How Wiz Became the Fastest Software Company to Hit $500M & Its Path to $1B
A comprehensive deep-dive into the secrets behind Wiz' rapid growth and Its Race to Become the Fastest Software Company to $1B
Readers,
Today, we’re exploring the remarkable rise of Wiz—how they became the fastest company ever to hit $500M in ARR in just over four years! This is a feat so impressive that only a handful of companies, like OpenAI, can claim a similar trajectory. What makes this even more fascinating is that while cloud computing has been around for over 15 years, the most successful cloud security vendor didn’t emerge until 2020. Yet, it was one of the last movers in cloud security with over 10+ predecessors in the past. How is that even possible? My goal is to unpack every bit of this detail!
After months of engaging with Wiz’s early co-founders and senior product leaders, I’ve gained a unique understanding of their success—an evolution that no other publication has quite captured. This is not just another article hyping Wiz; I’ve delved deep into the details to provide the nuanced analysis this story deserves.
Back in 2023, I wrote about Palo Alto Networks' evolution with Rak, and in 2021, I chronicled Cloudflare’s rise. Covering Wiz has been a long time coming, and I’m excited to finally share this in-depth report.
Generational cybersecurity companies like CrowdStrike, Zscaler, and Okta have set the bar for success in the cloud era. Now, as we look at the next wave of companies poised to cross the $100M ARR mark, Wiz stands out among a select group of rising stars like Abnormal Security (email security), Cribl (SOC), and Snyk (AppSec). If Wiz continues even at half its current growth rate, they are likely to hit $1B ARR within the next year.
In this piece, I break down Wiz’s evolution into three key phases:
Wiz 1.0: Solving the core visibility problem
Wiz 2.0: Adding context to visibility, both from the left (DevOps) and right (SOC)
Wiz 3.0: The Journey to $1B ARR—what it would take, the competition, and risks
Along the way, we’ll dive deep into the founding team and the unique non-product capabilities that have played a crucial role in their success. In the history of pure-play cybersecurity vendors, less than 10-companies have achieved this milestone. In the era of the cloud, only 3 companies have achieved this goal in the last 15 years! Will Wiz become the next one?
Key Facts About Wiz
Wiz For Dummies: If you’re new to the cybersecurity industry, Wiz is a cloud security platform that helps organizations identify, prioritize, and manage security risks across their cloud infrastructure. It provides visibility into cloud environments, allowing teams to detect misconfigurations and other security threats.
Fastest Growth in Software History: Wiz became the fastest company ever to reach $500M in ARR. By August 2022, they hit $100M in ARR in just 18 months, making them the fastest-growing software company ever. By the end of 2023, ARR climbed to $350M; By August 2024, it surpassed $500M in ARR. The company is poised to achieve $1B in ARR next year, which puts it in the category of legendary companies like OpenAI that have achieved such a mark quickly.
Late Entrant to CNAPP Market: Remarkably, Wiz launched as one of the last major players in the CNAPP space, with over 10+ competitors preceding them. Despite this, they outpaced rivals with a graph-based architecture, providing richer contextual insights than competitors and many factors in this report.
Wiz’s Value Proposition: Wiz solved a common customer pain point by offering not just risk identification but also a solution that connected risks across multiple cloud resources using its contextual, graph-based architecture—something its predecessors couldn’t efficiently achieve. It complemented this with remarkable execution and rapid deployment, making it possible to be successful relatively quickly. The 2021 Log4Shell vulnerability crisis was a critical moment that catalyzed their growth and early customer base amongst Fortune 100 companies.
Record-Breaking Funding: Wiz has raised over $1.9B, making it the largest private cybersecurity company. In February 2023, they raised an additional $300M at a $10B valuation. This total financing is the highest amount raised by any cybersecurity startup, second only to Lacework.
Industry Leadership: Based off my research talking with many cybersecurity leaders, I’ve never seen a private company command such large market share early into its story. Wiz famously declined a $23B acquisition offer from Google, which would have made it the second-largest cybersecurity deal. For context, only four pure cybersecurity companies are valued at $23B or more—Palo Alto Networks, CrowdStrike, Fortinet, and Zscaler. However, their decision to decline that offer shows how much room they believe is ahead of them.
Wiz’ Success In A Nutshell
A legacy of friendship and excellence
Wiz wasn’t just founded by a team; it was born from a family of friends with over two decades of shared history. The four co-founders and the early engineers all established friendships in their teenage years and subsequently worked at similar companies. Their camaraderie, combined with their shared origins as ex-IDF (military) software engineers, laid the foundation for their incredible journey. The team met through Israel’s Talpiot program, one of the country’s most elite military and intellectual groups, where they bonded over their passion for technology and drive for excellence. In 2012, they founded Adallom, a pioneer in Cloud Access Security Brokerage, helping enterprises safeguard data in SaaS applications. By 2015, Microsoft acquired Adallom, elevating the team’s cloud security research to new heights. Now, they have reunited to create Wiz—a company built on mutual trust, lightning-fast execution, and an unwavering commitment to solving their customers' problems.
Wiz’ incredible success can be boiled down to these three overarching themes:
Product
Underlying Architecture: Wiz pioneered using a graph database to solve the cloud visibility problem. Leveraging the graph, they significantly enhanced their cloud security techniques (around cloud attack path analysis, toxic combinations and enabling high-fidelity risk prioritization) over competitors at the time.
Front-end Simplistic UX: Wiz created an incredibly intuitive interface for developers to investigate cloud vulnerabilities. Its foundational source was the graph architecture that helped detect relevant underlying cloud issues (i.e. minimizing false positives). This made it easier for development teams to remediate problems quickly.
Relentless obsession with their customers: Wiz deeply understood their customers' pain points and adopted a unique approach to solving their problems. Unlike many companies that claimed to be customer-obsessed, Wiz truly listened and delivered. This insight came from their extensive experience leading core arms of Microsoft Cloud Security’s business and from countless in-depth conversations/discussions with hundreds of CISOs, within their network. The discussions gave them a deep understanding of the challenges cloud customers faced. An unwavering focus on understanding, listening, and solving customer problems sets them apart in the market.
The Role of Timing & GTM Execution
Timing: Wiz struck gold in three ways. First, they pivoted from network exposure to cloud security, leveraging their deep understanding of graph technology. Second, they launched the market's leading cloud security product just as Covid-19 accelerated companies' cloud transitions. Finally, when the Log4J vulnerability hit enterprises, Wiz demonstrated bold leadership in the security community by utilizing their graph model to help both customers and non-customers swiftly mitigate the attack by identifying and prioritizing assets at risk.
Building for scale with the largest enterprises early-on: Wiz targeted Fortune 500 companies from the start, drawing on their Microsoft experience to meet enterprise-scale demands. This early focus on major clients pushed them to create an elastic product capable of handling the scale and chaos brought on by Covid-19. Consequently, they gained invaluable insights into diverse cloud workloads and architectures—an advantage that would prove crucial in subsequent years.
