recent years, newer types of authentication mechanisms have been created that often grant privileges based on a person's role (RBAC) or on the attributes of the subject, resource, action, and environment involved (ABAC).
Multi-Factor Authentication (MFA): MFA requires users to provide two (and increasingly more) verification factors to gain access to applications, accounts, or even a VPN. An example is after entering the correct username and password, a user will get a text message with a unique number that must be entered before authorization is complete.
Access & Active Directory (AD): Directory stores are a central repository of login credentials, data and privacy consents, and preferences for each user profile, and they enable easy provisioning and management when onboarding new users. Like Okta’s Universal Directory, many directory solutions centralize user management, allowing IT administrators to assemble user profiles with attributes from multiple identity sources, manage lifecycle states, and set consistent user access policies based on different user contexts (location, IP, device).
Leading Authentication & AM Vendors
Microsoft’s Entra Platform
Microsoft's identity platform, "Entra," is the largest identity offering on the market. Microsoft began its journey into identity security with the launch of Azure AD, its cloud-based Active Directory (AD) product. The platform now spans user permissions and authentication, Cloud Infrastructure Entitlement Management (CIEM), and decentralized identity. Microsoft excels in the SMB market, where it packages various security products with solutions like Office365 and OneDrive. This strategy gives Microsoft a broad platform from which to sell security products. With over 865,000 customers and $20 billion in TTM revenue, Microsoft's business is thriving.
Looking ahead, Microsoft remains a threat in the market, in our view, with a unique advantage through its installed base of Active Directory and Azure AD customers. Microsoft continues to focus efforts on improving its security platform and has influence over customers with E5 and E3 licenses, particularly regarding utilizing Microsoft across greater portions of customers’ enterprise infrastructure. Microsoft is expected to remain a formidable competitor, especially for enterprises who are increasingly looking to consolidate vendors.
Microsoft's acquisition of Cloudknox further advanced Microsoft's strategy within CIEM. CIEM is crucial for managing and securing identities in cloud environments by ensuring that permissions are precisely aligned with the actual requirements of users and systems. They emphasize the need for robust management of permissions across various identities (human and non-human), enabling organizations to implement the principle of least privilege effectively. CloudKnox provides visibility, remediation, and monitoring capabilities to help organizations right-size permissions and manage them dynamically based on actual usage.
Okta
Okta holds the second-largest market share in the Access Management (AM) market, trailing only Microsoft. Its solution covers various authentication areas, such as universal directory, Single Sign-On (SSO), Multi-Factor Authentication (MFA), and API access management. Okta is renowned for its extensive integrations and customizations, which address many workforce identity use cases.
In 2021, Okta acquired Auth0 to bolster its presence in the Customer Identity and Access Management (CIAM) market, introducing a developer-led approach. Auth0 is a developer-centric IAM platform that authenticates, authorizes, and secures access to applications, workloads, users, and devices. Although the acquisition of Auth0 hasn't been as successful as anticipated, it has positioned Okta well within the customer market.
Okta recently launched an Identity Governance and Administration (IGA) and Privileged Access Management (PAM) product, further enhancing its lifecycle management and advanced server access solutions. This places the company in a strong position to lead the market consolidation with a fully converged IAM platform. Okta has the potential to become the leading platform, but only time will determine its success.
Identity Governance & Administration (IGA)
Identity Governance and Administration (IGA) is a core pillar of workforce identity. It combines Identity Governance and Identity Administration.
Identity Governance is about visibility, segregation of duties, role management, attestation, analytics and reporting, while
Identity Administration is related to account administration, credentials administration, user and device provisioning and managing entitlements.
IGA involves a set of policies, frameworks, and security solutions designed to manage and secure digital identities and access rights within an organization. IGA systems automate and streamline several critical functions related to digital identities. This market emerged from the convergence of user administration and provisioning (UAP) and identity and access governance (IAG) tools. Here’s a comprehensive breakdown of what IGA entails, its evolution, market perspective, and specific product offerings:
Identity Lifecycle Management
A core component of the IGA market involves managing the creation, maintenance, and retirement of user identities such as provisioning and de-provisioning users. This also involves policy and role management around defining and managing associated access policies. Additional aspects of lifecycle management include:
Entitlement Management: also known as access rights, permissions and privileges, controls what resources and, more importantly, what operations different identities can access - one identity might be able to look at data in a table (read permissions) while others can add, edit, and delete data (edit permissions).
