Part 1: Palo Alto Networks - Platformization Earnings Dilemma
Dissecting Palo Alto Network's Earnings Report and the implications for the cybersecurity industry
Palo Alto Networks recently announced one of its most important earnings results in a long time after shocking the industry with the announcement of a major strategy shift. This strategic shift is themed around “Platformization.” Over the next few months, its ramifications will affect every cybersecurity company competing in network security (Firewall & SASE), cloud security, and security operation markets (SIEM, XDR, EASM).
I hosted a webinar with Cole Grolmus, of Strategy of Security to discuss this topic (we had Nikesh Arora scheduled to join us to share more about this strategy, but it didn't pan out due to the massive decline in the stock/the PR required that morning). Watch out for something here in the near future. In this webinar, we did an analysis of the Palo Alto results and its implications for the industry (video attached later).
Today’s brief article summarizes the earnings debacle, demand fatigue and high-level explanation of this new platformization approach. However, over the next few days, I will be meeting with some leaders internally at PANW to get more information to inform a follow-up Part 2 report. Keep an eye out for it.
Key Actionable Summary
PANW plans to implement one of the boldest moves ever made by a cybersecurity company. The week of February 21, when the stock dropped 28%, could either be a historic moment for Nikesh Arora that propels their next move higher if they pull off this strategy successfully, or it could serve as the beginning of a decline if this new strategy doesn’t work.
In this part 1, I provide a general commentary on their earnings report and why the stock has declined. I plan to examine the ongoing debate around “demand fatigue” in cybersecurity. Are customers really fatigued, or are CISOs/security leaders demanding something else? I’ll also elaborate on Palo Alto’s strategy for platformization.
In Part 2, I’ll discuss in detail, platformization vs. best of breed in cybersecurity. I’ll outline each of the differences between how Palo Alto Network’s approach is much different than Crowdstrike, ZScaler and Microsoft. I’ll provide more case studies and updates around network security, cloud security and security operations. I’ll also clarify misconception around their AI security business.
PANW Earnings Debrief Webinar
Cole Grolmus and I hosted a webinar where we provided an analysis of the earnings report, we discussed the pros and cons to this new strategy approach by Palo Alto Networks and the major takeaways for cyber investors/operators.
Please find the full recording of our discussion below. I’ll try to provide some highlights from that conversation in this piece.
If you prefer to review a detailed transcript of our conversation, please visit here.
✨ Cybersecurity & SaaS Bootcamp Program ✨
🔋 Quick Announcement: Thomas Robb and I are excited to host our 4th Cybersecurity & SaaS bootcamp edition here.
Cybersecurity Industry Indepth: Over 3-weeks, we delve into all the major cybersecurity categories from cloud, endpoint, network security to AI. Participants will gain a solid understanding of the major cybersecurity sectors.
Software Modeling Foundations: You’ll learn all the fundamental SaaS metrics, from FCF to billings and how to build a financial model for software companies. This session is led by former Morgan Stanley Analyst Thomas Robb.
Learn & Network: Participants engage with cybersecurity leaders to gain insights into the industry and future trends. This includes networking opportunities with top-tier participants.
🔋 Bootcamp Guest Speakers include a CISO, a Top VC and an Industry Analyst:
Alfonso Yi, Vice president of security at Prudential Financial. He leads a multi-million-dollar cybersecurity portfolio in New York City.
Shomik Ghosh, Partner at Boldstart Ventures. Shomik Ghoshand his team were leading investors behind one of the first funded AI security companies (Protect AI). We'll discuss AI Security, how AI is impacting cybersecurity and emerging VC trends.
Fernando Montenegro, Senior Principal Analyst at Omdia Global Cybersecurity. We’re pleased to host one of the leading cybersecurity analysts who will give us a 360-degree angle on the latest trends and rankings of the largest public and private cybersecurity companies.
PANW - What Really Caused The Stock To Decline 28%:
Palo Alto lost almost $30B in market cap value (although it has recouped most of those losses). I suspect the decline will last for a few quarters. So the key question is what happened? At a high level, PANW lowered its full-year billings and revenue outlook for its full fiscal year. There were a couple of factors behind this lower outlook and resulting stock decline.