The opportunity in the cloud was large and big: Companies were spending nearly a trillion dollars on core cloud infrastructure, with approximately 10% of their budgets allocated to cloud security. By building a comprehensive platform early on, Wiz positioned itself to easily develop additional products, creating a powerful flywheel effect.
Incredibly talented founding team and culture
The founding team was exceptionally talented: As former Talpiot cadets—an elite Israeli military program—they were physics intellectuals with a strong drive to achieve ambitious goals. They had built and exited one of the most successful startups to Microsoft. Each co-founder possessed a unique skillset that enabled rapid scaling. Having worked together for over two decades, the team had also developed deep trust. They were highly selective in hiring, bringing in some of the brightest minds to join the team early on. The company culture emphasized ambition and speed. I share some fascinating details on the founding team at the end of the report because I want us to focus on the core details behind their success.
Let’s dive in!
Wiz 1.0: 2020-2022
The story can be broken down into three core foundational pivotal points in their evolution. We’ll begin the first core foundational bricks. In the early days of the company’s founding, solving the cloud visibility problem was key. At the time, cloud architecture wasn’t new to many large enterprises, but after migrating workloads to the cloud, companies encountered several significant challenges:
How do they gain clear visibility into their environments?
How do they prioritize real risks and eliminate noise?
How do they get a good handle on cloud risks and remediate them?
In my co-authored initial report with James, at Latio Pulse on CNAPP, I noted that, in the early days of cloud security, several companies (more than 10)—preceded Wiz, each attempting to address these issues.
However, Wiz approached the visibility problem differently, offering unique solutions that set them apart from their predecessors. In their first product, Wiz Cloud. They solved the following:
Agentless scanning (Visibility)
Leveraged a graph (Prioritization)
Strong focus on the persona (Development teams)
Everything Starts With The Underlying Architecture
The key to Wiz’s success lies in its graph-based architecture, which powers everything from its database to its user experience. The idea of using a graph database was nothing new in 2020, but utilizing it as the foundational platform for solving cloud security incidents and vulnerabilities was breaking new ground.
Why do you need a graph?
In this context, a graph is a data structure that represents entities (e.g., cloud assets, workloads, or users) as nodes and their relationships or interactions (e.g., access permissions, data flows, or network connections) as edges. A graph-based model is fundamentally a representation of relationships between two cloud entities;
Nodes (vertices): These represent cloud assets such as compute instances, storage, users, security groups, or services.
Edges (links): These are the relationships or interactions between the nodes, such as permissions, network connections, data flow, or access control policies.
Cloud environments are inherently complex, with thousands of resources constantly being created, modified, and destroyed. A graph-based model enables Wiz to map these dynamic, interconnected components—including virtual machines, containers, databases, APIs, and networks—into a cohesive structure.
What sets Wiz apart from competitors?
Traditional security approaches, which rely on scanning individual assets or configurations in isolation, struggle to provide the full context of how these assets interact or what risk those interactions pose. Wiz’s graph-based architecture, on the other hand, allows for a comprehensive understanding of how these assets interact, giving security teams visibility into potential vulnerabilities or misconfigurations.
This architecture enables security teams to fully map and understand their entire cloud infrastructure, a critical need in today’s dynamic multi-cloud environments.
Wiz’s graph creates a visual and analytical map of the cloud infrastructure, showcasing resource interactions and highlighting potential risks. This deep visibility allows teams to analyze misconfigurations more effectively than competitors and, more importantly, to understand the full cloud context.
For instance, security teams can easily create searches and convert those searches into saved dashboards for other teams to use, driving product adoption across the organization. A fundamental understanding of the graph is crucial for their product success.
How The Graph Translated to a Top-Tier User Experience
A graph-based model allowed Wiz to:
Visualize Complex Relationships: Graphs provide a clear representation of how different cloud resources are connected. For example, they show how a database might be connected to an internet-facing virtual machine, or how a user account might have over-permissioned access to critical workloads. This level of visibility helps identify attack paths and misconfiguration.
Prioritize Risks Based on Context: One of Wiz’s key differentiators is its ability to prioritize security risks by analyzing the context of vulnerabilities. This context allows Wiz to analyze and prioritize risks based on various factors, including security, business impact, network, identity, data, and more. For instance, a vulnerability on an isolated virtual machine might not be critical if it’s not exposed to the internet or lacks sensitive data. However, if that machine has a misconfigured firewall or is connected to other critical resources, the risk becomes much higher, and Wiz flags it for more accurate risk prioritization.
Efficient Attack Path Analysis: Wiz's graph can trace potential attack paths quickly and highlight chain vulnerabilities. For example, an attacker might exploit a vulnerability in a less critical system to move laterally within the environment and access more valuable assets. Wiz’s graph model maps out these attack paths, helping security teams focus on the most significant risks. If a vulnerability is detected in an exposed database, the graph can immediately show which services, applications, or users are connected to that database. This provides teams with context about potential attack paths, helping prioritize critical issues over less impactful ones.
Contextual Remediation Workflows: With a graph, all assets, their configurations, and interdependencies are available at a glance, enabling targeted remediations prioritized by interconnected risk rather than isolated severity. Wiz's graph model fundamentally reshaped how cloud security teams and developers contextualize and remediate cloud security issues. It retains context on all resources and configurations, allowing Wiz to offer specific, step-by-step remediation recommendations tailored to each resource. By understanding complex relationships efficiently, querying relevant information becomes easier. Additionally, because graph databases maintain both direct and indirect relationships between resources, they enable targeted and highly specific remediation workflows.
Automated Dependency Tracking and Impact Analysis: Graph databases allow for automated tracking of dependencies between resources, configurations, permissions, and workloads. This enables security teams to quickly understand how changes in one part of the cloud may impact other parts.
Misconfigurations
For Example, Misconfigurations are one of the leading causes of cloud security incidents. With a graph-based model, Wiz excels at identifying and contextualizing misconfigurations, such as:
Over-Permissioned Roles: Identity and access management (IAM) misconfigurations are common in cloud environments. A graph can show which users, services, or roles are over-permissioned and how they could be exploited by malicious actors.
Network Exposure: Wiz’s graph can reveal whether critical assets are improperly exposed to the internet or to other untrusted networks, enabling quick identification and remediation of misconfigurations.
Data Flow and Compliance: Understanding where data flows within a cloud environment is critical for compliance and security. A graph-based model helps visualize how sensitive data moves between different parts of the cloud, ensuring that the right security controls are in place.
Wiz wasn’t first. Why Did The Competition Lose?
