SACR Cybersecurity 2026 Outlook
2025 in Review, 2026 Forecast: What changed in cybersecurity platforms, M&A, AI security, SecOps, and identity and what we expect next.
Hello everyone,
Happy New Year! We’re excited to share our first report of this year! The goal of today’s report is threefold:
SACR Updates & Initiatives in 2026: To give readers a preview of what to expect from us in 2026 across our publications, starting tomorrow.
Top Lessons learned in 2025: To summarize the top lessons learned and key trends across cybersecurity last year.
Our predictions for the upcoming year 2026: To share our predictions for the year ahead. We want to give our readers a preview of what to expect from us this year across our publications starting tomorrow.
SACR Updates & Initiatives in 2026
At SACR, we are proud to serve as a bridge between the voices of security leaders and the innovations of leading cybersecurity vendors. We have two announcements to share.
New Team Members
In 2025, we were pleased to welcome two deeply respected and highly technical researchers to the firm: Aqsa Taylor (CRO) and Lawrence Pingree, a former Gartner leader with over 30 years of experience in cybersecurity. Over the coming year, readers can expect to see more reports authored by both of them, including collaborations with external contributors.
Local Community Events
Throughout 2026, we will be launching new initiatives, including hosting community dinners where security leaders can exchange ideas in a private, peer-driven setting. Our first events will take place in New York City and Dallas, TX. Details are below.
For those unfamiliar with our CISO Arm, please visit our official website to review past events and webinars. As part of our mission to democratize cybersecurity research and to deliver insights that are unbiased and free of product pitches, we have a number of topics and events planned for early this year that we would like to highlight.
Watch our teaser:
In-Person Dinner | New York City — January 28
We covered cloud runtime security last year during an exclusive dinner with security leaders in San Francisco. In two weeks, we are bringing that conversation to New York City.
We will be joined by a CISO speaker from one of the leading global banks headquartered in New York City. If you are a security leader looking for practical lessons and real-world takeaways from seasoned professionals, this event is for you.
All registrations are subject to approval, and seating is extremely limited. Register below.
2025 TRENDS AND 2026 PREDICTIONS
Let’s dive into today’s analysis:
2025 Snapshot: Platform Consolidation and AI-Driven Deals
If 2024 was defined by “wait and see,” 2025 was the year the floodgates opened. Cybersecurity experienced a historic $96B in M&A deal value across 400 transactions, representing the highest volume and value in the industry’s history, a 270% year-over-year increase.
The last few months have seen unprecedented M&A activity. According to Momentum Cyber's new report, the cybersecurity ecosystem saw $96B in record deal activity, and we saw $20.7B in total financing volume, for a $119B in Strategic Activity Across Acquisitions, IPOs & Financings.
This activity was driven by two forces:
A small number of extremely large acquisitions
Continued concentration of venture capital into AI-focused security companies
Strategic buyers prioritized cloud security and identity, while investors favored companies with proven scale, durable demand, and credible AI potential. Although still an emerging segment, AI Security was the most active financing category, with 144 capital raises.
Google’s acquisition of Wiz and Palo Alto Networks’ acquisition of CyberArk were among the largest and most consequential deals of the year. These transactions reflect a clear market mandate: simplification for the security stack.
CISOs are moving away from supplementing tool stacks and toward replacing outdated point solutions with integrated platforms. That said, net-new purchases are still occurring, but only for point solutions that create entirely new categories or solve previously unaddressed problems.
Strategic buyers such as ServiceNow, Palo Alto Networks, and Cisco spent 2025 assembling unified platforms by acquiring best-of-breed vendors. The rationale is straightforward: in an era of machine-speed attacks, managing dozens of disconnected dashboards is a liability.
SACR Coverage Areas: 2026 Predictions
SACR primarily focuses on four major cybersecurity domains, so we will focus most of our reflections, analysis and predictions on categories that we have in-depth expertise and knowledge. We met over 400+ companies in 2025 and spoke to hundreds of cybersecurity leaders, practitioners and participants across the ecosystem to inform our opinions on the following commentary.
Cloud & App Security Coverage
Data & AI Security Coverage
Security Operations Coverage
Identity Security Coverage
Please expect to see multiple in-depth analyses, reviews, and reports across the following categories this year.
