The Future of SOC Automation Platforms
A deep-dive into the evolution of security orchestration and automation response solutions (SOAR) and the future AI-native automation platforms.
Welcome, Software Analyst readers!
Today's piece is the final report in my series of research reports before RSA. It focuses on SOC automation platforms. It is a sequel to my initial report on the evolution of the Modern Security Data Platform. We’re focused on the right side of the security data stack, which emphasizes the role of AI response and automation within security teams. This report goes into depth, covering the automation ecosystem across SOAR, hyper-automation, and AI-SOC companies. We uncover all the current developments happening.
Actionable Insights
Enterprises have not yielded the benefit of their automation platforms. As large enterprises built out successful SOC teams with SIEM solutions and a vast array of security tools, they’ve had to deal with the growing alerts that these tools generate. The combination of tool sprawl, skill shortages and alert fatigue has prompted the need for automation solutions, which we will discuss extensively throughout this report.
Given the recent breakthroughs in AI, particularly around LLMs, we are yet to see the true value of security automation tools. We believe security automation tools will leverage their deep integrations into the existing security stack and rich historical workflow data to become the data fabric for which the future SOC AI Assistants are built, transforming struggling units into proactive powerhouses.
We’re beginning to see this revolution happen now. The market is gearing up for a significant evolution in how SOC teams function and the future of SOC automation. As a result, there has been a drastic uptick in investment activity, with $175M+ of capital being deployed into Hyperautomation/A-SOC companies in April-24 alone!
The rest of the report guides you through the history of security automation platforms, from in-house bespoke automation scripts and generalist automation tools to how the industry evolved to security-focused SOAR platforms, Hyperautomation and the recent emergence of AI-SOC startups.
Acknowledgements
A massive thank you to Torq Security, the hyperautomation company, for partnering with me and supporting the software analyst blog. Without partners like them, it would be impossible to make this research public. This research piece was compiled after speaking to founders and operators of the leading automation companies Torq, Tines, Mindflow, and operators. This report was written in in collaboration with Josh Trup of Nauta Capital. Check out his blog. Disclosure: Nauta Capital is an investor in Mindflow.
Defining The Security Operations Centers (SOCs)
Before diving deep into automation and the challenges faced by security teams, it's important that we begin by clearly defining the Security Operations Centers (SOC). SOCs are crucial centralized units within organizations dedicated to monitoring, detecting, analyzing, and responding to cyber security incidents. These units play a pivotal role in protecting an organization's digital assets, infrastructure, and sensitive data against a variety of cyber threats.
While Security Operations Centers (SOCs) are crucial in protecting organizational assets, their daily operations are far from glamorous. SOCs are often characterized by high volumes of mundane, repetitive tasks that are critical yet tedious. To better understand who handles these essential responsibilities within the SOC, let's explore the various roles and functions that contribute to the organization's cybersecurity efforts.
Roles and Personas within the SOC
SOC Manager: Responsible for overseeing the operations within the SOC
Security Analysts: Security analysts are the frontline defenders in a SOC. These are the core team members who monitor and analyze organizational security posture on an ongoing basis. They are typically tiered in levels
Tier 1 (Security Analyst I): Monitors alerts to triage, categorize, and conduct initial analysis. They determine the severity and escalate incidents to higher levels.
Tier 2 (Security Analyst II): Handles more complex analyses, often involving detailed forensic investigation, to validate and prioritize incidents.
Tier 3 (Security Analyst III): Focuses on advanced threat detection, deep dive investigations, and mitigation strategies. They also develop and tune security measures.
Security Engineer/Architect: Responsible for designing, building, and maintaining the SOC’s security infrastructure. This role involves configuring and tuning security tools, developing automation scripts, and ensuring all technologies are integrated and optimized.
Compliance Auditor: Ensures the SOC and the organization comply with all necessary industry regulations and standards related to information security.
Depending on the size of the SOC team, other roles can include:
Incident Responders
Threat Hunters
Forensic Analyst
Threat Intelligence Analyst
Key Functions of a SOC
Erik Bloch, Head of Detection and Response at Atlassian, author of the Security Operations Metrics Manifesto has written extensively about the key functions of the SOC. Below is a quote that captures it:
SOC teams allocate their time across different types of security incidents, based on the average resolution time for each category.
Human vs. Machine Generated Events: The data indicates an average distribution where human-generated events slightly exceed machine-generated ones, with a ratio of 6.8 to 6.3. This highlights the significant human element in cybersecurity management.
Phishing Reports: A considerable amount of SOC resources are spent on addressing phishing incidents. It typically takes about 2-3 hours to resolve each new report. Given the high volume of phishing attacks, this activity significantly impacts SOC workload.