Several predecessors of Wiz at the time leveraged relational databases relative to Wiz’s Graph. While a popular competitor in the market at the time used an agentless deployment approach, allowing it to scan cloud environments without requiring the installation of agents on each workload. However, this company and predecessors still faced challenges compared to Wiz because, while it offered visibility across workloads, its system was more focused on identifying isolated risks without as much depth into contextual correlations between different resources. They only emphasized the visibility of all running workloads, but this doesn’t extend into the broader architecture that could capture context and complex toxic combinations in the way that Wiz’s graph-based architecture does. The large predecessors at the time like Check Point CloudGuard, Aqua and Palo Alto Networks had heavy traditional agents (not eBPF as we know it) that that customers were deeply unsatisfied with at the time (but had no better solution). These agents had rule-based alerts, and scanned workloads in isolation giving lots of false positive alerts. While agents were effective for providing in-depth monitoring at the workload level, they required more time and resources to deploy, manage, and update. Since these increased deployment complexity and operational overhead compared to Wiz’s streamlined agentless deployment.
Why Graphs Are Critical in Securing Cloud Environments
It’s all about relationships, context and connecting dots. Let’s explain:
Mapping of Risks: In cloud environments, security isn’t just about the individual assets but understanding how those assets interact. A graph-based approach offers holistic visibility, allowing security teams to visualize the interconnections between cloud resources and assess whether those connections introduce security risks. Attackers often exploit small, seemingly insignificant vulnerabilities to escalate their access or move laterally across cloud environments. Wiz’s graph-based model simulates potential attack vectors and maps out threats, enabling organizations to take preemptive action.
Efficiency in Identifying and Prioritizing Risks: In cloud security, not all vulnerabilities are created equal. The graph model allows Wiz to contextualize vulnerabilities by understanding their impact on the broader cloud infrastructure.
Context-Aware Risk Management: For example, an exposed database containing sensitive customer data connected to an over-permissioned service account, would be flagged as a higher risk than an isolated system. The graph helps prioritize remediation efforts by showing which vulnerabilities have the highest potential for exploitation.
Reduced False Positives: Wiz's ability to map dependencies and relationships using the graph model reduces false positives. By understanding the context around a security event, Wiz can determine whether an issue truly poses a threat, as opposed to merely flagging all vulnerabilities without understanding their impact.
The graph DB enhances huge flexibility: Additionally, the flexibility of Wiz’s graph DB allows for the easy addition of new asset types and relationships as they evolve.
Visibility: Agentless Scanning
Wiz addressed the most basic yet fundamental cloud security need— cloud visibility via agentless vulnerability scanning. While simple in concept, implementing this feature effectively posed significant challenges. Wiz managed to execute it exceptionally well, outperforming competitors at the time. Wiz prioritized visibility as the foundation, delivering a user experience that focused on providing fast, clear insights into cloud environments.
Wiz launched different scanners for a variety of vulnerabilities, but specifically they had a highly effective agentless scanner that helped teams identify vulnerabilities quickly, offering rapid time-to-value and deployment for even the largest enterprises. By leveraging its graph-based architecture, Wiz built a more advanced agentless visibility solution, enabling software development teams to easily visualize threats across their networks (internet-facing versus non-internet-facing risks).
Wiz’s success stems from meeting market demands at precisely the right moment. In the early days, cloud visibility was a slow-emerging problem for security teams, as they attempted to migrate their on-premises tools to the cloud. Between 2020 and 2021, as companies rapidly moved to the cloud and faced attacks like Log4J and the Capital One breach, Wiz’s solution proved pivotal.It offered a non-intrusive way to gain visibility with agentless scanning, which was critical, with security teams beginning to realize the scope of cloud security challenges.
As the market evolved, security teams began recognizing the limitations of a purely agentless approach, such as the lack of code context and runtime defense. Rather than sit on their laurels and double down on its agentless approach, Wiz anticipated this shift and expanded its capabilities, introducing an agent (almost two years ago), GitHub integrations, and a Data Security Posture Management (DSPM) solution. Although some of these features may not be as advanced as those of competitors, Wiz’s focus remains on delivering an exceptional user experience, rolling out features precisely when customers need them.
Three key product capabilities set them apart from their competition:
Advanced Prioritization Engine: In the early days of Cloud Security Posture Management (CSPM), security teams were often overwhelmed by meaningless alerts that added little value. Wiz’s prioritization engine was an early attempt to correct this problem. While competitors typically scan individual assets in isolation, Wiz provides full context on how assets interact and the risks posed by those interactions. By using threat intelligence and context, Wiz ranks vulnerabilities, helping enterprises prioritize critical issues. Its low false positive rate—under 5%—ensures teams aren't overwhelmed by unnecessary alerts, giving it a competitive edge over competitors like CrowdStrike and Palo Alto, even though those providers now offer similar features.
Cloud Attack Path Analysis: Wiz's graph-based system naturally supports attack path analysis. It can prioritize risks by evaluating the context of vulnerabilities and trace potential attack paths quickly. It maps how an attacker might exploit a less critical vulnerability to move laterally across an environment and access more valuable assets. This context-driven analysis helps security teams focus on the most significant risks. While this feature has become somewhat commoditized, with many Cloud-Native Application Protection Platforms (CNAPPs) offering similar visualizations, Wiz remains ahead due to its early implementation and the flexibility of its graph search.
Toxic Combinations: Wiz toxic combo represents a BIG capability within Wiz’ product. When I refer to toxic combinations, I mean the intersections of seemingly benign configurations, permissions, and resource interactions within a cloud environment that, when combined could result in a serious security vulnerability. These combinations can lead to unintended privilege escalations, resource exposures, or breaches that wouldn’t be evident if each component were assessed in isolation. In cloud security, toxic combinations are a hidden and critical risk factor, making it vital to identify and address them proactively. This feature is enhanced by their graph database, which allows Wiz’s platform to contextualize risks by understanding how resources interact in real-time, thereby reducing misconfiguration alert counts by consolidating them into a single alert.
Now with clear visibility and context provided by the graph, security teams could assign specific remediation tasks directly to relevant developers or DevOps teams with full context into why each action is necessary. This minimizes back-and-forth communication and empowers teams to act confidently and quickly. Wiz’s Customers (which are mostly developers and cloud-teams, not security teams) frequently highlight Wiz's user-friendly interface and automation features, which allow security teams to quickly prioritize critical issues, and create common dashboards with engineering teams. Its intuitive scanning engine detects vulnerabilities out of the box, requiring minimal customization.