Access Requests, Reviews, Certification: facilitating the process for users to request access to resources and for administrators to certify or approve these requests. All of which is enabled by a process keeps records of access and actions for compliance and security monitoring.
This evolution was spearheaded by industry leaders like SailPoint (focusing on IAG) and IBM (focusing on UAP). The adoption of IGA solutions is more prevalent in mid-sized to large enterprises due to the complex and varied needs of managing numerous departments and disparate systems. These organizations often require robust IAM programs that include dedicated IGA solutions to manage their comprehensive and intricate identity and access structures effectively.
Emerging IGA Vendors
Sailpoint has the largest market share within the IGA market. It was one of the first movers in this category and ushered in most of the innovations within this market category. However, our report is focused on the future of the IGA market and how it's evolving, so we’ve decided to focus on a few emerging vendors and showcase how each of these vendors are shaping the future of IGA. We review:
P0 Security
Veza
ConductorOne
Opal Security
ConductorOne
ConductorOne focuses on cloud-based authorization and access control. They address the challenges presented by cloud environments by prioritizing visibility across a company's cloud environment. Their solutions are designed to manage digital identities, ensuring secure access and handling identity-related tasks across various platforms and infrastructures. They also automate secure access across various applications and infrastructure. Their platform enhances security and compliance by integrating seamlessly with a broad range of technologies and offering extensive visibility into user activities and access rights.
A major differentiator for ConductorOne is their emphasis on seamless integration with a wide range of applications, whether SaaS, on-premises, or infrastructure. They provide extensive integration capabilities that allow organizations to automate access and identity management across diverse systems. Secondly, a core premise of ConductorOne's solution is their emphasis on Just-In-Time Access (JIT) and Zero standing privileges. These methodologies ensure that permissions are granted temporarily and only when needed, reducing the risk of unauthorized access and enhancing security. Overall, we see ConductorOne as one of the emerging companies solving the cloud identity challenge.
Opal Security
Opal security is a next-generation authorization platform focused on workforce identity. They address both human and non-human identities—such as APIs, service accounts, and automated processes that play critical roles. Opal Security's platform focuses on enhancing robust control over who and what can access critical systems and data across enterprise SaaS applications. The company's authorization platform is designed to adapt to the scale of an organization, offering features like ephemeral access management, role-based and attribute-based access control, and comprehensive management of privileged accounts. Organizations looking for next-gen IGA providers specifically to provide granular and context-aware security generally adopt their platform.
Disclaimer: Please note that the spotlight overviews on P0 Security & Veza are paid partnerships with the software analyst research blogs. We provide a full overview of their platforms.
P0 Security (An RSA Sandbox Finalist)
P0 security is a universal cloud-access governance platform that integrates into developer workflows, enhancing cloud security across all identities—human and machine. P0 Security aims to provide solutions that offer both visibility and orchestration, thereby enhancing security without requiring extensive manual effort from security teams. They were selected as one of the top 10 finalists at the RSA sandbox. The core pillars of P0 security's product aligns with most of the complaints we heard from customers researching the identity market.
Visibility and Inventory
P0 Security emphasizes the comprehensive inventory and visibility of all identities within an organization, including both human and non-human identities. Specifically, their product aims to dive deep into cloud environments that are crucial to developers, such as AWS, GCP, Snowflake, and Kubernetes. This initial focus is pivotal because cloud is the complex area of the identity ecosystem with a larger surface area.
Identity Posture Management
In managing secure postures, P0 Security assesses risks associated with each identity and assigns ownership. This is critical for both human and machine identities, where the latter includes service accounts with possibly extensive privileges and unused credentials. They enhance security posture management by ensuring data access is appropriately controlled based on real-time needs and security policies. This visibility is crucial for effective governance and security posture management. P0 ensures that access rights are always current and appropriate to the role and status of the identity.
Cloud Infrastructure Entitlement Management (CIEM) is another aspect that P0 Security integrates into its offerings, aligning with their focus on orchestrating access. By managing the inventory of identities and continually assessing the security posture, P0 Security can ensure that entitlements are correctly aligned with need and risk, preventing over-provisioning of rights which can lead to potential security risks.