True Positives: These incidents, while fewer in number, require extensive investigation, taking about 8-10 hours to resolve. True positives are definitive security breaches that the SOC successfully identifies and handles internally without escalating to Incident Response (IR) teams.
True Positive Benign: These are incidents where the detection systems correctly identify an activity, but additional context reveals it to be benign. Handling these cases is less complex than managing false positives and represents an area ripe for procedural refinement.
It is a challenge to distinguish between outputs (immediate results of SOC activities) and outcomes (long-term effects and changes resulting from SOC actions). For a deeper dive into security operations metrics and strategies for enhancing SOC efficiency, see his Security Operations Metrics Manifesto and his detailed post on the topic. For more insights into improving SOC metrics and operations, see his previous analysis: Security Operations Metrics Manifesto.
Today’s Challenges Faced By Modern SOC Teams
Originally tucked away in the metaphorical, and sometimes literal, basements of organizations, the Security Operation Center (SOC) has emerged into the spotlight in recent times, receiving the recognition its long deserved. Like with most breakout actors, athletes or musicians, this rise in status and fame has brought with it budget increases in double-digit percentages annually and a seat at the board.
According to Gartner, global spending on information security and risk management technology and services surged from $66 billion in 2003 to an estimated $175 billion in 2023, reflecting a growing understanding of cyber security's critical importance within organizations. This shift has also been mirrored in boardrooms worldwide, where cyber security has transitioned from a technical issue to a top-tier strategic concern. This elevated priority has propelled investments in advanced security infrastructures and has solidified the role of SOC teams as fundamental to organizational resilience and risk management strategies.
To understand this new(ish) found fame, lets unpick what has driven it over the past 20+ years. Cyber Security has always been a never-ending race, but the rate of change is accelerating. Since the dawn of time, companies have been leveraging new technologies to run and improve their offerings. More recently, this has been digital evolutions including the advent of the internet, the introduction of mobile or the transition from on-premise to the cloud and now AI. It comes as no surprise that the attack surface of an organisation has grown drastically both in size and complexity….and that’s without even thinking about how remote working has 10x’d this problem.
Parallel to the expansion of the attack surface, threat actors have dramatically advanced their tactics. The growth in cyber attacks is not just about quantity; the sophistication of these threats has evolved profoundly. Today's cyber adversaries deploy a range of complex strategies, including polymorphic malware, ransomware, and sophisticated phishing schemes that are more challenging to detect and counteract. This escalation in both the volume and intricacy of attacks has significantly compounded the challenges faced by SOC teams, who must continuously adapt to protect their organizations against increasingly cunning adversaries.
In response, organizations have found themselves leveraging newly assigned budget to buy and roll out a diverse array of security tools to protect and address multiple facets of security threats. According to a talk at RSA 2019 by security operations consultants from Palo Alto Networks, small organizations use 15 to 20 security tools, medium organizations use 50-60 tools and large organizations use as many as 130 tools! This phenomenon is widely known as tool sprawl. The consequence is a fragmented security infrastructure where managing and integrating these tools becomes a huge operational burden.
As a result, the proliferation of security tools has inadvertently led to alert fatigue among SOC teams. As each tool generates its own stream of data, the volume of alerts to monitor, triage, and respond to escalates rapidly. This deluge can overwhelm analysts, leading to critical alerts being overlooked or dismissed, thus diminishing the effectiveness of threat detection and response efforts. Moreover, dealing with the massive amounts of security data effectively often calls for more sophisticated security information and event management (SIEM) systems, which can further stretch SOC budgets due to their complexity and the high cost of data ingestion and analysis. The economic impact is compounded by the fact that SIEM solutions frequently generate numerous alerts, many of which may be false positives, thereby increasing operational costs and complicating the effective use of these systems.
The relentless pace and escalating demands placed on SOC teams as the risk of a breach increases has contributed to poor staff retention. The high-stress environment, compounded by the constant need to manage an array of complex tools and respond to incessant alerts, can lead to burnout. This situation is exacerbated by the industry-wide skills shortage, which places additional pressure on existing staff, making retention an even more critical challenge for organizations striving to maintain robust cyber security defenses. Enterprises are grossly understaffed with over 3.5 million unfilled positions across SOCs globally.
With such a state of affairs in cyber-defense, it doesn’t come as a surprise that enterprises take an average time of 277 days to detect cyber security breaches. The battleground continues to be tilted in favor of the adversaries despite decades of concerted investment into the SOC and its team. Amidst the doom and gloom outlined above…there is indeed a hopeful prospect on the horizon: the emergence of Security Automation tools and the advent of AI-driven defenses which aims to alleviate and offload the growing pressure put on the SOC.