Five Crucial Factors At Play To Hit The First $100M
Making the graph visually appealing for users
Timing of the launch
Early Wiz customers
Building for scale and breadth
Lack of customer education
Making the Graph Visually Appealing for Developers
Almost anyone can look at this graph, visually map it, and connect the dots on how to investigate an issue in the cloud. Wiz Attack path visualization don't just show the potential breach scenario - it also pinpointed the critical steps to sever a toxic combination and close an attack path. This provided actionable insights and clear guidance on what security measures need to be implemented, saving valuable time and resources. It made it easy for teams to track, investigate and made it “fun“ to use daily
Early Customers
Today, Wiz commands over 45% of the Fortune 100 companies, but its path to success was forged early on by learning to scale rapidly for large organizations. Many of Wiz’s initial customers were enterprises with 10,000 to 100,000 employees, managing tens of thousands of different cloud assets. This forced Wiz’s team to architect their platform for massive scalability from the outset. Their experience at Microsoft, where they specialized in building for scale, proved invaluable in ensuring their solution could handle the demands of these large enterprises.
Notable early customers like Bridgewater, FOX, Cushman & Wakefield, and Avery Dennison, along with global brands such as BMW, Colgate-Palmolive, Chipotle, LVMH, Mars, Salesforce, and Slack, were crucial in shaping Wiz’s capabilities to meet the growing needs of cloud-native environment
Building For Scale & Breadth
Scalability became one of Wiz's core strengths. The platform was designed to adapt seamlessly to growing workloads and increasingly complex cloud-native use cases. Unlike many competitors, Wiz minimizes the need for custom rule creation or extensive manual configuration by handling common cloud environments natively. This approach allows organizations to scale effortlessly without being burdened by operational complexity, ensuring that Wiz continues to provide value even as cloud environments expand.
Timing Was A BIG Factor
Timing, in many different ways, was a crucial factor. Timing for the fact that the company was founded at a time (onset of the pandemic) when companies where transitioning to the cloud was a critical factor for every technology company. The pace at which companies were making this transition necessitated a security-first approach of visibility into everything happening in their cloud environment. Another crucial timing element was the Log4shell attack - which was responsible for Wiz capturing a significant part of its early customer base.
Log4shell Attack [CVE-2021-44228]
The most critical moment in Wiz’s history was the Log4Shell vulnerability crisis in December 2021, one of the biggest attacks in cybersecurity history. The Log4Shell vulnerability (CVE-2021-44228) was a major security flaw in the Apache Log4j library, which was widely used in web applications and cloud environments. Attackers could execute arbitrary code remotely, affecting countless applications globally, and many organizations struggled to locate and patch affected instances across their infrastructure.
Wiz rapidly responded by scanning for all instances of Log4j across cloud workloads, mapping interconnected assets, instances, applications, user roles, and sensitive data flows. Their real-time insights allowed organizations to assess whether a vulnerable Log4j instance was on an internet-facing server or had access to sensitive information, enabling teams to prioritize patching based on exposure risks rather than CVE scores.
Wiz’s approach went beyond simple detection. By mapping the connections between Log4j libraries and application dependencies, server workloads, and cloud resources across multiple cloud providers, Wiz quickly identified where Log4j was present—even in remote services or less-visible instances that traditional scanning tools might miss.
Not all instances of Log4j posed an equal risk; some had higher exposure based on configuration and usage. Wiz’s graph-based approach allowed security teams to prioritize vulnerable instances that were internet-facing, connected to critical data, or part of sensitive workflows. This contextual risk scoring helped security teams focus on the most critical areas first. The graph visualization of dependencies also enabled teams to have contextual remediation paths. In short, Wiz’s security graph gave customers context for each vulnerable instance, highlighting which workloads were internet-facing, had high privileges, or required immediate remediation. This approach was especially valuable for high-priority assets, such as databases or systems containing sensitive data, where exposure could cause significant damage.
To further support the industry, Wiz published a series of blogs and resources, offering guidance on how to detect and prioritize the remediation of Log4j issues using their platform. Some of its public research that got wide praise and attention includes:
Log4Shell Meltdown: How to protect your cloud from this critical RCE threat
Bridgewater swiftly remediates Log4shell vulnerabilities with Wiz
Log4Shell 10 days later: Enterprises halfway through patching
Wiz’s platform was widely recognized for its effectiveness in handling the Log4Shell crisis, as it provided organizations ways to deal with the issue and control over potentially vulnerable instances across multi-cloud setups.
Lack of market education on the problem aided rapid deployment and sales
One key factor behind Wiz’s rapid adoption was that its target customers, many of whom were large enterprises, were already well aware of the risks and challenges associated with cloud security. These organizations didn’t need to be educated on why cloud security was critical; they were actively seeking better solutions that could address their complex needs or to replace the poor solutions they had. This readiness made it easier for Wiz to sell its product, as conversations with CISOs focused less on the 'why' of cloud security and more on the 'how' Wiz could provide deeper, scalable protection and quick deployment of security. This allowed Wiz to accelerate its sales cycle and quickly gain traction amongst Fortune 100 companies.
Key Insights from Wiz 1.0
Several critical factors drove Wiz's rapid growth to $100M, many of which have been outlined above. The key to this success lay in addressing a well-known problem with a unique solution: building a security graph that not only scaled effortlessly but also offered advanced agentless visibility, rapid deployment, and highly contextual alerts. This powerful combination enabled organizations to gain deep insights into their cloud environments without the operational burden of traditional security tools. While much of Wiz’s growth was driven by its innovative approach and execution, there was also an element of timing and luck that played a role in the company’s journey.
Wiz 2.0: 2022-2024: Cloud Platform
The Wiz’s evolution subsequently continued as they began building the framework for a comprehensive platform anchored by its security graph. Initially focused on helping companies overcome visibility challenges, Wiz laid the groundwork for further growth by extending its capabilities both left and right of the cloud infrastructure. This journey began by addressing cloud risks originating from application code and soon expanded to recognize that many threats also emerge when applications are in runtime.
Throughout its history, Wiz has made only two acquisitions (Rafft and Gem), each carefully aligned with its platform objectives of left and right of the cloud: ie. to secure code and defend cloud environments. These acquisitions reflect Wiz’s strategic foresight during the critical 2022–2024 period, positioning the company to stay ahead in the evolving cloud security landscape. Let’s explore each of these acquisitions in more detail:
Wiz Code (Shifting Left)
Over 50% of Wiz users sit outside the security function. The vision of securing code goes back all the way to December 2021. At the time, Raaz Herzbeg, Wiz’s Head of Product, stated:
“We are releasing something today…I honestly believe will transform the way organizations do cloud security by basically enabling them to extend that type of solidified scan across any architecture type and any cloud, and also extending that across the full development pipeline…. The way it works is that admins can define the security policy they want to apply to the code in the pipeline. As the code moves through the production cycle, it continually checks it for anything that falls outside of compliance and flags it for fixing before it becomes a problem”
Recognizing that many early Wiz users were development teams, the company aimed to listen to developers’ needs and ensure secure application development. In December 2021, they launched "Wiz Guardrails," designed to create a unified security policy that protects code from creation to production. “Wiz Guardrails” initially came in the form of a command-line interface (CLI) application, extending Wiz’s initial product coverage from cloud infrastructure to the development pipeline.
