Platform Consolidation In Cybersecurity: A Palo Alto Networks Case Study
A deep-dive on what defines a cybersecurity platform and lessons from Palo Alto Networks
Earlier this year, my friend Rak Garg and I initially wrote about the rise of Palo Alto Networks and explored their path toward becoming the first $100B security company.
It’s been 9-months since that report, so I wanted to write an update on how Palo Alto Networks (PANW) is progressing toward that goal and explore their platform consolidation strategy. PANW recently wrapped up its 2023 fiscal year, where they hosted a medium-term investor update. During this presentation (which, before it, had a lot of drama), they provided investors with a vision of their strategy and gave us lots of data points about the health of their business.
Today’s piece provides an analysis of this presentation and recent earnings call. I dive into PANW’s three major business portfolios and their approach to creating a cybersecurity platform across network, security operations and cloud security.
Key Actionable Summary:
Platform consolidation has been a major theme across the software industry in 2023. Particularly in fragmented industries like Cybersecurity with over 4000+ vendors and 30+ sub-market categories, which I discussed in my last piece. However, we rarely see any analysis that defines or elaborates on what this platform consolidation actually looks like within an enterprise. Recently, PANW has given us fitting examples of what this looks like across three large markets in security.
As a refresher, almost six years ago, Palo Alto Networks was known as an on-prem firewall security company with failed expansions into new markets and multiple CEO changes. However, since Nikesh Arora took over in 2018, they have successfully expanded from core firewalls into three platforms. These can be categorized into network security (firewalls and SASE), cloud security, and the cortex security operation center (SOC) platform.
This strategy has proved successful as today, Palo Alto Networks now generates over $3.2B in ARR from its next-gen security products (i.e. cloud and software products), currently just under 40% of revenue and expected to grow to >50% over the next 2-3 years. Across these newer platforms, SASE has surpassed $1B in ARR, Prisma Cloud is over $500M ARR, and the Cortex SOC business has achieved $1B in bookings.
The next big driver of growth that will define Palo Alto’s success is how well they execute on their SASE and XSIAM 2.0 business portfolio over the next 3-5 years. SASE is a more competitive market, but it is one of the largest and fastest-growing markets in security. They have a clear roadmap for how to execute on this market, but less so with XSIAM. The XSIAM business is a new product that consolidates many point solutions within security operations, but comes with a lot of unknowns on how well customers will react at scale to it. Still, the product gives them little to no competition, which means it will create massive opportunities if they can penetrate this market.
In their most recent Q124 earnings report, they showed why they are further inching closer to becoming the first $100B security company. They reported quarterly revenue of $1.8B and are on pace to grow to $8.2B for the full year 2024, at around 20% YoY. This growth was combined with strong bottom-line metrics of non-GAAP margins of 26% and Free cash flow margins of 38%, proving they have something working.
Notably, this was one of their first quarters where PANW’s results significantly outperformed many of its networking peers like Fortinet, Checkpoint, Cisco and Juniper growth, who all grew single digits/cut revenue growth. This quarter gave us more evidence of how PANW has further differentiated itself from legacy security players and should be categorized more closely with emerging players like ZScaler and Crowdstrike.
The core story around PANW is platformization, consolidating multiple-point solutions into a central platform, and upselling this to their large 60K customer install base they've built over the years. This strategy appears to be going well based on these recent metrics, and we’ll explore each below.
💡Cybersecurity & SaaS Bootcamp 🚀
We are pleased to host our 3rd bootcamp! The cybersecurity bootcamp comprises of the following:
Cybersecurity Industry Overview: A 3-week bootcamp that provides an in-depth exploration of introductory cybersecurity frameworks, such as cloud, endpoint, and network security. Participants will gain a solid understanding of cybersecurity using simple frameworks, as well as insights into what sets leading cybersecurity companies like Crowdstrike, Palo Alto Networks, and startups apart.
Software Modeling Foundations: In addition to the bootcamp, we offer an optional session on building SaaS metrics and a financial model for software companies. This session is led by former Morgan Stanley Analyst Thomas Robb.
Learn & Network: Participants can engage with a cybersecurity executive to gain insights into the industry and future trends. This includes networking opportunities with top-tier participants from investment and technology companies.