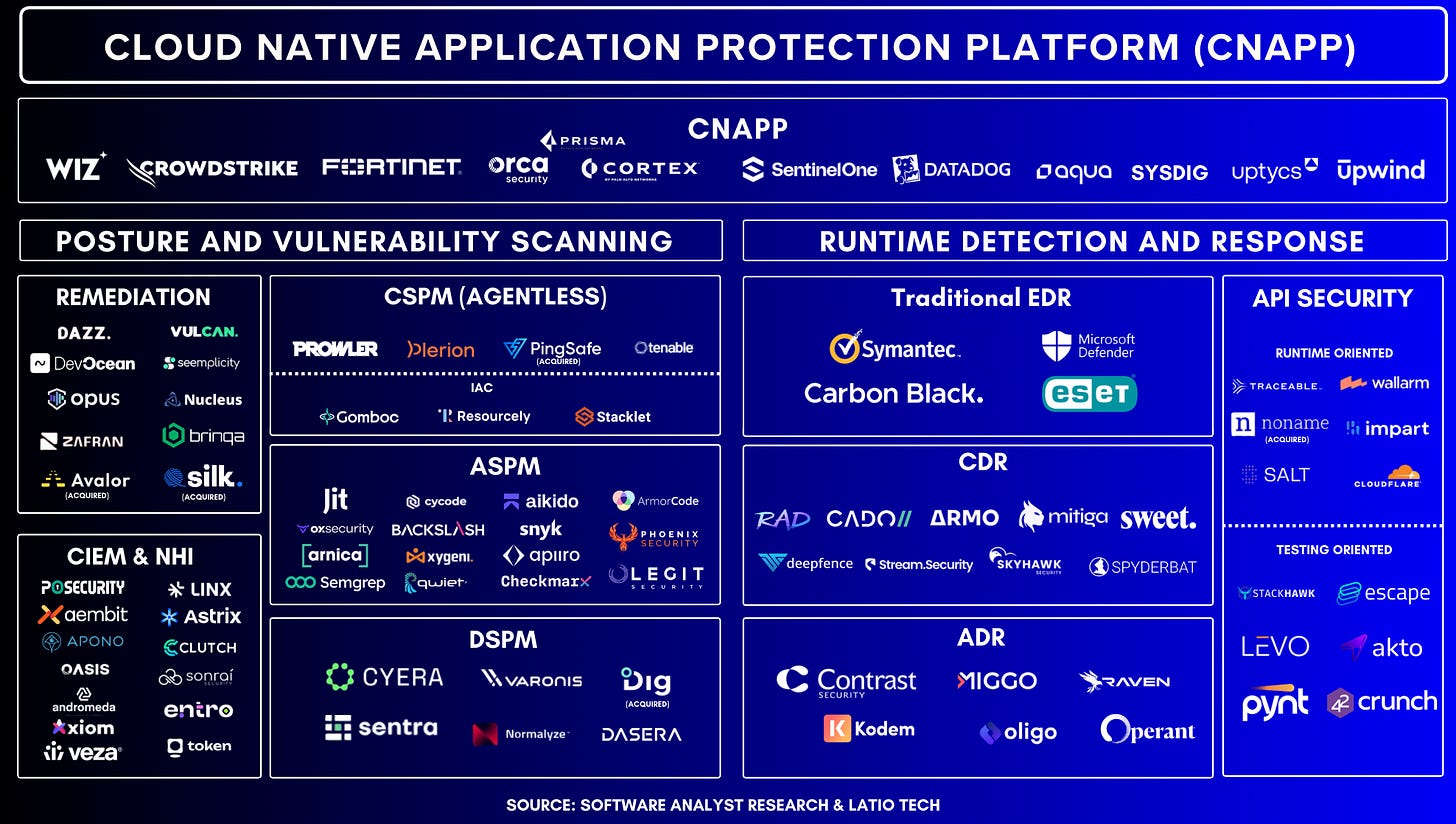
Cloud & Application Security
Cloud & SecOps Trends / Cloud Security Runtime in 2026
Google, one of the leading AI players, paying up for one of their largest ever acquisitions in their history for Wiz is a signal that they believe the cloud will be a critical asset in their race to dominate AI workloads.
One of our biggest predictions coming into 2026 is that cloud runtime workloads will become critical for AI agent deployments. We foresee a closer convergence / collaboration between SOC and cloud security teams. Historically, these teams have been fragmented and they have been separate departments focused on different types of attacks, risks and solutions. We don’t believe there will be a full convergence because of the dynamic, but we see more of an empowering of SOC teams to better understand cloud alerts.
We believe CSPM is dead and a commodity. Everyone does posture. The market has been mostly won by the leading vendors. While initial posture management is critical, 2026 is seeing a shift toward cloud security runtime, the real-time protection of active workloads. This trend highlights the need for defences that can catch lateral movement and active threats at “cloud speed”. Modern strategies prioritize moving security into production environments to provide a final layer of defence against sophisticated threats that bypass static configuration checks. We also believe that deeper application inspection will become more critical for cybersecurity teams.