Since many of early Wiz users were development teams, they always had the vision of catering of listening to the developer and understood how important it was for applications to be built correctly from Code. In December 2021, they launched what was then called “Wiz Guadrails” - designed to create a single security policy to protect code, from creation to production, essentially extending the coverage of the original product from the cloud infrastructure to the development pipeline.
November 2023
Wiz continued its developer-focused strategy by acquiring Raftt, a startup with extremely talented employees who understood the code problem.
This acquisition was primarily centered around bringing in talent that deeply understood the developer problem. Raftt provided Wiz with speciality in developer environments which run in the cloud since Raftt’s product enabled developer collaboration while using existing local IDEs and workflows.
James at Latio Tech has more details on Wiz Code:
“Raftt was working on the hardest problem that exists in the Developer and DevOps spaces, connecting local developer environments into cloud kubernetes environments. This acquisition made no sense if the goal was to band-aid another product the way ever major CNAPP player tends to go about things. Instead, it made perfect sense for building a meaningful native solution.”
Some of the best analysis of Wiz Code can be found on Latio Tech in this piece and Latio Pulse.
Today: Code to Cloud Mapping
Wiz has expanded its presence in code with a wide variety of products, including tools for scanning code repositories. They have also further enhanced their ability to trace risks in the cloud automatically back to the code and teams that introduced them, providing in-code remediation guidance to developers, container image integrity and in-cloud agentless SBOM scanning. The announcement of Wiz Code represents the culmination of a three-year journey for Wiz in Developer security.
In a previous post, I discussed the role of Wiz Code. While the product may not offer the depth of features found in some competitors, it encompasses many core capabilities necessary for teams to effectively develop within cloud environments. Wiz Code is an ASPM product which provides its own SCA, IaC and secrets scanning, while also ingesting findings from SAST (Checkmarx integrations) and DAST solutions.
It’s important to note that today, SAST ingestion is not limited to Checkmarx;findings can be ingested into the Wiz Security Graph from any 3rd-party SAST scanner (no limitations). Checkmarx is simply the first officially certified integration, part of the WIN – Wiz Integration – extensibility platform. Wiz has many more certified integrations in the pipeline for the future.
I recommend that people read James’s full analysis of the Wiz Code. This is also a good resource.
I would like to highlight two core capabilities:
Code-to-cloud Pipeline Mapping: This pipeline, built around the security graph, correlates vulnerabilities in application code with their deployment context, mapping issues directly to cloud environments. Users can click on a vulnerability in a container in production and see the repository and docker file from which it originated. By tagging containers and tracking metadata, Wiz provides security from **code to runtime**, identifying specific vulnerabilities and exposing their cloud risks, such as internet exposure or sensitive data.
Enhanced developer experience with unified policy engine: Wiz Code allows security teams to enforce a single set of security policies across the entire software development lifecycle—from version control through CI/CD pipelines and up to the Wiz Admission Controller for Kubernetes. This unified policy engine covers key areas like secrets management, SCA, IaC, and sensitive data, ensuring comprehensive protection across workflows. Integrated into developer environments such as VS Code, GitHub, and GitLab, Wiz Code surfaces real-time security insights and automated fixes directly within their user interfaces. Security and development teams can configure policies once and embed them across IDEs, pull requests, and builds, ensuring consistent security throughout the process.
Overcoming CLI deployment challenges: Traditional security scanners deployed via CLI in CI pipelines often face limited visibility and require complex setup. Wiz Code connects directly to your Version Control System (VCS), gaining full visibility over all repositories simultaneously. This streamlines the security process and reduces gaps, eliminating the need for piecemeal CLI integrations and ensuring security is applied uniformly across your codebase and CI/CD workflows.
Device-based authentication: Wiz Code now includes device-based authentication for the Wiz CLI, streamlining secure access to repositories and development tools. Combined with IDE integrations, such as VS Code, developers can authenticate securely and receive real-time feedback on code security without leaving their coding environment.
Pipeline Security Posture Management: Legacy developer security often focused narrowly on code vulnerabilities, neglecting to secure the very tools and environments developers rely on daily. Wiz Code extends Wiz’s Cloud Security Posture Management (CSPM) capabilities to developer environments, including version control systems (VCS) and CI/CD pipelines. By integrating configuration data from these developer tools into the Security Graph, Wiz Code enhances visibility and provides more accurate risk prioritization, enabling security teams to focus on critical attack paths. By enforcing robust branch protection policies, limiting permissions, and establishing strict access controls, Wiz Code helps harden CI/CD pipelines against supply chain attacks and build trust in the developer infrastructure used to deploy applications to the cloud. Additionally, the configuration rules are mapped to emerging frameworks such as OWASP TOP10 CI/CD Risks and OpenSSF Source Code Management Best Practices, enabling teams to assess their compliance with out-of-the-box reports.
I’ve heard that Wiz Code's adoption rate among its customers is off the charts. As Wiz Code scales and adds more capabilities, it aims to establish itself as a one-stop AppSec solution with security context from code through cloud deployments.
Wiz Defend (Shifting Right)
Although Wiz Defend may appear new, its development has been ongoing. Since 2022, Wiz has launched products related to [Cloud Detection and Response (CDR)](https://venturebeat.com/security/rsac-2022-trends/) and introduced the Wiz Runtime Sensor on June 5, 2023.
The acquisition of Gem Security in 2024 helped accelerate the delivery of a product designed for SOC and Incident Response teams. Wiz Defend empowers SecOps teams to stop threats before they become breaches by automating investigations and visualizing threats, enabling rapid, informed responses to sophisticated cloud-native attacks.
Some of the best content on Kubernetes focuses on understanding how to handle Kubernetes clusters. Here are some great resources that I highly recommend reading:
Wiz Runtime Sensor
Once companies have established good visibility into their cloud environments and a solid posture as their cornerstone, they often become concerned with preventing threats within those environments.
The Wiz Runtime sensor is a lightweight eBPF agent used to collect true runtime signals, such as runtime network usage, processes, and memory use. It’s important to note that most signals, including vulnerabilities, host configurations and more, are still collected from their agentless API-based scan. Wiz can detect both known and unknown threats, including cryptocurrency miners, remote shells, ransomware, rootkits and techniques commonly associated with cloud and Kubernetes actors, such as container escape, remote code execution, lateral movement and persistence, and more. As shown below, Wiz can detect vulnerable containers.