For full details, please visit Cybersecurity & SaaS Bootcamp. We have a final 30% discount that ends this Friday. Use the Code: FRIDAY30. If you have any questions, let us know!
Plaformization In Cybersecurity
We often hear the word vendor consolidation within cybersecurity with little to no fruition. The average number of security tools used in an enterprise ranges from over 30+ to 60-70+, depending on the organization's size. There is also a shortage of security talent available to manage these growing tools.
Palo Alto Networks is finally showing us real examples of what it is to become a security platform and the results that emerge from it. Infact, Palo Alto Networks doesn’t refer to its strategy as just consolidating several security point solutions, it refers to its strategy as platformization. Now what does this mean? My friend, Cole Gromus, wrote a great article titled The Audacious Future Of Palo Alto Networks (worth reading everything). He differentiates between platformization and vendor consolidation.
Consolidation ≠ platformization. Vendor consolidation focuses on cost savings, not value. The drivers for platformization are very different. It is not the same as vendor consolidation. While platformization may involve consolidating products and vendors, saving money is just a byproduct. The main driver is to achieve better security outcomes and value for companies using the platform. Platformization goes beyond consolidation and involves intentional activities to integrate products and unlock value that would not be possible without the integrated platform.
PANW’s platformization is a more calculated approach to building a platform. Hence, platformization and standardization is a problem that needs to be solved. It’s important to note that due to the different architectures in cybersecurity, its important to have one platform that overlays ALL areas of cybersecurity. Instead, platformization can only happen with sub-segments of cybersecurity. For example, Crowdstrike can easily consolidate products within security analytics and endpoints or Okta within Identity Access management (IAM) and adjacent identity market than it is either Crowdstrike or Okta to dive into a new market like firewalls. The only way this can happen is through large acquisitions, but it is still impossible to merge those into one integrated platform. Therefore, platformization with key market segments makes sense and this is what is happening with Palo Alto Networks.
When Nikesh was appointed as CEO in 2018, it was discussed in his first public interview that although he didn't have the technical chops of cybersecurity, his wide-ranging leadership experience, from leading Soft Bank to leading marketing in the early days of Google and his leadership roles in finance at T-Mobile were going to be critical in enabling Palo Alto capitalize on its strengths in firewalls to create a large security platform. Nikesh has delivered on that promise so far, with the stock currently at all-time highs, outperforming some of the leading tech names by 300% since 2018. A huge part of its success comes down to them expanding into newer markets and delivering on their promise of building a security platform. We got lots of evidence of this platformization strategy from their two most recent earnings call/investor presentation. Let’s dive in.
The Palo Alto Networks’ Platform
Palo Alto Networks found product-market fit with its initial firewall product before expanding into security operations (SecOps, SOC) and, eventually, cloud security. The company would find the transition from product to platform initially challenging, with early acquisitions between 2014-2018 failing to meaningfully increase market share in new categories. Today, PANW offers over 30+ products across three major areas:
Network Security (Zero Trust): This portfolio is focused on delivering networking services and security for the network. Their future TAM for this platform estimates that more cloud-based, zero-trust network services around SASE will continue to grow over the next two years:
Core firewall products (hardware, software, and virtual firewall form factors).
Secure Access Service Edge (SASE) business.
Prisma Cloud Security (Code to Cloud): Prisma Cloud has 12+ modules focused on securing code from development/build to protecting cloud infrastructure and workloads in runtime on the cloud. The TAM for this platform relies on the proliferation of new applications being built and deployed on the cloud due to better AI agents that enhance developer productivity.
Security Operation Center (Autonomous SOC) platform: The cortex business is centred around providing products and services that optimize the work of security analysts. This is the largest TAM because it includes components of XDR, EDR, SIEM, SOAR and EASM market sizes. PANW’s vision is to create a centralized platform powered by AI that can unify most of these solutions which, thereby, optimizes the work of the SOC.
In my initial piece with Rak, we explained the history of these business segments, their evolutions, and the key acquisitions that made it possible to reach where they are today. Feel free to read it here to continue reading this report. For the rest of the report, I’ll give an update on how these businesses have progressed over the past few months.