Resources on the topic:
Some industry-wide resources are available for you to read and familiarize yourself with the topic.
Some great resources cover this topic more in-depth.
Application Security (Vibe Security) Will Grow in 2026
In 2025, software development reached a definitive tipping point, with the explosion of agentic AI and “vibe coding.” This shift marked by the widespread adoption of tools like Cursor and Windsurf allows developers to ship entire applications at a velocity that has effectively rendered traditional, human-paced security reviews obsolete.
The central challenge for 2026 is that while AI-generated code is moving fast, we need to secure coding assistants and agents. Research indicates that approximately 24% of AI-generated code contains critical security flaws, frequently because models prioritize functional performance over rigorous security logic. Traditional AppSec assumptions are failing, and many companies are building new solutions to help solve for insecure patterns like hardcoded secrets or unsafe functions. We anticipate security leaders investing in “VibeSec” (Vibe Security) for their developers. We expect lots of developments here since CISOs are no longer attempting to block AI usage; instead, they are implementing a multi-layered defensive framework.
Cloud Complexity & Remediation as the next focus
As cloud security matures for many companies, especially with the growth of hybrid cloud. Despite healthy budget increases, 49% of CISOs identify the sheer complexity and sprawl of cloud resources as the top barrier to a successful security program. Organizations are often buried under a fragmented stack of more than 25 tools, leading to alert fatigue and significant blind spots across multi-cloud environments. The 2026 objective will continue to focus on remediation and simplifying their cloud stack.
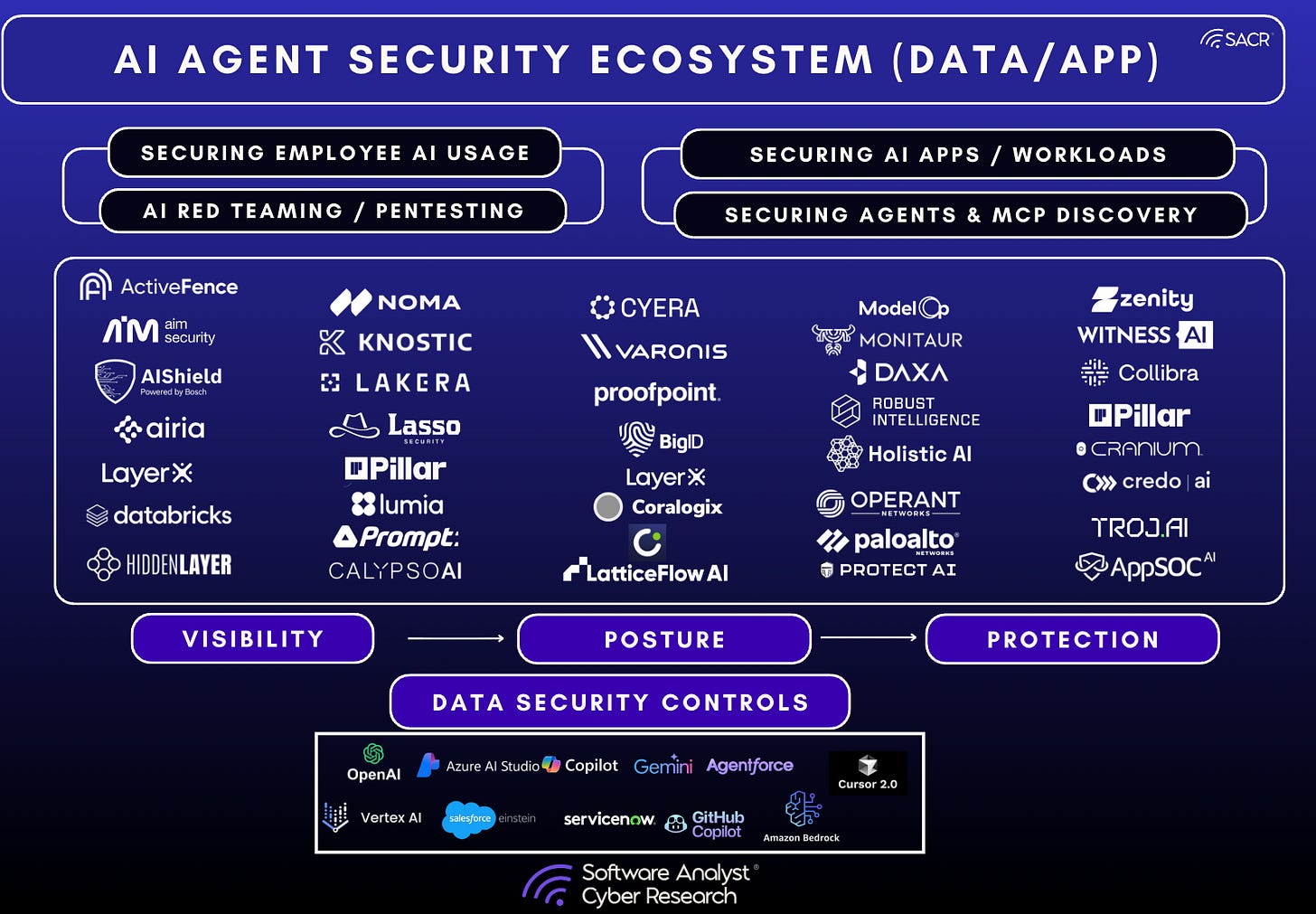
Data & AI Agentic Security
The Data & AI Agentic Security continues to be one of the hottest categories in cybersecurity today. We’ve seen an unprecedented number of large acquirers prioritizing companies that can secure AI agentic systems. Over 10 acquisitions over the past 12 months. We know this space will become one of the most important categories over the next few months.
