No Vendor Consolidation In The SOC
The case for a modular security architecture within the modern SOC instead of a consolidated approach
Introductory Blurb
Since I published my last co-authored reports on the security data platform and SOC automation market, some interesting developments have occurred in the SIEM market. It is well-known news about the recent consolidation happening Palo Alto Networks’ acquisition of IBM’s QRadar, Crowdstrike's announcement of their full SIEM platform, and the LogRythmn & Exabeam merger to become one platform. Adjacently, Zscaler with its Avalor acquisition, Fortinet’s SIEM product and more I could list on. All the major cybersecurity players are making a conscious effort to move into the SOC.
What if there is no complete vendor consolidation within the SOC? i.e., no one platform that can provide all the technology requirements across the SOC. Could the Crowdstrike outage become the impetus for the tide to turn back? We’ll explore that hypothesis today.
While I do believe other areas of cybersecurity need consolidation, like SASE, Identity access and management, cloud, and app sec, the paradigm will be different within the SOC. We’ll discuss the implications of these developments and explore the pros and cons of a consolidated SOC relative to a best-of-breed SOC. My post was also inspired by reading Umesh Yerram’s piece, a prominent CISO who writes about the implementation of the modular cybersecurity stack and works by Omer Singer.
I have always believed that vendor consolidation would happen across different cybersecurity markets and industries, but I’m increasingly convinced that within the SOC, we won’t likely have one major platform—at least anytime soon. The recent issue with Crowdstrike points to a case where security leaders would be less hesitant to purchase their entire stack on one vendor to avoid such scenarios from happening in the future.
Thesis
My thesis is that nobody has fully built the complete SOC technology platform that covers all areas where one large platform dominates the market, providing a unified system from data pipeline, data ingest, analytics, and autonomously responding to threats. The large vendors are incentivized to pitch this all-in-one strategy. However, I believe we will have “modular consolidation within the SOC” ie. a SOC stack where companies have modular solutions that fit the requirement for their security needs. They pick the best solution for XDR/SIEM, automation or data pipeline etc.
Most of this premise comes from the fact that we still don’t have a successful all-in-one SOC company. We can acknowledge that Splunk is dominant today in the SIEM market, but it is a well-known fact that Splunk is hated, and it is likely in decline over the next few after its recent acquisition by Cisco. Similar to how successful companies like Crowdstrike have built a name for themselves in endpoint (yes, despite everything happening), Wiz in cloud security, Okta in identity etc. It’s likely we won’t have a top name for the SOC market for a long time.
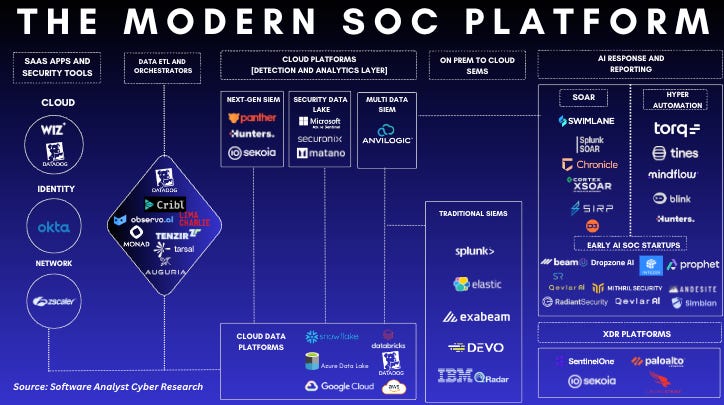
Below is the market map I created to illustrate how, in today’s SOC, companies gravitate to the best-of-breed solution for each of the major pillars below. The fragmented nature of the SOC will likely remain this way for a long time. We’ll explore some of the reasons much more in the piece.
Torq Technologies: My talk on the SOC automation market
I had a conversation with Torq about the evolution of the SOC automation market. I discussed some findings on how automation and AI are meant to change the SOC over the next few years. Read the full article here:
Exploring the Future of SOC Automation with Francis Odum. Alternatively, you can watch the full video below.
Today’s Sponsors:
Every once in a while, I meet with new vendors where I’m pleased with their products. A big shoutout and thank you to Intezer and Sekoia for sponsoring the software analyst newsletter.
Intezer is an autonomous SOC platform built to analyze, reverse engineer, and investigate every alert like an experienced security. Intezer’s objective is to fully automate the tasks of Tier 1 SOC Analysts, extending the capacity and capabilities of analysts to comprehensively triage every alert and prioritize the critical threats. This ultimately helps fill in the talent shortage that is plaguing many security teams.