How We Got Here: History & Evolution of the SOC
The concept of SOCs has its origins in the early days of Cyber Security and has evolved significantly over the years to meet changing security needs.
Proliferation of security tools
As SOCs have adapted to increasingly complex cyber threats, they've often opted for "best-of-breed" point solutions to enhance specific aspects of their defense capabilities which has driven the emergence of tool sprawl over time. Originally, SOCs employed a manageable number of specialized tools, but the growing complexity of the digital threat landscape necessitated a broader arsenal.
This sprawl obscures visibility across the security team, making it difficult for analysts to gain a unified view of threats and vulnerabilities and increases the complexity of incident response workflows. Consequently, critical alerts may slip through the cracks due to the overwhelming volume of notifications from disparate systems, each requiring separate assessments. The integration challenges of these tools can lead to delays in response times during critical threats, as data needs to be correlated manually across systems.
The Emergence of SIEMs In The SOC
I have written about the evolution of the modern SOC in a previous research report. In there, I discuss extensively about the role of SIEMs and how they have extensively come to define the current SOC. However, it is worth diving into some history of these solutions briefly here.
In 2005, SIEM (Security Information and Event Management) systems began gaining prominence. These systems integrated and aggregated different logs and security data, providing a centralized view for monitoring and analyzing potential security events. As we moved further into the digital age, Next-gen SIEMs and data lakes started becoming crucial tools for SOC (Security Operations Centers) analysts. These cloud-native SIEM tools, like Anvilogic, Panther Labs and Hunters AI, support SOC analysts in their incident response challenges together security automation solutions for advanced security teams at large companies. We already discussed extensively about how Multi-data SIEMs like Anvilogic are core to this evolving SOC landscape.
For example, a platform like Anvilogic multi-data SIEM serves as the detection and analytics layer on a customer’s cloud data platform. Once it detects an event or creates an alert, it sends it out to an automation platform (which we explain in more depth later in this report).
By 2010, SIEM systems became more sophisticated with capabilities to include not just log aggregation but also event correlation, alerting, and dashboards which aid in quicker detection of anomalies. The cybersecurity landscape continued to evolve rapidly in the 2010s, with increasingly sophisticated cyber threats such as advanced persistent threats (APTs), ransomware, and insider threats. Consequently, SOCs became more sophisticated as well, adopting advanced security technologies like Security Information and Event Management (SIEM) systems, threat intelligence platforms, and advanced analytics tools. The roles within SOCs also diversified, with dedicated analysts specializing in threat detection, incident response, threat hunting, and forensics.
The Rise of Automation In The SOC
At its core, automation has a single purpose: to let machines perform repetitive, time-consuming and monotonous tasks. This, in turn, frees up scarce human talent to focus on more important things or simply things that require a human touch. The result is a more efficient, cost-effective and productive workforce.
A persistent fear in cyber security and in the world more generally is that automation is here to replace humans. While somewhat justified, the reality is that automation augments human capability in executing security operations and, in some cases, helps organizations supplement and address the talent gap. As advanced as it may seem, automation will always be reliant on humans, completely configurable and under the supervision of security teams.
Different organizations and SOC teams have been approaching automation in different ways depending on budget, technical talent and team size. Some clear approaches include:
Bespoke automation scripts
Generalist Automation
SOAR Platforms
Hyperautomation
Advent of AI-SOC
1. Bespoke scripts (In-House engineering teams)
Before the advent of specialized security automation tools which we discuss extensively in the next section like SOAR (Security Orchestration, Automation, and Response) platforms, many organizations relied on bespoke, in-house scripts to manage security tasks. These custom scripts, while tailored to specific organizational needs, often required significant software engineering expertise to develop and maintain. As they were hard to update and integrate with other systems, this approach posed challenges in consistency and scalability.
Over time, the need for more robust, maintainable solutions led to the adoption of off the shelf generalist no-code automation (RPA) tools or Security Orchestration, Automation, and Response (SOAR) platforms if budgets allowed for it.
2. Generalist Automation (UIPath, Zapier, n8n etc.)
The first solution primarily for IT teams were generalist automation platforms like Zapier, n8n, and UIPath primarily focus on automating workflows across various applications and systems without the need for extensive coding knowledge. Although they are not specifically designed for security operations, their capabilities were helpful for SOC teams that had to deal with issues like automating the workflow between IT apps.