A shortfall in PANW’s Federal business: One of the core components that isn’t being discussed enough is the significant shortfall in their U.S. federal government business. They had around a $600M billings revenue shortfall which hit the income statement. A big chunk of that was the delayed or perhaps lost Thunderdome project from the Department of Defense’s Zero Trust network architecture project. Here's some background on DISA's Thunderdome architecture. A big shoutout to Dave Vellante from the CUBE for uncovering this issue. Why is the Gov’t or Federal business key? Simply put, the government is the largest revenue contributor to Palo Alto Networks. Fed govt spend accounts for 50-60% of the FY billings The Gov’t pays annually (most of Gov’t products are hardware/firewall based). These govt contracts are shorter than PANW’s average contract terms, so any shortfall hits them hard. This is going to be a lingering issue over the next few quarters.
Platformization strategy shift that lowers short-term growth: This is a mouthful of a word that means several things and that caught the headline. First, PANW plans to sell most of their products as a platform or bundle, rather than going in on a product by product basis. eg. PANW would much rather sell their SASE suite (which bundles 10+ products) rather than only going into a strategic account by only wanting to sell an individual product feature like CASB or DLP solution. In certain cases, they plan to offer some of their products/services for free for over a 6-months period to incentivize customers to commit long-term. All of this means that PANW would be taking short-term revenue and billings hits, but if customers value the incentive and their product quality, this could mean longer-term, steady revenue streams.
Weaker Growth Expectations: #1 + #2 means their revenue and billings growth should take a temporal hit over the short-to-medium term. Although, they grew revenue by 19% to $1.98B and grew billings by 16% to $2.35B this quarter. Their billings growth guidance for next quarter is estimated to decline to 2-4% from 16% - a material decline. A big slump to what the market was expecting. None of these are good for your market valuation.
PANW believes they can make up for these short to medium headwind with more larger deals as the contracts ramp which should sustain long-term growth.
Demand Fatigue In Cybersecurity (?)
There has been a lot of discussion amongst investors and operators about this idea of a “Demand Fatigue” highlighted during the earnings call. Some people are trying to use this as an opportunity to say cybersecurity demand is declining and the entire industry will soon be experiencing a hit. This is false, but let’s review the initial quote from the earnings call from Nikesh Arora’s opening statement.
The part that is new, despite the many demand drivers we're seeing, we're beginning to notice customers are facing spending fatigue in cybersecurity. This is new. As adding incremental point products is not necessarily driving a better security outcome for them. This is driving a greater focus on ROI and total cost of ownership amongst most customers.
S/O to Morgan Stanley’s Hamza for pinpointing this during the earnings call and asking Nikesh to clarify his comments. Nikesh provided this response:
Over the last few years, most of our customers have ended up spending more on cybersecurity than on IT. As a consequence, they're feeling like my budget for cybersecurity keeps going up in double digits every year because I'm trying to protect against every new threat vector, yet you see the number of breaches continues to rise. So our customers are sitting down and saying, if I spend more money, can you show me how I get a lower total cost of ownership across my enterprise? How do I spend less on the services that I have to deploy? And how do we get better ROI. So I think it's more about optimizing their current cybersecurity budgets as opposed to there being no demand. Demand continues to be very strong. The customers are demanding to get more for the amount of money they have allocated to cybersecurity.
Nikesh’s point was that IT and security leaders are rather just demanding for better utilization for the products they have in-house. Many companies are trying to avoid shelf-ware i.e products that get bought, but no longer serve a core purpose. It also means customers are demanding that existing customers offer much more products/services that fit their needs so as to avoid having to buy more products from external vendors. This is also about optimizing customers current spending.
The reality is that there is no cybersecurity demand fatigue based on lots of industry data and other competitors on the market. I wrote extensively about some of the spending patterns/budget expectations from CISOs coming into 2024. Most of these data points were from Q42023/early 2024. I’ve also joined calls with CISOs, and across everything I heard/seen, the consensus is that cybersecurity budgets are going up or at-most staying flat into the year.
