Building the Intelligence Layer for the Next Wave of Data Loss Prevention (DLPs)
How AI, DSPM, and Distributed Controls Are Turning a Legacy Safeguard Into a Modern Intelligence Layer
Actionable Summary
This report is the product of an independent analysis conducted with Cyera, whose support enabled deeper access to primary data, customer interviews, and technology briefings. Our shared objective is to give security leaders a clear, fact-based view of how Data Loss Prevention (DLP) has evolved from rule-bound gateways that struggle with cloud sprawl and gen AI risk to modern, context-aware platforms that merge Data Security Posture Management (DSPM) with real-time enforcement.
Key Points
The DLP landscape is at a critical inflection point; driven by the exponential growth of sensitive data, rising data breach costs, and rapid cloud adoption. As enterprises shift to hybrid work and digital transformation accelerates, traditional DLP tools, often cumbersome, siloed, and generating high false-positive rates, fail to keep pace. This dynamic environment underscores an urgent industry-wide need for smarter, adaptive solutions that can protect data seamlessly across increasingly distributed ecosystems.
The total addressable market (TAM) for DLP is expanding rapidly: It is projected to reach billions of dollars within the next few years. This growth is fueled by intensifying regulatory pressures, heightened sensitivity around intellectual property and personally identifiable information (PII), and escalating threats such as insider risks and sophisticated cyberattacks. Companies that can effectively address these challenges with robust and innovative DLP solutions stand poised to significantly capitalize on this expansive market opportunity.
The rise of generative AI has introduced new complexities and vulnerabilities; exposing sensitive information through unsecured AI prompts, inadvertent data leaks, and unmanaged shadow AI usage across enterprises. These GenAI risks, coupled with legacy DLP tools' inability to manage them, have created gaps that require immediate and innovative attention. Businesses must prioritize the integration of intelligent, adaptive technologies that can proactively detect and prevent sensitive data exposure in GenAI environments.
Historically, the DLP space has given rise to significant industry leaders and innovations, with early movers like Symantec, Forcepoint, and McAfee shaping foundational approaches. Yet, the legacy approach, anchored in static policies, siloed visibility, and agent-heavy deployments, is now inadequate against modern threats and digital workflows. The next phase in DLP innovation demands a transformational approach, shifting from reactive and rule-based solutions towards proactive, context-aware, and intelligent frameworks.
Cyera’s Omni DLP emerges as a transformative intelligence layer,
reimagining data protection by leveraging advanced AI to provide context-driven visibility, reduce false positives dramatically, and offer consistent policy orchestration across diverse environments. Rather than replacing existing infrastructure, Cyera integrates seamlessly, enhancing effectiveness, accelerating deployment, and significantly reducing operational overhead. This intelligence-driven approach represents a significant step forward, positioning enterprises to navigate today's complex data security landscape with greater precision, agility, and resilience.
Objectives of DLP Programs
The main goal of Data Loss Prevention (DLP) is to prevent sensitive information, such as intellectual property, personal data, or financial records, from leaving your organization's control without permission. This includes preventing accidental leaks, insider threats, and cyberattacks.
DLP solutions prevent the leakage of corporate data and the accidental transfer or loss of data. DLP is implemented according to dynamic content- and context-based policies and offers visibility into and contextual analysis of data-at-rest and in-transit across on-premise and cloud environments. The underlying technology uses data classification labels and tags and content inspection techniques to identify sensitive content and analyze actions related to its use. DLP also helps you comply with regulations (like GDPR), gives you visibility into where your data is and how it's used, and ultimately reduces the risk and cost of data breaches. It works by identifying, classifying, and monitoring sensitive data to enforce rules against unauthorized access and sharing.
The Urgency & Trends Showing Gaps in DLP
Companies are struggling to build effective DLP programs because it is so hard to understand the data and the context in which it is moving. YL Venture survey shows that according to Forrester’s “The State of Data Security” (July 2024), 83% of enterprises currently use endpoint DLP, but only 13% have fully deployed their data security capabilities in the cloud. This gap, combined with growing privacy and compliance demands, positions next-generation DLP solutions as critical components of future security strategies.
Meanwhile, the volume and type of data enterprises now handle has exploded. Based on insights from 218+ CISOs, 2025 is seeing increased budgeting to prioritize Data Security (including DLP) into their plans. The data suggests DLP is back: Almost half of data security projects involve data loss prevention, or DLP. This renewed interest isn’t just about compliance; it’s also about the opportunity AI presents to finally improve data classification at scale. While data security posture management as a separate category seems to be dwindling, secrets management, data vaulting and tokenization all showed up as projects in our conversations.