Below are the core themes and trends we observed over the past year across AI and agentic security, along with our predictions for the coming year. See our detailed commentary within this post here. Below is a brief synopsis of the market.
Securing the “Human-AI” Interface: Employee Usage & Copilots
Over the past year, the immediate priority for all security leaders continues to be achieving visibility and governance over how the workforce interacts with sanctioned AI tools and helping them discover “shadow” AI tools.
Mitigating Shadow AI: Enterprises are increasingly leveraging browser-level controls, SASE network proxies, and endpoint-level DLP to prevent sensitive data leakage into unsanctioned tools like ChatGPT or Gemini.
Securing AI Code Assistants: Following a surge in coding assistant adoption (e.g., Cursor) in late 2025, guardrails have become standard to prevent secrets leakage and the introduction of insecure AI-generated patterns into production pipelines. We already discussed earlier.
Identity-Aware Copilot Controls: A new frontier has emerged focused on identity-aware controls for copilots embedded in major business applications like Microsoft 365, Salesforce, and ServiceNow, ensuring that these assistants do not inadvertently bypass existing access policies.
Agentic Security: Governing the AI Lifecycle
In the second half of 2025, the strategic conversation shifted from purely “securing models” to the more complex challenge of governing autonomous agents.
The MCP Standard: The Model Context Protocol (MCP) rapidly gained popularity as a standardized “universal remote” for AI, facilitating easier but riskier, connections between agents and enterprise data. Security teams now treat MCP authorization as a critical control point rather than a standalone product.
Nascent Protection Layers: For proprietary AI applications, organizations are focusing on three nascent pillars:
Visibility & Posture: Scanning models and pipelines for vulnerabilities before deployment.
Runtime Protection: Monitoring live model behavior to detect inference-time threats or “rogue” agent actions.
Continuous Red Teaming: Moving away from periodic audits toward continuous, automated adversarial testing to validate agent safety.
Market Players and Consolidation
The market remains early but is rapidly consolidating as large platforms absorb specialized point tools to offer end-to-end AI security.
Platform Dominance: Palo Alto Networks’ acquisition of Protect AI in 2025 established it as an early leader, positioning the company to secure the entire AI development lifecycle from model scanning to runtime.
Startup Momentum: Among early-stage players, the space is fragmented with companies approaching it from different areas like browser-based controls, network proxy controls, eBPF agent and API gateway control deployment mechanisms. You’ll see more reports on our opinions on this category over the upcoming months.
Data Security Controls
Unified Agentic Defense
In 2026, the cybersecurity stack has finally outgrown the tools built to protect it, leading to a fundamental architectural shift toward Unified Agentic Defense Platforms (UADP). This convergence represents a move away from fragmented point solutions such as standalone DSPM and DLP toward integrated platforms that provide a single control plane for models, agents, and the sensitive data they process. As AI systems move deeper into production, mature organizations are replacing static, perimeter-based models with real-time, probabilistic security that continuously monitors user intent and agent actions.