The Race to $100B: The Palo Alto Networks Story
Thank you for subscribing to the Software Analyst (formerly Investi Analyst). I haven’t written in over a year, so this is my attempt at resurrecting my newsletter. I’ve been writing about private software startups at Contrary Research, but this newsletter will be focused on simplifying the technology behind
The Platform Journey So Far
Network Security (Zero Trust) Platform
1) Core Firewall Product
Historically, Palo Alto Networks’ core product was its firewall. As a refresher, a firewall exists between an organization’s intranet apps, websites, employees, campus (left of the image) and the Internet (right of the image) to filter and control data traffic; without a firewall, a company’s internal network would be directly accessible to anyone via the Internet. PANW’s firewall/network security can be categorized into the following functions.
The hardware firewall product secures data centers and campuses.
The software firewall business that secures cloud networks.
SASE, which secures hybrid work and remote branches.
PANW firewall business has been growing in low-single digits. Their product revenue, which covers most of the firewall business centred around hardware, is estimated to reach $1.6B in FY24, growing roughly 4% YoY, without much room for growth.
In the past and even within older enterprises, when users were predominantly in the office and applications in the data center, network security was delivered by a centralized firewall. However, with the migration of more workloads to the cloud, and more data centers being virtualized, many companies are moving toward virtual firewalls and network architectures like SASE (which I will discuss later). As a result, hardware firewalls are only going to decline.
Management reiterated they don’t expect much growth as they believe the addressable market for firewall is going to grow at low single-digit growth rates over the next few 5 years. There is no need to focus heavily on this business, as management doesn’t expect to invest more here, and overtime, it’s expected to lose its relevance to the company’s core focus. I believe, they should exit this business within the next 3-5 years and allocate all of its resources toward SASE.
2) Secure Access Service Edge (SASE)
SASE is the future of network security for enterprises, and this market will be a core (if not the main) part of the PANW $100B story, therefore, I need to go into some more depth here. In my deep-dive of SASE, I provide an in-depth explanation of SASE and analyze all its components. See below.
SASE Tailwinds
Gartner estimates the market for SASE will grow at an annual growth rate of 29%, reaching over $25 billion by 2027. It is currently one of the fastest-growing categories of security because of several tailwinds. SASE allows for the consolidation of many smaller network security tools into a larger SASE umbrella. For example, SASE aggregates products like SWG, FWaaP, CASB etc, into one. As cloud adoption and hybrid workforce grow, enterprises are looking for ways to expand their network security infrastructure securely and efficiently without having to reroute traffic through centralized data centers when accessing the internet. The rise in the growth of branch and satellite offices is another tailwind. The average enterprise has more users located at branch or satellite offices, with this growth driven partly by expansion into new markets or the acquisition of smaller companies.
PANW should go all in:
PANW recently reported the SASE business is growing 60% YoY, surpassing $1B in ARR. They also saw 35% of $5 million or greater network security transactions include SASE, up from less than 10% a year ago. As mentioned briefly, I believe overtime (within 3 years), PANW should deploy all of their resources from the hardware firewall business toward SASE and capitalize on this traction.
PANW has the second-largest market share in SASE using ARR figures, only behind Zscaler (which generates $1.9B in ARR). However, PANW can utilize its superior networking capabilities (SD-WAN) to win more markets, especially in the public sector (which they have around 12% market share based on their S1 Filings). In August, they were recognized as the only leader in single-vendor SASE. Earlier this year, they were recognized as a leader on Gartner’s SSE magic quadrant and Forrester zero trust edge wave. Most of these recognitions came as a result of their networking/NGFW capabilities completed with core SSE features.
Talon Security expands SASE opportunity:
The acquisition of talon security should further broaden their market opportunity within SASE. Historically, companies incorporated a technology called Remote Browser Isolation (RBI) technology as part of a SASE solution. RBI works at the network/endpoint level and isolates end-user browsing sessions from the local network and device. It protects users/employees when browsing the internet or accessing company apps. This isolation ensures that any malicious content encountered during web browsing does not reach the user's device or the enterprise network. RBI complements SASE in that companies can enforce security policies consistently across all web traffic, aligning with SASE's centralized policy management, especially for companies with many remote unmanaged devices and contractor employees. As many as 36% of workers classify themselves as independent workers, and many use unmanaged devices when consulting for an enterprise. In addition, employees increasingly use personal devices for accessing business applications. Security teams have a difficult trade-off because they are forced to favour employee flexibility at the cost of security risks or adopt cumbersome technologies like Virtual Desktop Infrastructure (VDI). The acquisition of Talon helps solve this problem. Talon has a next-gen emerging enterprise browser product that, when combined with Prisma SASE, enables users to securely access company resources from any device while keeping the employee experience high.