60% of organizations express a lack of confidence in their ability to detect and respond to data exposures. This situation is prompting security teams to re-evaluate and adapt their data security strategies for the AI era, with increasing consideration for utilizing AI for data protection. The growing consensus is that static policies and regex-based detection won’t cut it anymore. Teams want tools that can learn, adapt, and operate in real time. Many organizations are attempting to manage AI by identifying and protecting AI applications in advance. However, this approach is unsustainable. As AI becomes integrated into nearly every application, like Zoom, which now incorporates AI, it's impractical to isolate and protect only specific AI tools. Data security needs to adapt to a world where AI is embedded everywhere, not segmented. You can’t protect just “AI tools” when every tool becomes AI-powered.
The most commonly used methods in data inventory and discovery include Data Backup and Recovery (46%) and Data Loss Prevention (DLP) solutions (45%). While these tools play crucial roles in protecting and recovering data, they often function independently, leading to silos that limit visibility and coordination across the organization. And without shared context, even well-designed tools struggle to deliver meaningful insights.
Furthermore, most organizations already have multiple tools with Data Loss Prevention (DLP) capabilities, often six or more, according to a guest speaker we had from Cyera. To supplement this, a recent study found that 94% of organizations use at least two DLP tools, averaging more than three. In many cases, organizations are unaware of the full extent of these existing capabilities. This proliferation of tools leads to complexity, inefficiency, significant administrative overhead and alert fatigue.
Historical Challenges with DLP
High False Positive Rates
One of the most significant challenges with traditional DLP solutions has been the overwhelming volume of false positives, which in some cases can reach up to 90%. These false positives drain security teams' resources and attention, causing legitimate security incidents to go unnoticed amidst the noise. This issue stems from reliance on static, pattern-based detection methods like regular expressions, which fail to accurately discern the contextual nuances that differentiate benign actions from genuine threats.
Static and Non-Adaptive Policy Enforcement
Historically, DLP technologies have relied heavily on predefined, static rules and regular expressions to detect sensitive data. Such static policies lack adaptability, struggling to keep pace with dynamic business processes and evolving threat landscapes. Without adaptive capabilities or context-awareness, policies quickly become outdated, leading to coverage gaps, increased risk exposure, and operational inefficiencies from constant manual tuning.
Fragmented Visibility Across Environments
Traditional DLP tools often operate in isolation, creating significant visibility gaps. Enterprises typically employ multiple siloed solutions for SaaS applications, CASB platforms, email, endpoints, network traffic, APIs, and on-premises infrastructure. This fragmented approach prevents security teams from gaining a unified view of their data landscape, significantly complicating efforts to consistently enforce data protection policies and respond swiftly to threats.
Challenges with Emerging Generative AI Technologies
The rapid adoption of generative AI technologies has introduced new avenues for sensitive data exposure. Risks include inadvertent data leaks through prompts, intellectual property vulnerabilities via large language model (LLM) ingestion, unmanaged shadow AI tool usage, and inadequate protection against generative AI misuse. Traditional DLP tools, designed prior to these emerging risks, have been ill-equipped to detect and manage these nuanced scenarios effectively.
Time-Consuming and Resource-Intensive Deployments
Deploying traditional DLP solutions often demands significant time and dedicated resources, typically spanning weeks or months. The process involves substantial manual effort for policy management, tuning, validation, and ongoing maintenance. As a result, enterprises must allocate dedicated personnel solely for DLP upkeep, reducing agility, increasing operational overhead, and delaying time-to-value.
Operational Overhead from Agent-Based Models
Agent-based DLP deployments historically impose considerable operational burdens, including lengthy implementation cycles that can extend for years. These agents often lead to noticeable system performance degradation, complicating user acceptance and impacting overall productivity. Such operational complexities dissuade organizations from fully leveraging DLP capabilities, thereby leaving sensitive data inadequately protected.
Limited Effectiveness Against Modern Threat Vectors
Traditional DLP solutions frequently struggle against contemporary threats like ransomware, advanced data exfiltration techniques, generative AI exploitation, and automated threats from non-human identities such as bots and service accounts. Additionally, many legacy DLP products lack the capability to adequately manage API-based integrations or monitor automated bot activities within collaboration platforms like Slack, Microsoft Teams, and Office 365, leaving enterprises vulnerable to sophisticated threats that exploit these modern digital channels.