An example would be automatically creating tickets in a management system when an alert is detected by a monitoring tool. This reduced the manual effort required to transfer data between systems and ensures that action items are promptly addressed, enhancing the response time to potential threats.
However, the challenges with these solutions was that they lacked the features specifically tailored to the unique needs of security teams, such as advanced threat intelligence integration, incident response playbooks, or forensic capabilities that are essential for effective SOC operations.
3. SOAR Platforms
The limitations of general automation tools in addressing the needs of security operations centers (SOCs) especially companies moving to the cloud and drowning with alerts led to the development of specialized security automation platforms known as Security Orchestration, Automation, and Response (SOAR) solutions.
SOAR platforms were built with security-specific capabilities in mind, including threat intelligence/SIEM platforms integration, incident response playbooks, and automated workflows tailored for security incidents. These solutions were built to deal with the outputs of SIEM's by automating responses and providing tools for managing, planning, and coordinating incident response activities. These systems were designed to understand and prioritize alerts based on their security relevance, ensuring that SOC teams could quickly identify and respond to the most critical threats.
By 2018, Advanced SOAR platforms start integrating artificial intelligence (AI) and machine learning (ML) to improve threat detection and response, making these systems not only reactive but also proactive by predicting and mitigating potential security threats.
Legacy Vendors
Splunk (Phantom)
Phantom Cyber Corporation, acquired by Splunk in 2018, was one of the earliest and most well-known names in the SOAR space. Phantom’s platform allows security teams to automate tasks, orchestrate workflows, and integrate various security tools. Splunk's integration has further enhanced Phantom's capabilities, providing advanced analytics and a broader data platform to support complex security operations.
Siemplify
Siemplify, now part of Google Cloud, offers a security operations platform that is often categorized as a SOAR solution. It emphasizes simplicity and context in security operations, aiming to make it easier for analysts to manage, investigate, and respond to incidents. Siemplify's approach to SOAR combines advanced threat analysis with practical, scalable automation.
Demisto (By Palo Alto Networks)
Cortex XSOAR, formerly known as Demisto (acquired by Palo Alto Networks in 2019), was a comprehensive SOAR platform that had automation, case management, real-time collaboration, and threat intelligence management capabilities. It was one of the earlier companies noted for its security operations capabilities and marketplace for integrations and playbooks before it was acquired.
4. The Rise of Hyperautomation
The 2020s brought a range of challenges for Security Operations Centers (SOC) that existing Security Orchestration, Automation and Response (SOAR) tools struggled to manage. Cybersecurity threats became more sophisticated as businesses integrated more cloud-native data solutions and had to deal with many more security tools. All of these occurred simultaneously with a growing demand for experienced cybersecurity professionals, yet with limited supply of them.
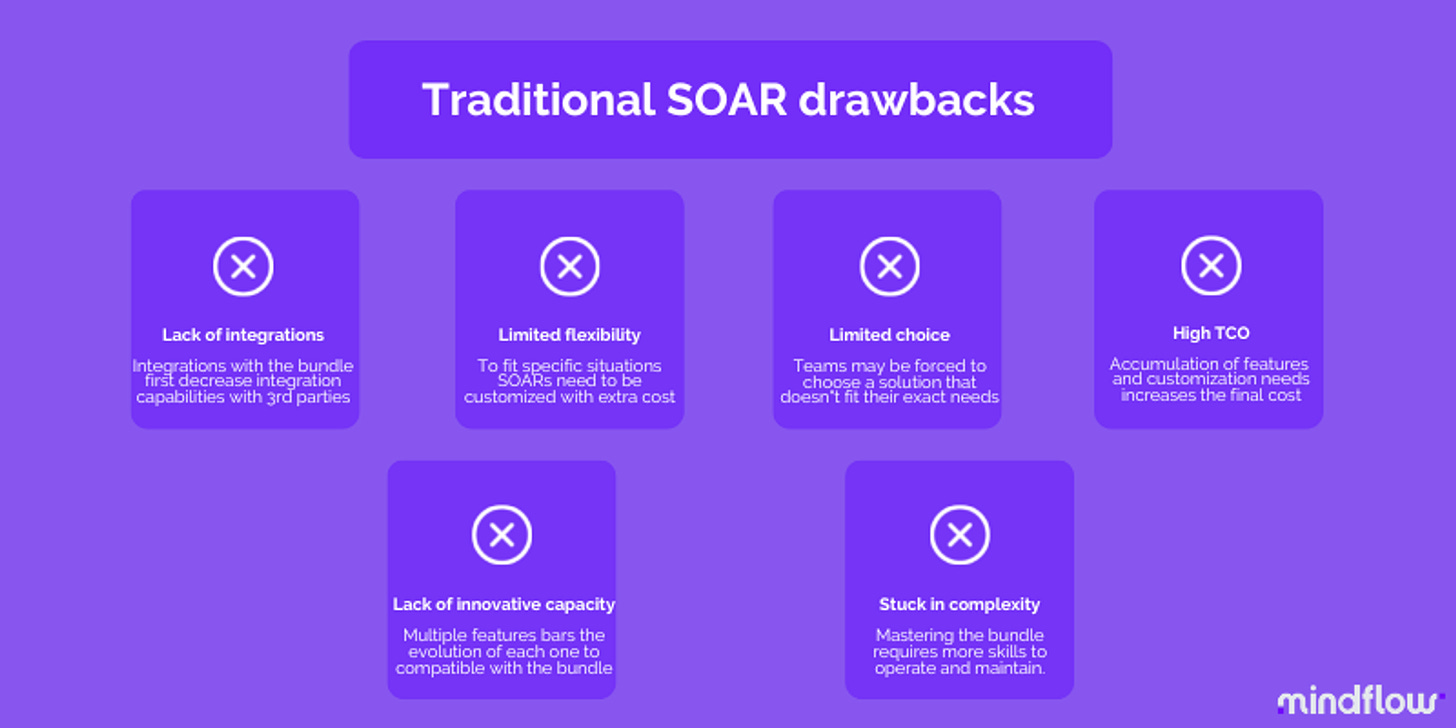
Below are some of the existing drawbacks of SOARs:
These legacy SOAR tools faced a significant challenge as they grew in size and complexity, often compelling organizations to hire experts or spend on professional services. These costs often far exceeded the initial price of the SOAR tool.