Sekoia.io is a threat intelligence-powered SOC platform that provides Extended Detection and Response (XDR) and SIEM solutions based on Cyber Threat Intelligence (CTI). Their solutions enhance modern SOCs' collaboration, productivity, and protection against cyberattacks. Sekoia is a platform that aims to exemplify this new breed of cybersecurity solutions, as they are poised to become the future of SIEM, SOAR, and a threat intelligence platform (TIP) by evolving into comprehensive SOC platforms.
The Basics Behind The SOC
History
The SIEM/SOC market has undergone many transitions over the years from Arcsight to Splunk and all the way to emerging native solutions on the market. There has been no shortage of solutions available for businesses with the need to store data

If we drill down to the basics, the primary purpose of a Security Operations Center (SOC) is to continuously monitor, detect, analyze, and respond to cybersecurity incidents and threats within an organization. It acts as the central hub for security and utilizes various technologies to detect and respond to security threats. Some of the core technologies utilized include SIEM, SOAR, EDR, NDR, CASB, VM, IAM, TIPs, and UEBA. Most SOCs have endpoint security at the heart of their technologies, and many of these solutions continuously monitor suspicious activities at endpoints and across the network.
At the heart of the SOC is the SIEM. As I wrote in my previous piece, the core premise behind a SIEM is to collect data, analyze it, and send an alert based on detection rules. SIEM systems aggregate, analyze, and correlate security event data from various sources within an organization to detect, monitor, and respond to security threats in real-time. They provide centralized visibility and facilitate incident response by identifying unusual or suspicious activities.
The final output of the SIEM is always handled by a security automation solution. When an SIEM detects an incident across any of your security tools, it triggers a SOAR/automation solution to automate certain response actions based on predefined playbooks. For example, the SOAR/hyperautomation platform can automatically initiate protocols to change passwords or shut down accounts if unauthorized access is detected.
Today’s Paradigm
Security tools have significantly changed over recent years. We’ve seen the market's rapid evolution over the last few years. More and more vendors have emerged within the SIEM space, and many have died along the way. Many of the leading providers ranked in Gartner’s 2024 Magic Quadrant for SIEM have undergone significant organizational and business changes in recent months. We’ll likely see more M&A activities of vendors merging to become stronger players.
While this happens, the SOC's tool stack has massively expanded. We now have modern enterprises struggling with ingesting and storing massive data volumes while trying to balance associated costs. Most enterprise systems don’t allow for scalable data ingestion without exponential cost increases, making organizations decide between managing costs and financial constraints. There is almost a cost-productivity curve where customers have to manage their scale relative to the ingest cost of available data. This complexity in price and a wide spectrum of data points has led to the rise and success of companies like Cribl and Anvilogic, which play a key role in managing security data before it reaches the SOC.
Commentary on the large SOC platforms
Crowdstrike
Crowdstrike is proposing to have this fully all-in-one platform. They announced their full AI-native SOC platform at the RSAC conference. The platform builds upon its original SIEM/log management platform, which it started after its initial acquisition of Humio. With its recent announcements, Crowdstrike has added a solution that incorporates more AI workflow automation to the existing alerts generated from the endpoint/cloud data it already gets.
They announced several enhancements to their platform. They have improved rapid data ingestion, including better connectors for AWS, Azure, and GCP, along with automated data normalization using advanced AI for accurate detection and response. They also integrated Charlotte AI, a generative AI security analyst that provides solutions in plain language and automates investigations, offering 150x faster search and 80% lower costs. New promptbooks and the Falcon Fusion SOAR UI also enhance workflow automation, streamlining detection, investigation, and response for better data handling and quicker reaction times.
Crowdstrike’s edge in the SIEM battle
A key feature of Crowdstrike’s Falcon Next-Gen SIEM is its single-agent, single-platform architecture that unifies native and third-party data. It is widely known amongst SOC teams that endpoint/EDR data is one of the largest datasets that SOC teams have to deal with when utilizing a SIEM. Crowdstrike’s bet is that they can get customers to point some of that endpoint data into their newly built SIEM. Endpoint data can also be complex to handle, requiring sophisticated engineering to handle edge cases, reduce duplicates, and more. Crowdstrike announced a system that leverages AI to automate data parsing and normalization, which enriches data to better identify and prioritize threats and support advanced threat detection and automated response mechanisms. They plan to incorporate their Fusion SOAR automation solution to complete the respond and remediation for their SIEM. As one of the largest EDR vendors and adding the right enhancements, they stand to benefit from easily migrating customers using those same endpoints to point some of that data into their SIEM solution.