Lack of DSPM Context
Effective data protection fundamentally requires a robust understanding of the underlying business context. Data sensitivity definitions should be consistent, regardless of the platform or environment, while accommodating contextual variations such as user location, device management status, or role changes. Distributed policy enforcement, employing unified core rules adapted to specific contexts, is critical to maintaining consistency across environments.
Equally critical is the foundational quality of data governance and architecture. Without structured data, comprehensive labeling, clear ownership, and access controls, DLP tools cannot accurately discern sensitivity or risk, leading to poor decisions and ineffective protection. Thus, security teams must integrate deeply with data governance efforts, leveraging clearly defined data structures and lifecycle management practices. Ultimately, successful DLP programs are built on intentional data architecture, comprehensive governance models, and collaborative efforts between security teams, data owners, and governance stakeholders.
How The Industry Has Solved Data Loss
Categories of DLP Solutions
Traditional DLP
Enterprise Data Loss Prevention solutions are comprehensive, standalone platforms specifically designed to protect sensitive data across an organization’s entire infrastructure. These robust tools typically offer centralized management, sophisticated data discovery and classification capabilities, and extensive policy controls across multiple data exfiltration channels—such as email, endpoints, network traffic, cloud applications, and on-premises repositories. Enterprise DLP systems are built to provide granular detection mechanisms, enabling businesses to enforce detailed security policies and comply with complex regulatory requirements. However, they traditionally demand significant investment, complex implementation processes, and dedicated teams to manage and fine-tune them effectively.
These solutions offer centralized policy management and reporting functionalities across a broad spectrum of common data exfiltration channels, including email, endpoint, network, browser, and cloud environments. EDLP platforms are designed to provide consistent policy definition, deployment, and alert monitoring across multiple channels. Some sample vendors: Symantec DLP (Broadcom), Forcepoint DLP and McAfee DLP (Trellix)
Embedded DLP (EDLP)
Integrated Data Loss Prevention refers to DLP functionalities that are embedded within broader security or productivity platforms, rather than standalone solutions. These integrated or converged solutions provide data protection as part of another primary offering, such as Secure Email Gateways (SEGs), Endpoint Protection Platforms (EPPs), Security Service Edge (SSE), or Cloud Access Security Brokers (CASBs). Although historically narrower in coverage compared to enterprise-grade solutions, integrated DLPs have significantly improved in recent years. They typically offer sufficient coverage and controls for common use cases like email protection, endpoint data leakage, and basic cloud data protection. The advantage of these solutions is their streamlined implementation, often reduced total cost of ownership, and simplified management within existing security stacks.
IDLP refers to DLP features that are natively embedded within other broader security solutions, such as Secure Email Gateways (SEGs), Endpoint Protection Platforms (EPPs), or Security Service Edge (SSE) platforms. Historically, IDLP solutions provided narrower channel coverage, often limited to one or two channels, and their features were less robust compared to EDLP.
Sub-Categories
Network (SEG, SWB, SSSE) focused DLP → Integrates DLP capabilities within network security tools like Secure Web Gateways (SWGs), Secure Email Gateways (SEGs), and Security Service Edge (SSE) platforms.
SaaS DLP → Designed to protect data within Software as a Service (SaaS) applications, offering visibility and control over data in cloud environments.
EDR/EPP DLP → Embeds DLP functionality within Endpoint Detection and Response (EDR) or Endpoint Protection Platforms (EPP), focusing on data protection at the device level.