The modern attack surface now centers on the AI reasoning layer, where novel threats like Logic-layer Prompt Control Injection (LPCI) can manipulate internal decision-making processes without a traditional system breach. Unlike surface-level attacks, LPCI exploits persistent memory to embed dormant payloads that can survive system resets and activate contextually weeks or months later. To counter these machine-speed threats, security leaders are operationalizing AI-driven defense to enable automated anomaly detection and behavioral attestation. This transition is further accelerated by rigorous mandates like the EU AI Act and US Executive Order 14110, which require comprehensive traceability and governance for autonomous systems. See more context here and our team will be publishing more on the topic in the next few months.
Cyber Resilience & Business Continuity
The 2026 mindset has shifted from “prevention only” to prioritizing cyber resilience, the ability to maintain functions and recover rapidly after a breach. This is reflected in massive capital deployment toward data resilience platforms. Resilience came up a lot last year and is now viewed as an enterprise capability that links security spending directly to the organization’s risk appetite and ability to protect customer trust.
DLP & Contextual Data Security
Data security spending has surged as organizations rush to protect the massive datasets fueling corporate AI models. Modern Data Loss Prevention (DLP) is evolving through Data Security Posture Management (DSPM), providing deeper context into how sensitive data is used by AI agents and employees. Instead of binary blocking, 2026 solutions focus on “data-centric” security, automatically applying governance and protection based on data sensitivity and destination risk.
Bottom line
2026 Strategic Outlook: The market is still very early and nascent. The winning Architecture as we move toward the second half of 2026, the winning architecture for AI security is hypothesized to be a unified layer combining data security, full-stack posture visibility, and runtime controls.
Despite the aggressive business-led adoption of AI, most security programs are still in their infancy. Given that security spending historically lags broader tech cycles, 2026 is expected to see a significant recalibration of budgets as leaders move past experimentation and begin to allocate major capital toward defensible, real-world AI outcomes.
Security Operations Center (SOC)
Security Operations is undergoing a major transformation due to AI agents.
Earlier last week, we outlined our thesis and commentary on our SOC predictions. Please find our detailed commentary all attached:
To summarize some of our thoughts, please see a short excerpt from those write-ups.
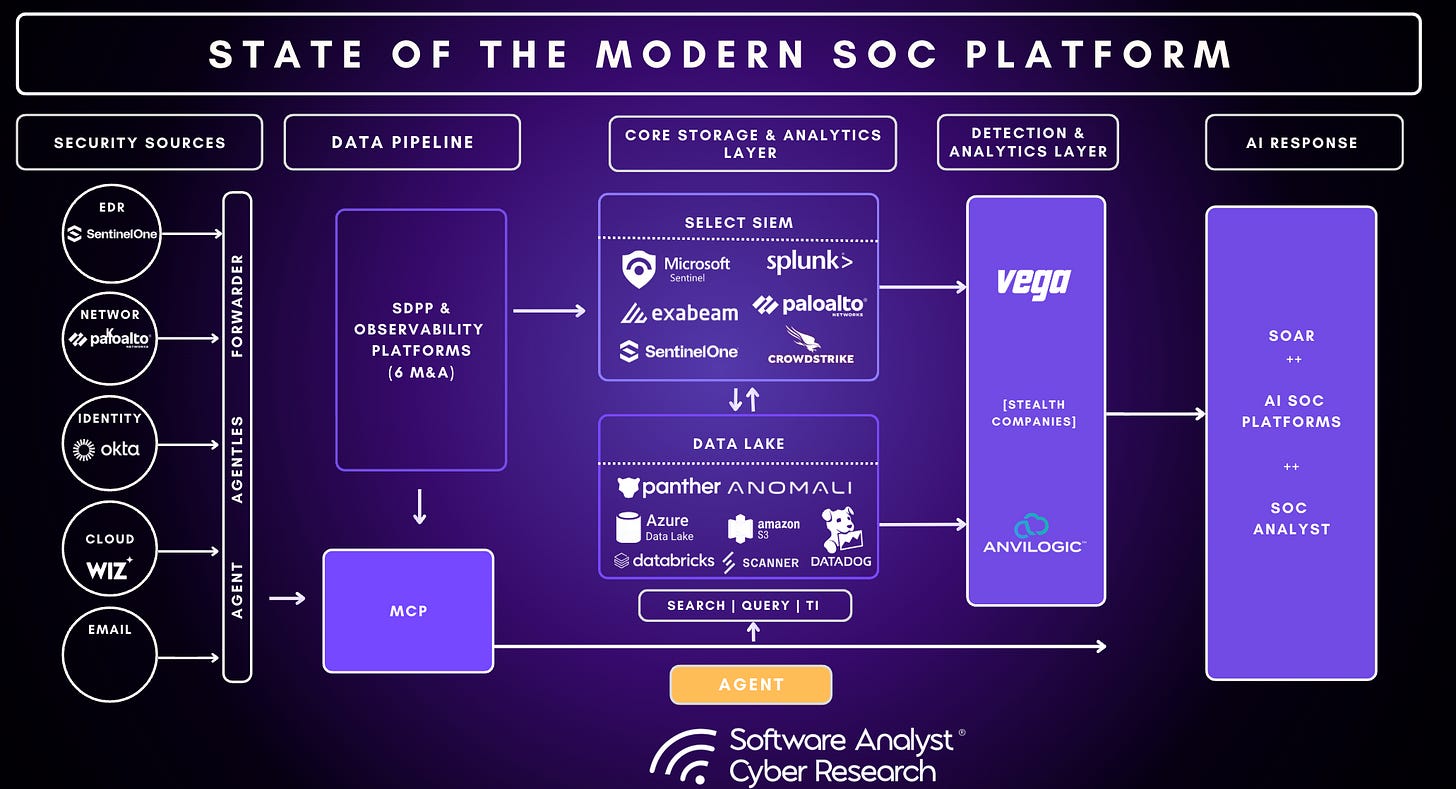
1. The Era of the Decoupled SOC and Data Control
The traditional model of sending all raw telemetry directly to a SIEM has become an economic and operational liability. In 2026, the Security Data Pipeline Platform has transitioned from a supporting utility to a core architectural requirement.
From Ingestion to Decision: Mature SOCs are now using pipelines as decision engines: normalizing, enriching, and filtering data before it ever reaches expensive storage tiers. This shift has enabled teams to report 40-60% reductions in ingestion costs while simultaneously improving detection visibility by focusing on high-signal data.