Palo Alto Networks
Palo Alto Networks has the closest product to a fully consolidated product across having an endpoint agent to a security data lake and a SOAR when they acquired Demisto almost five years ago. To further beef up its, SIEM solution in a strategic pivot, Palo Alto Networks (PANW) acquired IBM's QRadar. This acquisition marks a change from PANW’s recent focus on acquiring bleeding-edge technologies to fill gaps in its platforms. Instead, PANW is making a swift move to secure market share.
The acquisition positions PANW as a top 3 vendor in the SIEM/Security Analytics market, projected to exceed $20 billion by 2026. QRadar, historically commanding a 12% market share, enhances PANW's standing significantly. The collaboration aims to transition QRadar on-prem/SaaS customers to PANW's Cortex platform (XSIAM), already recognized as a leader in XDR. PANW estimates a total contract value (TCV) opportunity exceeding $2 billion from this migration. IBM’s QRadar assets, including QRadar SOAR and Randori Recon, will now be under PANW’s umbrella. This integration is expected to accelerate PANW’s market penetration, akin to gaining a speed boost in a race.
PANW’s Cortex XSIAM, introduced in early 2022, stands to benefit greatly from this expanded customer base. One of the biggest benefits is that this partnership will transform IBM into a PANW reseller and integration partner, with 1,000 IBM consultants trained on PANW products to handle non-strategic tasks. This acquisition and partnership highlight PANW’s strategic maneuvers to solidify its position in the SIEM market. Leveraging IBM’s established customer base and technological assets, PANW aims to enhance its Cortex platform.
Evaluating The Case for SOC Consolidation
Crowdstrike and Palo Alto Networks are naturally pushing this incentive to drive more vendor consolidation in the SOC as outlined above. The story of 2024 has been about the urgency around vendor consolidation. Naturally, this is a push amongst leading vendors. In this scenario, a vendor chooses to combine most of its platforms with one vendor. In most cases, the vendor sends all its data to this SIEM and builds its SOAR, XDR, threat intelligence, cloud logs, and other products around the vendor. This is a strategy that the leading large vendors push.
Some of the pros
Simplified Security Infrastructure: Integrating security tools into a single platform simplifies the security infrastructure, reducing the number of tools and vendors that security teams need to manage. This “single pane of glass” approach streamlines operations and minimizes complexity in contracts, relationships, and integration efforts.
Enhanced Context to Alerts: Unified platforms often come with extensive threat intelligence data, providing security analysts with richer context for alerts generated by the SIEM (which might reduce alerts). For example, a company like Palo Alto Networks, which has existing cloud and network security portfolios, can correlate and offer broader visibility across various security domains, enhancing its threat detection and response capabilities.
Centralized Management: Deploying a SIEM typically involves installing agents on multiple systems. Having a single vendor manage these sensors centrally can streamline deployment and management, improving efficiency and reducing overhead.
Some of its disadvantages
Vendor Lock-In: Relying on a single vendor for multiple security solutions carries the risk of vendor lock-in. If the organization becomes dissatisfied with the vendor or if the vendor experiences issues (e.g., outages - best example is the issue currently with Crowdstrike), switching vendors can be challenging and costly due to the deep integration of systems and data dependencies.
Reduced Customization and Flexibility: Large vendors often design their platforms for broad market appeal, which may limit customization and modularization options. Integrated solutions can become complex and bloated with unnecessary features, making them cumbersome and harder to manage for organizations with specific needs.
Increased Costs Over Time: While initial integration may offer cost benefits, vendors may increase prices over time, particularly for managing data ingest costs around compute and storage. The centralized power of platforms like Splunk can lead to higher costs as usage scales. See this Microsoft example here with Microsoft Sentinel vs Google Chronicle debate.
Industry-Specific Requirements: Different industries have unique security requirements. For instance, heavily regulated sectors like finance and insurance may prefer legacy SIEM solutions with centralized approaches, whereas consumer-focused enterprises might need more modular and flexible SOC setups. Integrated platforms may not cater equally well to these diverse needs.
The reality is that organizations can make informed decisions about integrating security tools into a unified platform, balancing the benefits of simplified management and enhanced context against the risks of vendor lock-in and reduced flexibility.
