Inside 1Password’s Enterprise Identity Transformation
How Access, Devices, and AI Are Reshaping Enterprise Identity
Overview
This report examines a blueprint for how a company can evolve from consumer password management into a credible enterprise identity security platform. We focus on 1Password because it has reached a milestone that many enterprise security vendors aspire to but rarely achieve: scaling into a large, durable enterprise business while simultaneously attempting to redefine its category.
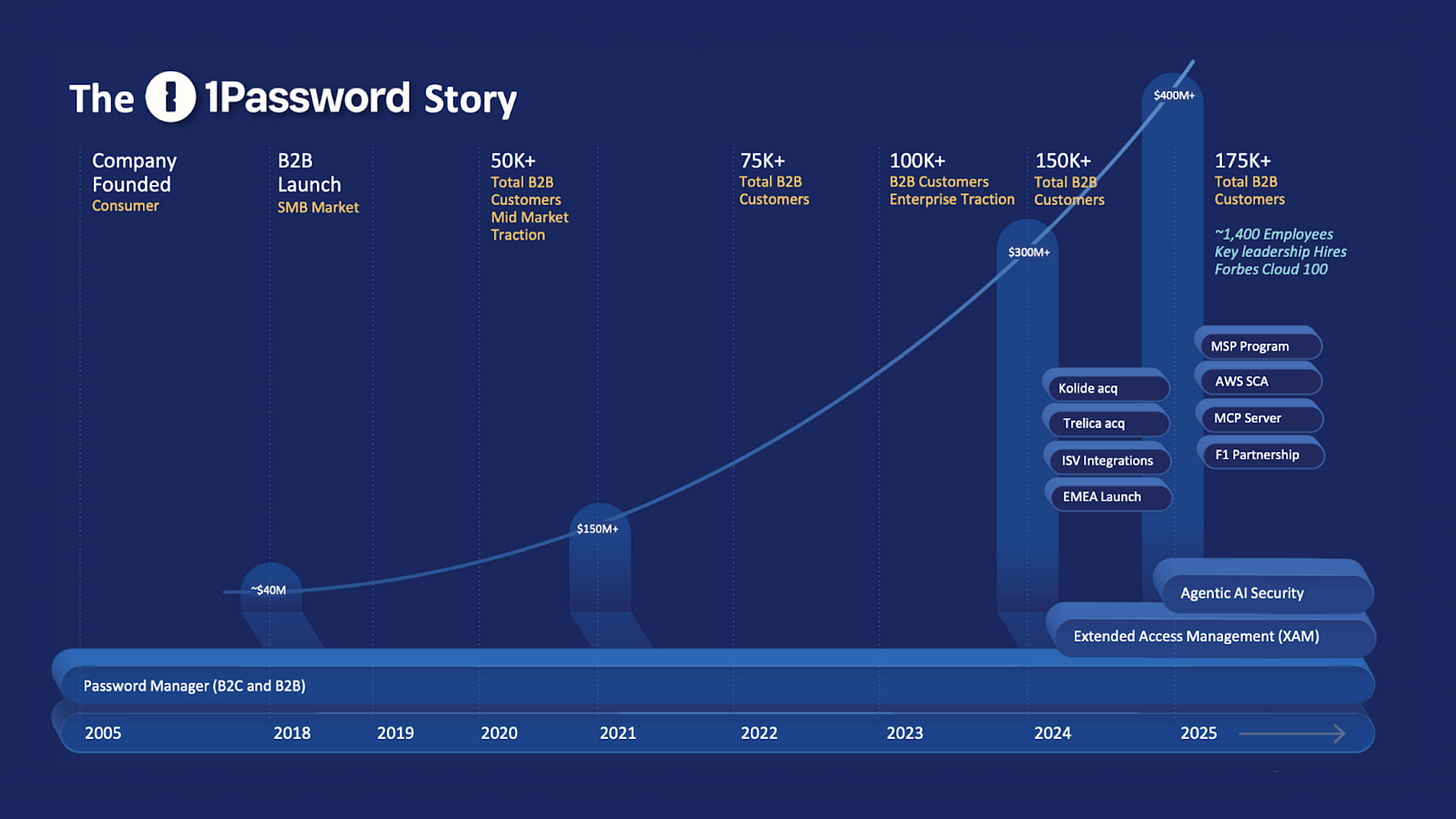
Over the past several years, 1Password has crossed a threshold that few security vendors reach quietly. The company has grown into a $400M ARR business while remaining free cash flow positive, demonstrating operational efficiency alongside scale. This combination is rare in the identity and access security market and offers a useful reference point for identity leaders navigating similar transitions. There are clear lessons to be drawn from this transformation, particularly for organizations attempting to balance growth with architectural discipline.
Today, 1Password reflects a successful maturation from a consumer-focused product into a financially robust enterprise security platform. The firm has successfully surpassed the following milestones:
$400M in Annual Recurring Revenue (ARR) while remaining free cash flow positive, demonstrating operational efficiency as it scales
More than 75% of revenue derived from enterprise customers, with a strong focus on higher-value accounts
A 70% compound annual growth rate (CAGR) among customers spending over $100K in ARR
This growth is reinforced by additional indicators of enterprise adoption and durability:
More than 180,000 business customers
Adoption across over 30% of the Fortune 100
Gross retention above 90%
Taken together, these metrics suggest that 1Password’s Extended Access Management (XAM) strategy is gaining traction as a sticky, operationally meaningful component of access security programs. More importantly, they indicate that the platform now operates at sufficient scale, customer density, and strategic ambition that its architectural choices spanning enterprise password management, device trust, SaaS governance, and emerging non-human identity access warrant closer examination.
Accordingly, this report evaluates 1Password’s platform evolution not to validate a narrative, but to assess whether its expanding role at the intersection of identity, endpoint posture, and workflow-level access reflects a durable shift in how access security is being constructed in SaaS- and AI-driven enterprises.
These metrics matter not as proof of inevitability, but as evidence of relevance: 1Password now operates at sufficient scale, customer density, and strategic ambition that its architectural choices spanning enterprise password management, device trust, SaaS governance, and emerging non-human identity access deserve rigorous, critical analysis.
This report examines platform evolution not to validate a narrative, but to assess whether 1Password’s expanding role at the intersection of identity, endpoint posture, and workflow-level access reflects a durable shift in how access security is being constructed in SaaS- and AI-driven enterprises.