Lifecycle Management and Identity Governance for Access
P0 Security encompasses the entire spectrum of access rights management from provisioning to deprovisioning of users. This includes closely managing how access rights evolve as roles change or as individuals transition in and out of the organization. Importantly, P0 Security integrates these into the developer workflow to ensure that security and compliance are maintained without disrupting productivity. An important part of their offering is the ability to use just-in-time and short-lived access controls, for a variety of cloud resources, such as storage buckets, virtual machines and various cloud services.
P0 Security approach deeply integrates with the needs and workflows of modern cloud-first environments, particularly those involving developers. This ensures that their security solutions are both robust and adaptable, capable of scaling with organizational growth and technological advancements.
P0 Security Differentiators
P0’s Focus on Cloud-Native and Developers
P0 Security explicitly targets cloud environments (Infrastructure as a Service (IaaS) and Platform as a Service (PaaS), which is a significant shift from traditional security solutions that may have been more oriented towards on-premises infrastructure. Their emphasis is due to the complex security challenges of managing machine and human identities in dynamic cloud environments. Further, it is due to the larger surface areas presented by IaaS and PaaS, where configurations and management play critical roles in security.
P0 Security primarily targets greenfield opportunities among cloud-native customers. This focus is designed to address the unique challenges of managing machine and human identities in dynamic cloud environments.
Another significant differentiator for P0 is their developer-centric strategy. P0 Security differentiates itself by emphasizing integration with developer-centric tools by speaking the language of developers and integrating with the tools they use, P0 ensures that security becomes a seamless part of the development lifecycle
Next-Gen IGA Competitive Positioning
P0 Security aims to be what can describe as the next-generation SailPoint, enhancing the capabilities of traditional PAM solutions. They focus on governing access to sensitive data and keeping track of where this data resides, which is increasingly important in distributed cloud environments. This approach not only addresses access but also data governance, thereby providing a more holistic security solution.
Veza
Veza is an identity security platform that provides organizations with tools to manage access rights and data security across cloud, SaaS apps, and on-premises systems. They have a comprehensive solution that features over 200 total integrations, a flexible permissions data model, and robust capabilities in managing a broad spectrum of identities—from human users to non-human accounts like service accounts. Veza automates critical aspects of identity management, such as offering detailed access reviews and user provisioning, ensuring granular control and compliance with security policies.
Breadth & Depth of Identities
The first premise of Veza’s platform is visibility, which encompasses a broad range of identities, including human users, non-human accounts like service accounts, and contractors. This comprehensive approach ensures that all possible access points across an organization are secured and managed effectively. The depth of the platform’s capabilities in managing these identities lies in its ability to identify and categorize different types of accounts and enforce appropriate access controls for each. They provide detailed controls for different types of accounts, tailored to their specific roles and access needs.
To enable this visibility, Veza’s platform is unique in how comprehensively it integrates with other systems. Veza offers over 200 integrations, providing a robust framework that allows seamless connectivity across a diverse set of apps (SaaS, on-prem, and custom), data storage, and platforms. This extensive integration capability is critical for organizations looking to maintain a consistent security posture across various applications and services.
Capabilities in Access Reviews and User Provisioning
We noted that Veza has strong capabilities in access reviews and user provisioning, a critical area where tools like Sailpoint have traditionally forced customers into specific workflows. Veza offers more flexibility and granular control over permissions and identity management, allowing organizations to implement security measures that are directly aligned with their specific policies and compliance requirements.
They provide detailed insights into permissions, enabling precise control over what resources a user can access. Veza allows organizations to tailor the access review and provisioning processes to better fit their operational and security needs.
Rapid Time to Value - Veza’s platform allows for much more rapid integration, particularly for organizations looking to expand their Access Review coverage to replace manual processes, which can be purchased and deployed independently of Provisioning. Veza’s modern developer tooling and Open Authorization API (OAA) allow developers to become effective much more rapidly than with legacy IGA products.