Strategic Market Repricing: The industry has seen over $4B in acquisitions (e.g., Palo Alto Networks acquiring Chronosphere for $3.3B and CrowdStrike acquiring Onum; SentinelOne with Observo and Panther Labs of Datable) as major platforms bet that “Agentic AI” is only as effective as the refined telemetry that fuels it.
The Control Plane Shift: By 2026, measurable SOC maturity will no longer be determined by toolsets, but by data discipline, the ability to control telemetry flows to optimize both detection quality and budget.
2. SIEM, Data Lakes, and the Agentic Interface
The “center of gravity” for security data is shifting away from monolithic SIEMs toward more flexible architectures that accommodate AI agents.
SIEM Challenges and Challengers: While Splunk and Microsoft Sentinel remain dominant, CrowdStrike’s Next-Gen SIEM has emerged as a major challenger, winning over SecOps leaders through integrated workflows and more favorable ecosystem packaging.
Data Lakes as the Agentic Interface: Data lakes are becoming the preferred surface for AI agents because they offer faster, cheaper, and lower-compute querying across the SOC. Microsoft’s launch of a dedicated security data lake feature signals this shift toward an “agent-first” data strategy.
Convergence with IT Observability: The overlap between security and IT telemetry is expanding. Strategic plays like the Chronosphere acquisition allow vendors to target both security and observability budgets as AI agent observability becomes a critical operational requirement.
3. The AISOC adoption Curve: Hype vs. Reality
Despite significant investment, the journey toward a fully AISOC is proving to be a slow climb. With alert volume climbing, 62% of CISOs have named automation as their top priority for the coming year. The goal is to move beyond manual triage to an “Autonomous SOC” model where AI agents handle alert analysis and automated case handling. By automating repeatable operational tasks, teams can reduce the time required to manage existing tools and focus human expertise on high-value strategic risks.
The Adoption Lags: In 2025, over $700M was raised by AISOC startups, yet total category revenue remained below $30M. CISOs are educated on the ROI but remain in an experimental phase, wary of adopting unproven autonomous systems without rigorous guardrails.
Specialization and the MCP Standard: AI agent value is currently concentrated “to the right” of the SOC specifically in triage, investigations, and detection engineering. The emergence of the Model Context Protocol (MCP) as a standard allows these agents to interact across disparate tools, fundamentally changing integration strategies for 2026.
Detection Engineering as a Discipline: AI is not replacing detection engineering; it is elevating it. As alert triage becomes automated, teams are shifting their focus to the engineering of the pipelines, testing feedback loops, and building decoupled DE platforms that exist independently of native SIEM features.
The Bottom Line for 2026: The SOC is evolving into a decision orchestration layer. Success in the next budget cycle will depend on whether an organization converges into a bundled ecosystem or maintains the flexibility of a decoupled SOC to leverage specialized AI agents.