Core Thesis
Over the past two decades, 1Password has evolved from a consumer password manager into a company increasingly focused on redefining how access is governed across humans, devices, applications, and, more recently, machines. This report examines that evolution through the strategic bets 1Password has made in response to structural gaps left by traditional IAM, PAM, and endpoint-centric security models.
This analysis evaluates where that thesis holds in practice, where it remains aspirational, and where execution risk is non-trivial. Drawing on customer conversations, architectural review, and broader market context, the report distinguishes between capabilities that are operationally mature today and strategies that are still forming. It also places 1Password’s platform ambitions alongside incumbent IAM, PAM, and secrets management vendors not as a wholesale replacement, but as a complementary layer that may prove valuable in environments defined by SaaS sprawl, unmanaged access paths, and emerging AI agents.
For security leaders navigating identity sprawl and access complexity, 1Password represents a credible attempt to collapse multiple control planes into a more human- and workflow-centric access model. Whether that attempt succeeds will depend less on vision alone and more on convergence, packaging discipline, and the company’s ability to translate strategic narrative into a cohesive, operational platform.
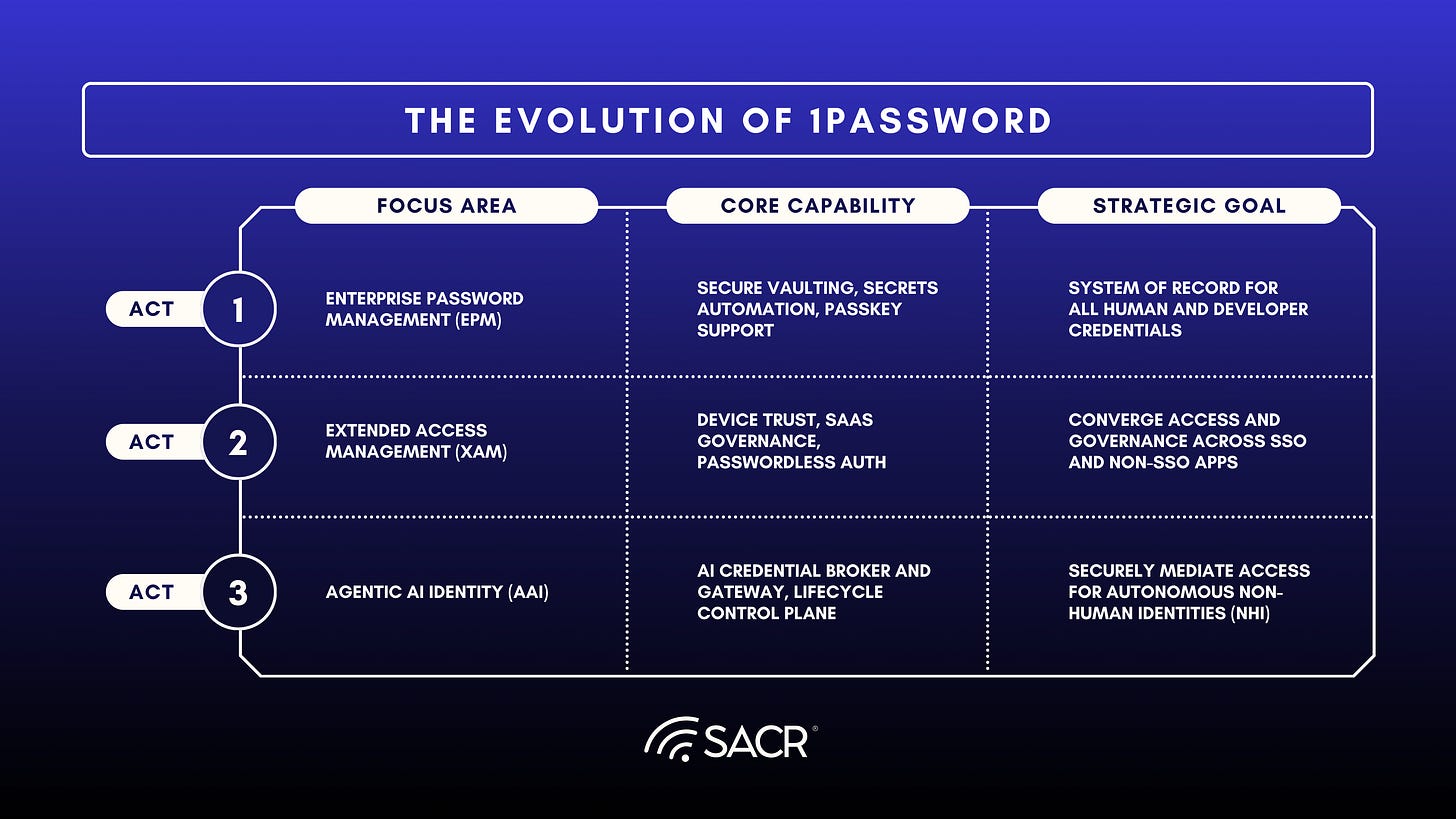
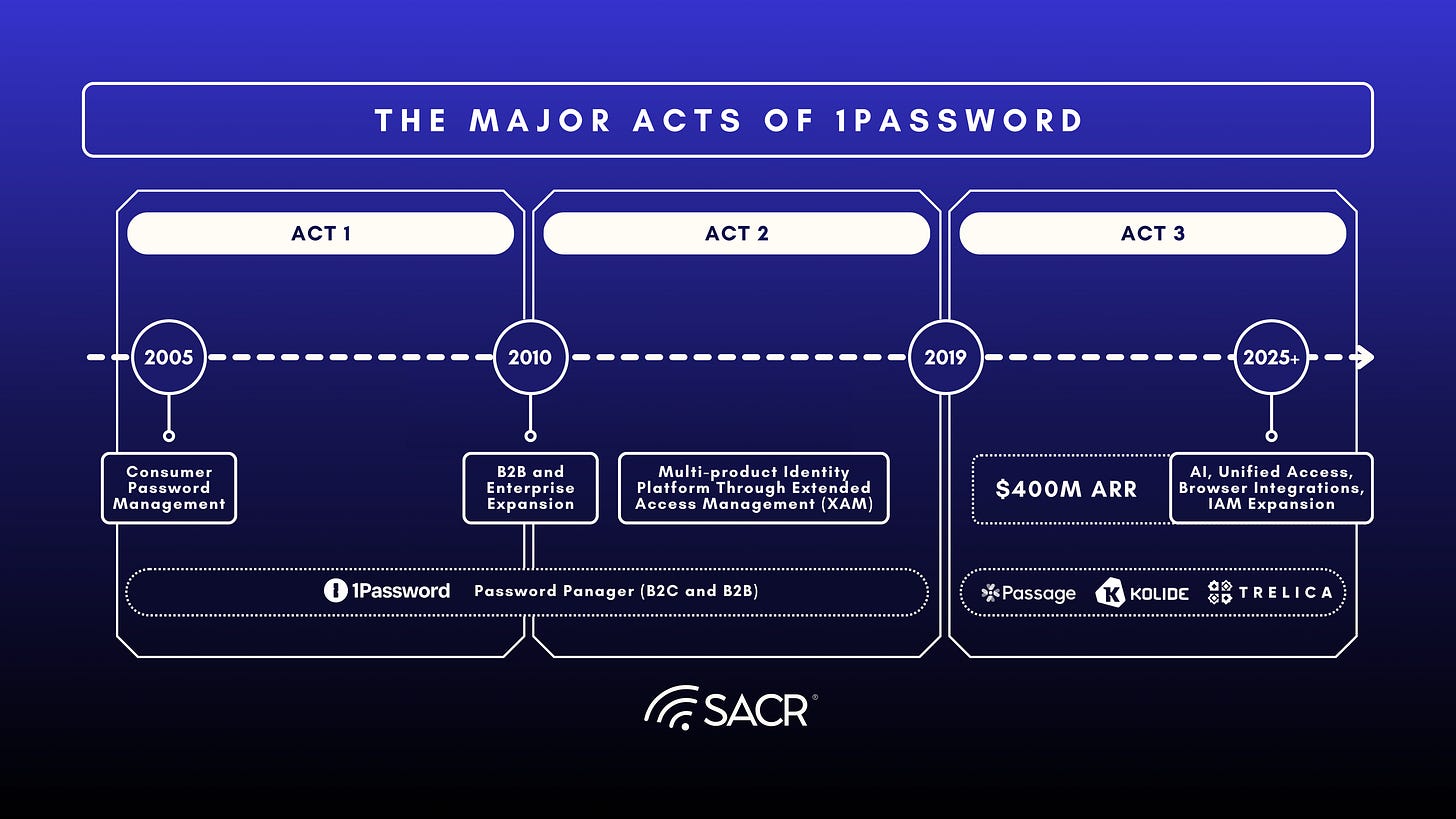
The Three Acts of 1Password
Founded in 2005 as a human-centric password vault, 1Password’s early years were shaped by a singular focus on trust, strong encryption, and ease of use. That foundation enabled the company to establish credibility with individual users before expanding its scope and ambition. Over time, this evolution can be understood as a series of distinct acts, each marking a shift in how 1Password approached access security and enterprise scale.
Act 1: This phase focused on vaulting and password management, emphasizing secure credential storage and usability. This phase culminated in 1Password’s expansion to more than 100,000 enterprise customers globally, marking its transition from a consumer product into an enterprise-grade platform.
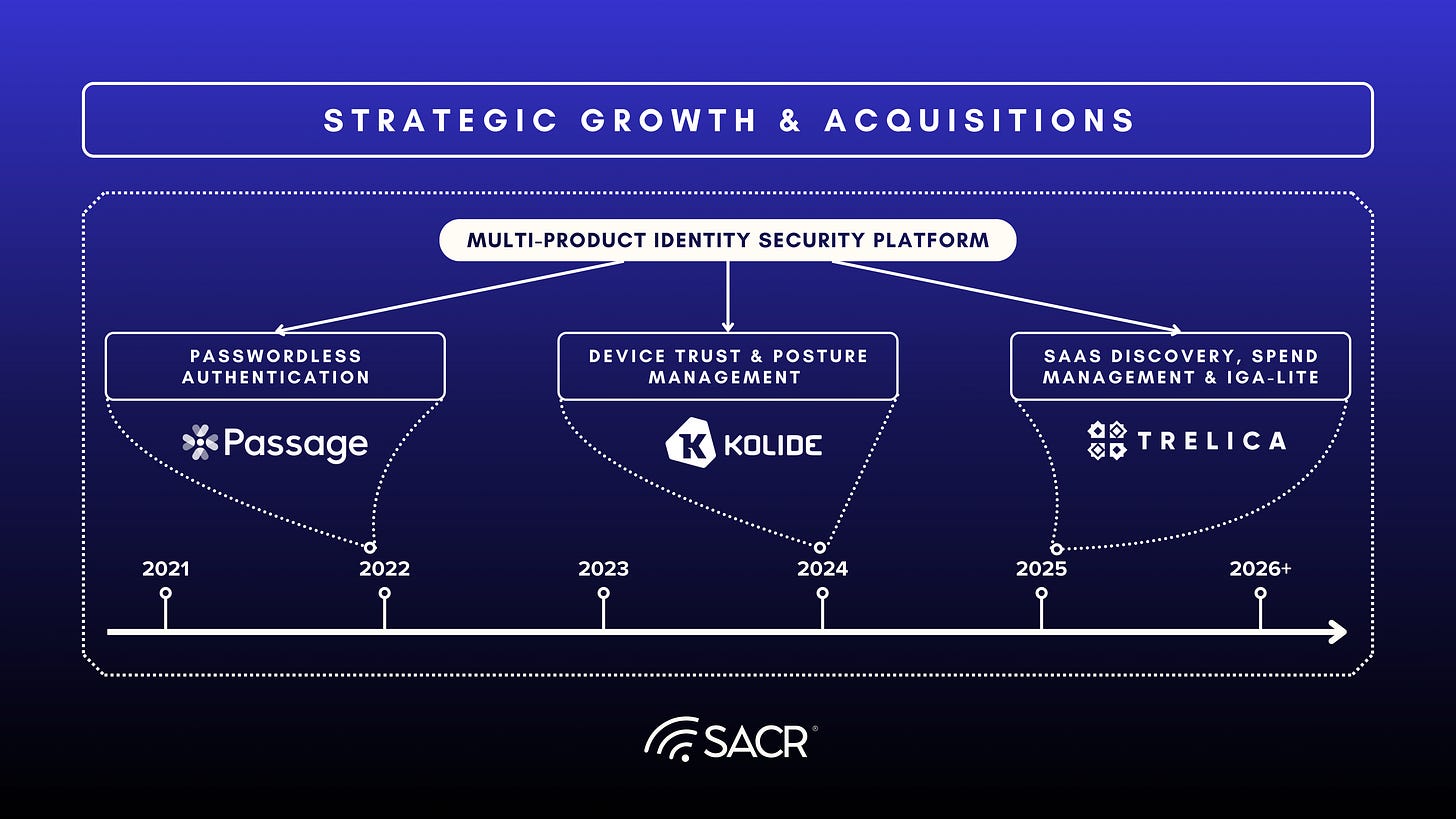
Act 2: This phase reflected a broader response to the growing complexity of digital identity. Through its Extended Access Management (XAM) strategy, 1Password began unifying password management, device trust, SaaS management, and passwordless authentication. Acquisitions including Kolide, Trelica, and Passage formed the technical foundation of this integrated identity platform.
