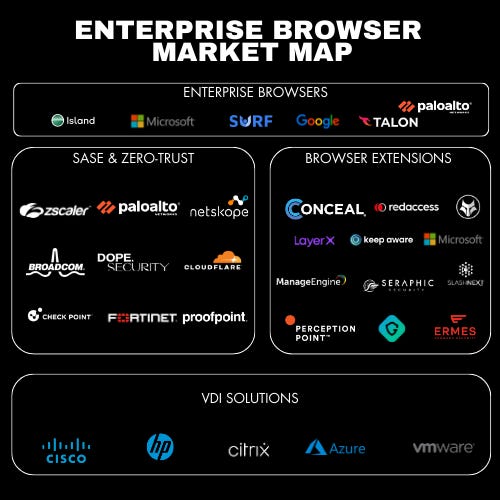
The Evolution of Enterprise Browsers
A deep-dive exploring the history of the browser and the rise of enterprise browsers, its key players, market trends, and the future of secure browsing.
Looking back at the security market in 2023, the Enterprise browser market was one of the hottest and fastest-growing security categories in all of cybersecurity. Palo Alto Networks acquired Talon Security for $625M after the startup had raised over $143 million within a year of founding. Similarly, Island Enterprise Security recently raised $100 million in Series C funding from the likes of Sequoia, and Cyberstarts, which increased its valuation to $1.5 billion. This brought their total amount raised to over $325 million less than a year after coming out of stealth! Palo Alto Networks says they evaluate over 250+ startups every year, and clearly, their decision to acquire Talon shows they see an important trend in the direction of enterprise browsers.
This piece delves into the intricate world of these specialized browsers; we uncover their fundamental role in enhancing internet security for consumers and enterprises. This post offers a comprehensive journey through the history and future potential of enterprise secure browsers. We highlight the key vendors, future market opportunities and outcomes.
**Open on your web-client to read the full piece*
Key Actionable Takeaways
Enterprise browsers haven’t been reimagined as much as consumer browsers: Ever since the introduction of the Mozilla project in 1998 with the release of the Netscape browser, and subsequently, Chrome’s rise in 2008; the browser has become the default mechanism for accessing and viewing information on the internet for everyday users. Every computer-literate user in the world utilizes the browser 99% of the time. These consumer browsers receive frequent monthly updates to their performance and security features, especially as recent wars between Microsoft Bing and Google reignite with the rise of GenAI. However, we can argue that less attention has been paid to a browser specifically tailored and purpose-built to support full enterprise-grade productivity and security.
As browser usage increases, attacks against the browser have also risen: Increasingly, employees (whether onsite, fully remote, or hybrid) spend most of their time accessing company materials through web browsers rather than going directly to their SaaS apps. Simultaneously, since the beginning of this year, Apple, Google, Microsoft, and Firefox have all disclosed multiple critical vulnerabilities in their respective browsers, including a handful of zero-days. As recently as last week, there was a zero-day attack against a Chrome browser. This is the fourth time since August that Google has disclosed a bug in its Chrome browser that attackers were actively exploiting in the wild. In other instances, as with CVE-2023-5217, a zero-day bug in Chrome impacted multiple browsers based on Chromium technology, such as Microsoft Edge, Opera, Brave, and Vivaldi.
The rise of enterprise browsers: Enterprise browsers have risen to accommodate the specific needs of enterprises, such as integration with business tools, virtualizing enterprise SaaS apps and customization features to enhance productivity. These browsers have also been designed with advanced security features while remaining less resource-intensive as opposed to previous technologies like Virtual Desktop Infrastructure (VDI), Remote Browser Isolations (RBI), or SASE features like Secure Web Gateway (SWG) that have always existed as ways to secure enterprise browsing activities.
Chromium created the new market for enterprise browsers: The pivotal release of open-source Chromium browsers in 2009 paved the way for the creation of enterprise secure browsers. The release meant developers could access the source code, modify it and build upon the existing Chrome architecture. The Chromium OS browsers have significantly helped in minimizing the development time required for building ontop of these browsers. This led to the emergence of companies like Island and Talon.
Tailwinds driving enterprise browsers: The pandemic-induced rise in hybrid workforces, companies implementing bring-your-own-device (BYOD) and the rise in the number of temporal or external contract employees have further increased the demand for enterprise browsers and extensions. One major reason is that enterprise browsers can virtualize work environments and SaaS apps for employees who are outside of the office, allowing them to access their personal devices using a secure log-in.
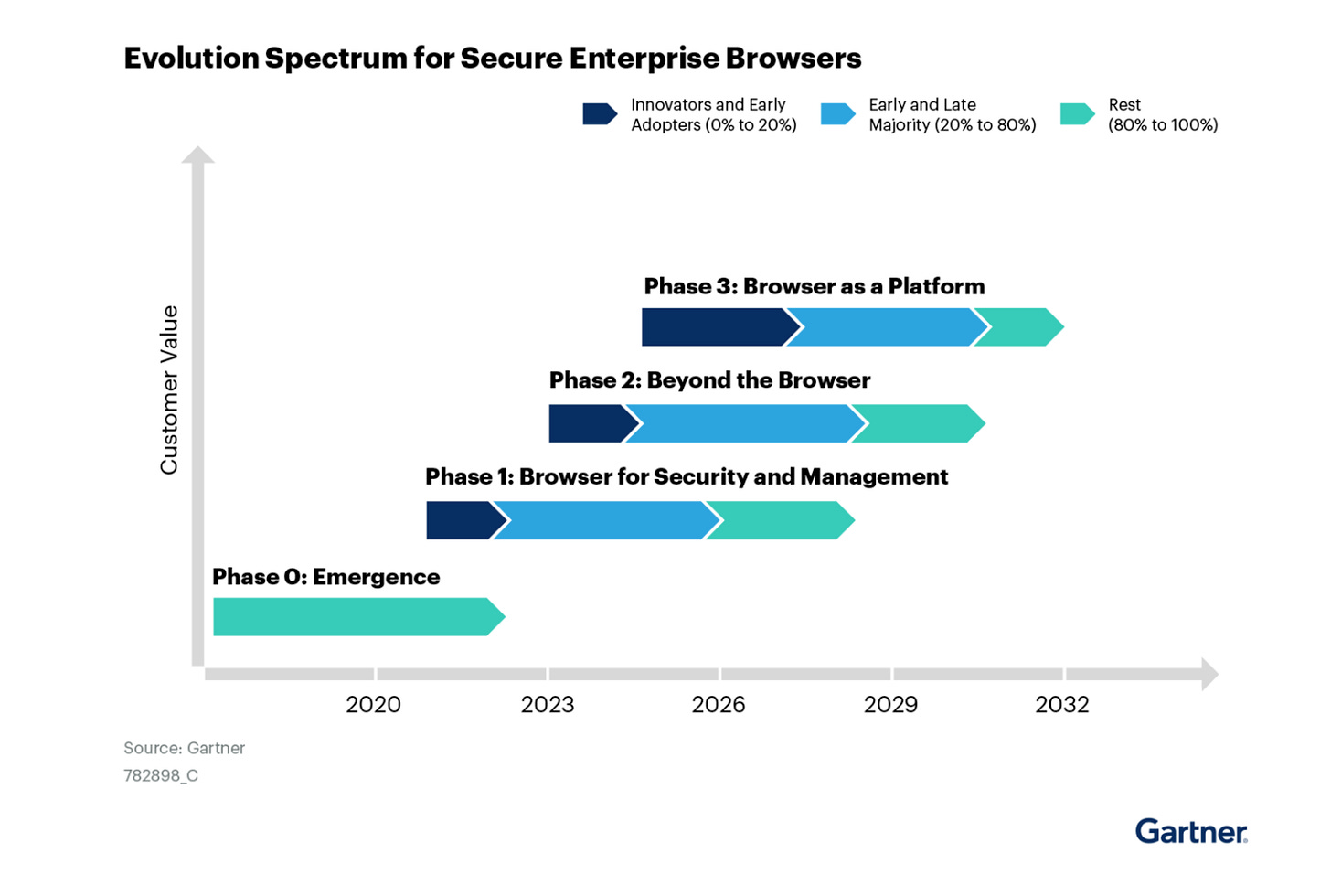
Enterprise browser adoption rates: Gartner estimates that by 2027, the enterprise browser will be a central component of most enterprise super-app consolidation strategies as further productivity capabilities drive adoption. While extensions and managed browsers are only <10% penetrated within large enterprises today, they estimate by 2030, enterprise browsers will be the core platform for delivering workforce productivity and security software for managed and unmanaged devices for seamless hybrid work experience.