Consequently, these challenges led to the emergence of a new market, termed as Hyperautomation by Gartner.
Hyperautomation
These platforms automate repetitive and time-consuming security tasks, allowing SOCs to focus on more strategic activities. They provide a vast array of security and infrastructure integrations delivered through easy to use no/low-code UIs for creating custom automation workflows. As a result, less technical staff can easily setup automation and orchestration processes including enhancing incident response capabilities, and streamlining operations. By reducing manual intervention, these solutions improve efficiency, decrease response times to threats, and bolster overall security posture, making them invaluable for modern cybersecurity environments. Below is an easy case study of this workflow:
Example Use Cases for Security Hyperautomation
IAM: Automating user onboarding and offboarding processes, ensuring that access rights and permissions are updated dynamically as team changes occur. Another focuses on real-time access reviews and permissions adjustments to maintain security compliance and reduce risks.
Threat Hunting: Automating the process of gathering data from disparate sources to quickly identify threats across the environment. It also enables automated responses to identified threats, streamlining the remediation process.
CSPM: Use cases include continuous monitoring and compliance checks against cloud environments to ensure configurations meet best practices and regulatory standards. Another use case automates the response to misconfigurations or unauthorized changes, quickly reverting changes or alerting teams.
SOAR vs Hyperautomation Solutions
Its also important we note that legacy SOAR solutions primarily assisted SOC and Incident response teams. However, next-generation automation solutions like Torq handle those use-cases, but go further by handling a broader range of CISSP domains and use-cases across the security stack.
These include Asset Security, Security Architecture and Engineering, Identity and Access Management, Security Assessment and Testing, Software Development Security, and Network Security, in addition to the domains covered by SOAR.
Organizations might prefer SOAR if their main goal is to streamline their SOC operations, such as incident response, threat intelligence, forensics, and vulnerability management. Conversely, hyperautomation could be a better fit for organizations seeking to implement a comprehensive automation strategy across various cybersecurity functions and departments. To read more about these differences, we encourage reading more from Cybersec automation’s blog.
Hyperautomation Market Landscape
Torq Security
Torq is an AI-driven hyperautomation company that addresses the critical needs of SOC teams by automating and managing their tasks. Their platform, referred to as 'HyperSOC', saves SOC analysts time and energy when responding to security events. It assists in investigation, triage, streamlining of incident response cases, and remediation at scale. These capabilities contribute to reducing manual workload and streamlining incident response actions. While Torq is often compared to Tines, our report emphasizes Torq's unique features. We believe both companies have significant differences that are important for readers to understand.
Torq was established in 2020 by founders with extensive security backgrounds and expertise. This wealth of experience gave them a deep understanding of the complex challenges that security operations teams face. This specialized understanding has enhanced Torq's effectiveness and connection with security teams.