Granular Permission Control - Veza's platform allows for very detailed and granular control over permissions. This capability is essential for effective access reviews and user provisioning because it ensures that each user has the appropriate level of access based on their specific role and responsibilities. By offering granular insights into what resources a user can access and what actions they can perform, Veza enables organizations to tailor access rights precisely, enhancing security and operational efficiency. Veza's ability to handle a wide range of identities, including human users, service accounts, and contractors, plays a crucial role in both provisioning and access reviews.
Access Visibility and Intelligence—They use an Access Graph to visualize and manage access rights, which provides an intuitive and comprehensive overview of who has access to what. This visibility is key for conducting thorough and effective access reviews, allowing security teams to easily spot anomalies and make informed decisions about access provisioning.
Effective Permissions - a key part of Veza integrations includes a “translation layer” that expresses the individual system-specific permissions (which can be hard to understand for non-experts) into plain language for business users. Leveraging the common tasks of “create, read, update, and delete,” these Effective Permissions allow a much more informed Access Review process since reviewers can really understand the decisions they are making.
Privileged Access Management (PAM)
Across any organization, certain employees or accounts have ‘privileged’ access to critical systems and admin accounts. These are often developers, engineers, and IT professionals that hold the proverbial “keys to the kingdom”. Privileged Access Management, or PAM, is the sub-category of Identity Security that adds an extra security layer for such users.
Examples of privileged accounts include domain controllers, admin rights for databases or applications, public & private cloud access, desktop & server OS admins, networked devices, and more. Over the years, the market has evolved from being focused on on-premise system administration to cloud ‘secrets’ management. The lines between PAM, IGA, and IAM have also increasingly blurred.
History
About a decade ago, Privileged Access Management (PAM) was a niche category, largely unrecognized with a market size below $1B. CyberArk, the market leader, didn't cross $50 million in revenue until 2013. Despite this, the importance of PAM, especially for larger enterprises, was gradually increasing. When CyberArk went public in 2014, its stock surged 60% on its first trading day, nearly achieving a $1B market cap.
Today, CyberArk is nearing $1B in Annual Recurring Revenue (ARR) for 2024 with a market cap surpassing $10B. The Total Addressable Market (TAM) for core PAM is projected to exceed $4B in 2025. In the span of 10 years, PAM has evolved from a niche category to a crucial component of cybersecurity and identity security strategies.
The adoption of PAM accelerated following numerous breaches that highlighted the significance of privileged accounts. The 2014 Sony Pictures hack serves as a notable example. In this incident, a hacker group known as "Guardians of Peace" accessed and released vast amounts of confidential company data. It was later revealed that the hackers had found a folder labelled "Passwords" containing shared admin account credentials. This event underscored the critical role of privileged accounts, or "keys to the kingdom."
Components of PAM
The core components of a Privileged Access Management (PAM) suite begin with eliminating the concept of a "Password" folder and storing all privileged account information in a secure "vault". Once a company has located all privileged account credentials and stored them in the vault, they can add additional security controls as needed.
In the early years of the PAM market, leading suites like CyberArk included:
Enterprise Password Vault: This protects and manages all privileged accounts.
Privileged Session Manager: This feature adds real-time monitoring and detailed recording of command-line keystrokes, isolating all privileged activity from potential bad actors.
Application Identity Manager: This component focuses on managing privileged credentials that may be embedded in applications, service accounts, and scripts.
On-Demand Privileges Manager: This module allows for more granular controls of admin accounts by restricting certain commands.
Privileged Threat Analytics: This tool detects and alerts administrators to abnormal privileged account behavior.
Identity Threat Detection & Response (ITDR)
As depicted earlier, we view ITDR as further right of the identity stack. The increase in identity-based attacks has created the need to secure not only user identities but also the underlying cloud infrastructure that hold these identities. In recent years, bad actors have found ways either through credential stuffing, leveraging passwords from past breaches to bypass authentication technologies and cause harm within an enterprise.
ITDR has emerged as a layer of defense focused on securing and managing the identity infrastructure like an active directory either with the cloud provider. ITDR enables customers reduce the time between a breach and detection. ITDR solutions enable security teams to identify all service and privileged accounts within their networks against any compromises. To minimize lateral movement post-breach, ITDR solutions monitor authentication traffic creating a baseline of standard behavior to identify anomalous activity. Some of the leading vendors in this category include:
Crowdstrike
SentinelOne
Semperis
Cisco (Oort)
Some of the vendors in this market are very good at protecting against identity attacks within active directory (like Semperis). Some vendors like the EDR players have brought their capabilities from malware detection into this category like Crowdstrike (leveraging an acquisition of Preempt) and SentinelOne (leveraging its acquisition of Attivo networks).