Wiz enables security teams to set custom detection rules that can identify and respond to specific threat behaviors. This feature supports monitoring for sophisticated cloud-native attack tactics, such as remote shells, cryptocurrency miners, and ransomware, giving teams the ability to block threats automatically or send alerts as needed. By combining insights from Linux workload activity with cloud configurations and identity data, Wiz delivers a comprehensive overview of the threat landscape. By correlating runtime signals with audit logs and cloud-specific behaviors, Wiz offers a contextualized view of potential vulnerabilities and attack paths, helping security teams prioritize and act on critical issues more swiftly.
Wiz has enhanced its agentless vulnerability scanning by integrating runtime workload insights, allowing teams to prioritize remediation efforts based on real-time threat signals rather than relying solely on static CVE scores.
Bolstering The Cloud Detection & Response (CDR) Solution
In April 2024, Wiz announced its acquisition of Gem Security for $350M. It’s largest acquisition primarily to allow them enhance their CDR capability.
Gem was an agentless CDR solution. Although it included inventory scanning, its primary focus was on logs and real-time data rather than periodic scans, thereby shortening the time required to investigate and contain cloud-native threats. In contrast to static industry solutions that lack real-time monitoring capabilities, Gem’s technology centralized real-time visibility into multi-cloud environments and provided automated incident timelines to help understand the root causes of cloud breaches. This focus on cloud-native investigation leveraging real-time analysis of log data was a necessary complement to Wiz’s existing sensor capabilities.
A core theme throughout this report is the synergy between Wiz’s Security Graph and Runtime Sensor, which together map out entire attack paths—from initial access through lateral movement—offering a cohesive view of an attack’s progression across cloud workloads, Kubernetes, and infrastructure control planes. This is critical for faster responses and prioritizing threats. For example, when attackers traverse cloud layers to access critical data, traditional tools struggle to piece together the attack. Wiz’s unified approach correlates indicators like suspicious network connections and identity actions, flagging coordinated malicious activity across cloud components that would otherwise appear as isolated, low-priority alerts.
In summary, the role of an agent based solution for detecting cloud security threats is vital. Wiz defend provides a broad, context-rich perspective across workloads, containers, and Kubernetes clusters, pinpointing vulnerabilities and correlating threats within the unique and dynamic context of the cloud environment.
Powerful GTM & Out Executing Competitors
Wiz 1.0 and 2.0 were primarily driven by a powerful sales engine that helped build on the foundations of a great product. Wiz did not establish a fully functional sales team until a year after launching its product. The company's story is one where the product essentially sold itself to customers. Once the product was fully developed, some core elements of its GTM strategy included leveraging partnerships with cloud marketplaces as a critical pillar.
Emphasis On Hiring A Few 10X Employees: I spoke with an investor in Wiz who shared that one reason for Wiz's early GTM approach was its deviation from widely recognized best practices, opting instead for a strategy authentic to the company. Rather than hiring a typical sales force with over-assignment ratios based on spreadsheet guidance or overly engineered sales playbooks, Wiz focused on recruiting exceptional 10X representatives and empowering them to hone their craft. These representatives consistently achieved over 1000% of their quotas on average. Additionally, each founder made it a point to meet prospects around the clock, a practice they continue to uphold today.
Multi-Cloud Marketplaces: From the outset, Wiz adopted a multi-cloud strategy to meet customers across various cloud ecosystems, including AWS, Google Cloud, and Azure. They recognized that many organizations, including major enterprises, were increasingly making purchases through these marketplaces. Consequently, Wiz leveraged platforms like Tackle’s Cloud GTM Platform to streamline marketplace sales and improve efficiency through automation, reducing transaction times and providing transparency across internal teams.
Co-selling with Cloud Providers & Partner Alignment: Co-selling is a foundational aspect of Wiz’s GTM strategy. By collaborating directly with cloud providers, Wiz enhances engagement and benefits from shared resources and brand influence. Notably, 99% of Wiz’s sellers have completed at least one marketplace transaction, underscoring the success of this model. An additional factor in Wiz’s GTM strategy is **partner alignment with hyperscalers like Microsoft and AWS. Wiz has invested in aligning its product capabilities with each cloud provider’s ecosystem, co-engineering solutions that showcase a “better together” value proposition. This alignment involves careful selection of products and sales motions that best meet customer demand and maximize compatibility with cloud services. As a result, it not only enhances co-selling performance but also strengthens Wiz’s foothold across cloud platforms, amplifying its market reach.
In FY25, Wiz made significant investments in solution providers and system integration partners, focusing on sourcing business and establishing partnerships that can drive platform adoption. They secured executive sponsorship in key partners across the AMS, EMEA, and ANZ. With an international expansion plan and a signed Softbank C&S distribution agreement, Wiz is set to rapidly grow its partner business in APJ in FY26. Looking ahead, Wiz aims to expand its bench of partners who can deliver professional and adoption services around the platform.
Creating A Strong & Powerful Brand: Almost everyone in the technology world has heard of Wiz. The company has successfully built a strong brand among customers, often surpassing larger cybersecurity firms in private markets. It's clear that any CISO you speak with is likely familiar with Wiz, largely due to its impressive product capabilities. Wiz has distinguished itself from competitors like Palo Alto and CrowdStrike through creative branding that effectively communicates real value and shapes the conversation around cloud security.
Wiz’s marketing team consistently delivers tangible value - from their cloud security job postings site to their history of cloud breaches. Combined with genuinely helpful research led by the highly trusted Scott Piper and Alon Schindel Wiz has made meaningful community investments. The team excels in marketing strategies, whether through thoughtful gifts, custom shoes, or local events. This competitive ground game ensures that Wiz remains relevant in any CNAPP evaluation. Furthermore, their knack for generating buzz (e.g., speculation on potential acquisitions) keeps them consistently in the conversation. Notable examples include the Wiz Mart at the 2024 RSA Conference and the playful title of Chief Dog Officer, held by Mika R.
Wiz 2.0: The Cloud Platform That Led To $500M
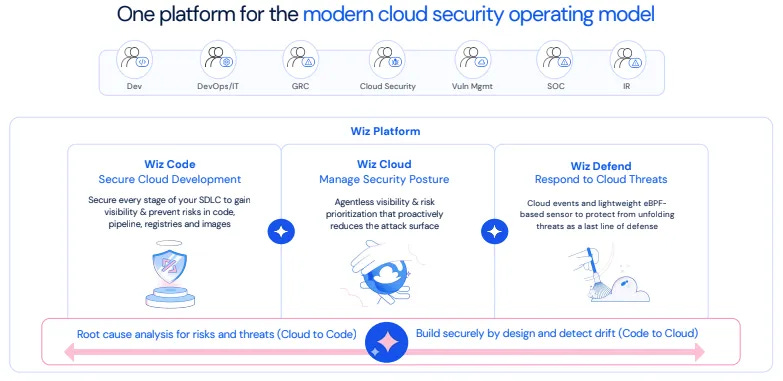
As Wiz wraps up its second phase, it can say it has a complete cloud security platform. One that integrates security across all phases, from software development to runtime, effectively closing the gaps that typically exist between different cloud and security teams. Although a big part of Wiz 2.0 is still early, requires further depth of capabilities and more importantly execution — despite this, it’s easy to understand how it has successfully hit a $500M ARR by implementing the following strategies:
Developer Workflow Security (Wiz Code): Wiz has built a platform that embeds security into the development phase, ensuring the security of code, dependencies, and configurations before they are deployed. This approach mitigates risks before applications reach production.