To summarize PANW’s SASE opportunity, PANW’s competitive advantage, as highlighted by the Gartner ranking, is its single-vendor offering, i.e. the ability to combine networking and security services in one central architecture. Many of their competitors, like Zscaler or Cloudflare, don’t have this networking backbone (around SD-WAN) that PANW has built over the years. Most of the largest enterprises that command a high % of security spend are within the public sector, or within financial/insurance verticals that still rely on a hybrid approach to implementing SASE. PANW has the upper hand in winning these market verticals because these enterprises have a mix of new and old network architecture. For a market growing almost 30%, combined with PANW’s market share of around mid-double-digits, there is no reason why this can’t be a $3B+ ARR business within the next 2-3 years.
The Network Security Zero Trust Platform
The ultimate vision for PANW within its network portfolio is to create a centralized zero-trust network security platform that centralizes these three products (firewalls and SASE) into a unified management plane. This means networking teams can more easily control, configure, and perform unified analysis as traffic comes in and out of the enterprises.
Customers can still buy one of each depending on their needs, but everything is now integrated into one security stack. They highlighted that 30-35% of the firewalls purchased are software, which means hardware still composes a large part. My only question here is understanding how difficult it is to stitch together and implement hardware and software firewalls along with SASE. Although these technologies are very similar in that they operate at the network level, my guess is that it will be hard to be “a zero-trust“ approach, especially when you have hardware firewalls. I’d assume everything leans toward SASE and over the next 5 years, they exit the hardware firewall business, or it becomes irrelevant. It’s important to note that firewalls will continue to play an essential in network security architectures and will do so forever, but PANW should eventually exit this business and leave this for Cisco, Checkpoint or Fortinet over the long term.
Cloud security (Code to cloud)
Prisma Cloud is PANW’s central cloud security product that aims to secure every aspect of an enterprises’ code, workload, and infrastructure in the cloud. Prisma Cloud now generated over $500 million of ARR since its initial launch in May 2019, making it the largest cloud security business. Although we don’t know its growth rate, it’s important to highlight that Crowdstrike recently shared that its cloud security module has surpassed $296M ARR, growing at 70% YoY. A huge part of CRWD’s cloud business caters primarily to cloud workload protection, and they recently acquired a developer security company, Bionic.ai, to expand their reach but, they lack the breadth of PANW’s products.
Prisma Cloud is the most comprehensive cloud security across development, build, and runtime areas in the cloud. They now offer 12+ modules across three broad areas:
Secure the code: They have code scanning products such as SCA, SAST, IaC scanning, CI/CD scanning and secrets scanning products. These are focused on helping developers detect vulnerabilities in their code and open-source tools. (Important to note that during their last earnings call, they specifically noted that their IaC scanning and CI/CD security modules have been significant drivers of growth in the cloud security sector compared to other modules)
Secure the cloud Infrastructure: They have products focused on securing virtual machines, containers, serverless and workloads once deployed on the cloud. It includes cloud security posture management (CSPM) and cloud workload protection (CWP).
Secure apps in runtime: They have cloud infrastructure identity and management (CIEM) and web application/API products that secure applications in runtime on the cloud.
The Cloud Security Platform
Gartner has given a glimpse of a cloud security platform with a theoretical explanation in their market guide for cloud-native application protection platforms. However, Palo Alto is creating the ultimate cloud security platform that covers all areas of code to the cloud (albeit most of it through acquisitions). The latest addition is the acquisition of Dig Security, to add data security posture management (DSPM) to this cloud security portfolio. This cloud platform is the vision or gold standard every cloud security startup will aim toward over the long term.