There are a number of emerging startups tackling the ITDR market using a different perspective like Hydden. For example, Hydden is primarily focused on Identity visibility across the entire Identity Attack Surface. Hydden’s continuous discovery platform can be deployed seamlessly on any infrastructure (cloud, on-prem, Windows, Mac, Linux, or container) to connect to any target identity system or application. The software maps every human and machine identity back to users, and provides continuous threat monitoring and alerting for indicators of compromise. Users can configure automated rules and workflows for orchestration and response actions and the platform integrates with 3rd party tools like SIEM and PAM vaults for deeper security.
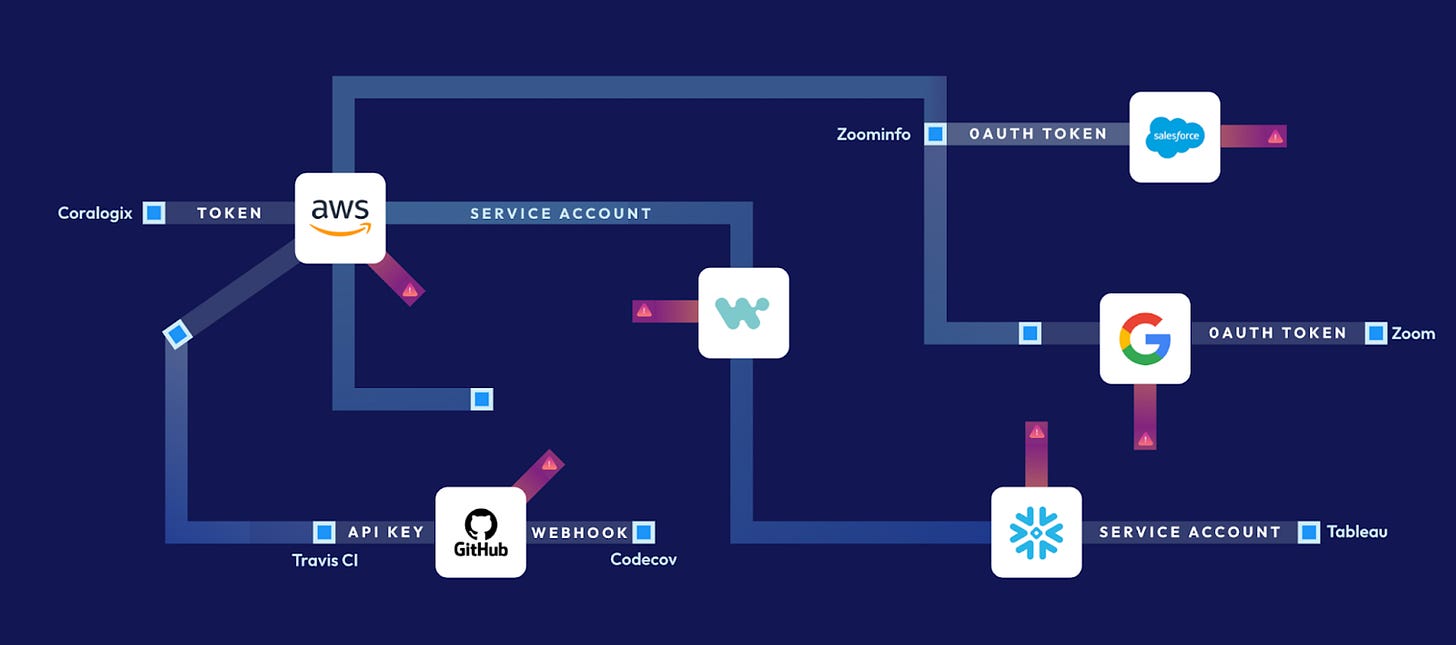
Non-Human Identity Security
The Identity Security market can also be divided into two main categories: human and non-human identities (NHIs). While the growth of human accounts has mostly flattened in recent years, trends like cloud-native architecture, microservices, SaaS, and API dependencies are driving exponential growth for non-human or machine identities.