Evaluating A Best of Breed SOC (& Why Its Likely The Future)
If the future of the SOC is not consolidated, it is likely that the future of the SOC will be more modular, especially as we move to a cybersecurity world that will be dominated by new types of attacks from generative AI and would require specialized solutions to deal with the variety of threats that could emerge. This approach to security detection & response architecture emphasizes the principles of standardization, flexibility, data ownership, cost-efficiency, and advanced technology adoption, especially with the rise of a new architectural change with LLMs.
This concept has emerged as the headless SIEM, i.e. a security data architecture product (security data lake, SIEM, data warehouse, XDR etc.) that focuses solely on processing, analyzing, and handling security data. Its functionalities are accessed and managed through an API or some command-line interfaces. Yes, a consolidated SOC reduces the number of tools that SOC teams want, but the biggest driver for the SOC is ultimately managing costs and being able to respond to the most important threats.
I’m not advocating for a plethora of solutions of 30+ solutions in the SOC, but an architecture with best-of-breed solutions that has three major components that fill the core components of the SOC (this is a simplistic model as many organizations have different stacks, but this is broadly a good framework from my research):
Pre-data processors and ETL solutions
Security data analytics and storage engine
Automation solution
Modular Security Architecture
This is a similar graphic but laid out with vendors. It is built around the Data Fabric concept, Defined by Gartner as an architecture and set of data services that provide consistent capabilities across a choice of endpoints spanning hybrid and multi-cloud environments. It aims to simplify data management and integration by making data more accessible and usable across various systems.
Pre-data processors and ETL solutions: This is a new and emerging category that has been rapidly growing since the birth of Cribl to $100M ARR. These vendors are the middlemen between your security tools and your SIEM. Once these vendors are adopted in a modular SOC, they help to significantly drive down the costs and alerts, ideally within your SIEM, which is the biggest challenge facing the SOC. There are two types of vendors here:
Data pipeline & ETL vendors: These vendors specialize in collect data from various sources, including logs, events, metrics, and traces from different security applications and IT systems then wrangle, transform these raw datasets, and normalize it into structured formats that are easier to analyze. They include normalizing data and filtering out irrelevant information. There are a number of vendors within this category, like Tarsal, Monad, and many others.
Data routing vendors: These vendors specialize in data optimization & enrichment before it gets to your SIEM. They can enrich data with contextual information, such as threat intelligence feeds, user identity information, and geolocation data, to provide more context for security alerts and incidents. Once the data is processed, these orchestrators route it to the appropriate destination, whether it’s a SIEM, a data lake, an analytics platform, or other storage solutions. There are a number of vendors within this category like the prominent players like Cribl, but you have emerging companies like Observo.ai
Security data analytics and storage solutions: The traditional all-in-one SIEM vendors have normally occupied. There are four types of architectures available to companies - the obvious SIEM, but we now have emerging multi-data SIEMs like Anvilogic, XDR solutions built around EDR, and data warehouse solutions like Snowflake. There is a case for large organizations standardizing with data lake technologies like Databricks and Snowflake, and I also see a role here for things like the Amazon security lake. While this makes sense today, we’ll see new data management platforms in the future with compelling security use cases. Across these deployment methods, companies can adopt standards such as the Open Cybersecurity Schema Framework (OCSF) to ensure consistent data formatting and easier integration with future Gen AI-enabled products.
As Oliver Rochford states, if a company has more builder archetypes/security talent with detection engineering skills, they will likely lean more toward the data lake option and the opposite.
Federated data model—This model also enables an increasingly new trend: a federated data model, which is a decentralized approach to data management where data remains in its original location but is accessible and queryable across different systems and environments. Instead of the notion of moving all the data to one repository, due to the constant change and data volume in today’s architecture, this model facilitates collaboration among different teams and departments by allowing them to access and analyze shared data in real-time. It also enhances data sovereignty and security by keeping data within its original environment, reducing the risk associated with data transfer and storage in centralized locations.
More aligned with the future architecture that involves AI/LLMs: One additional benefit that I gleaned from Umesh Yerram’s piece is that Retrieval-Augmented Generation (RAG) can enable companies to access and analyze their data by leveraging Large Language Models (LLMs) — Retrieval-Augmented Generation (RAG) allows security data to become part of the prompt used to query the LLM model. Thereby providing tremendous detection insights into security data and enabling robust threat-hunting capabilities.