It’s interesting to see why we need a vendor consolidator in cloud security, especially considering it’s still a relatively early market, but I’d argue we need more in this market than network security. The average enterprise company user now uses over 100+ applications, and with AI, this trend will only accelerate. The volume of open-source tools and risks is dramatically growing. A single vulnerability in code or risk in an open-source component that wasn't discovered during development can multiply in terms of risk once deployed in the cloud. The key then comes down to discovering risks in real-time, but with many companies having to deploy disparate products across, like CSPM from Wiz for your cloud environment and SAST tool from Synk for code scanning, all makes it all fragmented.
PANW is taking a different approach by building an integrated code-to-cloud product. Their pitch to enterprises is that you can buy one integrated platform with context across code-to-cloud. This pitch is appealing because many code scanning tools lack the context of the deployed code at runtime. Synk is attempting to do this with their acquisition of cloud security vendor, Fugue, but it appears it is taking time for them to do this well. With PANW’s approach, the goal is to ensure if there is a risk in the cloud, it can be traced back to the code level and vice-versa.
They provided a demo during this presentation. The strategy appears to be working as they provided examples of customers successfully signing multiple 8-digit contracts on this cloud platform, like a large global SaaS provider signed an $18 million Prisma Cloud deal to consume modules across this portfolio, indicating enterprises are beginning to standardize on this cloud platform. This is a difficult problem to solve, and we’re still in the early days, but this product has potential. It is setting the standard for what the end goal could be in cloud security.
Cortex: Security Operation Center (SOC) Transformation
PANW’s boldest vision lies within its cortex portfolio. They have a vision to create the world’s first autonomous SOC platform. A grand vision that aims to consolidate components of security products from SIEM, EDR, XDR, SOAR, and EASM into one large platform over the long term to modernize and automate as much of the security operations center (SOC).
If we step back for some context, it’s important to realize that PANW acquired several companies to build this portfolio to compete against Crowdstrike, Microsoft and SentinelOne in EDR. However, they have struggled with market share and dominance in their cortex business compared to their market presence in the network and cloud. The cortex portfolio has the following products:
Cortex XDR: Extended detection and response (XDR) and endpoint protection (EPP/EDR) merged with the cortex data lake.
XSOAR: Security orchestration automation and response (SOAR),
XPANSE: External attack surface management (EASM)
XSIAM: SIEM + SOAR that enables autonomous security operations powered by AI/ML
These five products have historically been used by security analyst teams within large enterprises to detect, investigate and respond to threats. Security teams have to context switch daily to manage different security products to investigate security log data/metrics to respond to threats. PANW wants to consolidate everything into one system called XSIAM.
XSIAM (Extended Security Intelligence and Automation Management)
It’s important to begin and understand the problems facing the modern SOC team at any average enterprise. On the issues most SOC face, Allie Mellen, Principal Analyst at Forrester, is one of the leading voices here. There are two blogs here, and here covering the challenges/fragmentation in the modern SOC. Many security teams receive thousands of alerts daily, many of which are false positives. These data come from endpoint, identity, cloud or attack surface products etc. The high volume of daily alerts received by security analysts results in a significant amount of data flowing into the SOC each month, requiring efficient storage. Also, this data overload poses a challenge for analysts to handle and interpret effectively. Enterprises cannot hire a considerably larger number of analysts to cope with the growing data problem. Enter, XSIAM 2.0.
XSIAM 2.0 is a new solution that builds upon three existing products - Cortex XDR for endpoint prevention and detection, Cortex XSOAR for automated threat response and Cortex Expanse for attack surface into one platform. The idea behind XSIAM is to collect data, refine data and generate insights for SOC teams.