This emerging opportunity - to focus more closely or entirely on all non-human identities, such as SSH Keys, Tokens, API keys, secrets, service accounts, and workloads - is both an expansion area for existing Identity players and an attractive market for startups to better address. Today, the average organization already has over 45x more non-human identities than human identities (per CyberArk and others). Yet, according to a recent Felicis Ventures CISO survey, Non-human or Machine Identity ranks as a top security pain point where CISOs desire more quality solutions. As we move into a more machine and AI-led era, this unsolved problem will come more into focus. Regarding the state of the NHI market, Clutch Security Founder Ofir Har-Chen said: “Given the fragmented nature of the non-human identity ecosystem, a holistic platform that covers the entire enterprise landscape becomes table stakes for organizations.”
History
Non-human Identities have been a problem for many years, and poor management has led to many of the recent high-profile breaches, such as Okta, Jumpcloud, Lastpass, and others. The problem has expanded from on-premises SSH key management to other forms of tokens and machine identities spread across SaaS Applications and Cloud environments. Nevertheless, the core SSH key problem is still overlooked and largely unsolved.
For instance, Venafi - a leader in machine identity - was founded in 2004 and became a unicorn in 2021 when Thoma Bravo bought a majority stake, valuing the company at $1.15B. According to 20-year-old Venafi, most large organizations use SSH keys across at least 1,000 systems or more, yet only 10% have a complete and accurate SSH key inventory. SSH keys are often managed manually by users or admins but can become lost and expired, leading to security liabilities.
As non-human identities increasingly include more secrets and DevOps tokens, the worlds of PAM and Machine Identity have come closer together. For instance, CyberArk acquired Conjur in 2017 (for $42M) to better protect secrets and manage machine identities in the DevOps lifecycle (per press release). According to Jefferies, roughly a third of CyberArk’s customers now purchase Secrets Management, in addition to core PAM.
Components of Non-Human Identity (NHI)
As an emerging category, the foundational components of a non-human identity platform are still being defined. However, using the Workforce Identity stack as a proxy, we can envision what an analogous platform for non-human Identities would look like. The foundation starts with a Source of Truth. For employees and human identities, this typically starts with HR systems like Workday and ERPs like SAP. Next, there is a lifecycle management layer on top - such as Microsoft AD or Okta, Governance and Privileged modules or platforms (like Sailpoint or CyberArk), and finally the emerging Detection and Response layer at the top.
This entire stack may need to be replicated for non-human identities. Various sources of truth across on-premise, cloud, and SaaS environments create a disjointed source of truth today across Github, CI/CD, various public clouds, legacy Microsoft AD, PAM, and more. A winning Machine Identity platform is likely to streamline detection and aggregation of API Keys, Tokens, Secrets, Certificates, and Service Accounts across all of these environments and apps.
More specifically, if we look at a leader like Venafi, we see a suite of products, including:
Control Plan for Machine Identities: a central hub for managing and monitoring
TLS Protect: focused on detecting and preventing TLS certificate outages
CodeSign Protect: ensuring code signing workflows keep keys secure, encrypted, and properly stored
Zero Touch PKI: managed and cloud-based Public Key Identification (PKI)
SSH Protect: tracking, monitoring, and lifecycle management of SSH Keys
Specialized offerings for Kubernetes
Alternatively, early-stage Astrix breaks down their non-human identity platform into four product capabilities:
Inventory: real-time discovery of non-human identities
Threat Detection: detect suspicious non-human activity in real time
Posture & Remediation: risk prioritization and response
Secret Security: protect secrets and lifecycle management
We also want to briefly mention Aembit (An RSA Sandbox Finalist). Aembit is a very early identity company that does authentication for workload identity companies. Similar to what Okta does for workforce identity, they also do the same thing. They provide a very secure way of delivering machine-to-machine credentials to workloads. They validate asset identity via contextual properties and integrations and then inject the approved credentials into the workload.
In summary, the core services that a non-human identity platform offers will likely mirror other IAM platforms, covering 1) detection and visibility, 2) security and management, 3) compliance and audit, and 4) analytics and remediation.