Sample vendors:
Microsoft Purview (DLP capabilities in Office 365, Defender)
Proofpoint (Embedded Email DLP)
Zscaler (DLP Embedded into SSE)
Cisco Secure Endpoint (Endpoint DLP)
Cloud-First & Modern API-Based DLP
Cloud-Native Data Loss Prevention solutions are designed explicitly for cloud environments and delivered predominantly as Software-as-a-Service (SaaS). These solutions leverage APIs and native integrations to protect data within cloud-based applications and services like SaaS productivity tools, cloud storage, and Infrastructure-as-a-Service (IaaS) platforms. Cloud-native DLP products focus on discovering, classifying, and protecting data directly within cloud applications, addressing modern security challenges such as unauthorized data sharing, misconfigurations, shadow IT, and data misuse within collaborative and generative AI platforms. Unlike traditional DLP, cloud-native solutions offer rapid deployment, easy scalability, reduced operational overhead, and better alignment with agile, cloud-first IT strategies. Sample vendors include Cyera Omni DLP (AI-driven cloud-native solution), Netskope Intelligent SSE – Cloud DLP and Nightfall AI
Next-Gen AI DLP Intelligence Layer (Cyera Omni DLP)
Cyera Omni DLP
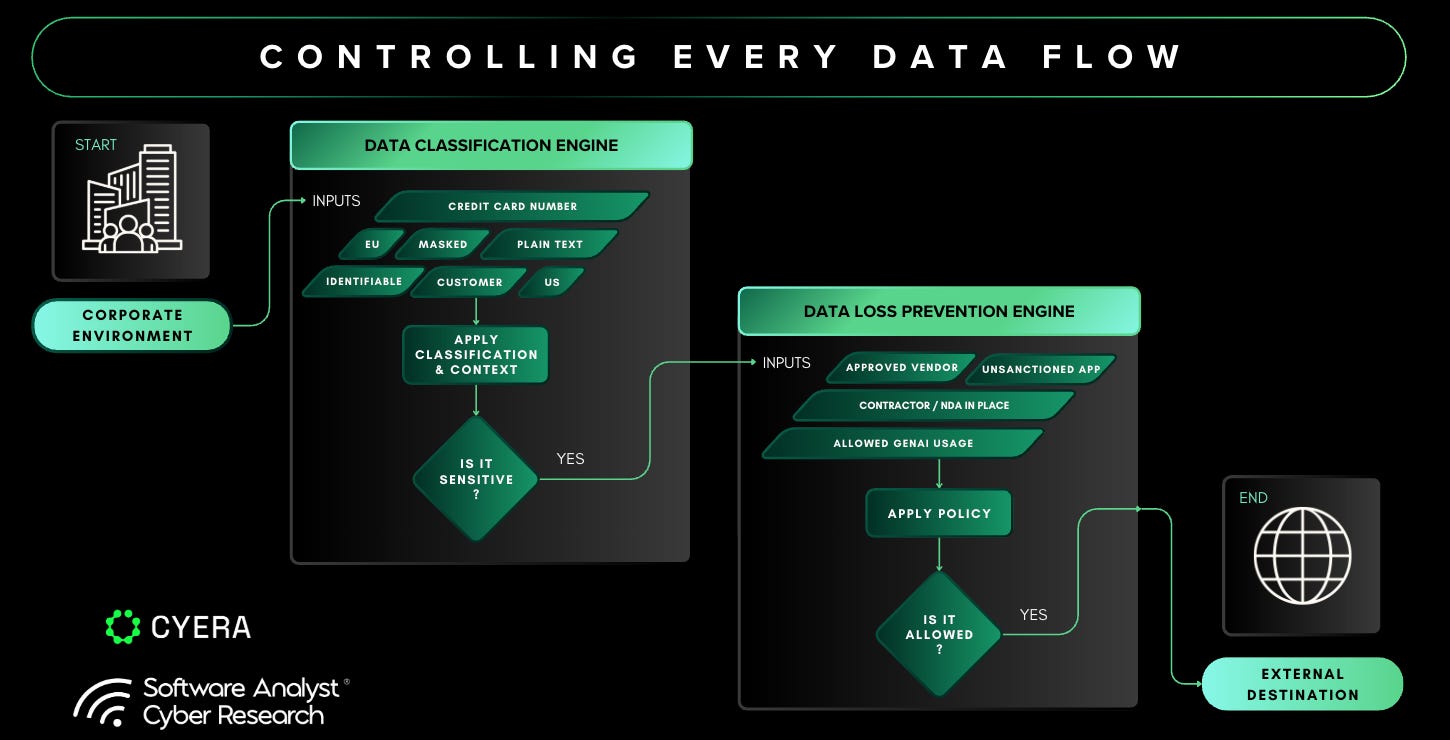
Cyera Omni DLP, part of Cyera’s Data Security Platform, is an AI-native Data Loss Prevention solution that serves as a unifying intelligence layer for an organization’s data security stack. It functions an AI-first “policy brain” that sits above the data enforcement tools customers already own. It ingests Cyera’s own DSPM-driven classification engine (“Data DNA”) and identity context, then re-scores each event as it passes through email, web, SaaS, endpoint, or AI channels such as Microsoft Copilot and ChatGPT.
Cyera deploys Omni DLP by integrating with the APIs of existing DLPs and security tools that serve as control points and use browser extensions, mail gateways, or endpoint/kernel agents.
The system learns from past alerts and continuously refines policy recommendations through A/B testing. Cyera claims this reduces noise by up to 95%, without requiring teams to manually tune rules.
History & Context
Before Cyera unveiled Omni DLP, they acquired Tel-Aviv-based Trail Security in October 2024 for about US $162 million, betting on real-time data-in-motion controls.