Automation solutions: Companies can adopt more modular best-of-breed automation technologies to perform repetitive and time-consuming tasks. The biggest challenges with the legacy SOAR vendors are the costs and significant implementation hassles around building out workflows. Developing and maintaining automation playbooks for new types of threats and rules can be complex for many SOC teams who want to focus on important alerts. With more modern hyperautomation solutions like Torq or autonomous tier 1 solutions like Intezer, these solutions filter and prioritize alerts based on predefined rules and machine learning algorithms. This reduces the number of false positives for SOC teams to analyze and highlights the most critical alerts that require immediate attention. These solutions help accelerate detection and response times while minimizing human errors and improve the accuracy of threat detection and incident response.
A similar depiction of a modular SOC architecture
There are a number of reasons why this works as a general framework for many organizations:
Verticalized solutions based on compliance requirements: Different industries have unique SOC requirements or compliance protocols they need to follow. Financial services, for example, need centralized SOCs due to stringent regulations, while AI/cloud-native companies benefit from distributed architectures. This diversity makes it difficult to apply a one-size-fits-all approach to SOCs. organizations to choose the best available solutions for specific security functions. This flexibility ensures that specialized tools, such as those for intrusion detection or malware analysis, can be deployed to address specific needs effectively.
Cost Efficiency: As much as people make the argument that consolidating solutions with one vendor is the solution to managing costs, based on all the research I’ve done and customer calls, there is no valid evidence that over the long-term, a company saves costs by using a large platform. The upfront costs are cheaper, but it only grows overtime. However, a best-of-breed reduces cost because a company may decide to use the best storage engine that optimizes costs for them. They may utilize an XDR or security data lake if they deal with more real-time, hot data use cases - this could be a media company, etc. They can deploy specialized tools to optimize their spending on security technologies. This deployment method helps to keep data lake optimized and cost-effective by segregating high-priority security data from routine logs to alternate low-cost solutions
Scalability Concerns: Best-of-breed SOC can scale more easily as new threats emerge or as an organization's network expands. This modular approach allows for incremental upgrades and changes without significant disruptions, facilitating growth and adaptation. For example, Airbnb’s security data challenges evolved as the company went from being a 600+ company to over 6,000+ employees which led to the founding of Panther Labs.
Redundancy and Resilience: Using multiple solutions from different vendors increases redundancy and resilience in security operations. Crowdstrike best exemplifies this situation. If one technology solution fails, others can maintain security operations, minimizing downtime and enhancing overall security.
Example of a Best of Breed XDR & SIEM Provider
There are many solutions which I featured in my previous report such as Anvilogic, Hunters, but I wanted to extensively cover an XDR + SIEM solution that covers a key component of the middle of the stack below.
Sekoia
Sekoia is a platform that aims to exemplify this new breed of cybersecurity solutions, as they are poised to become the future of SIEM, SOAR, and a threat intelligence platforms (TIP) by evolving into comprehensive SOC platforms. Their platform combines detection, response, and prevention capabilities in one solution, eliminating the need for on-premise infrastructure and allowing for faster implementation with lower maintenance costs.
Sekoia.io is a threat intelligence-powered SOC platform that provides Extended Detection and Response (XDR) and SIEM solutions based on Cyber Threat Intelligence (CTI). Their solutions enhance modern SOCs' collaboration, productivity, and protection against cyberattacks. Sekoia aims to become the leading Security Service Delivery Platform (SSDP), enhancing go-to-market (GTM) strategies for Managed Detection and Response (MDR) and Managed Security Service Providers (MSSPs). Their goal is to reduce complexity for customers.
Sekoia Product Lines
Sekoia Defend (XDR + SIEM Offering)
Sekoia Defend integrates next-gen SIEM, orchestration, incident response, and CTI into a unified platform, providing a centralized and comprehensive solution for cybersecurity. The platform's agnostic approach adapts to various technologies, both on-premises and in the cloud, with an expanding integration catalog and custom integration capabilities. As a SaaS solution, Sekoia Defend ensures secure and accessible global use, enabling users to connect from anywhere via a dedicated URL. The platform supports multiple event collection methods, including push and pull modes, with a vast catalog of 200+ integrations, making it easy to collect and manage security data. Sekoia Defend employs behavioral, CTI-based, and anomaly detection in real-time, providing proactive defense against a wide range of cyber threats. Events are normalized using Elastic Common Schema (ECS), facilitating transparent and auditable data handling. Enrichments with CTI observables and organizational assets enhance the context for analysts. Automation and correlation features incorporate SOAR capabilities with easy-to-use playbooks, allowing users to automate responses, streamline workflows, and execute actions at scale, enhancing the efficiency of cybersecurity operations.