Identity Security TAM & Segmentation
We’ve tried to make the case that identity security is core to any security program so it would be a good idea to take a step back and see what the data says. When we spoke with security leaders at large enterprises, all positioned identity as a top three priority and they expect to increase spend over the next 3-5 years. Additionally, these companies spend between 20-30% of their total security budget on identity-related solutions.
What we heard from our conversations seems to align with broader surveys - including Barclay's most recent CIO Survey (1H24), which shows IAM as the #3 priority behind endpoint and cloud security. Barclays noted that although IAM ticked down from its #2 spot, overall interest increased the most compared to other areas of security. Also, since identity is a core component of cloud security (CIEM & CDR) we believe identity security has a strong link to the cloud security market.
Another signal that shows the segment’s importance is how well it’s growing compared to the overall information security market. Gartner estimates the 5Y CAGR (’21-’26) of IAM to be 13.3%, above the 10.3% growth of the total infosec market. When looking into the segments, it lines up well with what we see happening with financing/acquisition activity, mainly table stakes solutions like authentication (i.e., MFA, SSO) are saturated within enterprises - they are now turning their focus to visibility, managing access and policies, monitoring, and workflows which are now capturing more budget. It’s no surprise that cloud-native solutions are driving growth as companies transition from legacy, on-premises deployments to cloud-native, SaaS solutions.
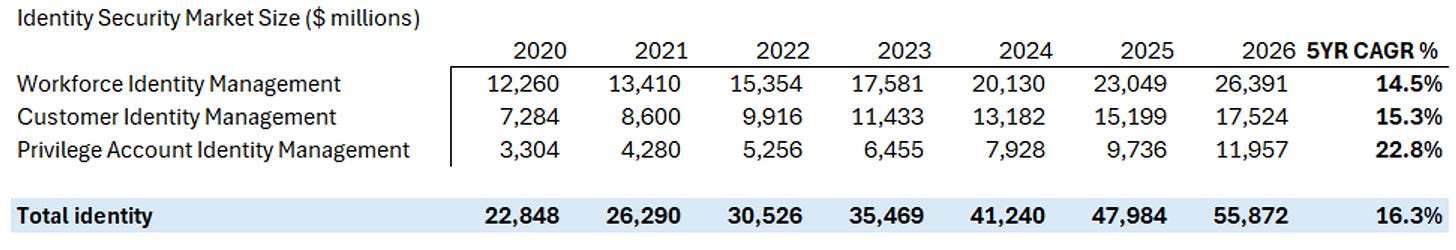
Another interesting cut of the market comes from Technavio, bucketing by workforce, customer, and privileged identities. According to Technavio, workforce identity, the solutions that help keep internal enterprise resources secure while providing access to employees, accounts for 50% of the identity market and is growing at a CAGR of 14.5%. Customer and privileged identity management share the remainder at 32%, 18%, respectively. Customer identity manages external identities, like signing into your favourite retailer to complete a purchase and is expected to grow at a CAGR of 15.3%.
Privileged users are those with more privileges than basic users, they are the ones who can grant access to other users, install software, access critical resources, or modify to a greater ability. These accounts are specifically targeted by malicious users to gain access and move laterally across an organization. Privilege accounts include non-human identities like workloads, API keys, and service accounts. Privilege account management is forecasted to grow the quickest at a 22.8% CAGR. Note, we view privileged account management as mostly a workforce identity sub-segment.
Predictions On the Future of Identity
Cloud Infrastructure Entitlement Management (CIEM) to take more prominence: We expect to see more vendors incorporate CIEM into their solutions as more enterprises move to the cloud. CIEM has emerged as a new way to manage cloud identities. One of the biggest challenges for organizations moving to the cloud is that there are more and more privileged and entitled users. Relative to technologies like CSPM (cloud security posture management), CIEM has evolved into a category for managing privileged users in cloud environments using some of the core components of PAM and IGA. We align with Gartner’s view of CIEM that addresses entitlements around developer resources like access to file shares, database tables, and workloads. Over the long-run, we expect that CIEM will become the umbrella terminology that brings together the PAM and IGA market. We expect this market to be one of the fastest-growing categories over the next few years.