We have lots of data points from other cybersecurity companies that show there is no demand fatigue. Over 8+ public security companies (CyberArk, Cloudflare, Varonis, Qualys, Gen security, and large players like Checkpoint, Fortinet, ZScaler) that have reported that announced strong earnings and beat analyst expectations. None of them had any severe gloom around the current cybersecurity spending environment.
There are other major tailwinds that should drive security demand into 2024. One of the major propellent is the new SEC disclosure rule. The new SEC mandate requires prompt disclosure material incidents, which often result in companies reporting those incidents before a full assessment can be done or incidents remediate it. This SEC is driving more spending on security products to ensure companies have visibility and remediation into these attacks. Read more to understand reasons why this new rule will prompt many security companies to invest more into their security stack.
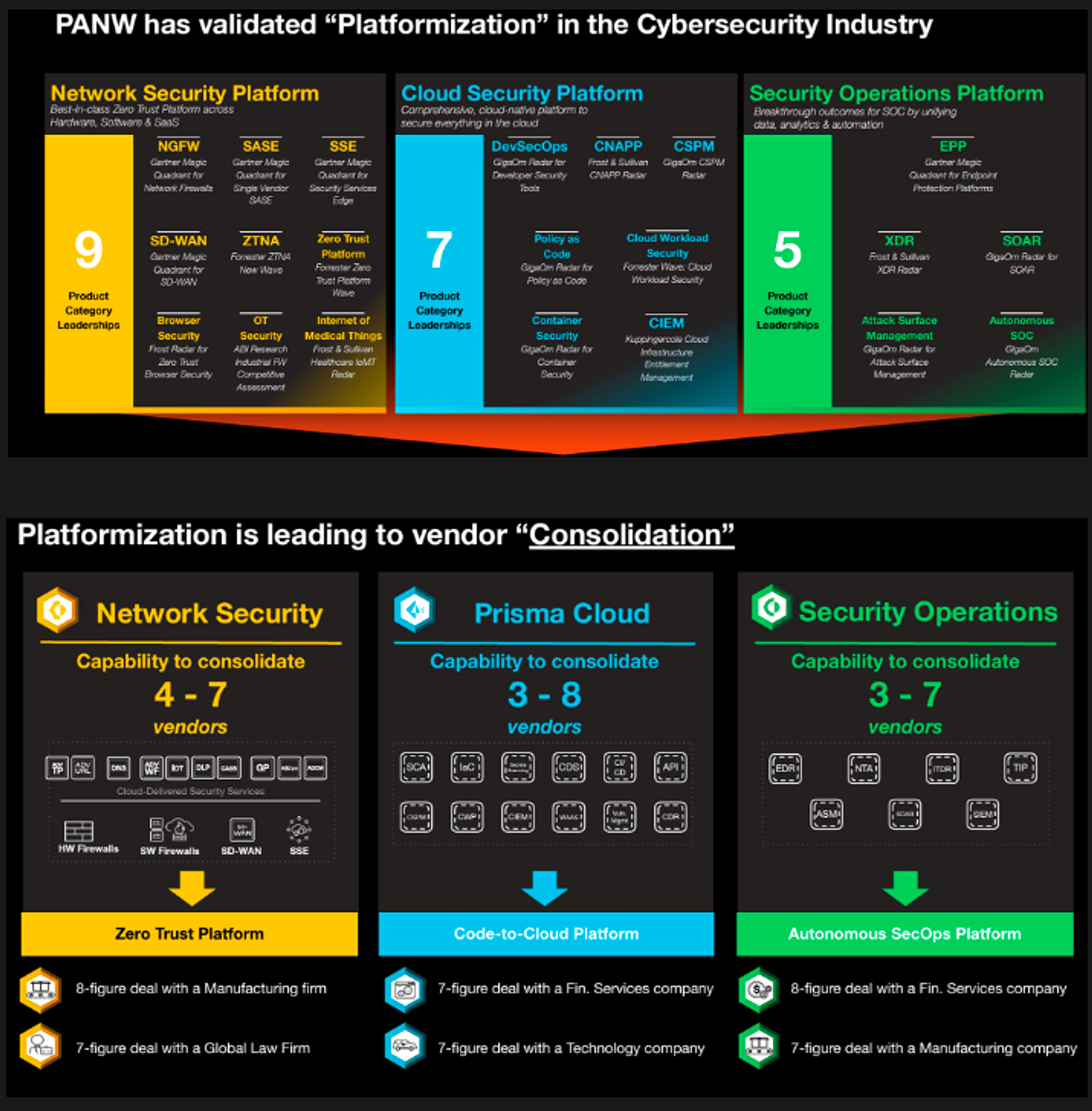
PANW Platformization Strategy
I won’t write much on this topic until Part 2 (after discussions with internal PANW leaders), but I’d like to share the platform consolidation piece I wrote a couple of months ago on Palo Alto Networks. Please check it out below.