The strategic imperative behind this shift was the need to close what 1Password describes as the “Access-Trust Gap,” the systemic risk created by application sprawl, device heterogeneity, and fragmented identity controls. Extended Access Management, introduced in 2024, represents the architectural response to this challenge. XAM is designed to converge controls where access actually occurs by unifying Enterprise Password Management, SaaS Governance, and Device Trust across both SSO and non-SSO applications, establishing a Zero Trust policy framework at the point of interaction.
Act 3: The company’s next chapter builds on these vaulting and secrets management strengths to capture emerging opportunities in AI, browser-based access, and identity management.
Act 1: Enterprise Password Management (EPM) as the foundation for a Unified Identity Security Platform
Today, 1Password’s architectural anchor is its Enterprise Password Management (EPM) core. This zero-knowledge vault serves as the singular “system of record for all workforce credentials,” spanning both human users and non-human identities (NHI), thereby establishing the essential foundation for secure vaulting and policy enforcement.
1Password offers a secure, zero-knowledge vault for encrypting and storing credentials, passkeys, API tokens, and other sensitive information for both individuals and teams. Its architecture ensures that user data remains private even in the event of a breach, as only users can decrypt their information. Core features include browser plug-ins for automatic credential filling, strong password generation, and cross-device synchronization, balancing security with usability.
Initially, 1Password succeeded by making good password hygiene accessible to everyday users, helping them move away from insecure practices such as password reuse or storing credentials in plain text.
As organizations increasingly adopted SaaS applications, the need for enterprise-grade password management became more pronounced. Employees frequently relied on personal credentials for work accounts, increasing the risk of credential reuse and security incidents. While Single Sign-On (SSO) and Multi-Factor Authentication (MFA) became standard controls, they often failed to cover the full range of enterprise applications, leaving visibility gaps that password managers like 1Password were designed to address.
Major Phase In Act 1: B2B Expansion and Enterprise Password Management
Recognizing growing demand from businesses, 1Password introduced team and enterprise plans with centralized administration, policy enforcement, and audit trails. Integration with identity providers enabled federated access management and improved visibility for IT and security teams.
Beyond standard passwords, the EPM core expanded to handle a wide range of digital identity artifacts, positioning it as a centralized repository for sensitive access material. These include passkeys, API tokens, SSH keys, authentication tokens, and secure credit card information.
Security Features for Enterprises:
As part of its enterprise expansion, 1Password added several mature capabilities to strengthen its offering for business customers:
Integration with SIEM systems such as Splunk for event streaming and alerting
Admin dashboards for policy control and credential usage reports
Support for unlocking via SSO providers (Azure, Okta, Google Workspace)
More advanced enterprise capabilities:
Developer Solutions: Recognizing the growing importance of developer velocity and the risks associated with secret sprawl, 1Password expanded into DevOps. The acquisition of SecretHub in 2021 enabled the launch of Secrets Automation, providing a centralized system for managing and retrieving secrets required by applications and infrastructure. This capability supports secure storage and retrieval of API tokens, SSH keys, and infrastructure secrets directly within developer workflows, with integrations for IDEs such as VS Code and a command-line interface (CLI).
1Password Shell Plugins: These plugins enable seamless authentication to third-party CLIs without manual credential input. Developers can build and share plugins through an open-source community, extending the platform beyond its original consumer use cases.
Master Key Password: The master password functions as each user’s root key and is never stored on 1Password’s servers. All encryption occurs locally, ensuring that only the user can decrypt their data. This architecture reinforces a user-first security model and deepens trust.
Security Watchtower: Security Watchtower continuously scans for exposed credentials associated with known breaches. It alerts users when stored credentials are compromised and provides remediation guidance, shifting 1Password from a passive storage tool into an active participant in user security posture.
By the end of this phase, 1Password had established mature capabilities across breach monitoring, login autofill, passkey and API key storage, authentication token handling, and secure credit card storage. Together, these capabilities positioned the company as a trusted enterprise security vendor managing credentials for more than 180,000 organizations.
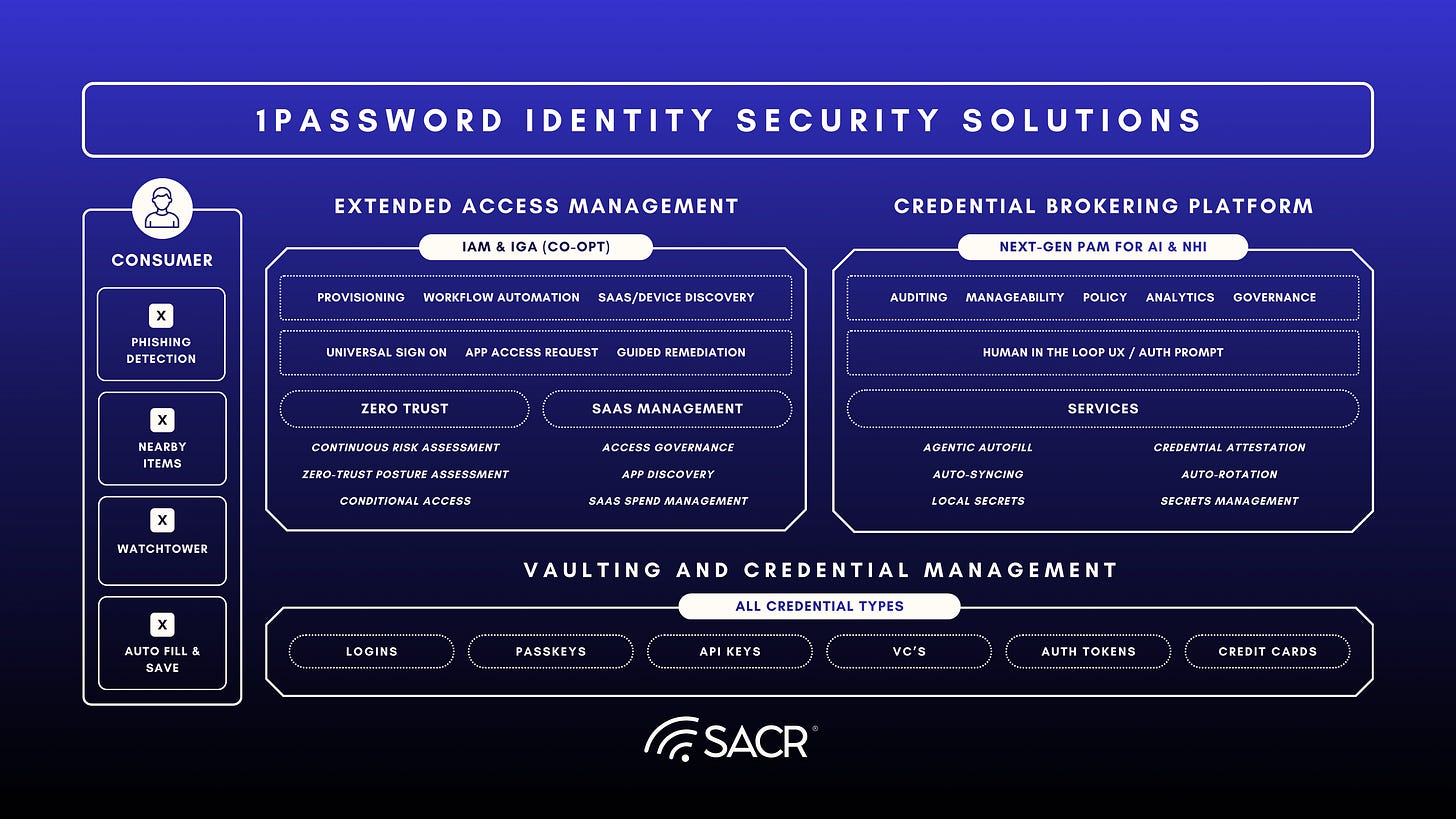
Act 2: Extended Access Management (XAM); Unifying Access and Governance