Further Consolidation Amongst Leading Identity Platforms: We expect to see further consolidation within this market. For example, a 2022 Gartner survey suggested that 75% of client organizations are pursuing an identity vendor consolidation strategy, up from 29% in 2022. Most vendors within the identity realm have responded with new offerings that push into identity areas tangential to their core offerings. We anticipate more workforce identity companies trying to consolidate IGA, AM and PAM into one central cloud solution. In some cases, these consolidated platforms could appear in the shape of CIEM or a large cloud-access management solution. We’re seeing examples at work with Thoma Bravo’s acquisition and we anticipate more of it within the market.
Growing market opportunity and importance of non-human identities: We believe non-human identity (NHI) will continue to be a prevalent market. If we consider that the $20B+ Identity Security market today focuses almost entirely on human identities, security for non-human identities has the makings to be one of the next big things across security. Otherwise, this market is difficult to size at this time. As per precision reports, the global Machine Identity Management market size was valued at USD $1.2B in 2021 and is expected to expand at a CAGR of 12.25% during the forecast period, reaching USD $2.4B by 2027. If we add AI and automation to the mix, the oversight of NHI may soon hit a tipping point. As organizations build in more scripts for automations, lean on Robotic Process Automation (RPA), and experiment with autonomous AI agents, better solutions for NHI security will be paramount. Over the next few months, Francis will be writing more about this topic in more depth.
Growth In Customer Identity and Access Management (CIAM): The demand for customer identity solutions is increasing due to the expansion of companies' digital customer footprints, the introduction of privacy requirements by legislative bodies (like HIPAA, GDPR, CCPA), and the rise in high-value digital transactions, which add complexity and risk. Therefore, CIAM solutions are becoming essential for organizations aiming to enhance user experience and ensure secure digital engagement with their customers.
An Evolution of PAM: Privileged Access Management (PAM) has changed a lot with the shift from on-premise to cloud environments, incorporating trends such as DevOps and Zero Trust. Though the PAM market leadership positions have been consistent, with CyberArk in the lead, followed by BeyondTrust and now Delinea (created through Centrify and Thycotic merger), others focused on the Cloud and DevOps, like Hashicorp, have also entered the fray. For organizations that are entirely in the cloud, PAM can often be more simplified with developer-focused access portals.
The cloud shift has also led to some convergence of the traditional "swim lanes" between IAM, IGA, and PAM, and market leaders are expanding into adjacent areas through acquisitions and internal development. For example, CyberArk acquired Adaptive to enhance its IAM solutions and Okta introduced Privileged Access in December 2023. We expect to see more convergence, especially between IGA and PAM when it comes to cloud-native organizations in particular.
Convergence does not mean that the core principles of PAM go away. Instead, the ideal state may very well be some level of PAM and added security across all accounts that can dynamically adjust safeguards based on risk levels and behavioural activities. This approach, although challenging due to the traditional separation of PAM from other IAM functions, aims to enhance security across an organization's entire digital environment. Companies like CyberArk have had an eye on this future for some time (see image below for depiction), and the convergence of identity technologies may help this finally come to fruition.
Authorization has its Authentication ‘moment’: For both internal and external-facing applications, many elements of Authentication (AuthN) have been solved to some degree. For instance, there are now many out-of-the-box options for app & website developers to authenticate and manage users. However, when it comes to Authorization (AuthZ) (i.e., granular controls once inside the app), the market has been slower to develop and most apps have homegrown AuthZ controls. We expect to see more momentum to solve AuthZ challenges with out of the box ‘AuthZ as a Service’ from the likes of Oso, Permit, and others. Oso founder, Graham Neray, sums the trend up well, stating "over the last 15 years, companies like AWS, Stripe, and Twilio taught us to offload anything not core to our value prop to a third-party API. Authentication underwent this transition years ago and is now commoditized. Authorization is the next layer to be unbundled.”
If you found this identity research helpful, please like and share. You can also subscribe to receive future cybersecurity research reports on emerging cyber themes, companies, and categories.
















Great article! Nothing about DID/VC from W3C and ZKP?
Exceptional insights! This article reflects deep expertise and offers valuable clarity on such a critical topic.