Architecture
The Torq's architecture is fundamentally a cloud-native solution. It's built around Natural Language Processing (NLP), AI and a wide variety of integration capabilities. These capabilities allow it to collect, analyze, and filter data, information, or security from a wide range of security tools across the enterprise. A key part of this functionality comes from its ability to respond to security events and alerts. These can be generated directly from SIEM tools or from a company's cloud stack, such as SaaS Apps. Their system processes considerably more security events than traditional SOAR solutions by employing advanced data aggregation and normalization techniques. This approach ensures that their system remains efficient and effective, even during intense "event or alert storms."
Torq recently announced its HyperSOC solution, an advanced AI automation that builds on their existing Hyperautomation platform. The HyperSOC allows analysts, engineers, and managers within SecOps to automatically deal with false positive security alerts, manage incident investigations, and respond to cases. Their HyperSOC also allows users to implement automation without requiring extensive technical skills. Although Torq can handle complex workflow automation use-cases for a company, it remains intuitive due to its template-driven workflow creation capabilities. This allows for quick deployment and ease of use, greatly reducing the complexity and time-to-value when compared to traditional SOAR solutions mentioned earlier in our report.
Extensibility
Lastly, their solution has a comprehensive and open integration framework that allows for vast extensibility. As briefly discussed earlier about its integration capabilities, their solution enables seamless connection to any system within an organization's stack through its open architecture. This extensibility is crucial for creating a unified security posture that integrates across varied environments, including cloud services like AWS, GCP, and Azure, and on-premise systems. Their solution allows companies to go beyond APIs for extensibility. Companies have the flexibility to expand their number of use cases with capabilities such as SSH, PowerShell, SQL, Python, BASH, Kubernetes, AWS, GCP, Azure CLI, and other scripting or programming languages.
They also have a DIY approach to integration. Unlike traditional platforms that may require costly professional services to build connectors for third-party tools, Torq supports a 100% DIY approach. This enhances its utility and reduces the total cost of ownership. The platform also supports a wide variety of programming and scripting languages. This empowers technical users to bring their own code, further enhancing the system’s versatility and utility in complex IT environments.
More Security Focused & Deeply Embedded Within SecOps
Our analysis of Torq and its competitors reveals that Torq has more security use-cases and is well-embedded within security teams. Torq’s HyperSOC offers extensive connectivity and open integrations across any security and infrastructure stack. It enhances the capabilities of SecOps professionals by using generative AI to automatically investigate the severity of threats and initiate optimal escalation and strategic resolution efficiently.
There are two use-cases where we would like to highlight that Torq specifically shines in:
SOC Automated Workflows: Their platform enables enterprises to create no-code, expert-curated template workflow libraries and recommendations for basic Tier-1 SOC analyst tasks. Torq allows for customizable automation workflows. Organizations can tailor their automation workflows in Torq, defining operational parameters that fit their unique security needs and environments. This level of customization extends Torq’s applicability beyond traditional security tasks to encompass operations across collaboration, communication, and infrastructure applications.
Hyperautomated Case Management: Traditional systems often require security analysts to gather data from various sources to investigate an alert manually. This process is time-consuming and can delay the response to threats. However, solutions like Torq allow organizations to merge AI-driven insights with hyperautomated playbooks to seamlessly automate the entire case lifecycle from identification to resolution. This continuously calibrates security responses across multiple security tools, enhancing the overall security posture.
In summary, Torq's key differentiators include its architecture, extensibility, and deep integration within SOC teams. The company's significant growth over the past four years underscores these points. Creating an automation solution for a small startup is one thing. However, building automation at a large scale introduces a whole new set of complexities. Torq has demonstrated their ability to execute and scale their automation solution effectively.
For more on Torq: We encourage interested readers to visit the Torq website for a full overview. Torq is also offering demos of Torq HyperSOC exclusively for RSAC attendees, between May 6-9, at Booth #4415, North Hall, Moscone Center, in San Francisco.
Tines
Tines provides a security automation platform designed to optimize and automate complex and repetitive security processes. The platform is built with flexibility, allowing users from sophisticated security teams to tailor automation workflows to their needs. The origin of Tines is rooted in the founders' own experiences in security at companies like eBay and DocuSign, where they encountered the challenges of excessive manual work and the inefficiencies of existing security tools. Below we’re planning to outline some of the core differentiators for Tines security:
Differentiators Expanded:
Usability and Accessibility: Tines stands out for its emphasis on a fast, secure, and straightforward approach to automation. By reducing the complexity often associated with automation platforms, Tines makes powerful technology accessible to a broader audience. Their no-code and low-code solutions particularly appeal to teams without extensive programming skills, lowering the barrier to entry and allowing more users to benefit from automation technologies.