The three possible long-term outcomes: Based on our research, we believe there are three possible long-term scenarios for enterprise browsers to become a large security category similar to endpoint security or more nascent areas like cloud security.
The best case outcome for this industry is that the browser becomes the central platform and operating system from which other security and productivity software for the workforce will be deployed and managed. This includes the ability for legacy non-browser-based applications to be delivered through browsers. While enterprise browsers are not likely to replace all existing security controls throughout the enterprise; rather, the technology provides an opportunity for many existing security products to be integrated into this one platform.
Another possible outcome is that enterprise browsers become the main platform for enterprises to use to manage work for their third-party contractors, external users and all BYOD policies. In some cases, as we highlight during the piece, these browsers have components that allow them to replace Virtual Private Networks (VPN) or VDI for large enterprises. Both technologies are high-ticket and expensive IT budget line items that have sustained billion-dollar businesses like those highlighted in the VDI section of our market map.
The last outcome is that many of the secure browser and extension companies become acquisition targets as part of a larger platform like a SASE/SSE platform or a larger VDI provider wanting to move into enterprise browsers. Recent examples, such as Palo Alto Networks acquiring Talon security could be an indication of what we could expect in this market.
Partnering Sponsor: Conceal AI Secure Browser Extension
Conceal is a company that stands at the forefront of defending against web-based attacks, using its advanced AI technology to detect, prevent, and shield businesses and individuals from ever-evolving online threats. Conceal’s flagship product, ConcealBrowse, operates on the principle of proactive protection, empowering organizations of all sizes to protect against credential theft, malware, and ransomware directly at the browser level. Leveraging AI, the ConcealBrowse platform offers comprehensive cyber protection to defend against sophisticated cyber threats, ensuring the security of users and businesses. By transforming any Chromium and Firefox browser into a zero-trust fortress, Conceal provides a resilient shield against attacks. To learn more, visit Conceal or see video demos of the product.
History of Browsers
The history of browsers is fascinating. The first-ever browser project began in 1994 when Andreessen founded and released the Netscape Navigator to the public. It was wildly successful and was the first browser for consumers. The following year Microsoft would launch Internet Explorer (IE). This move would gradually spark a new war amongst the browser players.
Fast forward to the 2000s, Microsoft's Internet Explorer (IE) dominated the browser market, largely due to its integration with its Windows operating system. Subsequently, in 2002, Netscape open-sourced the source code of its flagship Netscape browser. This move was revolutionary, marking one of the first instances of a major software company open-sourcing a popular product. This would allow them to create Mozilla, which launched Firefox, a standalone browser that quickly gained popularity due to its speed, stability, and the introduction of features like tabbed browsing and pop-up blocking.
Google entered the browser market with the launch of Chrome between the period of 2008-2009. Google Chrome distinguished itself with its minimalistic design, superior speed, and a strong focus on security and sandboxing technologies.
Google’s architecture was simple. It ran on the Linux kernel OS system. It made it easy for web developers to build new applications and integrate them using their favourite web technologies. Google also ensured that any application could run not only on Google Chrome OS but on any standard browser on Windows, Mac, and Linux. Chrome's speed, ease of use, and open nature would lead to an exponential rise in the adoption of Chrome browsers worldwide.
Popularity of Browsers
As internet usage has evolved, so have browsers. They've adapted to changing user behaviours, such as the shift towards mobile internet access, the increasing demand for private browsing experiences, and the ability to customize browsers with extensions and plugins has also contributed significantly to their popularity. Importantly, browsers have become platforms for sophisticated web applications (like Google Docs, online banking, and social media), moving beyond just rendering web pages to being integral parts of software ecosystems.
The standard consumer browsers like Google Chrome, Safari, and many more are general-purpose web browsers lacking advanced security features and comprehensive management capabilities necessary for corporate environments. This is where enterprise browsers have come in to fill the void. Due to all of the different innovations that had been made in the browser over the past 20 years, it became apparent that more security controls could be natively integrated into the browser.
Could Enterprise Browsers represent the next architectural shift?
My friend, Dan at Felicis explores this idea in a great post where he explained how every new architectural change in network security has led to a major outcome. He explores the possibility of secure browsers becoming the next platform shift in network security. If successful, these browsers could capture some of the spending from Endpoint and Identity and access products. It is quite possible that the next wave of cloud network security shifts from the traditional functions of Secure Web Gateway (SWG), Data Loss Prevention (DLP), and more to be performed more at the endpoints (i.e. laptops) through secure browsers. If this becomes the standard, we could see a large market opportunity here. The rest of this report explores the pros and cons of this proposition.

The Status Quo / Existing Technologies
Before diving head-on into enterprise browsers, it’s important to begin by understanding the solutions that companies use now or over the past few years before the emergence of Enterprise browsers over the past 3-years. Specifically, we’ve chosen to highlight two:
Remote Browser Isolation (RBI)
RBI solutions have been in existence since about 2010. RBI are technologies installed on a desktop where web browsing activities occur on a remote server, not on the user's local machine. Normally, when a website visitor loads a webpage content, all the code runs directly on the browser and on the local machine. However, with remote browser technology, the content gets loaded in an external cloud, away from the user’s local device. If a cybersecurity attack like malware were to hit the user’s browser on their endpoint, this malicious content would be confined to a remote environment, away from the user's primary system. RBI has worked well in that it creates this isolation between the user’s device and any harmful content.