In this piece, I want to address some of the key points discussed around platformization during the earnings call. Platformization is a strategy where they want to help their customers by consolidating the number of security products their customers use down to a few vendors. In the examples below, they plan to help companies consolidate 10+ products in their network suite to around 4 or less as well as a similar approach across their other product suite.
It’s important to understand that PANW’s strategy is not to become the single vendor to provide a comprehensive set of security tools and services for their customers. Its almost impossible for one company to provide all the cybsersecurity solutions for one company. This is an important misunderstanding I’ve been seeing across the industry. For example, identity (IAM) and email security are pretty large budget items for 90% of security teams, but Palo Alto has decided they won’t even venture into those markets. They don’t have solutions there and they are fine allowing their customers use products from those vendors.
This alternative approach to platformization is for customers to adopt a best-of-breed approach where, based on the attack vector that needs protection (e.g. data security and privacy solutions or, purchasing cloud security vendors for cloud workloads etc.), the customer goes out to purchase and choose the best provider to solve that problem, rather than expect their largest vendor to do it for them. In this model, companies don’t mind handling and dealing with multiple different vendors to secure different parts of their technology stack.
Why Palo Alto Networks Is Embarking On This Strategy (Now):
There is a big question for PANW on why they have decided to pursue this aggressive strategy now. Some people have suggested that most of it is prompted by the fact that they may be losing market share or trying to use price to incentivize certain customers. There are a number of reasons they’ve taken this direction from the last earnings call. The biggest reason is that they see this as the only way to aggressively take market share from competitors and double their business from here. Here are some other practical reasons:
Easing Customer Switching Costs And Execution Risks: They highlighted that customers often face risks when executing significant changes in their IT environments. Anyone who has worked at large enterprises knows this problem well. This issue is more prevalent among large Fortune 500 companies with thousands of employees. These companies have multiple old licensing agreements with different vendors. Worse still is that these Fortune 500 companies still have lots of workloads on-prem and many are still transitioning to the cloud. Hence, they encounter friction points when replacing multiple products simultaneously. With PANW's new strategy, the goal is to facilitate this process by helping these companies standardize on one platform by easing off the transition from an old vendor to a new one by offering products for free for a fixed period of time and overtime, hope the customer builds and standardizes on PANW’s suite.
Another issue following the execution risks are the financial terms when their customers deal with the issue of double payment and multiple complex contract terms when replacing vendors. PANW plans to solve this issue is by approaching customers who are considering PANW’s product, but do not want to pay upfront. They plan to approach customers (who want or are considering PANW’s product) before their license agreement with another vendor expires and once they gain their contractual commitment, they will offer those customers an extended rollout period which allows them to demonstrate their platform benefits. In many cases, they are wiling to offer their product for free for over six months. Customers can then start paying them after the obligation of the legacy vendors ends or as the customer wants. Essentially, they want to bear the cost of the transition for their customers with lower upfront financial commitments.
Wade off competition: Since PANW has the financial and technological prowess of many of their competitors to absorb some of the short-term costs of providing customers with their products for free, if successful, this could give them a significant upper hand against their competitors. All of this is built around the premise that their customers trust them to provide the best product for whatever threat vector they need from them. This will strengthen their competitive prowess when negotiating with customers. Many companies simply can’t afford to provide this level of financial flexibility for their customers.