As the market matured, 1Password recognized that password management alone was insufficient to address the realities of modern enterprise access. This recognition drove the expansion toward comprehensive access security, resulting in a set of capabilities designed to address persistent customer challenges around passwords, vaulting, and device-level assurance.
Traditional IAM systems often struggle with real-world complexity. Unfederated identities, unmanaged devices, and unsanctioned applications create enforcement gaps across the enterprise. 1Password’s Extended Access Management (XAM) vision is intended to close these gaps by unifying password management, device trust, SaaS governance, and conditional access within a single platform. This represents a shift away from isolated point solutions toward an integrated model for securing access across devices, applications, and identities.
The Emerging XAM Platform
Kolide, Trelica, and Passage collectively form the backbone of 1Password’s Extended Access Management (XAM) platform. Together, they create an integrated system designed to unify password management, device trust, and SaaS governance under a single identity-aware framework. While the platform continues to evolve, XAM represents a clear transition toward a multi-product identity security strategy.
Core Principles of XAM
Unified identity and access policies
Real-time device posture verification
Integration with both SSO and non-SSO apps
Centralized governance and visibility
XAM represents a move toward a “trust fabric”, where every credential, device, and application interaction is verified and governed under a consistent policy engine. The long-term objective is to converge conditional access, SaaS governance, and device trust into a seamless experience for both users and administrators.
A unified dashboard would enable consistent policy enforcement across endpoints, support contextual authentication, and simplify operational management. In this model, 1Password positions itself as a central platform for Extended Access Management across both human and non-human identities.
Pillar 1: Device Trust and Posture Management (1Password Device Trust)
The technology acquired through Kolide formed the core of 1Password Device Trust, shifting access control from static identity checks to real-time, conditional enforcement. This capability ensures that access decisions consider both the user’s identity and the health/compliance of the device attempting access.
Device Trust relies on an osquery-based agent that continuously evaluates more than 100 predefined health and compliance signals across both managed and unmanaged devices. Enforcement is delivered through Extended Device Compliance, which uses the 1Password browser extension to act as a gatekeeper. When a device is non-compliant, access to web applications (both SSO-protected and non-SSO) is blocked, and the user is guided through a structured self-remediation flow.
This user-centric remediation model has emerged as a meaningful differentiator, validated by customer feedback for reducing IT support burden while preserving policy rigor. The platform’s ability to extend enforcement across the entire application portfolio, particularly non-SSO applications, closes a significant blind spot that traditional identity tools often leave unaddressed.
Pillar 2: SaaS Access Governance and IGA-Lite (1Password SaaS Manager)
The acquisition of Trelica, now branded as 1Password SaaS Manager, extended the platform into lightweight Identity Governance and Administration (IGA-lite). This capability addresses application sprawl and the security risks associated with shadow IT, where unsanctioned SaaS applications proliferate outside traditional identity controls.
SaaS Manager integrates with more than 350 systems, including identity providers, finance tools, and browser agents, to continuously discover sanctioned and unsanctioned SaaS applications, including emerging AI services. It provides essential IGA-lite capabilities across the employee lifecycle, such as automated access reviews, streamlined onboarding and offboarding, and license optimization through usage tracking.
These governance capabilities also generate the audit trails required to support compliance frameworks such as SOC 2.
Pillar 3: Passwordless Authentication (Passage)
The acquisition of Passage provided the foundational technology for WebAuthn and passkey orchestration, positioning the company as a leader in the shift to passwordless authentication.
1Password’s implementation addresses a key obstacle to enterprise-wide passkey adoption: shareability and synchronization. The platform allows users to securely store, sync, and share passkeys across devices and teams via shared vaults, eliminating credential chaos while maintaining centralized, granular policy control.
Additionally, the earlier acquisition of SecretHub (2021) enabled the launch of 1Password Secrets Automation for DevOps credential management, extending its reach into developer operations.
Voice of the customer
As part of this analysis, SACR spoke directly with 1Password customers to understand how the platform performs in real-world enterprise environments. The following perspectives highlight recurring themes across adoption, operational maturity, and platform integration.
OpenTable
From OpenTable’s vantage point, 1Password has evolved from a “useful password vault” to a credible foundation for a broader access posture. However, the platform still feels like two strong products running in parallel rather than a single integrated system.