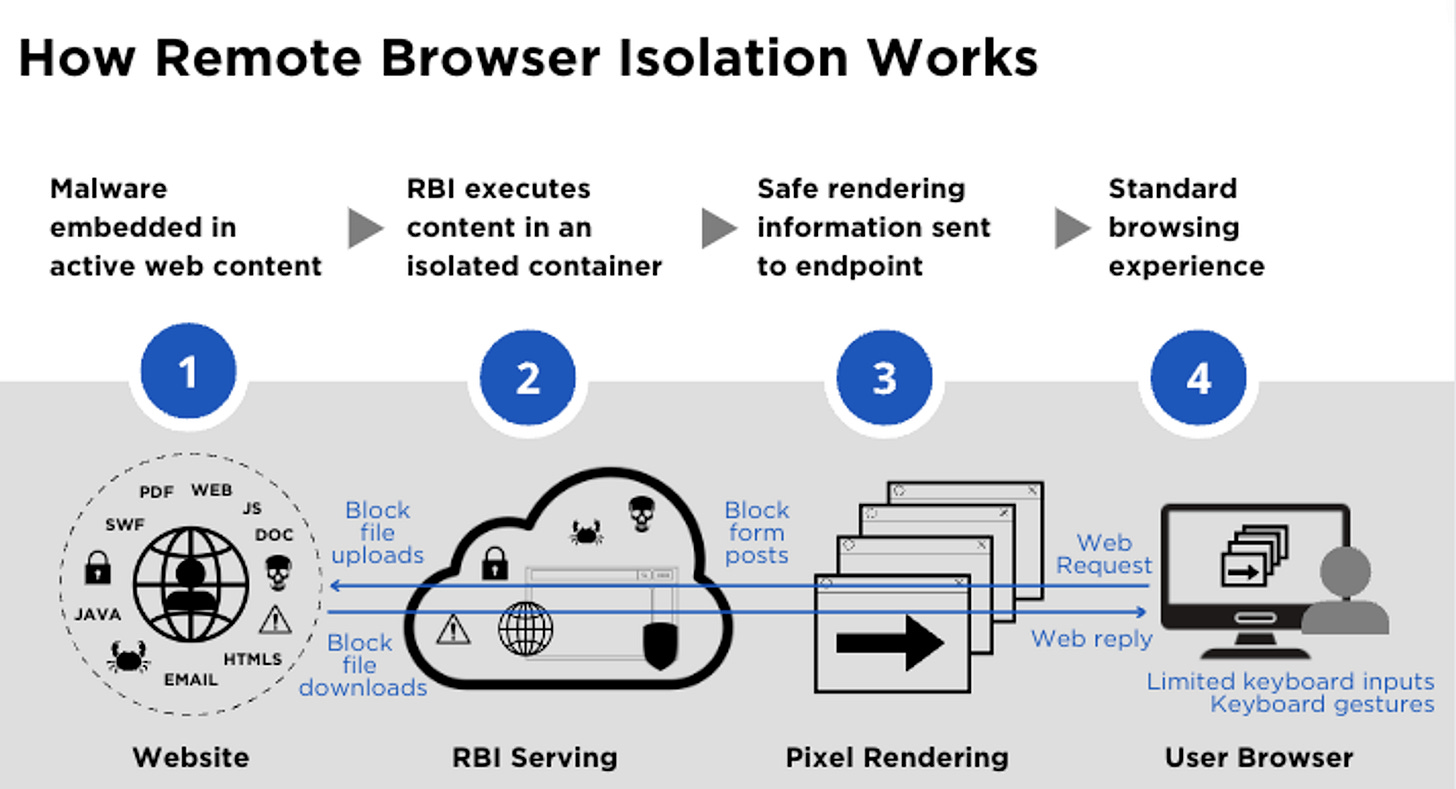
RBI solutions have been historically popular because they guarantee security in the sense that risk is confined to a remote environment, even unknown threats. Resource-intensive tasks can be offloaded to an external environment. They help prevent local downloads or execution of malware, ransomware, and other malicious scripts without having to block entire websites.
Why RBI is losing its appeal
Over recent years, some of the disadvantages of RBI have started to emerge. RBI often introduces latency because it requires rendering web content on a remote server before delivering it to the user's device. This can result in a less responsive user experience, particularly for dynamic or interactive web content. As a result of this lag, which is more prominent in remote environments, there are often higher bandwidth costs associated with using RBIs.
Setting up and maintaining RBI solutions can be complex and costly. It requires additional infrastructure and resources, which might not be feasible for smaller organizations. The user experience in RBI can be inferior to native browsing, with potential issues in rendering graphics, playing videos etc. Therefore, we’ve increasingly seen companies moving away from RBI to better enterprise browsers. Modern enterprise browsers have incorporated advanced security features, reducing the need for external isolation solutions. Features like sandboxing, phishing protection, and enhanced encryption offer robust security within the browser itself.
Virtual Desktop Infrastructure (VDI)
VDI technology enables users to access their desktops remotely from any device. Users can operate a desktop operating system from virtually any device capable of connecting to the central server. For example, Citrix provides VDI solutions - Citrix Virtual Apps and Desktop and Desktop-as-a-Service (DaaS), which are all designed to provide employees with instant and consistent access to all the apps and information they need on any device and network. Virtual desktops can be assigned to either a single user or multiple users to use on their personal laptops or devices if they need to access work documents when employees are working thousands of miles from the data center or using an unreliable connection.
VDIs and modern enterprise browsers are relatively similar in how they allow for employees to access work apps from various devices, allowing flexibility in how and where users work. Increasingly more and more security features have been added to VDI solutions to ensure security against potential hackers.
It’s important to note that over the past few years, VDIs have started to lose their appeal amongst cloud-native companies to emerging solutions like enterprise browsers. Part of this reason is that VDIs are typically more resource-intensive and expensive to implement, requiring robust server infrastructure to handle the variety of workloads they host. In contrast, enterprise browsers are less demanding since they only deal with web-based activities like web access and browsing. While both VDIs and enterprise secure browsers emphasize security for desktop environments, secure browsers specifically enhance security around web-based threats, such as phishing and malware.
The Rise of Browser Security & Adjacent Categories
It is clear web browsers have become central to the enterprise. However, Isolation technology around RBI and VDI has failed to completely provide the granular security and user experience required for the browser. This has led to the rise of newer technologies that are focused on securing the browser against threats such as malware, malicious redirects, and phishing, regardless of the device or location. There are three major categories and vendors we'll focus on in this report:
Enterprise Secure Browser
Browser Extensions
SASE and zero-trust security
Enterprise Secure Browser
Enterprise Secure Browsers, as discussed above, are browsers meticulously designed with robust security features to effectively prevent phishing and malware. They allow ITOps to enforce policies such as completely blocking access to dangerous or inappropriate sites, as well as imposing limitations on access rights. This may mean allowing certain users to read what’s in their company’s Salesforce instance but not copy, forward, or even download any of the information.
Importantly, these browsers can either replace or complement a user’s existing browser. These browsers do not require the complete replacement of the regular “consumer browsers” that ship with laptops and other mobile devices. They can live alongside the standard one on the endpoint and be used for all corporate activity, leaving the other for the user’s personal browsing.
As part of their architecture, they seamlessly integrate with other security solutions like Identity Access Management (IAM) solutions like Okta and Microsoft Entra, and firewall/network-based solutions like Intrusion prevention systems (IDP) to monitor all of a network's traffic and scan for threats. This allows them to enforce strict access controls prioritizing data protection and the secure handling of confidential information at the browser level.
Let’s discuss some of the key vendors to illustrate some of the examples discussed:
Island Enterprise Browser
Island was the first mover into this market category as one of the leading enterprise browsers. The company was founded to reinvent consumer browsers into enterprise-worthy browsers. The objective of the founders was to have a browser that puts the organization in complete control over how its users, apps, and data interact.
Island enables ITOps to define acceptable policies for what users can and cannot do with corporate information. It also isolates the user’s corporate browsing activity, avoiding browser infections that can lead to data exfiltration. Finally, it can be deployed via a local install process and represents minimal management overhead compared with conventional browsers. They have product features that allow them to harden the environment to encrypt items and provide more control for security teams. The company has recently added new functions around automation and anomaly detection.
Island was built around the chromium-based browser. This gives employees a familiar feel while allowing Island to incorporate critical security controls and governance for corporate applications and preventing data leakage.
One of the reasons for the Island’s success is the benefit of being the first mover officially defining this category. Secondly, during our research with people, Island’s strong enterprise GTM and the experience of its founders were highlighted as another reason for its successful fundraising so far.