Sekoia Open-Extended Detection & Response (XDR)
Sekoia believes in the open XDR model, backing its vision with a massive portfolio of third-party integrations, and allowing customers to request new ones through a straightforward process. This flexibility and openness allow it to find growth opportunities from organizations undergoing digital transformation and those looking to protect their environments while avoiding vendor lock-in. To enhance protection across both cloud and on-premises ecosystems, organizations need to consolidate threat detection, investigation, hunting, and response across multiple domains with XDR.
Sekoia has a long history in the threat intelligence industry, leveraging this expertise to build a comprehensive solution that enhances any SOC team. To set the context for readers, CTI involves the collection, processing, and analysis of information about potential or current threats.
The goal of CTI is to identify and prepare for cyber threats by providing actionable insights and intelligence to security teams. CTI technology gathers data from various sources, including open-source intelligence (OSINT), commercial threat intelligence providers, internal logs, dark web monitoring, and threat feeds. Analysts use this data to identify indicators of compromise (IOCs), tactics, techniques, and procedures (TTPs) used by threat actors, and potential attack vectors.
Sekoia's proprietary CTI is managed by the largest private team of dedicated CTI researchers in Europe. This expertise explains why Sekoia is a partner of Europol EC3 for intelligence sharing against cybercrime and contributes to international takedowns. They have an extensive threat detection and research (team) who have built a library of 900+ detection rules over the past decade. This has helped inform their threat intelligence (IOCs, reports) and their products. This is a core differentiator that enables any customer especially those on the midmarket who need an out-of-box solution. This leads to faster time to value which reduces the need to write new detection rules. This aligns well with the SSDP strategy which strives to enable the customer to focus on the service without having to preempt resources to maintain their own rule catalog.
Additionally, Sekoia provides a comprehensive view of the most active cyber threats and their associated technical indicators (IoCs). The platform includes all the intelligence produced and contextualized by their threat and detection team. Key features include:
Proprietary and exclusive sources: Strategic intelligence reports, C2 Tracker, Malware Watcher, YARA Tracker, telemetry, and observations.
Open Source Intelligence (OSINT) and commercial sources: Triage, ThreatFox, Phishtank, Abuse.ch (URLhaus, Malware bazaar, feodotracker), MWDB.
On average, about 150,000 new IoCs are added to their platform each month, with more than 50% coming from Sekoia's exclusive sources. Their database includes over 6 million threat-related objects, including 3,000 malware samples used in 7,000 attack campaigns by 200 attacker groups and 600 intrusion sets.
Sekoia's advanced threat detection team generates reports on current and emerging threat actors and vulnerabilities to inform their clients. This intelligence comes from Sekoia's investigations and technical capabilities, as well as third-party sources. Customers can incorporate their IoCs derived from their context and partner CERTs.
Sekoia provides numerous options for disseminating their intelligence to third-party security systems for various use cases:
Within a SIEM, detection and hunting capabilities can be enhanced by using additional IoCs or providing extensive context for operations.
Within SOAR, to enrich, contextualize, and support analysts in incident response activities.
In Threat Intelligence Platforms (TIP), to add a source of intelligence to a consolidated database used for detection or contextualization.
Directly into security devices (EDR, firewall, etc.) to supply the solution with additional indicators, such as IP addresses or file hashes, to improve preventive blocking or detection.
The intelligence can be disseminated to third-party systems (SIEM, SOAR, TIP, EDR, Firewall, etc.) through their native integrations and dissemination capabilities like TAXII 2.1, APIs, etc.
How Both Work Together
By combining threat anticipation through knowledge of attackers (Sekoia Intelligence) with automation of detection and response, the Sekoia SOC platform (Sekoia Defend - XDR) provides security teams a unified view and total control over their information systems. Its interoperability with third-party solutions and compliance with international technical standards enable organizations to maximize their existing technologies.
Sekoia enables customers to focus their human resources on high-value missions, optimize their cyber-defense strategy, and regain the advantage against advanced cyber threats.
Sekoia For MSSPs
The Sekoia SOC platform is built for MSSPs to sell MDR services using an XDR approach. MSSPs need a robust solution to serve multiple clients, and Sekoia helps with centralizing management and streamlining requirements for delivering operations. The goal is to maximize SOC resources' efficiency, resulting in cost savings and improved service delivery for all clients. Sekoia enhances client security management, optimizes alert qualification and management using a comprehensive overview with integrated SIEM and CTI.