OpenTable adopted 1Password to bring order to what it described as a “wild west” of browser-based secrets, standardizing on the vault approximately four to five years ago through a company-wide rollout. The organization continues to run Delinea Secret Server for certain infrastructure credentials and HashiCorp Vault for production secrets, with plans to migrate remaining Delinea usage and reduce reliance on built-in browser vaults.This bifurcation reflects a common enterprise pattern: 1Password excels in human-centric secret handling and cross-team vault hygiene, while automation-heavy, machine-to-machine secrets remain managed through infrastructure-native platforms such as HashiCorp Vault.
On operational maturity and vendor posture, OpenTable’s Corporate IT leaders describe 1Password as a disciplined software company with responsive incident handling, strong customer engagement, and a willingness to help customers maximize value from the platform. Integrations are central to perceived value, with Okta support, particularly group-based controls and SCIM, cited as essential for governing private and team vault access.
At the same time, OpenTable views 1Password Vault and XAM as distinct products with meaningful seams. While optimistic about convergence, the team is pragmatic that password management and posture enforcement are separate disciplines that require careful integration rather than surface-level unification.
Finally, the customer noted that packaging matters. An independent XAM SKU was viewed as attractive for organizations seeking posture enforcement without paying for vaulting in environments where infrastructure-native tools already manage machine secrets. Notably, OpenTable is currently the only Booking Holdings brand using XAM, suggesting that clearer packaging and messaging could unlock broader adoption across related business units.
Overall, OpenTable’s experience suggests that while 1Password has earned the right to expand its platform, success will depend on reducing operational friction, such as reliance on SCIM Bridge and delivering high-leverage capabilities at the identity-endpoint intersection, including endpoint-level PAM, an enterprise browser with integrated controls, and AI-assisted fleet intelligence.
If 1Password makes those moves while preserving its maturity and customer empathy, OpenTable’s trajectory indicates that 1Password can play a differentiated role alongside, not necessarily instead of, the infra-native secrets stack that modern enterprises already trust.
MixMode Customer
From MixMode’s vantage point, 1Password’s value proposition begins with pragmatic compliance and quickly extends into everyday operational trust with some seams still showing in support and packaging. MixMode implemented 1Password’s core vaulting ahead of hiring its first IT leader to satisfy SOC 2 requirements, a common enterprise on-ramp that rewards reliability over flash. Post-hire, the company layered in Kolide (now 1Password XAM) to enforce device trust at the moment of access, not because identity wasn’t already central, but because identity absent device assurance was considered an unacceptable gap as MixMode began serving large, high-stakes customers. In effect, the vault solved “who has the secret and how it’s handled” while XAM solved “what is the state of the device that’s asking for access,” which is precisely where many mid-market security programs stall. That MixMode runs a remote, fully corporate-owned device fleet with immediate device management enrollment made XAM’s posture-centric design a natural fit. On day-to-day experience, two design choices resonate. First, the end-user self-remediation model changes the support dynamic. The IT leader initially discounted it as “nice to have,” then came to appreciate how structured, guided fix paths reduce tickets when something drifts out of policy.
Integration posture is steady but not seamless. MixMode uses Okta as its IAM backbone and combines FastPass biometrics with XAM’s device checks to achieve a layered assurance model without purchasing Okta’s pricier device trust SKU. In practice, FastPass offers user-friendly biometric gates while XAM governs the rich posture baseline and policy rigor. Post-acquisition, MixMode sees progress, notably browser-based compliance for non-Okta apps and group-sharing connective tissue, but stops short of calling the combined experience a “single product.” That’s credible: identity and device posture are distinct disciplines, and merging them meaningfully takes more than shared branding. The non-SSO coverage is a real win in the messy middle of enterprise portfolios, where cost, vendor support, or narrow usage prevents SSO everywhere. Still, MixMode’s strategy remains to pull as much as possible into Okta over time, using XAM as the safety net where SSO is not viable.
Strategically, MixMode’s overall security philosophy underscores why 1Password’s trajectory toward “identity plus endpoint assurance” is resonant. Net-net, MixMode’s experience suggests 1Password’s platform is moving in the right direction: vaulting that satisfies compliance with minimal overhead, device trust that aligns with zero trust realities, and emergent integrations that extend coverage to the messy, non-SSO perimeter. Turning those parallel strengths into a tighter, more opinionated platform with fewer operational footnotes is how 1Password can stretch its advantage in identity-era access security for resource-constrained but risk-aware teams.
Voice of the Customer (VoC) Analysis: Operational Friction and Platform Maturity
Feedback from enterprise customers confirms the strategic value proposition: the EPM vault is viewed as mature and reliable, and XAM components, specifically 1Password Device Trust, provide the necessary endpoint assurance to meet Zero Trust and compliance mandates (e.g., SOC 2). The UX of guided self-remediation for device health is a key differentiator that measurably reduces IT support overhead.
However, the analysis of customer experience reveals key areas of friction that must be addressed to maximize platform leverage:
Integration Seams: The XAM components currently exhibit “meaningful seams,” which prevent the system from being perceived as a single, cohesive “trust fabric.”
SCIM Bridge Drag: The SCIM Bridge appliance requirement remains a source of operational drag for resource-constrained, cloud-first teams.
Customer Demands: Next-phase demands focus on closing last-mile security gaps: Endpoint PAM (Local Admin Rights Management), enterprise browser controls, and enhanced, AI-assisted Osquery reporting
Summary
Across OpenTable and MixMode, 1Password earns trust as a mature, reliable vault that standardizes human-centric secrets while Kolide/XAM adds the missing device posture needed to make identity the true perimeter. Both lean on Okta and value policy granularity and end‑user self‑remediation to reduce ticket load, with osquery providing useful investigative depth. The seams show up in similar places: SCIM Bridge remains operational friction for cloud-first teams, support responsiveness dipped post‑acquisition, and Vault and XAM can still feel like parallel products.
Customers consistently ask for next steps that converge identity and endpoint: endpoint‑level PAM to control local admin and close last‑mile gaps, an enterprise browser tightly integrated with vaulting and enterprise controls, richer out‑of‑the‑box osquery reporting with AI‑assisted insights, and packaging flexibility such as an independent XAM SKU. On the vault side, finer‑grained sharing that keeps credentials in sync outside of full vault membership would remove common workflow pain.
The voice of the customer is clear: keep the maturity and UX, reduce operational drag, and deliver opinionated capabilities at the identity‑device boundary to unlock platform leverage without forcing tool sprawl.
Act 3: Agentic AI Access Management (AAM): Securing Non-Human Identities (NHI) & Agents
Act 3 represents 1Password’s most forward-looking strategy: establishing itself as the identity layer for machine intelligence. This involves a direct confrontation with the challenges posed by autonomous software agents, which constitute a fundamentally new class of non-human identities (NHI) that legacy access management tools were not designed to govern.