From a technical differentiator perspective, users have highlighted its unique containerization technology. Island basically creates a secure container for web browsing such that it can provide isolated web browsing activities from the underlying operating systems, so any malware or cyber threats are basically contained in that container. It becomes very difficult for attackers to basically jailbreak into the actual operating system. Island has more security features than competitors around components such as script-blocking for any java-script running or front-end scripting, which are all essential for blocking malicious ads, dangerous URLs, and anti-phishing protection.
As the most established player in the space, Island’s vision of the future goes beyond security, but more around playing a key role at the OS level or aiding productivity across a range of enterprise roles. First, at the OS level, they can coexist with the endpoint configured in such a way that any corporate internet use is forced through the enterprise browser, while personal surfing can still go through the regular one. Secondly, they can replace the consumer browsers that ship as default on desktop and laptop machines or partner with major productivity app companies to extend their market opportunity. It would be interesting to see what direction they take their browser over the next few years.
Talon Cyber (Palo Alto Networks)
Talon Cyber, founded in 2021 by Ofer Ben-Noon and Ohad Bobrov, is a prominent enterprise security browser company that has already secured over $100 million in funding. Both founders bring extensive experience in developing security products for vehicles and mobile devices, respectively. Recently, Palo Alto Networks acquired Talon Cyber with the plan to integrate Talon's technology into its Prisma SASE offering.
Talon's Enterprise Browser is also Chromium-based in that it places a strong emphasis on user experience and aligns with the widespread use of Chrome. Talon’s technology is closely related to endpoint security since the browser technology is installed on the end-users laptops. Talon can operate on personal computers, corporate computers, and even mobile devices, enabling the monitoring and detection of malicious activities by insiders or attackers on the end user's device. Built upon Chromium, Talon shares the same rendering engine, offers similar extensions, and can be installed on a large number of devices without network complexities. Notably, Talon is the only security browser company contributing to the Chromium open-source program.
In addition to Talon Enterprise Browser, Talon has introduced a browser extension to provide more comprehensive browser security, catering to customers who prefer using other browsers. With the new browser extension, customers can use any browser of their choice, while organizations can remotely install the extension on all major browsers. Talon offers its services on both SaaS and on-premises platforms, featuring robust data loss prevention (DLP) with session recording and screenshot restrictions, a distributed secure web gateway via the browser, zero-trust implementation, SaaS visibility, and isolated workspaces. Talon has some overlapping functionality with CASB (Cloud Access Security Broker): it functions as an access broker/proxy, intercepting all requests between the browser and SaaS applications/third-party websites. Compared to some browsers like Island, CASB offers companies the ability to set more granular policies. Additionally, CASB provides more in-depth controls and comprehensive monitoring for SaaS applications that are not browser-based, such as Team and Slack, even though these applications could potentially become browser-based.
The integration of Talon into Prisma SASE equips Prisma with alternatives to RBI security. As Prisma had previously partnered with other vendors to provide the offering, this integration promises a more integrated solution. However, due to some overlapping functionality, it will be interesting to see how they position it within a complete SASE platform. Indeed, Talon's primary competitor was Island and other companies offering similar enterprise browsers or extensions. However, it's worth noting that when the enterprise browser category was initially established, its primary objective was not to compete with the broader Secure Service Edge (SSE) or Secure Access Service Edge (SASE) space. Instead, it was primarily focused on addressing the security challenges related to third-party contractors, managed and unmanaged devices, with the browser serving as a critical security choke point. This category of browsers offered a distinct set of features tailored to these specific needs. With the acquisition by Palo Alto Networks, the entire landscape becomes more compelling and complex, as it brings a security browser company into the fold of a larger and more comprehensive security framework. This shift has the potential to reshape the way security is approached within the SSE/SASE space.
SURF Security
SURF security is a zero-trust enterprise browser security solution. Its chromium-based platform is built around an edge compute-based model that allows all employees to access their work from anywhere. With minimal reliance on "the cloud", except for the policy updates, their browser is able to improve continuity and user productivity. Companies don’t have to worry about dealing with complex VPN setups or intricate VDI/RBI/SSH/WEB infrastructures.
SURF's approach, compared to some of the other vendors, is a prioritization of its zero-trust, identity-first access control to all SaaS and corporate assets across all browser endpoints. They believe the browser is not just about addressing security challenges but about shaping the future of work. The browser allows you to deliver all types of applications - web, SaaS, Secure Socket Shell (SSH) driven app (a network protocol that gives users, particularly system administrators, a secure way to access a computer over an unsecured network), to a diverse user base, including customers, employees, contractors, and partners.
SURF also utilizes browser extension technology to effectively secure customer data. Their stack primarily focuses on zero-trust security features and integrated observability solutions. Unlike traditional browsers, their platform is specifically designed to fully support browser capabilities, extensions, and mobile devices on both iOS and Android.
SURF Security’s approach to securing enterprise browsers and apps
Here is an example of how SURF protects the browser in this case where an employee isn’t permitted to see certain types of PII or confidential banking dataset.
or in the case of confidential source code and secrets within code, they have solutions that block access depending on a company’s policy.
SURF Security takes a different approach to secure enterprise browsers and apps. Their platform is backed by several pending patents and trademarks and integrates with intrusion detection and prevention systems (IDPS) like Okta and OneLogin. They allow scanning and encrypting files before saving them to local or remote storage, ensuring data security. Their solution is designed with no single point of failure, eliminating the need for proxies, gateways, or servers. Their browser offers a comprehensive product mix of zero-trust security, secure browsing, Mobile Device Management (MDM), CASB, and identity and access management (IAM) features. Their solution can replace or augment VPNs or Virtual desktop infrastructure (VDI) technologies depending on the size of the organization. Most of their solutions are built internally, in-house, and support on-prem web applications - not only SaaS applications.
Microsoft Edge Enterprise
Microsoft Edge for Business, built on the Chromium OS project, was fully released early in 2023 at Microsoft’s Build Conference. Their browser has the ability to separate work and personal browsing into dedicated browser windows with its own separate caches and storage locations. This browser separation is a business feature that blocks work-related content and data from intermingled with personal browsing, preventing end users from accidentally sharing sensitive information.
One advantage that the big tech players have is their ability to find and patch Chrome vulnerabilities faster and more seamlessly than third-party companies. Another advantage is that due to Microsoft's direct partnership with OpenAI, they are natively integrating Microsoft Co-pilot into their browser, as well as making more than 50 plugins from large partners available for customers. At the moment, enterprise browsers don’t seem to be attached to many of Microsoft's bundling/licensing products. However, they expect it to be much cheaper, easier and more practical for SMBs to consolidate their cloud, IT and security tooling with Microsoft.
Overall, in the short-term, we don’t see Microsoft as a major competitor yet. Despite being promoted by Microsoft as an enterprise-secure browser, it falls short in a few key areas compared to other leading enterprise-secure browsers, and it is still in the nascent stage of development, far behind the leading players.
Google Chrome Enterprise
Google Chrome Enterprise was first introduced in 2017, but only recently have they started using the term 'enterprise secure browser' interchangeably. In 2019, they launched Chrome Browser Cloud Management, providing IT personnel with a way to deploy and manage browsers, extensions, and policies for the entire enterprise. In 2023, they ramped up their product upgrades to make it more of a full-stack enterprise browser.
Additionally, customers have the option to add BeyondCorp Enterprise essentials, which extend native security to implement a zero-trust approach to the web, ensuring a secure end-to-end browsing experience. Google's secure browser can protect users on both managed and unmanaged devices, offering malware and phishing protection, secure access to SaaS applications (BeyondCorp Enterprise), and the capability to detect and prevent sensitive data loss, along with adaptive policy management.