Customization and Integration: Tines provides a flexible framework that allows users to build and integrate with any tool or data source. This capability is crucial for SOCs that need to adapt quickly to new threats without waiting for vendor updates or new integrations. Tines supports a philosophy of "build, run, and monitor" offering robust backend support for these tasks, which enhances reliability in mission-critical environments.
Market Adaptability and Expansion Beyond Security: Tines has successfully transitioned from a security-focused solution to a workflow automation platform for teams in IT, infrastructure, engineering and beyond. They report that while 92% of their customers use Tines for security, a significant 15% employ the platform for non-security tasks such as IT operations and fraud detection. This adaptability has allowed Tines to tap into larger markets beyond traditional security, addressing a wider range of business needs.
Strategic Market Positioning: Tines has been particularly effective in replacing traditional SOAR platforms like XSOAR, Phantom, and Demisto, especially in high-end market segments. Their ability to operate across different environments—on-premises, cloud, or hybrid—and to offer single-tenant deployments sets them apart, making Tines a preferred choice for enterprises requiring flexible deployment options.
Future Strategy and Innovation with AI: Tines has recently enhanced their automation capabilities with AI, particularly in “built time” and “run time” processes. Two new AI-powered capabilities launch for US and Sydney-based tenants on May 29, with other regions to follow. The new AI action brings the power of a secure and private LLM to workflows as they run - data never leaves the tenant. Automatic transform leverages AI to generate code from user prompts, accelerating the ability to build robust data manipulation into workflows.
Tines differentiates itself through its robust, flexible, and user-friendly platform that caters not only to security needs but also to a wide range of business processes. By lowering the technical barriers associated with automation and expanding its capabilities with AI, Tines is well-positioned to lead in both the security automation market and the broader field of enterprise automation. Their focus on honesty and functional efficacy in a market often dazzled by superficial features sets a foundation for sustained trust and reliability with their customers.
Mindflow
Mindflow is a no-code Security Orchestration, Automation, and Response (SOAR) platform that aims to let security and IT professionals connect to any security or infrastructure tool via their proprietary integration engine to easily build automated workflows for handling repetitive tasks. This can include handling phishing alerts, vulnerability management, Threat intelligence etc. Like other SOAR platforms, Mindflow gathers intelligence from disparate systems to enable SOC analysts to enrich and triage alerts, and ultimately respond to incidents more effectively and expeditiously. However, unlike SOAR solutions, Mindflow was architected to be extremely easy to use - no development skills required, and incredibly flexible with a vast number of integrations to most security and IT tools. This allows teams to create workflows that mirror even the most nuanced processes within their enterprise that run autonomously, enabling people with varying degrees of technical abilities to automate repetitive tasks such that they can spend time on more important tasks.
To enable large scale automation at enterprise level, Mindflow aims to cover all business processes, logic and services. As a result, Mindflow has developed an innovative approach to enable the integration of more than 650 products with 100% of their API operations enabling seamless automation.
A key part of Mindflow’s no-code strategy is the integration of Large Action Model technology which enables engineers to interact with their extensive tool ecosystem using natural language, effectively lowering the entry barrier for enterprise teams. AI-driven agents can intuitively identify and configure optimal actions, thereby optimizing the workflow design and operational processes.
Palo Alto Networks (XSIAM)
It’s important to note that the XDR vendors have been moving quickly into this market. As discussed earlier and in previous episodes, Palo Alto Networks acquired Demisto (a SOAR) vendor. In recent years, Palo Alto combined several critical security functions such as Endpoint Detection and Response (EDR), Extended Detection and Response (XDR), Attack Surface Management (ASM), Security Information and Event Management (SIEM) together with Security Orchestration, Automation, and Response (SOAR) into a central platform called Cortex XSIAM 2.0. XSIAM leverages its AI models to automate the processing and correlating of security data across different sources to identify patterns that may indicate potential security threats. The automation part of their platform is designed to simplify the workflow of security operations by centralizing the management of security tasks across of Palo Alto’s security tools and provide faster incident remediation. We believe Palo Alto Networks remains a core vendor to watch within this market over the next few years.
BlinkOps
BlinkOps is a pioneering security automation company that revolutionizes how security teams interact with technology. Their platform, described as a security automation copilot, harnesses the power of generative AI to facilitate the creation of security tasks and processes. This platform stands out by offering a user-friendly approach that significantly simplifies the integration and automation of complex security operations.