Deployment and Cloud Posture (Wiz Cloud): Once applications are deployed, Wiz offers visibility into an organization’s multi-cloud environment, resources and workloads through agentless scanning, allowing security teams to monitor and understand the security posture across all asset
Runtime Security and Threat Detection (Wiz Defend): Through Wiz Defend, the platform extends security into runtime, enabling organizations to detect and respond to live threats and incidents within their cloud environments in real-time.
Central to this integration is the Wiz Security Graph, which underpins Wiz’s platform by integrating data across all stages—development, deployment, and runtime. Over the past four years, Wiz has successfully developed these capabilities into a single platform. Unlike many competitors, Wiz has largely built its platform capabilities in-house rather than relying on multiple acquisitions. This strategy has allowed Wiz to maintain a unified codebase and a coherent user experience, creating a more seamless platform while reducing friction often associated with integrating acquired products. To further understand CNAPP, I highly recommend visiting this market guide by Gartner that simplifies many of these concepts.
Wiz 3.0: The Journey To $1B
When Assaf addressed Wiz employees after declining Google's $23 billion offer, he outlined the company’s ambitious goal to achieve $1 billion in revenue by 2026. In the history of cybersecurity, fewer than ten companies have reached this milestone.
In fact, out of more than 10,000 companies in the cybersecurity industry, only around 10 have achieved the $1 billion revenue mark (a mere 0.00001). This represents an extremely challenging goal within a short timeline of just five years.
When we look at the history of software and technology companies, there have only been a handful of companies.
Building A Mega Platform: Road To $1B?
As Wiz embarks on this ambitious journey, the critical question is whether it can maintain momentum. The next phase of Wiz’s evolution heading into 2025 will hinge on its positioning to meet its growth targets of $1B. The biggest question is how can Wiz subsequently extend its influence beyond its current strengths in agentless Cloud Security Posture Management (CSPM) to code and runtime analysis, especially as competitors reach feature parity?
The Cloud Security Market Opportunity
The cloud security market was valued at approximately $31 billion in 2023 and is expected to grow at a compound annual growth rate (CAGR) of 13.1%, reaching around $75 billion by 2030. This core market growth is driven by the increasing reliance on cloud services across EVERY industry and the demand for more robust security solutions to protect cloud-based environments. The core cloud opportunity is massive, but subsequently, many adjacent markets outlined below are within the context and premise of a cloud security vendor making it very for them to easily move.
Navigating competition
Another perspective of my graphic above is that it shows the competitive landscape adjacent to Wiz. The biggest challenge they face is that many of their product capabilities are relatively easy for competitors to replicate. Effectively managing the competitive landscape against companies like CrowdStrike, Palo Alto's Prisma Cloud and Microsoft Defender—Wiz's fiercest competitors—will be crucial for its future success. Additionally, emerging startups such as SentinelOne, Upwind Security, Datadog and newer runtime startups like Sweet Security and Armo will be key to watch as they pose a growing threat with their robust product offerings.
That said, it’s important to understand the massive data flywheel (leveraging the graph from some of the largest enterprises in the world), network effects across customers and non-qualitative components such as a powerful brand the company that every CISO recognizes. Many of these are advantages over the fierce competition.
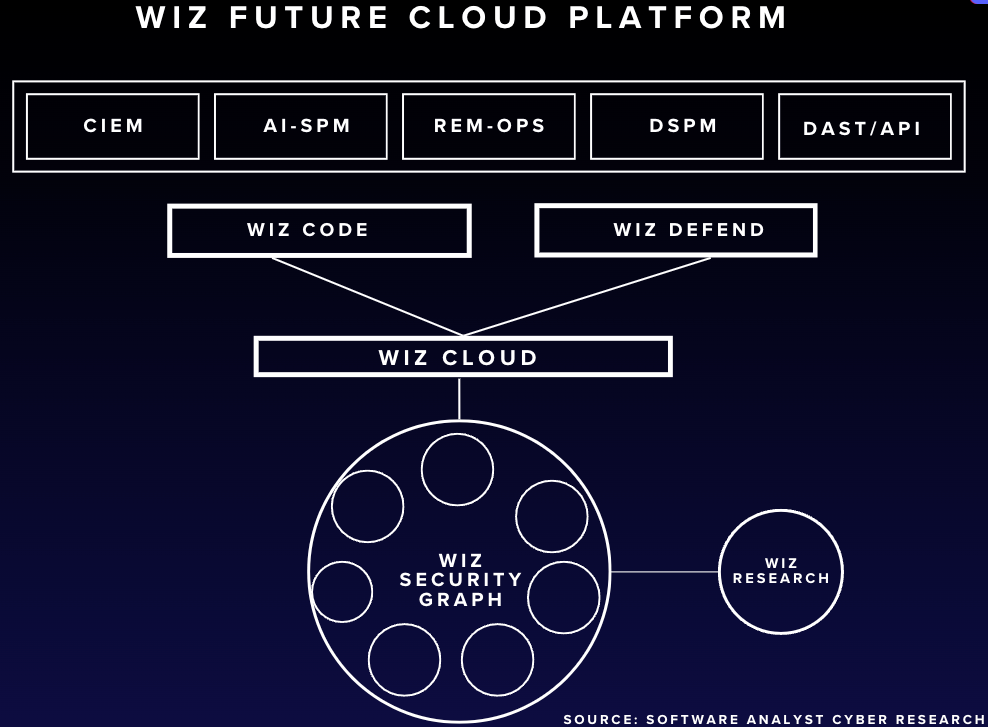
Future of Wiz: Expanding within cloud security niches
Going Deeper Into ASPM & SAST In Wiz Code: is becoming a key area for cloud security, especially as companies increasingly rely on microservices and API-driven architectures. Wiz could offer a full ASPM suite by integrating real-time application behavior monitoring and API security tools.
Advancing their agent-based solutions: While Wiz excels in agentless scanning, it has not yet fully matched the deep workload visibility and runtime protection offered by their competitors, according to our customer discussions. It'sIts worthwhile to note that Wiz has had an agent-solution for a long time. Additionally, the ADR space continues to gain traction, with competitors introducing unique runtime offerings. Many enterprise cloud environments also operate on mixed operating systems, and since Wiz lacks a Windows offering, companies may need to supplement their security with solutions from CrowdStrike.