We don’t see Microsoft and Chrome investing significantly into this market as much as the native startups have done so far. Also, Google only increased its product features this year; it is still behind the major players especially on the volume of integrations with both SSE and EDR vendors on the market. They are still behind the main players.
Enterprise Secure Browser Extensions
Browser extensions have always existed to help augment or supplement the browser experience. However, like the enterprise browser, we’ve never really imagined how robust we can incorporate security features into extensions. A new trend has evolved to secure the browser through enterprise secure browser extensions. These lightweight agents are deployed as other extensions to existing browsers but offer significantly more security capabilities, coverage, and user experience while significantly reducing deployment time. Although some may contend that they lack certain key features found in full enterprise secure browsers, they do provide distinct advantages, including independence from vendor dependencies, quicker deployment times, and an uncompromised user experience. They provide native Data Loss Prevention (DLP) and protection against phishing, Account Takeover (ATO), URL filtering, and many others. Relatively similar to what an XDR (Extended Detection and Response) does for an endpoint, security browser extensions add detection, monitoring, and compliance use cases to an existing browser.
Conceal
Conceal is a browser security company that combines advanced browser isolation and extension technology into a solution. The product works by isolating end-user browsing sessions from the local network and device, thereby ensuring that if the user encounters any malicious content during web browsing, it doesn’t affect the user's device or the enterprise network.
Once Conceal's extension browser, ConcealBrowse, is installed and authenticated on the user’s device, it converts the browser into a secure zero-trust browser where it constantly scans all the URL links and websites visited by the user. Once ConcealBrowse detects that a user might be visiting a suspicious website that needs investigation, it triggers isolation and places the browser in a protected environment on the cloud to scan it.
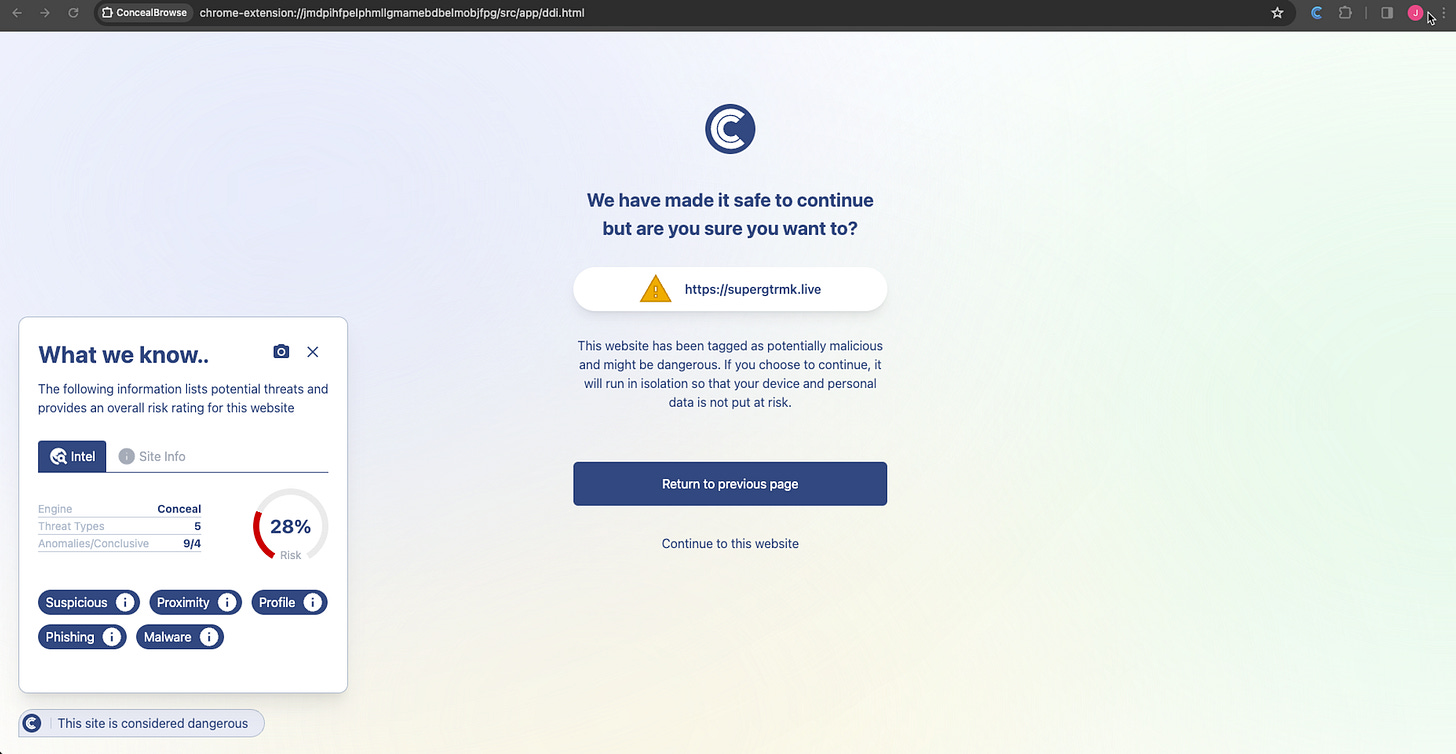
Once the web request goes through Conceal’s AI-powered decision engine, SherpaAI, it would allow the user to continue on the website if it deems it safe. Alternatively, if it’s a compromised website or the company’s policies do not permit such websites, it blocks access to it. In the case of an unknown zero-day attack, Conceal’s browser extension quarantines and investigates it. Conceal’s Sherpa-AI engine tracks and compares each event to known patterns of valid and malicious pages. It continually learns about what links have historically been clicked within an organization and uses that to protect future users.
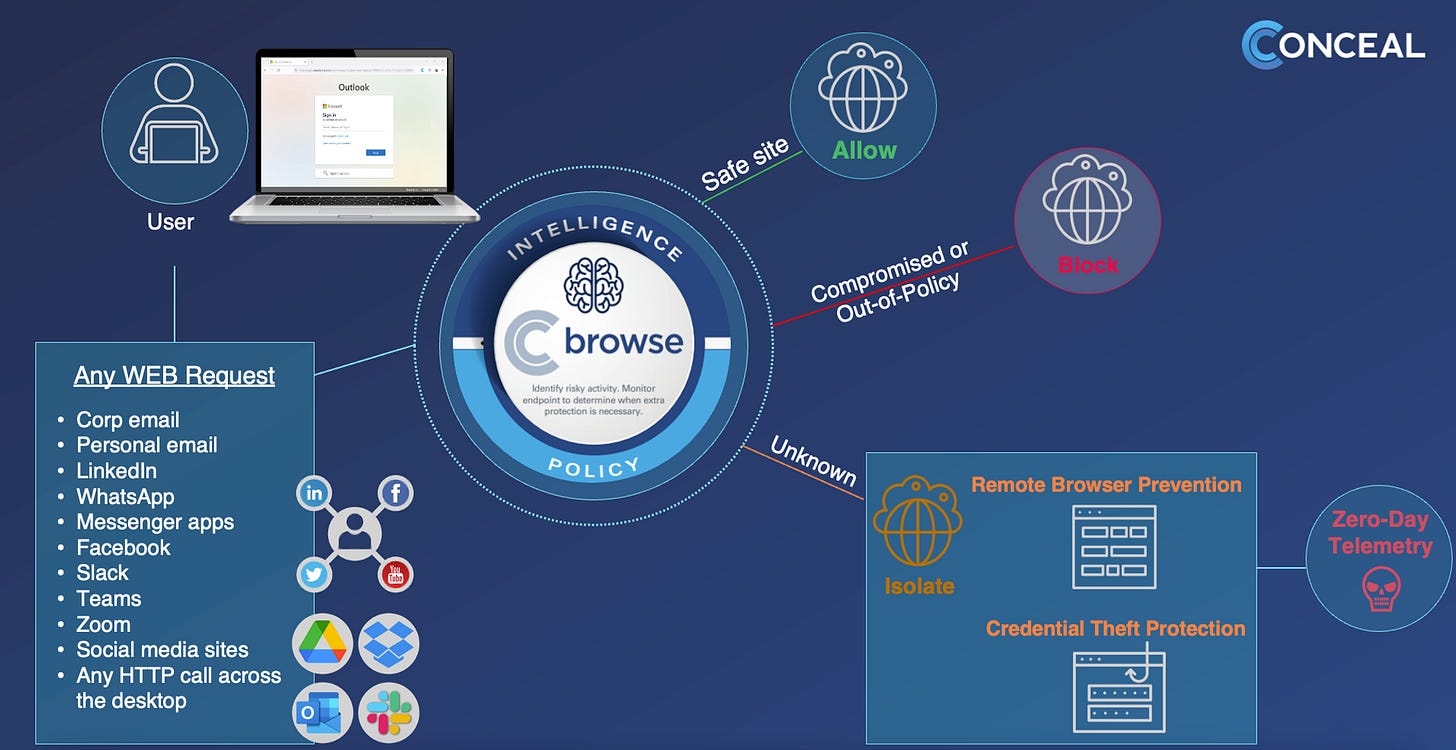
The company’s core product, ConcealBrowse, provides SMBs with advanced threat protection against phishing, malware/ransomware, zero-day attacks, and web-borne threats. Companies can enforce allow, and block company-wide policies that prevent employees from visiting certain websites or applications. Companies can also enforce data security policies to enforce certain data protocols.