As of March 23, Blink’s security platform offers several features aimed at automating security. Its key updates include Blink Copilot, the AI system that can generate workflows based on text prompts; a drag-and-drop editor for customizing workflows; a library of more than 7,000 pre-built automated workflows for common security tasks; an integration hub for connecting the platform to other security tools; and a workflow engine for executing the automated processes at scale across on-premises and cloud environments.
SentinelOne & Stride Security
Recently, SentinelOne announced its acquisition of an early-stage company, Stride Security. Stride provides next-generation security orchestration, automation, and response (SOAR) and hyper-automation use cases. SentinelOne expects to integrate it together with its existing XDR platform.
5. Advent of the AI-SOC
Recent advances in AI, particularly around LLM agent systems are ushering in a new era of security automation capabilities. Although many of these early startups redefining this category are not mature enough to differentiate clearly from the hyperautomation solutions, their intiial product demos are capturing attention from security practitioners, CISOs and investors alike. They are built around the promise that AI agents will be capable of fully-autonomous operations, mimicking SOC analysts by mastering the unique querying languages of various tools, interpreting security data, and planning investigations while escalating serious issues for human review and resolving benign alerts.
These startups want to leverage recent LLM capabilities into their automation solutions. Primarily within LLM’s capabilities in 1) Data extraction and manipulation: How LLMs can learn each platform’s unique querying language and data structures, operating like a subject matter expert to query and parse results from dozens of tools. Secondly, LLM’s Interpretation and planning features. LLMs can be trained to interpret results with common-sense security analysis. They can plan each step of an investigation, and then make a final determination if a set of evidence is most likely malicious or benign. All of these features are being leveraged by emerging startups.
AI-SOC Solutions
As a result, there has been an explosion of new companies coming to market with products aiming to Automate the SOC (ASOC), and become an independent SOC analyst in the team. In the last month alone, there has been $175M+ of capital distributed into Hyperautomation/ASOC companies globally. Some of these include:
AI Agents are making the promise that security teams wont need to configure more rules-based playbooks. Instead, AI analysts will be integrated just like another member of the SOC team. They perform Tier 1 investigations on their own – escalating real issues for human review and closing benign ones. These virtual analysts can respond to threats in minutes, 24/7. They never get tired or forget the context of previous alerts. And with feedback from other analysts, they continuously learn more about the organization, systems, and investigation best practices. We believe its too early to tell how likely this promise will come true.
Commentary on Future Trends & How We See The Space Evolving
As we look to the future, macro trends continue to suggest an escalation in both the complexity and volume of threats, which will likely drive significant growth in security budgets. These funds are expected to be channeled increasingly towards innovative tools designed for proactive and predictive measures. The ongoing rise of remote work will continue to push the boundaries of traditional security perimeters, requiring more adaptable and flexible solutions.
According to Deloitte & Google Clouds Future of the SOC report, SOCs find themselves wrestling with a decision to change their ways or continue burning out, barely managing their current technology stack. Is there a way for the SOC to evolve or change their approach? Doing so would improve their ability to detect and respond to threats, and protect their organizations from cyber attacks. Maintaining the status quo risks falling behind as business and IT threats continue to evolve. They propose there are two approaches for the SOC in this situation:
Transform your SOC: This involves completely overhauling your SOC, from its architecture and processes to its staffing and training. Typically, this means evolving to a more engineering-led approach such as Autonomic Security Operations or consolidating into one central platform.
Optimize your SOC: This involves making incremental improvements to your SOC, such as adding new tools and technologies, refining some processes, or improving your incident response processes.
While the idea of completely transforming your SOC as described above is appealing, the practicality of securing board approval to overhaul everything from scratch is completely unrealistic. This is where Hyperautomation platforms become crucial. These tools not only introduce automation to previously manual processes but also enable the development of more complex workflows. This allows SOC teams to gradually shift from skepticism to embracing a fully automated, AI-assisted operational model. With deep integrations into the existing security stack and rich historical workflow data, these platforms lay the groundwork or…may become the data fabric for which the future SOC AI Assistants are built, transforming struggling units into proactive powerhouses.
The Rise of Autonomous security operations centers (ASOCs)
We see a trend is moving towards fully autonomous security operations centers (ASOCs) where AI-driven systems predict threats, initiate responses, and adapt security measures in real-time without human intervention, significantly reducing the time from threat detection to response. We see this happening by 2025 and beyond. We don’t believe the evolution of the SOC will be binary move. However, we expect an optimization that over time will feel like a full transformation to SOC teams.


















Great overview for helping rookies to be up to speed with nextgen SOC ! Well done
Great write up! Looks like another company Brick Layer has entered the AI-SOC Space