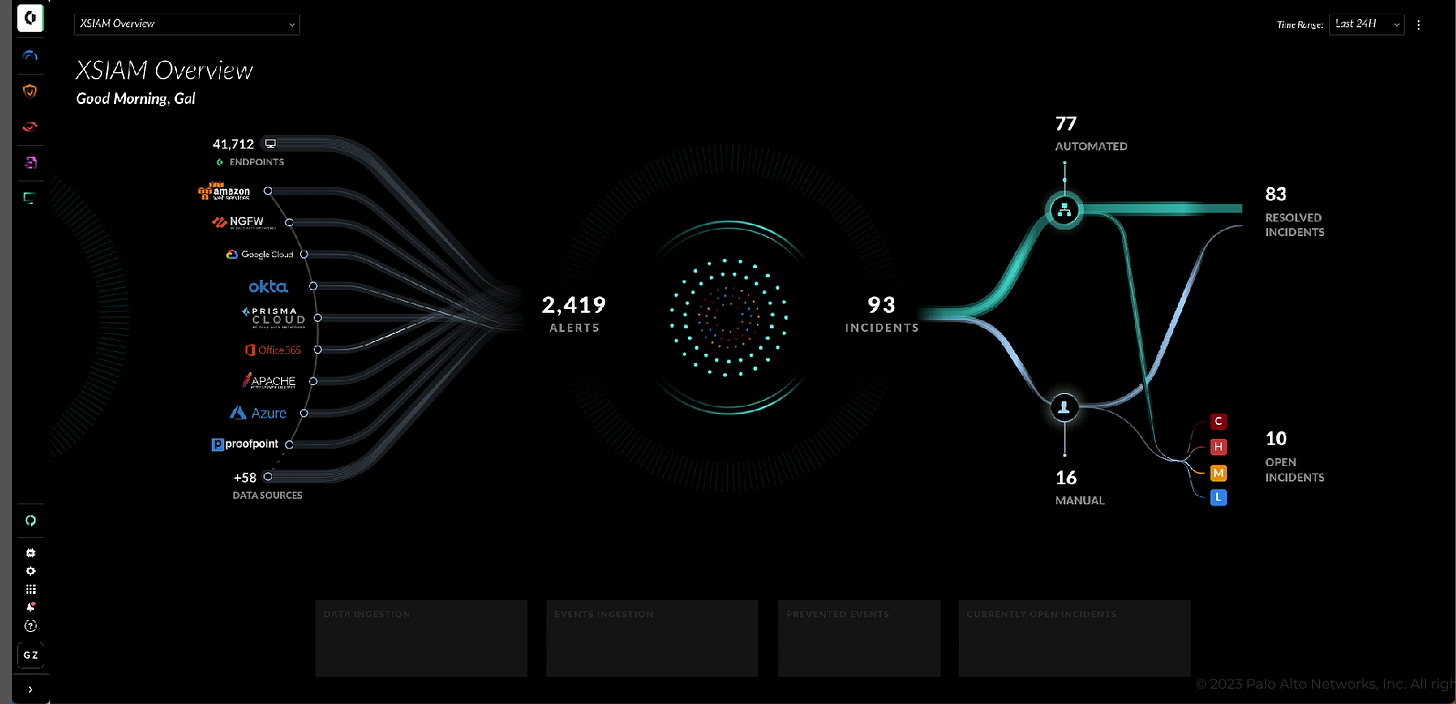
The first step is to collect data from endpoints, network, identity systems, cloud, and applications. The second step is ingesting, normalizing, and creating data mapping. The final step is generating insights for the SOC with AI (+3000 models) to analyze low-confidence signals, stitch them together with raw data and get enough context to resolve most of them automatically, presenting the user only with all of an incident and full context for each of those incidents, but with more emphasis on proactively staying ahead and predicting threats. For example, If an analyst receives 2400+ alerts using AI/ML in XSIAM, all of that can be compressed into 93 actionable incidents that an analyst needs to focus on.
The key across everything is to ensure everything is automated as much as possible to allow security analysts to focus on more complex security tasks. There is also an emphasis on mean-time-to-detection (MTTD) and resolving security incidents in real-time. This vision is what many security analysts have dreamt about for many years, but it is a difficult problem considering the data infrastructure and architecture required to make this work.
PANW provided some metrics to show this business is gaining some traction. They crossed the 5,000 customer milestone in Cortex. Within a year of launching XSIAM, they’ve gone from zero to $200 million of bookings to now over $1B in the pipeline. However, it’s important to note that this product is a high-ticket item for enterprises. The average ACV so far is over >$1M with 3-5 year commitments. Over the long-term, XSIAM has the potential to replace the role of Splunk within the enterprise. As Splunk plans on becoming integrated with Cisco, this could provide PANW with some short-term winning opportunities.