Security Service Delivery Platform (SSDP)
SSDP is an emerging theme designed to enhance the delivery of managed security services. SSDPs provide a centralized interface for managing multiple security tools, including SIEM and XDR systems, allowing security analysts to monitor and respond to incidents without switching between platforms. SSDPs enable quicker and more effective incident responses by standardizing and automating response actions. Gartner envisions decoupling security service delivery platforms (SSDPs) from services as a go-to-market strategy, leading to a modular solution offering. To read more about this SSDP trend, refer to this blog by Sekoia.
Sekoia.io's product is designed for MSSPs and large enterprise SOCs, offering a competitive edge over leading vendors like Hunters, Panther and also Stellar Cyber through its pricing and comprehensive feature set. By integrating CTI, XDR, and SIEM capabilities, Sekoia provides a powerful and flexible platform for modern cybersecurity needs.
Example Of A Best-of-breed Automation for Tier 1 Analysts
Intezer: Emerging Autonomous SOC Solution
It is a well-known fact that the complexity and volume of threats have increased while the demand for expertise in security operations has only worsened. While many organizations are dealing with staffing shortages, companies like Intezer leverage AI to deliver an autonomous SOC platform that automates many tasks within the SOC. Their solution automates many of the tasks for Tier 1 SOC analysts around incident investigations, managing the triage and response protocols with the ultimate goal of effectively augmenting and improving the productivity of the SOC analyst.
Intezer was originally founded to research and develop threat detection and analysis technology using a proprietary technology called genetic analysis, a complex process for analyzing software code to automate response. This specialty in genetic analysis enabled them to analyze any threat (fileless, files, URLs, etc.), accelerate incident response, reduce false positives, correlate threats, and trace their origins.
Intezer’s founders knew that analysts don't have the time or tools to analyze every artifact or code snippet, so they built their solutions to automate triage of alerts from security tools. Intezer's first product earned a reputation in the industry for malware analysis and memory forensics, and it is now a core piece of the AI-engine powering their Autonomous SOC platform which average less than 5 minutes to deeply investigate and triage each alert.
Intezer’s AI SOC Solutions
My goal below is to break down how Intezer’s product works as a framework for understanding how it compares to other SOC automation products or services. Intezer states their solution can enhance or fully replace alert triage services by MDR (Managed Detection and Response) providers. They see two new startups with products based on generative AI, Dropzone AI and Radiant Security, as their direct competitors.
Data Ingestion & Analysis
The first process for Intezer is that it connects directly to an organization’s alert sources via API Key or plugins. Intezer ingests alerts and supports triage through its extensive integrations with endpoint (EDR) security, SIEM providers, email security tools, and several SOAR providers such as:
SIEM tools: They ingest security events and log alerts from Splunk, Sumo Logic, Microsoft Sentinel, Elastic SIEM, and more.
User-Reported Phishing Pipelines: They can ingest and monitor email inboxes from platforms like Microsoft Office 365, Google Workspace, or Proofpoint.
Endpoint security products: They have a special, easy-to-set-up process for integrating with EDR solutions including CrowdStrike, SentinelOne, and Microsoft Defender.
Security Orchestration, Automation, and Response (SOAR) tools: They also integrate with SOAR tools through dedicated apps in each vendor’s marketplace to collect suspicious emails or other alert types like Tines, Cortex XSOAR, Splunk SOAR, and more.
Depending on the solution above, Intezer is able to collect all relevant data associated with an alert, including files, processes, command lines, log data, evidence from process arguments, URLs, IPs, and more. Intezer has some unique processes using a variety of techniques that include the use of their generative AI and proprietary machine learning. Other methods include genetic analysis, sandboxing, static analysis, open-source intelligence (OSINT), memory analysis, and reverse engineering to analyze each piece of collected evidence to determine accurate alert triage verdicts and incident response actions.
Triage & Response
Intezer categorizes and classifies the risk associated with each alert and decides whether to escalate it based on its investigation results.
For basic or lower-level cases, the platform auto-remediates false positives using a customer’s existing detection systems. This reduces the time required for a security analyst to review this case or make a quick fix.
For confirmed threats, Intezer provides assessments and recommendations, including detection content and its out-of-the-box hunting rules to guide the response process. This reduces the number of escalated alerts reviewed by a team. In some cases with a confirmed threat, they can conduct deeper forensics on the endpoint, applying Indicators of Compromise (IOCs) and other hunting rules, or other recommended next steps that are based on industry best practices to dive into an issue.