Trail had been operating largely in stealth, but its founders (graduates of Israel’s Talpiot elite technology program) had already built an AI-native DLP engine that could inspect live data flows, correlate user context, and suppress more than 90% of false positives in test environments. From Cyera’s vantage point, Trail filled the biggest functional gap in its platform. Cyera’s strength until that point was data-at-rest intelligence: an agentless DSPM layer that discovers and classifies sensitive assets in cloud and SaaS estates with high precision. What Trail added was the missing “control plane” for data in motion: policy creation, prompt inspection, AI-driven anomaly scoring, and enforcement hooks into email, SaaS, SSE, and endpoint channels.
By fusing Trail’s DLP brain with Cyera’s classification graph, the combined stack could answer two long-standing CISO questions in one workflow: What data do I have, and can I stop it from walking out the door, primarily through GenAI tools?
The integration happened quickly. Within six months of closing, Cyera productized Trail’s engine as the Omni DLP product, using Trail’s LLM inference layer to auto-tune Microsoft Purview, Zscaler, Netskope and other in-place DLP controls while layering new inline protections for AI prompts and browser uploads. The Trail acquisition explains why Omni DLP feels less like a bolt-on feature and more like an integrated pillar of Cyera’s Data Security Platform. Trail supplied the real-time enforcement capabilities; Cyera brought the data intelligence and identity context. Together, they underpin the unified, AI-native DLP approach now recognized in the market as Omni DLP.
New Architecture Model
AI-Native Controls
This architecture provides several meaningful differentiators. First, Cyera owns both halves of the equation: data-at-rest discovery via DSPM and data-in-motion control via Omni DLP. This means policies inherit precise, column-level classifications rather than generic regexes and “credit-card” strings.
We’ll note that the "learned classifications" that Cyera provides are GenAI-based classifications that are unique to that specific customer's environment. This often accounts for about 20-40% of the total classification categories which they discover within a customer environment
Second, the large-language-model at the core of Omni interprets full payloads (including prompt-and-response flows to LLMs) and explains its decision in plain language, a feature absent from most legacy stacks and critical for building trust with business users. Third, Omni is designed to integrate with existing infrastructure, such as Microsoft Purview or SSE platforms. This avoids rip-and-replace deployment models and turns existing licenses into smarter enforcement channels.
Unified Risk View
Cyera Omni DLP provides unified protection across all three data states: in motion, at rest, and in use. This pervasive coverage spans files, applications, diverse cloud environments, and specific solutions that touch AI tools like Microsoft Copilot and ChatGPT. It's "AI-brain DLP," which adaptively detects and monitors real-time changes in data, user behaviour, and environmental shifts, thereby maintaining consistently low false positives and high accuracy. The platform offers a consolidated, 360-degree view of data in motion, enabling organizations to assess data risks comprehensively by channel, severity, and category. It also provides actionable insights to prioritize critical alerts based on factors such as risky users, high-risk destinations, and the recency of activities.
Evaluation Criteria For Modern DLPs
Cyera's approach transcends traditional data-in-motion DLP by offering a truly holistic protection model that encompasses data in all three critical states: at rest, in motion, and in use. This comprehensive coverage is achieved through the synergistic integration of Data Security Posture Management (DSPM) and Data Loss Prevention (DLP).
We were impressed with the following core capabilities of Cyera Omni DLP relative to the limitations of traditional DLP:
AI-Powered Alert Prioritization: Cyera leverages AI to help security teams cut through the noise, prioritizing only the most critical alerts. This significantly reduces the burden of "alert fatigue" and allows security personnel to focus their efforts on incidents that genuinely matter.
Gen AI Visibility and Protection: Omni DLP provides comprehensive visibility across GenAI tools, going into data interactions, from the initial prompt to the AI's response. It detects data that violates policy and enriches this information with crucial context from sources like Active Directory (AD) and Human Resources Information Systems (HRIS) to accelerate incident triage.
AI-Guided Policy Management: The system continuously analyzes alert trends, user behavior, and historical data to intelligently recommend, test, and deploy highly accurate, risk-aware policies. These policies are designed to dynamically adapt to the evolving environment, ensuring protection without inadvertently creating new security gaps. They also have detailed alert analysis - this feature also extends to how they manage every alert. Upon flagging a potential data loss event, Cyera Omni DLP assigns a severity ranking and provides an AI-powered, detailed analysis. This includes clear explanations of why an action was flagged, when it occurred, who was responsible, the intended destination, and the severity level, often accompanied by a simple summary and related alerts for efficient investigation.