Navigating the challenge of serving these diverse personas: They have to navigate the challenge of solving for left and right of the cloud. Most CNAPP platforms have been developed primarily for cloud security engineers, often with systems engineering or DevOps backgrounds. This focus has skewed these platforms toward scanning and contextual insights. However, as detection and response capabilities become more prevalent, the user personas for these alerts will increasingly include Security Operations teams, who have different preferences and requirements. Currently, no vendor has effectively addressed this split persona problem with a UX that satisfies both groups.
Expanding To Areas Adjacent to Cloud Security
Wiz has significant opportunities to expand beyond its basic capabilities into DSPM, API security, DAST, CIEM, AI-SPM and unified remediation operations (Rem-Ops). By focusing on integrating these capabilities into a cohesive platform that addresses the needs of DevOps, Security Operations, and development teams, Wiz can become a comprehensive security platform for enterprises. Each of these areas offers substantial growth potential, and by capitalizing on emerging trends and filling in gaps in the cloud security landscape, Wiz can position itself to reach its $1 billion revenue target and beyond.
Founding Team
I’ve provided a large amount of detail into the product and the future roadmap. However, it’s important to recognize that none of this would be possible without the team and huge talent density internally at Wiz.
I’ve gotten the chance to meet with a few co-founders and early team members. I also got to interact with Shardul Shah at Index Ventures (one of Wiz’s earliest investors who backed the founders back early in their Adallom days), who was kind enough to share some context. I wanted to share some context on how crucial the team was to the founding story.
A complete trust between the founders and a clear division of roles and responsibilities enabled them to focus on their areas of expertise with excellence (Assaf—brand and sales; Yinon—product; Ami—underlying technology; Roy—R&D). As soldiers, Wiz's co-founders were recruited to join Unit 8200, an elite cyber intelligence division. Their shared experience provided the education and tools necessary for entrepreneurial success.
Although each has been vital to the company’s success equally, if we were to distill the unique strengths or "superpowers" of Assaf, Ami, Yinon, and Roy into a single word or phrase, what would they be?
Assaf Rappaport - The Visionary Leader
Assaf, the "face" of Wiz, is renowned for his people leadership. He brings a powerful vision to the company, driving fundraising, branding, sales, and strategic partnerships. His unique ability to connect with industry giants, negotiate deals, and convey Wiz's mission makes him a natural frontman. Assaf's gift for storytelling and influence has been instrumental in securing support from top CISOs and investors alike.
Yinon Costica - The Product Architect
Yinon sits at the intersection of vision and execution, described as someone who always delivers on his promises. As one of the minds behind Wiz's product strategies, he helps the team anticipate market needs and identify new growth areas. His customer empathy and commitment to spending significant time talking with clients keep Wiz's product roadmap attuned to evolving customer needs. An academic educated at top institutions, Yinon's diverse knowledge base has enhanced his role significantly.
Roy Reznik - The Engineering Virtuoso
Known for setting the bar high, Roy operates more behind the scenes, but his engineering and R&D prowess forms the backbone of Wiz's architecture. A gifted mind from an early age, renowned for his work with graph databases, Roy has contributed significantly to their meticulous utilization of graph technology to enhance research and product development.
Ami Luttwak - The Technical Mastermind
Ami embodies the "CTO mind"—known for his ability to get to the essence of things and sift through noise. Deeply technical and knowledgeable, he has been one of the key minds responsible for ensuring Wiz's technological superiority. His experience as a Talpiot cadet and his role at Adallom have positioned him as a core leader at Wiz, where his passion for simplifying complex tech challenges has enabled him to create architectures that scale seamlessly.
The Early Heroes
Wiz's success wouldn't have been possible without its early team members.
Raaz Herzberg, CMO & VP of product strategy at Wiz - a UX and product expert, was employee #5, joining just two months after the company's founding and contributing critical insights into product design and user experience. Before Wiz, Raaz led security products at Microsoft, including Azure Sentinel. Raaz is a veteran of the intelligence unit of the Israeli Defense Force, where she started her career in cybersecurity.
Several other critical individuals, like Shir Tamari, head of research, and Alon Schindel, VP of AI & Threat Research, both former IDF engineers and researchers, brought depth to the research that continues to fuel Wiz's growth.
A Unique Culture: Pods within Squads
Every successful company in the history of technology has had a mix of the core skillsets to scale a company very quickly. Where one founder is weak, another founder is strong.
Overall, Wiz's culture embodies agility, competitiveness, and collaboration. Based on my discussions with employees, people at Wiz are proud to work there and are glad to share that with their networks. It’s easy for any industry observer to see it all on LinkedIn. (They introduced a “Wizfluencer” program, pink banners on many Wiz employee’s profiles on LinkedIn where Wiz employees volunteered to be ambassadors for their company’s brand.
Their product teams operate in a "Pod within Squad" structure, allowing cross-functional teams to move rapidly and autonomously. For Assaf and his co-founders, winning has always been the only option. This mindset has created a culture of intensity and excellence. Assaf and his co-founders hired many of their military cohorts, fostering early synergies. From the outset, the team was highly motivated and technically proficient, with a burning desire to succeed.
As we think about the future, beyond everything discussed, some of the biggest impediment to reaching their next goal lies in the human elements:
The hunger and ambition they had in their early days in 2020/2021.
Attracting the top 10% of talent (across engineering and sales into executing in these new product areas).
The overall success of the company hinges on these two core criteria, the talensity and culture to continuing executing as they did to achieve $500M
Concluding Thoughts
Wiz’s success is built on a foundation of truly listening to its customers, approach a common problem with a new solution, an incredibly talented team and obviously timing. Their pioneering use of a graph to solve cloud visibility challenges, coupled with a seamless UX for developers, set them apart early on. By focusing relentlessly on their customers’ needs and scaling their product for enterprise-level clients, Wiz has positioned itself as a leader in the cloud security market at a remarkable pace.
As Wiz looks toward the future, the path to reaching $1B in revenue is clear through three key drivers:
Continued product expansion in cloud & managing the intense competition. Thsi will mean expanding their platform within cloud security solutions, but having to be as good in adjacent cloud area.
Scaling with the workloads of their existing enterprise clients. They need to leverage their success with Fortune 500 companies to expand with them as they migrate more cloud workloads and deepen these customer relationships.
Lastly, continuing to attract top talent and fostering a culture of ambition and speed to fuel growth which is the lifeblood for any success platform company.
With these factors in place, Wiz is well-positioned to reach the $1B milestone, but this journey will certainly involve many hurdles and challenges.


















What a brilliant analysis! Thank you so much for this!
i just did a bunch of research on Wiz this month .... and BAM you come out with this piece.