1Password has the opportunity within the identity security layer for machine intelligence, positioning it to disrupt legacy PAM by securing the access requirements of autonomous software agents, a new and highly dynamic class of Non-Human Identities (NHI).
The Challenge: NHI and the Access-Trust Gap
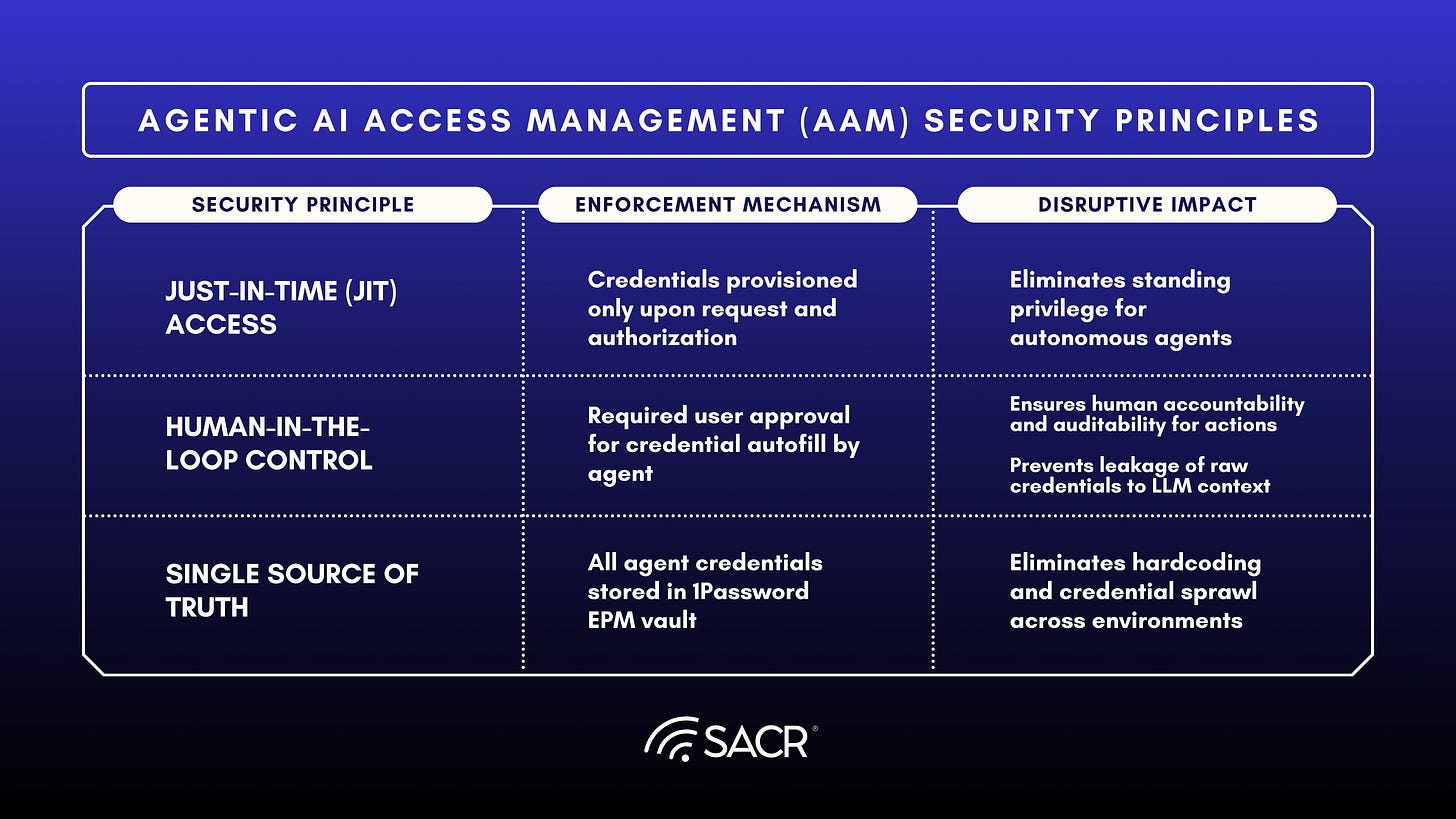
The proliferation of Agentic AI creates identity sprawl and a critical access gap. AI agents operate probabilistically, needing access to internal systems via credentials (passwords, API keys) often designed for human use. Since existing access solutions were not designed for dynamic, probabilistic machine identities, developers risk hardcoding secrets, leading to over-privileged agents and minimal auditability, a recipe for data loss, as 80% of unauthorized AI transactions stem from internal misuse or misconfiguration.
Agentic AI Credentials Broker (AICB)
Agentic AI Credentials Broker (AICB) is designed to secure and govern AI agents with the same zero-knowledge rigor applied to human identities. This capability, launched in April 2025, is built on the core EPM foundation.
The first practical application is Secure Agentic Autofill (SAAF), which directly addresses the credential risk for agents that mimic human browser use, such as those running in headless browsers. We can categorize them as:
AI credentials vaulting and management: What we have today with EPM including how we can enable developers
AI credentials broker and gateway: Future state of what is possible for end-point, browser and programmatic agents
Some real world case studies:
1Password Real-World Validation with Browserbase AI: 1Password recently signed a new partnership with Browserbase AI that validates the SAAF model by integrating the 1Password browser extension directly into the Comet browser, a personal AI assistant. This allows the AI assistant to perform actions (like booking reservations) using the user’s vaulted credentials. Crucially, the credentials are delivered via an end-to-end encrypted channel, protected by the Noise framework, ensuring that raw secrets are never exposed to the AI model or Browserbase servers. 1Password also has a basic extension integration partnership with Perplexity AI.
Zero Standing Privilege (ZSP): SAAF enforces a ZSP model by providing credentials Just-in-Time (JIT), only when access is required. While the default is human-in-the-loop authorization, going forward, we will also support policy-based asynchronous workflows. This approach minimizes the exploitable surface area and provides essential human or policy accountability for autonomous actions.