Automated Rule Creation: Moving beyond the cumbersome and often inaccurate reliance on complex regular expressions (regex), Omni DLP's AI learns to accurately recognize an organization's unique sensitive data (using its DSPM context). It then automatically generates detection rules that are native to the enforcement tools already in place, meaning the rules are translated into the policy language of each DLP control point for inline enforcement. With every alert, the AI continuously learns, adapts, and refines these policies, drastically reducing the manual effort required for fine-tuning. This data-centric DNA feature allows them to easily break down the elements of a triggered alert, assess its inherent risk level, and determine whether it constitutes a false positive. This granular analysis empowers security teams to make confident, data-driven decisions, eliminating guesswork.
Proactive Insider Threat Detection: The solution is adept at identifying early indicators of insider data exfiltration. It achieves this by analyzing behavioral patterns, access patterns, and data sensitivity across an enterprise's DLP or security controls, allowing security teams to discern between routine work and emerging risks before they escalate into a full-blown breach.
Reduced Deployment and Management Friction: Compared to traditional solutions, Cyera Omni DLP has a faster time-to-value. It leverages API integrations and existing infrastructure where possible, minimizing the need for new agents or hardware. Its unified console and intelligent automation significantly reduce the ongoing administrative overhead (fewer consoles, fewer tickets to chase, and simplified policy workflows). This ease of deployment and use is a competitive selling point, especially for lean security teams that can’t afford massive projects to overhaul DLP.
Intelligent Alerting and Contextual Analysis: The service alerts security admins to potential data loss events, ranking them by severity. Its AI engine provides a detailed analysis for each alert, explaining why an action was flagged, when it occurred, who caused it, the intended destination, and its severity. It also offers a clear summary and highlights related alerts for the data security team.
API-based AI integrations: Next-gen solutions specifically address API-based AI integrations and the use of bots within platforms like Slack and Office 365, ensuring comprehensive coverage in modern work environments.
Cyera integrates into existing environments without requiring new servers, proxies, or causing disruption. Its fast API connectivity enables rapid setup, often within minutes, facilitating the orchestration of policies across an organization's pre-existing DLP stack.
Future Prediction for DLP
AI and ML Enhanced Detection as an Intelligence Layer
Legacy DLP relies on regular expressions and static dictionaries, which misfire on both richly formatted business documents and novel obfuscation tactics. Modern platforms graft an intelligence layer of machine-learning classifiers, natural-language models, and graph analytics onto that foundation. Supervised models learn the semantic fingerprints of sensitive data such as contracts, design specs, M&A decks, so they can spot partial excerpts, rephrased text, or screenshots that would bypass regex.
Unsupervised anomaly-detection engines establish baselines for every user-data-channel tuple and surface deviations that indicate insider exfiltration or compromised credentials. Critically, these AI engines feed continuous feedback loops: analysts label alerts, the model recalibrates, and false positives fall while detection recall climbs. Deployed properly, the ML layer also serves as an orchestration hub, enriching DLP alerts with context from DSPM, IAM, and UEBA systems so that security teams see a single, ranked queue instead of thousands of noisy events.
AI-Driven DLP for Generative-AI Risk
This builds on the previous point. Gen AI platforms, whether public services like ChatGPT or enterprise copilots embedded in SaaS, create a bidirectional risk channel: sensitive data can flow into prompts, and proprietary model outputs can leak back out. An “AI DLP” layer monitors that conversation at three points: (a) prompt inspection before the request leaves the user device, flagging or redacting PII, regulated data, or source code; (b) in-model telemetry that tracks what the LLM ingests and how it is retained or cached; and (c) post-response analysis that verifies no sensitive material is echoed back or stored in unsecured links and vectors. Shadow AI usage is surfaced by correlating browser telemetry, SaaS audit logs, and expense/procurement systems to reveal unsanctioned tools and rogue API tokens. To be effective, the solution needs fine-grained policies such as “allow anonymized financial metrics to ChatGPT but block customer account numbers”, plus dynamic risk scoring that tightens controls if a user suddenly starts exporting large training sets. This capability must extend beyond a single chatbot, as AI functionality is embedded across every productivity suite, and the inspection and control logic has to follow the user’s identity and the data itself, not a static list of domain names.