Alert Triage Use Cases
Intezer integrates and automates alerts that cover a wide variety of tasks across SIEM, SOAR, EDR alert triage and user-reported phishing. Intezer can be bought as a standalone product to automate alert triage or can be complementary in the case where a customer has a SOAR. In cases where a customer already has a SOAR, Intezer can integrate with it to ingest alert data or for case management.
The benefit is that Intezer provides valuable information to enrich incident tickets or cases, adding deeper context to the investigation and response process. Intezer's assessment automatically resolves or de-prioritizes tickets as a false positive, reducing extra alerts and allowing teams to focus on higher priority threats. Intezer’s AI-powered platform uses sophisticated algorithms to make decisions like an experienced SOC analyst, reducing the need for human intervention.
By combining an existing SOAR tool with Intezer’s powerful automation, security teams can simplify playbooks or automate even more processes. Intezer supports Splunk Phantom, XSOAR, Chronicle and a wide number of integrations. Connecting via SOAR allows users to leverage Intezer’s decision-making and analysis capabilities for a wide range of custom alert sources and playbooks, such as the investigation of suspicious emails and employee-reported phishing. Intezer’s focus is on providing off-the-shelf functionality that complements other solutions, reducing or eliminating the need for managed triage services. It’s important to note that Intezer doesn’t “build” workflow automations since their AI-native product performs the core workflows.
It's important to highlight that many MSSPs use Intezer, as more organizations have turned to service providers to manage their SOCs. Some of the world’s largest MSSPs currently use Intezer to automate processes for their in-house MDR service. Many of these MSSPs use Intezer as the cornerstone of their AI strategy, using it to provide faster triage and deeper, without an extensive manual labor required to staff their SOC.
Intezer’s objective is to fully automate the tasks of Tier 1 SOC Analysts, extending the capacity and capabilities of analysts to comprehensively triage every alert and prioritize the critical threats. This ultimately helps fill in the talent shortage that is plaguing many security teams. Intezer’s competitive advantage lies in their expertise in threat analysis and reverse engineering which they’ve utilized to build a highly curated prioritization engine that’s able to enable to filter high-fidelity alerts. They’ve also built a wide number of integrations with many technologies used in the SOC, especially for EDR and reported phishing pipelines. Intezer has built a robust amount of Fortune 500 customers. The company has found great success serving MSSPs and mid-sized businesses with robust enterprise security teams. Most of their customers turn to them to manage their talent shortage, high alert volume and rising costs of managing their SOC.
In such a case, Intezer is an example of this approach for a niche area of the SOC, but there are many more providers that I discuss in my automation report.
What The Future Holds
In conclusion, while a consolidated SOC simplifies operations, reduces vendor complexity, and enhances alert context through integrated platforms, it does pose some risks as a “blanket rule“ such as vendor lock-in, limited customization, and escalating costs over time. Conversely, a disaggregated SOC offers the advantage of best-of-breed solutions tailored to specific security functions, greater flexibility and scalability, and encourages innovation through engagement with multiple vendors.
Despite the potential challenges of management complexity, integration, and potential alert fatigue (depending on the context of the organization), a modular SOC's ability to provide specialized, resilient, and adaptable security solutions makes it a superior choice for organizations aiming to maintain a robust and dynamic cybersecurity posture.
Note that various components will require consolidation, but within SOC, I believe that by modularizing their architecture, companies can rip and replace any component with best-of-breed at any time as the attack landscape changes while maintaining complete control over their security infrastructure. A modular architecture allows easy replacement or upgrades of individual components, ensuring adaptability and control over your security infrastructure.













Probably this will be a super long comment section but one of the other issues around consolidation is the adoption and phase out of standards: now we have OCSF which seems to getting traction but before we had CEF, LEEF and another one I can't spell anymore like EDF. We had a good run with OpenC2 but not many vendors are supporting it. Now we have multi agent behaviour and probably new other protocols will need to be established by OASIS or other orgs. What about CACAO playbooks, I know only SEKOIA has decent support but nobody really allows a full import/export.
STIX 2.1 has a good adoption into TI but we cooperated to the IR extension module and I wonder how long it will take to be adopted. What about VERIS for IR, how many vendors are supporting that and the overlap with STIX2.1 as well. If the community keeps floating around standards we will never achieve consolidation. Each new competitor in this space need to support around 500+ connectors pretty much they need to be written from scratch! Would love to talk about this problem in an interview if you are interested.