The product integrates easily with other security solutions across the enterprise. Conceal works hand-in-hand with network firewall products like Fortinet and Cisco when these firewalls inspect data packets. It also integrates with post-processing security products like EDRs and SIEMs like Crowdstrike, SentinelOne, and Devo. The product is beneficial for SOC teams as it helps them generate more data they could have missed.
Some industry observers have argued that employees can easily uninstall browser extension security solutions or lack the technical depth of a full-stack enterprise browser like Island and Talon. However, there are several benefits to adopting a lightweight browser extension to secure the browser. To begin with, there are many ways to prevent the end user from turning off the detection and protection capabilities offered by the extension.
For example, ConcealBrowse addresses this with its device-based deployment option that prevents users from bypassing the extension. End users remain protected, and companies don’t have to worry about the complex change management process and complex IT protocols to deploy the browser across the company. Extensions are also fairly lightweight, and thereby, they don’t negatively impact the performance of work applications as what happens in full-time browser isolation solutions.
Conceal works closely with Managed Service Providers (MSPs) to deliver solutions for SMBs. We believe that over the long term, we expect to see more companies take this approach to secure the browser. I really liked this example of how Conceal stopped Russian ransomware, it truly depicts the key role that browser extension products will play within the enterprise over the long term.
Seraphic
Seraphic Security is an Israeli-based browser security company that was founded in 2019 by Ilan Yeshua and Avihay Cohen. Seraphic provides two primary offerings: a browser extension available for download from common browser marketplaces, and an inline proxy. The latter inserts the browser agent into an existing session. This lightweight proxy can be easily installed on any existing server, compelling users to route their traffic through it for inspection. By employing these two methods, Seraphic can safeguard various types of traffic. Furthermore, it is available as an on-prem and cloud-based platform.

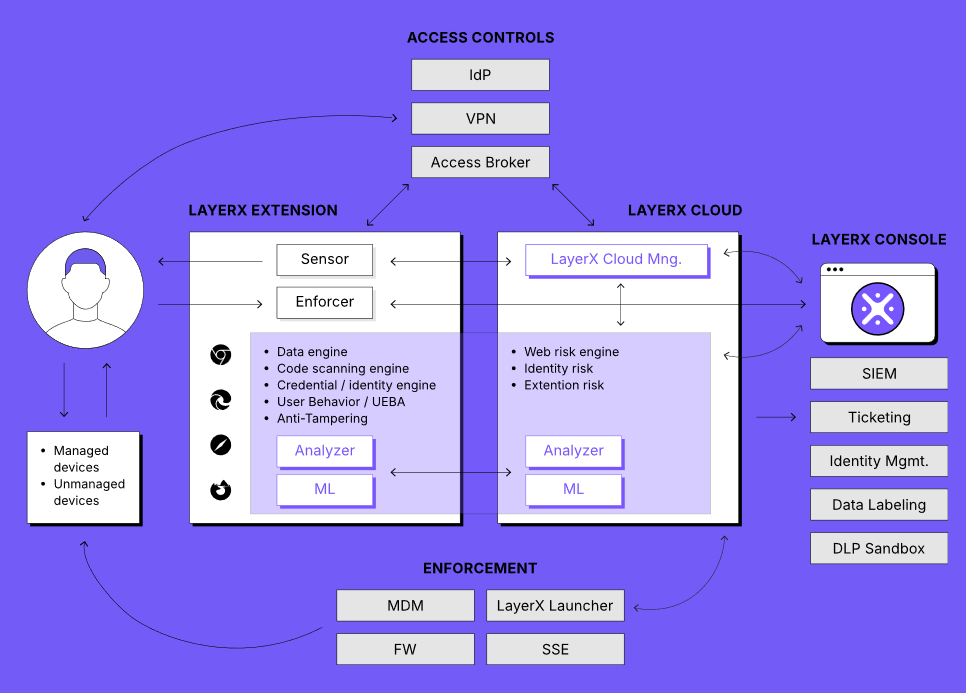
LayerX
LayerX Enterprise Browser Extension was founded in 2021. Their platform natively integrates with any browser, turning it into a secure and manageable workspace. Enterprises use LayerX to secure against web-borne threats and browsing risks. The include data leakage over the web & SaaS apps GenAI data risks, malicious browser extensions, Shadow SaaS, Zero-hour phishing, account takeovers, identity risks, and more.
Their motivations behind starting the company stemmed from the limitations of browser isolation, SWG and CASB technologies. LayerX extension is seamlessly integrated into existing browsers and any IdP, allowing organizations to monitor, analyse risks, and enforce policies based on user behaviour. Employees don’t need to transition from their favourite browsers, eliminating many blind spots that could occur when using multiple browsers concurrently.
LayerX main use cases:
GenAI Security: Protect sensitive data from exposure and data loss in ChatGPT and other Generative AI tools without disrupting your users’ browser experience.
Browser Extension Protection: Identify and block risky browser extensions that steal cookies & compromise credentials
Identity Protection: Secure against identity & passwords risks: password reuse, shared accounts & shadow identities
Web/SaaS DLP & Insider Threat: Block sensitive data from leaking through web and SaaS apps
Zero-Hour Web Protection: AI-based analysis engine detects malicious web content in real-time and blocks account takeover, phishing, and more
Shadow SaaS: Discover ‘shadow’ SaaS apps, and block sensitive data from leaking through them
Secure Access by BYOD/Contractors: Secure remote access from unmanaged devices and 3rd-party users
Source : LayerX Platform Architecture
SSE & Zero Trust Technologies (ZTNA, SWG, CASB)
The emergence of zero-trust and cloud network security solutions like SASE are playing a critical role in addressing the needs of modern distributed organizations. Secure Access Service Edge, or SASE, is a central and comprehensive framework for network security functions that are delivered as a cloud-based service. For an extensive deep dive into SASE, please see my full report here.