Adaptive, Context-Aware Policy Management
Static “one-size-fits-all” DLP policies break the moment a developer works from home, a salesperson joins a new territory, or a file’s classification changes. Adaptive policy management uses real-time context like device posture, geolocation, peer-group behavior, recent role changes, and even project metadata, to tune enforcement on the fly. For example, downloading a sensitive CAD file inside the corporate network may be normal, but the same request from an unmanaged tablet on public Wi-Fi raises the policy threshold: the download is watermarked, usage is limited to a VDI session, or the action is blocked outright. Context engines pull telemetry from EDR agents, IdP logs, CMDBs, and business systems (HRIS, CRM) so a single classification update or role change instantly ripples through every control point. Decisions are rendered at the edge; browser plug-ins, SaaS APIs, or endpoint agents, ensuring millisecond-level responses without hair-pin routing. The result is a living policy fabric that aligns security with business intent: strict when risk is high, invisible when workflows are legitimate, and always synchronized with the organization’s evolving data landscape.
Unified Visibility Policy Architecture
Organizations must transition from legacy, on-premises architectures to cloud-native, cloud-delivered DLP solutions. This approach provides greater scalability, reduced complexity, and seamless integration across hybrid environments, effectively addressing distributed workforces and cloud-based workflows.
To overcome fragmentation, security and risk management leaders should adopt solutions that provide unified visibility and centralized policy orchestration across SaaS applications, endpoints, networks, cloud services, and on-premises environments. This holistic, integrated approach ensures consistency and comprehensive coverage of data protection
The next chapter of data-loss prevention pivots on a single, cloud-hosted “policy brain” that maintains every sensitivity label, compliance rule, and zero-trust mandate while distributing machine-readable controls to the exact places data moves such as laptops, SaaS workspaces, developer pipelines, and edge devices. By enforcing policies locally, security teams erase blind spots created by direct-to-cloud traffic and VPN bypasses, letting a file be blocked in Slack on an unmanaged laptop yet flow unimpeded for an authorized developer on a managed build server.
At the same time, the market is collapsing traditional silos, DSPM, CASB/SSE, SSPM, and legacy DLP into unified data-security clouds that treat identity as the primary control plane and evaluate every read, write, or share through the combined lens of user intent, environmental risk, and data sensitivity. Lightweight language models embedded at the endpoint now detect risky copy-paste events or screen captures before content ever leaves the device, giving organizations sub-second prevention without routing traffic through a bottleneck. In short, the future of DLP is not a bigger gateway but an intelligent, context-aware fabric that distributes one authoritative rule set to every control point and adapts in real time as users, data, and threats evolve.
Unified Data Security Solution For DSPM + Gen AI Powered DLP
Modern data security should increasingly rely on a synergistic approach merging Data Loss Prevention (DLP) with Data Security Posture Management (DSPM). A powerful force combined, DLP adds the controls and action missing from DSPM, and DSPM adds the deep data understanding and context missing from DLP. This integration helps us understand and protect sensitive data across its entire lifecycle.
Modern AI-DLP uses agentless solution to combine advanced AI, real-time enforcement, and seamless integration to provide a dynamic, adaptive framework that effectively protects sensitive data across all complex data environments of today.
Thus, vendors are blending traditional DLP capabilities (e.g., data in motion protection) with DSPM to address data at rest and lineage requirements. It's hard to understand what was breached if you don’t have a tool. DSPM really helps to understand the scope of the breach and its materiality.
Case studies:
The context: Cyera acquiring Trail Security was the perfect illustration of this dynamic at play. As discussed, the power of leveraging labelled data by DSPM solutions together with GenAI-powered DLP engine has improved the capability for DLPs today, relative to over 20-years ago. All of this is powered by more data leading to more accurate detections, because the use of more discovered and classified data improves the accuracy of data in-motion. Beyond Cyera, some companies like Proofpoint are adding DSPM functionalities to their DLP platforms, signalling a convergence of solutions.
Traceability for investigation: Leveraging DSPM/AI simplifies how DLP engines are built. Instead of relying on handcrafted rules or regular expressions, DSPM provides the baseline logic. The DLP engine uses that logic to create accurate detection rules with minimal human input. This shift improves visibility across every stage of the data lifecycle, at rest, in motion, and in use. It also allows security teams to understand the full journey of data, including who accessed it, where it was sent, and when it moved across environments. Earlier, this type of traceability didn’t exist. Most teams had no way to track whether a sensitive file was exfiltrated, accidentally shared with a contractor, or pulled into an AI model. Now, they can detect not just breaches, but intent, including insider misuse, copy-paste behaviour, or data exposure inside generative tools.