The risks involved: The core summary is that this is a risky strategy, both from a financial and product perspective. The financial consequence means lower revenue and billings growth for the next two quarters (while they offer these free products to customers). There are risk factors if customers trial out these products, but don’t want to commit longer-term or if they find ways to get out of their existing contracts to avoid being locked-in for the longer haul. Some customers just dont want one vendor to manage a huge part of their security stack to minimize vendor lock-in.
Secondly, this will require PANW to have the best products in many of their categories. Beyond the ease of pricing/costs, customers must feel pretty confident about Palo Alto Network’s product quality and innovation on emerging threats. They must feel that PANW’s product offers the best protection for the right threat vector and hence this is what would give customers the confidence to standardize on PANW’s platform. This will likely require more acquisition and R&D costs while not earning as much revenue over that short-term. There are many more things which I’ll elaborate upon in my next report.
Part 2 Of This Report:
In my next piece, I’ll dive into more details around the platformization vs. Best-of-breed pros/cons, industry updates/themes across cloud, network and security operations. I’ll also provide answers to the following questions. These are strategic questions I’ve posed for Nikesh and the PANW team regarding their platformization strategy (I’ll share the outcomes of my conversations in that next piece):
In pursuit of platformization, how is PANW addressing the need to simplify deployment and mitigate execution risks, in addition to the financial incentives and cost savings you’re offering customers?
What strategies is PANW employing to sustain its best-of-breed status within its platform strategy, without relying solely on continuous acquisitions?
How is PANW managing the technical integration of its 21 products into three major platforms, especially knowing the distinct nature and users of these 21 products? We know some haven’t been as successful in stitching everything together
What are the primary challenges in executing this platformization strategy, especially given the failure of similar initiatives by industry leaders? Previous attempts at platformization failed primarily due to their focus on marketing over genuine technical product development. PANW's approach incorporates a crucial technical/product dimension, and what happens if you fail at this plan?
What is the ultimate goal of Palo Alto Networks' (PANW) platformization strategy, assuming it succeeds?
In addition, I’ll discuss how these compares to Crowdstrike, Microsoft and ZScaler.
Summarizing Everything:
Platformization takes time. Many of these strategic decisions will take time to know and understand their impact. It’s important to remind people that for companies to adopt and standardize on a platform, it takes months and years. They cited just how much time it takes their customers to adopt and standardize many security solutions on even one of their platforms. For example, for a new enterprise to adopt a SASE platform, it takes about 8 months to over a year. In cybersecurity, as much as customers care about cost savings and simplicity with platforms, customers ultimately care about effectiveness to protect them against cyber attacks.
The Palo Alto Thesis: The next few months are going to be challenging for PANW as they navigate the federal government shortfall as well as provide these platformization benefits for their customers. The good news is that there is no cybersecurity demand fatigue. All the major vendors have confirmed that cybersecurity demand is robust and strong coming into 2024. Ultimately, there is no dispute that large enterprises' demand for vendor consolidation remains high. Many security teams are bombarded with managing an average of over 50+ different security tools. PANW should be commended for attempting this bold approach. The company has successfully proven itself with successful acquisitions and leadership positions across its network security suite (Prisma Access/SASE), Cloud Security suite (Code-to-Cloud, Prisma Cloud), and Autonomous Security Operations (Incorporates SIEM, XDR, AI Security, EASM, EDR). The company is forecast to grow its next-gen software business by 34-35% over the next year. Despite this strategy shift, they’ve maintained their FCF and margin guidance for over 35%. They’ve made tremendous progress in transitioning the business to 80% recurring revenue thereby reducing their reliance on firewall/hardware growth relative to their competitors.
Before sharing my takeaways from my discussions with Nikesh’s team, I will share some of the latest trends within cloud and application security in the next week. Thank you for reading! If you have any questions you want me to discuss / bring up, please leave them in the comments.






Interesting how PAN is going for platformization while other vendors, like Securonix, advise against 'all-in-one' solutions, even though Securonix is in a good position to be a platform itself.
https://www.securonix.com/blog/the-perils-of-over-consolidation-in-cybersecurity/
Awesome work Francis!