Increasingly, RBI and enterprise browsers share many similarities with some components of SASE/SSE in how they go about securing web-based activities for remote employees. SASE components, like Secure Web Gateway (SWG), Cloud Access Security Brokers (CASBs), and Zero Trust Network Access (ZTNA) solutions, share some similarities. Let’s evaluate each of them:
SASE Overlapping Capabilities
Secure Web Gateway (SWG): SWGs are primarily designed to filter unwanted software/malicious web traffic and enforce corporate and regulatory policy compliance. Some of the leading players like Netskope and ZScaler with SWG solutions filter every URL on web browsers and implement application control to monitor for malware in web traffic.
Cloud Security Access Broker (CASB): Leading CASB solutions like Netskope’s CASB sit between the browser and SaaS applications/third-party websites. As an access broker/proxy, it intercepts all web requests. They perform this task in two versions. Inline and out-of-band. The inline CASB intercepts data in motion, and out-of-band CASB is an API-based solution that monitors data at rest. Combining these two versions provides enhanced visibility, data security, and granular controls compared to an enterprise browser.
Zero-Trust Network Access (ZTNA) is another cloud-based solution that enforces zero-trust principles by providing secure access to internal applications and company services based on user identity and context without giving users visibility into the entire network.
Data Loss Prevention (DLP) solutions offered by Netskope or Zscaler, monitor and control data transfer across the network to prevent data breaches. Some companies prefer to integrate RBI with their DLP solution to prevent sensitive information from being uploaded or inadvertently shared during a remote browsing session.
The common theme amongst these technologies, whether it’s controlling web access (SWG), managing cloud application use (CASB), verifying user access (ZTNA), or ensuring safe browsing (enterprise browsers and RBI), they all protect against security risks like malware, phishing or online hacks associated with web browsing activities and internet use. They also critically enable secure access to web and cloud resources for remote and distributed employees.
Through a zero-trust solution like SASE with each of the components discussed above or that utilizes one of them with some form of isolation technology, companies can secure most of their employee's web browsing activities. Noting, of course, that SASE is more internally focused on its capabilities to protect an enterprise network. Meanwhile, Enterprise browsers protect internal web activities but incorporate more external employees who need to access a company’s resources.
Some of the limitations of SASE solutions compared to browser-based solutions:
Enterprise browsers have the capability of providing more in-depth security to fully support unmanaged or BYOD devices than a pure-play SASE.
SASE platforms struggle to fully support third-party access and support for critical business initiatives, particularly in the case of large mergers and acquisitions (M&A) that involve the integration of diverse employees and their different solutions. They may also struggle with supporting remote third-party access for troubleshooting or support for large enterprises that need remote call center productivity, including VoIP support.
Some SASE providers with weaker RBI solutions lack strong visibility and may struggle to control encrypted and encoded cloud application traffic. However, granular browser solutions like SURF can control how users use those applications while incorporating strong data controls.
SASE solutions perform most or all of their work in the cloud; they often rely on the use of SSL inspection to identify and protect against malicious content. However, there are data pathways where SSL inspection is not allowed due to privacy regulations and SSL Pinning. Enterprise browsers can go deeper to monitor traffic on these paths, provide the required protection and isolation, and forward file downloads to the SASE sandbox for scanning if desired.
As a result of some of these limitations, we’ve seen leading SASE vendors like Zscaler, Netskope, and Palo Alto Networks incorporating RBI or browser security. This allows them to enforce security policies for what data or information employees can see, including for contractor employees.
Zscaler utilizes its more advanced Zscaler RBI to protect enterprise users and their browsers through a direct-to-cloud proxy architecture. This allows a secure connection for employees to apps and websites regardless of location, with a browser isolation policy that covers headquarters, mobile and remote sites, and managed and unmanaged devices.
Similarly, Cloudflare integrates their SWG and ZTNA with their RBI solution to protect users from phishing attacks by preventing user input on risky websites and controlling data transmission to sensitive web applications.
Palo Alto Networks acquired Talon to provide more browser-level features within its SASE package but specifically to help companies manage their BYOD policies.
SASE presents both a threat and an opportunity for enterprise browser companies. It’s likely over the long term that enterprise browsers merge to become part of a larger SASE/SSE solution. We could see more and more acquisitions happen within this market where large SASE or firewall companies acquire enterprise browser companies. One of the major reasons is that while SASE provides many online security capabilities, enterprise browsers and RBIs provide a much more granular level of security and enforcement for web browsing experiences. Also, it is important to note that SMBs may not be able to afford some of the large ticket items associated with SASE solutions but may opt for an enterprise browser. In these cases, it's likely companies will reduce their spending on SASE features like SWG, ZTNA, and CASB in favour of a consolidated product like the enterprise browser or browser extensions. This could serve to reduce spend on VPNs, SASE or over the long-term, completely serve as a full alternative.
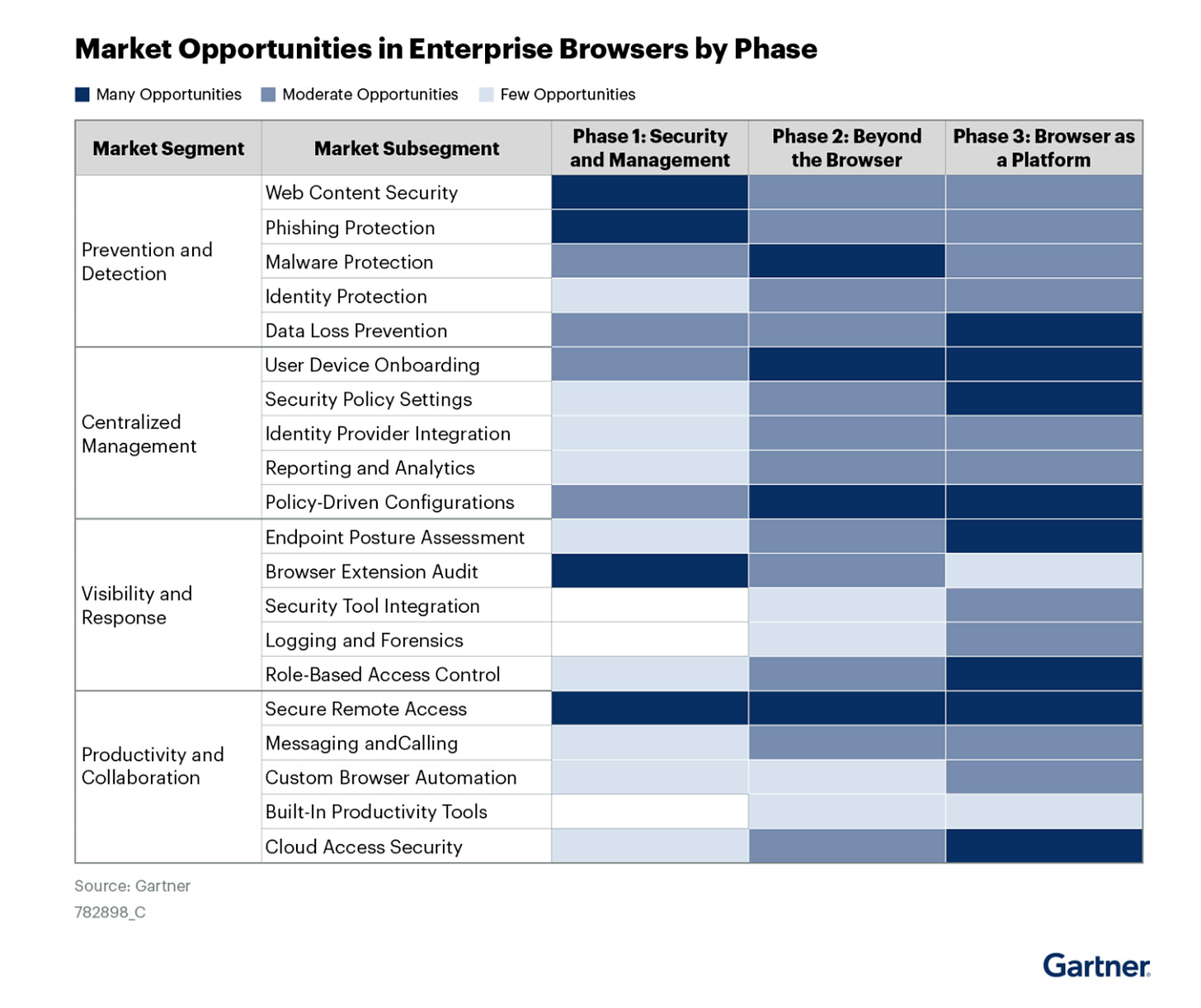
Market Opportunity
Below are some of the most important categories that make up the enterprise browser and extension markets.