The Agent Lifecycle Control Plane
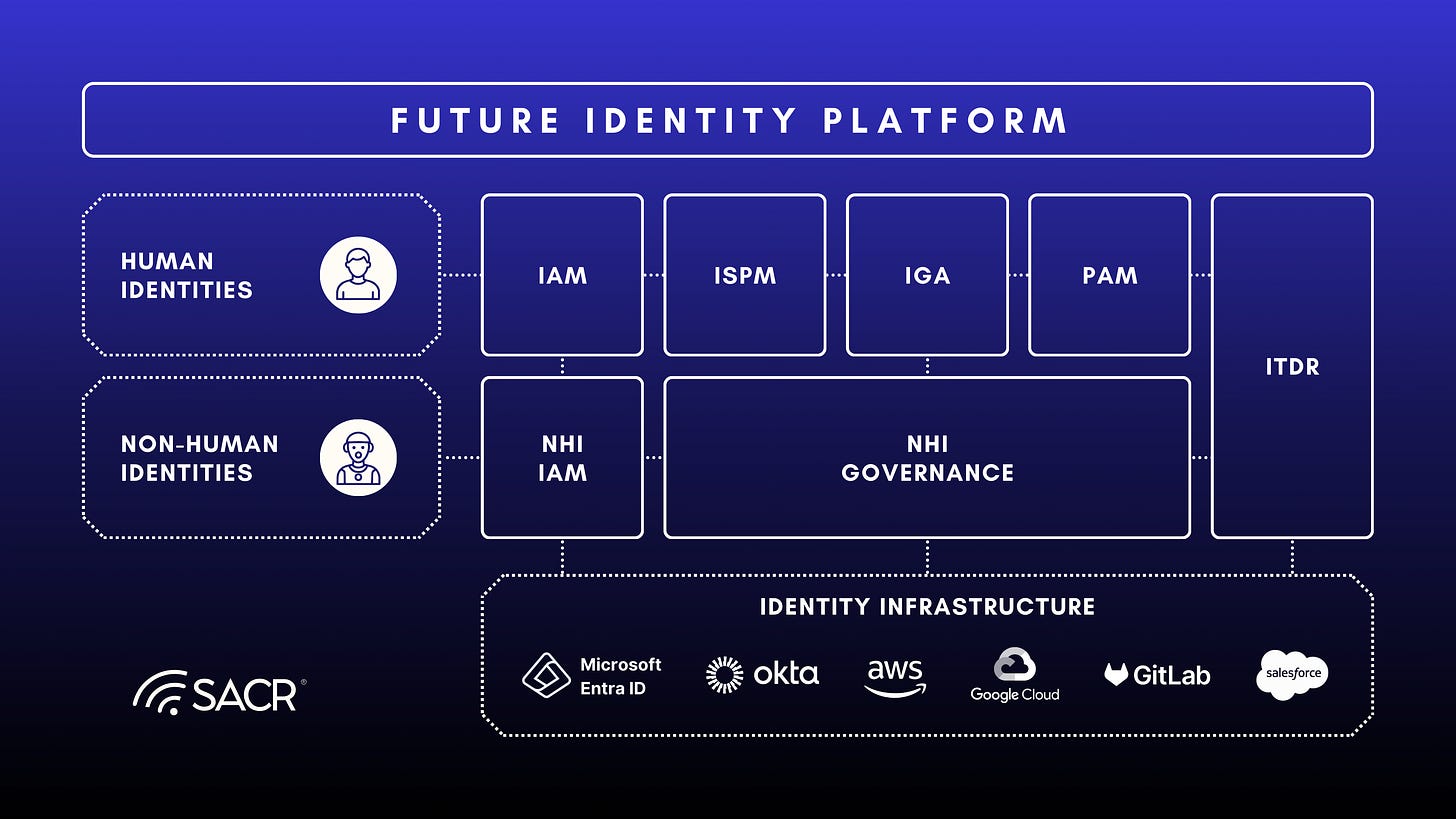
To manage the complexity of NHI, 1Password is building an Agent Lifecycle Control Plane that spans discovery, identity, credential management, authentication/authorization, and governance. The platform classifies agents based on interaction type (Browser-based vs. Programmatic), location (Remote vs. Local), and authority (Employee, Company, or Customer) to guide the application of appropriate security measures.
This architecture is fundamentally more agile and secure for dynamic AI agents than the heavyweight, session-brokering design of legacy Privileged Access Management (PAM) systems, positioning 1Password to define the NHI security segment.
Future plans include developing a dedicated, self-hostable AI Credential Gateway to broker programmatic requests, further challenging legacy secrets management and PAM tools for control over high-value machine access points.
Essential Table: Agentic AI Access Management (AAM) Security Principles
Market Positioning Within Identity Security
1Password’s evolution places it as a differentiated competitor in the identity security market, defining a complementary but aggressive position against established Identity and Access Management (IAM) and Privileged Access Management (PAM) incumbents.
Competitive Landscape: Differentiation in Access Control
1Password XAM is designed to capture the gaps left by traditional vendors, providing a unified approach to the entire access surface:
Vs. IAM/IdP Platforms (e.g., Okta, Entra ID): XAM functions as a critical extension layer. While IdPs manage federated access, XAM provides universal access governance by enforcing conditional policies against all applications (SSO and non-SSO) and providing real-time device posture assurance that MDM/IdPs often lack.
Vs. Legacy PAM (e.g., CyberArk, Delinea): Legacy PAM excels at high-assurance brokering for critical systems. 1Password’s strategic move into AAM, particularly with its JIT and ZSP model for dynamic AI agents, positions it to disrupt the lightweight end of the PAM market by offering a simpler, developer-friendly solution optimized for non-human identity at scale. User reviews consistently cite 1Password’s superior ease of setup and policy enforcement compared to legacy PAM solutions.
Vs. IGA Platforms (e.g., SailPoint): The 1Password SaaS Manager provides essential IGA-lite functions (discovery, lifecycle management) that suffice for mid-market and resource-constrained teams, or serve as a foundational data layer for larger IGA systems in the largest enterprises.
Conclusion
1Password’s transformation from a consumer password manager into a multi-product identity security platform demonstrates remarkable strategic evolution. Its acquisitions, technical innovations, and expansion into enterprise-grade capabilities reveal a clear intent: to unify password management, SaaS governance, and device trust under one cohesive system.
The company now stands at a pivotal point. The next phase should focus on unifying the XAM experience, deepening partnerships in IAM and AI security, and expanding its influence through developer ecosystems and browser integrations.
With disciplined execution and continuous innovation, 1Password is well positioned to become a leader in identity security for both humans and machines bridging the access-trust gap across devices, apps, and intelligent agents in the years ahead.




I’ve personally used 1Password as a password vault, but this report clearly explains how its identity security model actually works and how it compares with other solutions. Clear, and so well written!
This is very comprehensive. Especially loving the narrative framing here!