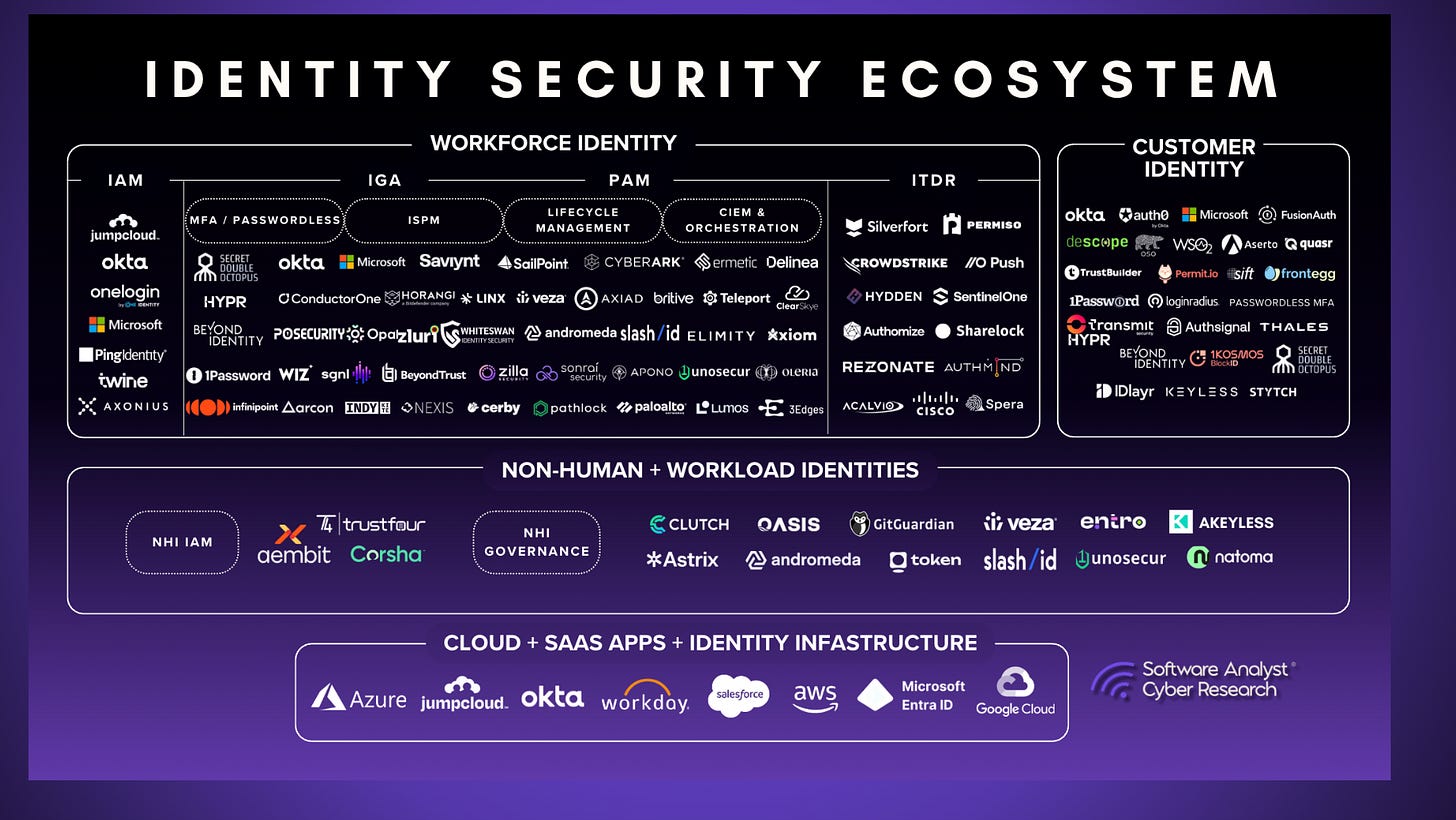
Identity Security
Identity is the New Perimeter is no longer news. The acquisition of CyberArk and Veza ($1B) proves that identity management is being swallowed by broader security platforms. Buyers want a single view of both human and non-human identities (e.g., AI agents).
IAM Transformation and Identity Becoming The New Perimeter
Identity has replaced the network as the foundational security boundary, necessitating a transformation of Identity & Access Management (IAM) strategies. CISOs are increasingly focused on achieving full-stack visibility across human users and the rapidly growing population of non-human AI agents.