The BYOD category is pegged as a significant opportunity because companies can significantly save costs on endpoint devices like laptops, mobile and office equipment that need to be shipped out for employees. Instead, companies can tell employees to use their personal devices, download the enterprise browser and log in to access all the important work documents they need. Talon security estimates as much as 70% TCO-savings for companies.
There are three areas in which we see the enterprise browser market becoming a large market opportunity.
The browser becoming an operating system.
Operating systems manage system resources like CPU, memory, and storage. Initially, OSs were the primary platforms for running applications. However, with the advancement of web technologies, browsers have also become platforms for running web applications (like Google Docs, online banking platforms, etc.). It's quite possible that over time, with more advancements on chromium, we could see an evolution into “Browser-as-a-platform.“
As the cloud continues to advance, more applications and services are moving online. The browser could evolve to be the primary interface for accessing these cloud-based apps and services, much like how an OS is used to access local applications. Today with the advancements in Chromium browsers, similar to an OS, browsers offer more customization and extensibility options, allowing users and enterprises to tailor their web-based computing environment to their specific needs.
If enterprise browser companies take on more partnerships with PC providers, we could see a case where the browser takes on a more advanced resource management role, like handling computing tasks, virtualized desktops, memory management, and storage, which are traditionally associated with operating systems. For enterprises, a browser functioning as an OS could mean streamlined access to enterprise applications and resources, easier management and deployment of tools, and enhanced security in a cloud-centric environment.
The consolidating platform for all web security features.
Enterprise browsers could consolidate many security tools together and capture existing spend from security categories within the enterprise. As the browser increasingly stakes its claim as the center of the knowledge worker’s corporate universe, enterprise browser vendors are increasingly developing security controls that live within the browser. Some of these use cases include elements of data loss prevention (DLP), configuration management, logging and integration with security information and event management (SIEM)/extended detection and response (XDR) platforms, identity protection, phishing protection, and monitoring for malicious activity across downloads and extensions.
It is highly likely that Enterprise browsers replace or reduce spending for EDRs like CrowdStrike, VPNs, VDI, RBI, and some SASE features especially amongst small and medium-sized enterprises. Enterprise Browser products have the opportunity to consolidate and centralize many important security capabilities, such as secure remote access, malware protection, remote browser isolation, data leakage prevention, email security, etc.
Although this is another more elaborate topic that can be discussed in the future, there is the opportunity for non-browser-based applications like productivity or communication tools to be integrated into the browser. However, we are still a long way from this becoming a reality.
Rising tailwinds from the rise of remote work, temporal staff, and BYOD
Today’s organizations consist of a wide array of users: remote employees, part-time team members, vendors, partners, freelancers, and more. There are as many as 51.5 million contingent workers across the US. Additionally, the rise of BYOD is a trend that continues to grow post-covid. According to an HP Teradici Security Report, 48% of 8000 respondents said their companies were using employee-owned devices for work. 74% of respondents felt that BYOD use would be increasing.
Therefore, ensuring team members have secure access to corporate data and applications is already a significant challenge when using corporate-owned devices. It becomes even more difficult when employees bring their own devices. These risks are further magnified when integrating third-party contractors into the mix. In many cases, it's easier to have them “BYOD” and utilize enterprise browsers around them. The adoption of Enterprise browsers could see significant growth to match the rise in third-party contractors, temporary employees, and “local” employees operating with BYOD.
Some Roadblocks To Consider
The hyperscalers market share: The four largest browsers represent almost 90% of the browser market share. Most enterprise browsers or extensions are built around Google’s Chromium. These companies are also very dependent and are at the mercy of Google. The browser companies rely on the parent company’s version for critical security and performance updates.
Although relatively nascent and lacking in-depth features, Microsoft and Google have developed fairly capable enterprise browsers, which are relatively inexpensive to purchase. This year, these companies have released important updates to level up their product to match the core players. The key factor to watch is how much the hyper scalers invest in the enterprise security browser component of their browsers and, secondly, how many integrations they can get with most of the identity, EDR and SASE vendors.
Open-source nature is a double-edged sword: The fact that the Chrome OS is open-sourced means that a company with the budget and technical talent can build around the browser to match their enterprise need, or another startup could be easily developed. The other argument is that it is extremely difficult to build a new browser, even leveraging the Chromium OS. Many features fundamentally require an unnatural manipulation of the host browser to achieve their desired functionality together, and implementation is expensive. However, OSS without core differentiator around managed services or similar is always something for these companies to consider.
Existing security solutions (EDR, SASE, MDM): Organizations must have specific use cases to justify the purchase of a separate browser. If they already have an existing RBI that matches their needs, an existing EDR or SASE features like those discussed above, it becomes unlikely most companies will allocate budget to an enterprise browser without the ability to offset that spend elsewhere. Larger enterprises with much more complex architectures may be hesitant, except it serves a specific core function.
Employee Experience and privacy: While many current browsers have decent performance and customer experiences. These are still complaints about performance issues as they relate to connectivity, latency, and connection to apps. Some have argued that enterprise browsers are not as fast as your traditional browser because it's almost like spinning a traditional virtual environment. These are also complaints about how employees feel about tight security constraints/rights when using a fully replaced browser. It’s hard to change people’s behaviour around using the browser. In many cases, employees don't notice the major difference between the standard browser, but in some cases, they do so, and many employees complain that management could decrease usage of these solutions.
Summary
Similar to operating systems, browsers were not initially designed with a focus on security. However, significant efforts have been made over the years to strengthen security as a crucial foundation for browsers. As sophisticated attacks increasingly target browsers, enterprises have realized the pivotal role they play within an organization's security framework.
In the past decade, RBI technologies have dominated the market and been adopted by large enterprises. Recently, secure enterprise browsers have gained significant traction as they continue to incorporate advanced capabilities. While these browsers offer various functionalities, they still lack the depth of other security solutions available.
Currently, early entrants like Talon, which was acquired, and Island, which commands a premium valuation, appear to be successful. However, history shows that for the browser market to become a large market, it needs significant effort to become a dominant player in the market.
One possible outcome is that the browser could replace the entire operating system as the primary platform, or it could become a significant component of another security area like SASE. The recent acquisition increases the chances of the latter scenario, but only time will determine the long-term viability of this trend.
In 2024, I’ll be writing more often on cybersecurity themes, covering more software companies, trends around platform consolidation, Identity, AI/ML trends and many more for free. Subscribe to keep up-to-date on each of them.