I am becoming more confident in the potential of this business, but I believe it will take roughly about 3-years to fully see material gains. PANW also realizes this is not going to be an overnight success. This is why they’ve called it a SOC transformation. XSIAM cannot be easily installed overnight. It requires an enterprise to displace old security products that are embedded into the DNA of a company, like SIEM tools and get security teams comfortable with using XSIAM, which handles all these workflows.
Couple Of Financial Updates
It’s one thing to achieve platform expansion, and it’s another to maintain profitable growth in the process. PANW has managed to walk this rope tightly without eroding shareholder value. Palo Alto is expected to reach $8.18B at the end of fiscal year 2024, growing 20% YoY while maintaining 28% operating margins and steady 37% FCF margins.
There was a big headline during the quarter about how they missed their revenue billings guide by 2%. However, management clearly explained that this is primarily due to customers preferring to sign more shorter-term contracts rather than long-term ones. They are prioritizing giving customers flexibility. Looking at the underlying customer demand, we see that revenue remains resilient as RPO grew 25% and cRPO grew 22%. This suggests that demand and customer retention are strong, making billings less important.
Finally, an important observation from Palo Alto’s recent quarter is how it is further differentiating itself from its traditional competitors. Despite the current hardware firewall market slowdown, PANW is significantly outperforming its peers. For example, PANW achieved 16% billings growth and maintained a 17-19% growth guidance for the year. Meanwhile, some of its key competitors reported a contrast:
Fortinet saw a 6% YoY growth in billings and expects -6% growth for its next quarter.
Cisco witnessed a 7% YoY growth and lowered its revenue guidance to -6% for the next quarter.
Checkpoint experienced a -5% YoY growth in billings and also expects single-digit growth next quarter.
PANW’s next-gen software business now stands at $3.23B ARR growing over 53% YoY. 83% of PANW's revenue now comes from recurring sources. Although a long way ahead, PANW is further distinguishing itself from its legacy peers and aligning more with companies like Crowdstrike and Zscaler.
Platform Play
Palo Alto Networks’ platformization strategy is in full gear and appears to be gaining traction. Over 56% of the G200 customers have purchased one of PANW's three platform products (Strata, Prisma, and Cortex). They provided four examples of how large enterprises signed multiple eight-figure deals this past quarter, most of which resulted from customers already using PANW's network security solution (leveraging the install base). Additionally, deals over $20 million grew faster than deals over $10 million as their go-to-market motion appears to be increasingly successful in selling their platform.
PANW has taken a very deliberate approach to how they want to achieve this platformization. Lee Klarich, Chief Product Officer of PANW, emphasized this during their medium update presentation.
The second thing we're doing is making sure that when we integrate it, they're actually integrated together in solving hard problems that can't be solved as standalone capabilities. So, we're not just focused on consolidation, although that does provide value. Our goal is to deliver technical outcomes through integration that cannot be achieved otherwise.
This platformization journey will take time, and there will be bumps along the way. Currently, PANW has led the way in solving this consolidation problem, and the results are showing in their financials. Their next priority is to see if platformization enables them to capture more market share across cybersecurity. When asked about his major priority for Palo Alto Networks, Nikesh said he is trying to see if they can increase Palo Alto’s market share from single digits to mid-double digits, similar to what the likes of Salesforce have done in CRM. An extremely difficult task in a market with 4000+ vendors, but with these key product announcements, traction and a growing cybersecurity market, I believe they can achieve this goal.
Thanks for reading!
Francis
💡Cybersecurity & SaaS Bootcamp goes deeper on platforms in security
This report is a sneak peek into the presentation in our upcoming cybersecurity bootcamp. Our cybersecurity program delves deeper into each of these foundational components of cybersecurity and how companies like Palo Alto Networks and Crowdstrike have built incredible platforms.
Full details here → Cybersecurity & SaaS Bootcamp! We have a final 30% discount that ends this Friday. Use the Code: FRIDAY30. If you have any questions, let us know!











Great post Francis.
This is an in-depth report! Will take the time to read this weekend. Excellent job Francis.