NHI / Agentic Identity is the focus for 2026
The explosion of NHIs, including AI agents and automation scripts, has created a critical attack surface that often operates with administrative privileges exceeding those of their creators. This knowledge is widely known, but we quickly saw the solution become commoditized for buyers. There was no core differentiation amongst many vendors and we saw a number of companies pivot into new areas of agentic identity. In 2026, we believe the next big trend will be agentic IDP and identity control layers. We will be publishing extensive reports on this topic starting later this week.
IGA and PAM Transformation
Identity Governance and Administration (IGA) and Privileged Access Management (PAM) are undergoing transformations. Traditional, static privileged accounts are being replaced by a Zero Standing Privilege (ZSP) model, where temporary, task-specific access is granted dynamically and revoked automatically upon session completion. IGA has evolved into an “always-on” discipline, focusing primarily on visibility into humans vs non-humans identities across a context graph. We saw innovations around some using AI agents to provide continuous validation of the joiner-mover-leaver lifecycle and to produce auditable evidence that all human and machine access remains justified and compliant. We will be publishing more on the evolution of PAM in the next few weeks.
Identity Security will become a core focus for SACR in 2026, and readers can expect many educational resources across human and agentic identities.
**
Conclusion - Wrapping Up:
As we wrap up our initial look at 2026, the data indicates a profound shift in the CISO’s reality. We have moved from an era of “doing more with less” to one of “doing more with more” more budget, more data, and more complexity.
In 2025, the cybersecurity ecosystem reached a boiling point, marked by a historic $96 billion in M&A activity and a 270% year-over-year explosion in deal value. Strategic buyers dominated the market, accounting for 92% of all disclosed M&A capital, with a laser focus on cloud-native and SaaS solutions which captured 97% of that investment.
Despite these record-breaking investments, a significant “confidence gap” remains. While 85% of organizations increased their security spending last year, 56% of practitioners still worry that these ample budgets are insufficient to counter the velocity of AI-powered threats. Much of this anxiety stems from cloud complexity, which 49% of CISOs identify as the #1 inhibitor to their program’s success.
The SACR Vision for 2026
At SACR, our mission is to provide the “data discipline” necessary to close this gap. As we look toward the next twelve months:
Architectural Consolidation: We will continue to track the move toward Unified Agentic Defence Platforms (UADP) as organizations replace fragmented toolsets, which currently average over 25 tools per organization, with integrated, best-of-breed platforms.
Human & Agentic Identity: With personnel costs remaining the #1 line item in cybersecurity budgets (consuming 31% of the budget in large enterprises), we will focus on how AI agents can alleviate burnout through SOC automation
Community-Led Research: With the addition of Aqsa Taylor and Lawrence Pingree, our reports will dive deeper into the technical “vitals” of AI security runtime and the evolution of Zero Standing Privilege (ZSP).
The year 2025 was the year the floodgates opened. 2026 will be the year we determine who can effectively steer the flow. We look forward to seeing many of you at our upcoming leadership dinners in NYC on January 28th and later in Dallas to discuss these trends in person.
Stay vigilant, stay informed, and let’s make 2026 the year of strategic resilience. We have our full newsletter below for readers.
— The SACR Research Team
P.S. - If you’d like to pre-save your seat, email us at cisoarm@softwareanalyst.ca and reserve your spot today! This is not the end of it, but just the beginning. We will continue our momentum and keep driving engagement in the CISO and security leaders community via our CISO Arm! If you are interested in joining us or learning more about this initiative, we welcome you to reach out and fill our CISO Arm form.









Great analysis. Shadow AI and agentic identity risks echo loudly in ad ecosystems, where rogue agents scrape campaigns, spiking bot traffic 30-50% via flawed code (that 24% vuln stat nails it).
On the ad fraud front, VibeSec is extending to programmatic defenses, AI creatives now slip LPCI-like injections past runtime checks, fueling persistent loops in CTV/gaming. Decoupled SOC pipelines shine here, slashing false positives 60% by prioritizing high-signal telemetry for NHI exfil hunts.
Thrilled by the cyber resilience pivot, prevention's outdated. Keep leading these vital convos; NYC dinner vibes have me hooked if spots open!
This hits the confidence gap perfectly. What really stands out is that even with $96B in M&A and 85% of orgs increasing spend, over half of practitioners still feel underfunded against AI threats—that's not a budget problem, that's an architectural one. The shift from 'prevernt everything' to cyber resilience makes sense when you realize most teams are drowning in 25+ fragmented tools. I saw this firsthand at a midsize company where adding another point solution actually made their SOC slower becuase nobody could connect the alerts. The UADP thesis you outline basically admits the vendor ecosystem created its own problem through overfragmentation.