Key Challenges in Modern DLP Implementation
Adoption and Education Barriers
Organizations also face significant challenges in understanding and implementing comprehensive "Omni DLP" solutions that protect data across all environments. This is compounded by the need for security teams to undergo extensive training to effectively integrate DLP with broader data security strategies, requiring substantial time and resource investment.
Integration with Existing Security Solutions
A major hurdle for organizations lies in integrating new DLP capabilities into entrenched security architectures. Most organizations have legacy tools and fixed processes that cannot be replaced overnight. The security stack must be carefully restructured to support modern features while preserving existing protections, which creates a difficult tradeoff between innovation and operational stability.
Overlap and Transition From Existing Solutions
One practical challenge is making the most of Omni DLP alongside other enterprise DLP investments. Many enterprises already have some DLP controls in place, however imperfect. When introducing Cyera, they need a clear transition plan. If not managed well, there could be duplication of effort or even policy conflicts (as mentioned above). For example, if Microsoft Purview is also running, which tool’s policy takes precedence in a given scenario? During a phased rollout, security teams might see alerts from both systems and need to reconcile them. This transitional period can be confusing and labor-intensive if not carefully orchestrated.
It’s important for the organization to have a clear roadmap: perhaps first use Omni DLP in audit mode to get comparative insight, then gradually shift enforcement from legacy/Integrated tools to Omni once it proves its accuracy, and eventually retire or minimize the use of the old systems. Communicating these changes to IT and end-users is also important (especially if end-user behavior or notifications are impacted, such as changes in block messages.).
Ultimately, this is a change management challenge. It’s not just about deploying new technology, but reworking workflows, revisiting team responsibilities, and retiring legacy approaches. Cyera and its partners often assist with this transition by providing best practices and migration playbooks. Still, companies should plan time to tune Omni DLP’s policies to match or improve on previous implementations to avoid any loss in protection. The upside is that once the transition is complete, ongoing management overhead drops significantly. But for large enterprises, getting there can be a project that spans weeks or months for a global enterprise.
Market Competition
New solutions in the market often encounter resistance from organizations that have made significant investments in traditional DLP and DSPM tools. This challenge is particularly acute for emerging vendors who must clearly demonstrate their value proposition against established vendors, highlighting unique features and capabilities that justify the transition to their platforms.
Conclusions
Data-loss prevention is entering a decisive new phase. Rule-heavy, agent-centric platforms that once dominated the market now struggle against cloud sprawl, hybrid work, and the unpredictability of generative AI driven workflows. What today’s security leaders need is not another rip-and-replace exercise but an intelligence layer that meshes with the controls they already own, whether those are Microsoft E5 DLP features, SASE inspection points, or niche SaaS connectors and lifts them to a consistent, context-aware standard.
That intelligence layer is arriving through the convergence of DSPM and DLP. By discovering and classifying data at rest, DSPM supplies the business context, who owns the data, how sensitive it is, where it travels using a rule-based DLP has long lacked for data in motion. When the two work in concert, policy decisions shift from brittle pattern matching to risk-based judgments, dramatically lowering false-positive noise while tightening prevention on genuinely risky transfers.
Artificial intelligence accelerates this convergence. Large-language models can now fingerprint unstructured content, map lineage across multi-cloud stores, and predict a user’s intent in near real time. Deployed as a policy brain rather than a bolt-on feature, AI continuously refines classifications, auto-generates granular rules, and prioritizes only those incidents that merit human review turning DLP from a perpetual tuning exercise into a self-optimizing control.
Cyera exemplifies this modern trajectory. Its platform begins with broad, agentless discovery, applies AI to classify and score data risk, and then feeds those insights back into whatever DLP stack the customer already operates. In doing so, Cyera transforms legacy deployments from blunt instruments into adaptive, zero-trust enforcers. Meanwhile, its roadmap toward full data lineage, endpoint-level prevention, and deeper GenAI safeguards positions it to keep pace with how data is actually created, shared, and consumed.
The lesson for security leaders is clear: effective DLP in 2025 and beyond will hinge on unified discovery, AI-driven context, and distributed enforcement not on bigger gateways or longer regex lists. Enterprises that embrace this model will not only cut operational drag and alert fatigue; they will establish a resilient data-security fabric ready for whatever innovations—and risks—the next decade brings.
Thanks for reading.
The Software Analyst is offering a Cybersecurity Bootcamp that delves into all the introductory elements of cybersecurity. If you want to expand your knowledge across data security, please visit this page for more details.








Great to see another amazing post!
A modern DLP, that leveraged DSPM data was the need of the hour. Glad to see Cyera take the lead!