The Complete Guide to the Growing Impact of Non-Human Identities in Cybersecurity
The report discusses the importance of non-human identities (NHI), the key vendors tackling the problem and why we are seeing a resurgence in this area.
Introduction
Readers,
Today, we’re exploring the theme of non-human identities (NHIs). NHIs have been among the buzziest topics this year, second only to AI security or AI SOCs.
One of my popular research reports earlier this year was on identity security. The focus at the time was primarily on human identities. However, the case for non-human identities (NHI) and its challenges have begun to resonate with CISOs and security leaders in 2024.
This report aims to provide an overview of NHI, explain why they are gaining traction, discuss its future outcomes (feature or platform) and provide a detailed breakdown of the major vendors in this market. The report helps differentiate between the key players across the identity ecosystem.
I got the chance to speak about NHI in New York City to an audience of CISOs and security leaders last week at an NHI conference. My goal is to share the key insights from my discussions with top leaders and the work I’ve gathered based on results from large global security leaders.
(Open in your browser for ease of reading.)
Key Reader Takeaways
Non-human identities (NHIs) refer to digital identities associated with applications, services, and machines. They include all the bots, API keys, service accounts, and OAuth tokens — all of which are credentials that allow machines to authenticate, access resources, and communicate with each other.
NHIs significantly outnumber human identities in any enterprise stack, with roughly 17 NHIs for every human identity. Indications are that for every 1,000 employees, there are over 20,000 NHIs. While NHIs are nothing new, there is a clear reason for the resurgence of their importance over the past 13 months.
NHIs are not located in one central location—they are fragmented and dispersed across systems. As a result of this large dispersion, companies find it difficult to pinpoint them. The biggest challenge enterprises face is gaining full visibility and maintaining an inventory of all NHIs across their enterprise stack.
One key finding is that currently, there is no clear identity solution that fully addresses the problems associated with NHIs. Modern identity security tools such as Identity Access Management (IAM), IGA, PAM, and ITDR offer partial visibility into NHIs within an enterprise, but none provide a holistic solution. This is why we've seen a new crop of companies trying to solve this issue.
There have been some critical debates around the future of NHI; I provide a strategic discussion on how they integrate with existing solutions within the enterprise and how to expect the future evolution of the industry.
Thank you to the software analyst's partners, such as Astrix, Entro, Natoma, Clutch, and Aembit, for helping to make this research project come together.
*****
The rising ecosystem for non-human identities
The rest of the report analyzes every component of this ecosystem market and how it will evolve over the next decade. A big part of the challenge is closely tied to the fragmented approaches that enterprises are using to solve this problem today. Based on extensive research and work I’ve done, it is clear no solution holistically solves the problem.
Fragmented process
This research report, which included 800+ security and IT leaders, similarly showed how organizations currently deal with the NHI challenge. This report clearly explains the reason for the rise in the ecosystem in the market map earlier.
Disjointed approaches for managing NHIs today
Some organizations utilize some form of CIEM, PAM, or PKI integrations to manage aspects of their machine identity challenge. Many organizations either use manual scripts or processes to deal with the issue. Based on the current fragmented identity ecosystem, where no one solution solves the problem, it is clear that the industry requires a comprehensive solution, which I have proposed above and discussed throughout the report.
Proposed Future Enterprise Identity Stack
Since no vendor solves this problem and the issue of NHIs deserves a holistic solution, the big question is if each of these traditional categories of identity security remain separate in the future - having their distinct swim lane or if we will see a convergence across both categories. The report delves into everything.
SA Quick Announcement & Report Acknowledgments:
Big shoutout and thank you to some of the leading NHI vendors and software analyst's partners, such as Astrix, Entro, Natoma, Clutch, and Aembit, for helping to make this research project come together.
Thanks to Lalit Choda, founder of the NHI Mgmt Group, for his contributions and review of the report giving feedback.
Francis - Bootcamp Announcement: We’re pleased to host my 6th and final cybersecurity bootcamp featuring a number of prominent cybersecurity leaders. This is a 2-week bootcamp that goes in-depth into the cybersecurity industry and provides security frameworks, including cloud, endpoint, and network security. The objective is to provide participants with a good grasp of cybersecurity using simple frameworks while also learning what differentiates the leading cybersecurity companies like Crowdstrike, Palo Alto Networks and emerging startups across multiple categories.
Identity Security Categories
The history of enterprise identity security solutions is fascinating. In my popular report this year, An In-Depth Overview: The Future of Cloud-Native Identity Security, coauthored with Alex Krongold and Daniel Bartus, we broke down the identity market and provided a thorough understanding of the identity ecosystem, with the main focus on workforce identity.
Foundational Identity Concepts
At its core, identity and access management (IAM) is about knowing ‘who (or what)’ is taking ‘what’ actions on ‘which’ resources to ensure people and processes remain productive while simultaneously remaining secure - across people and machines.
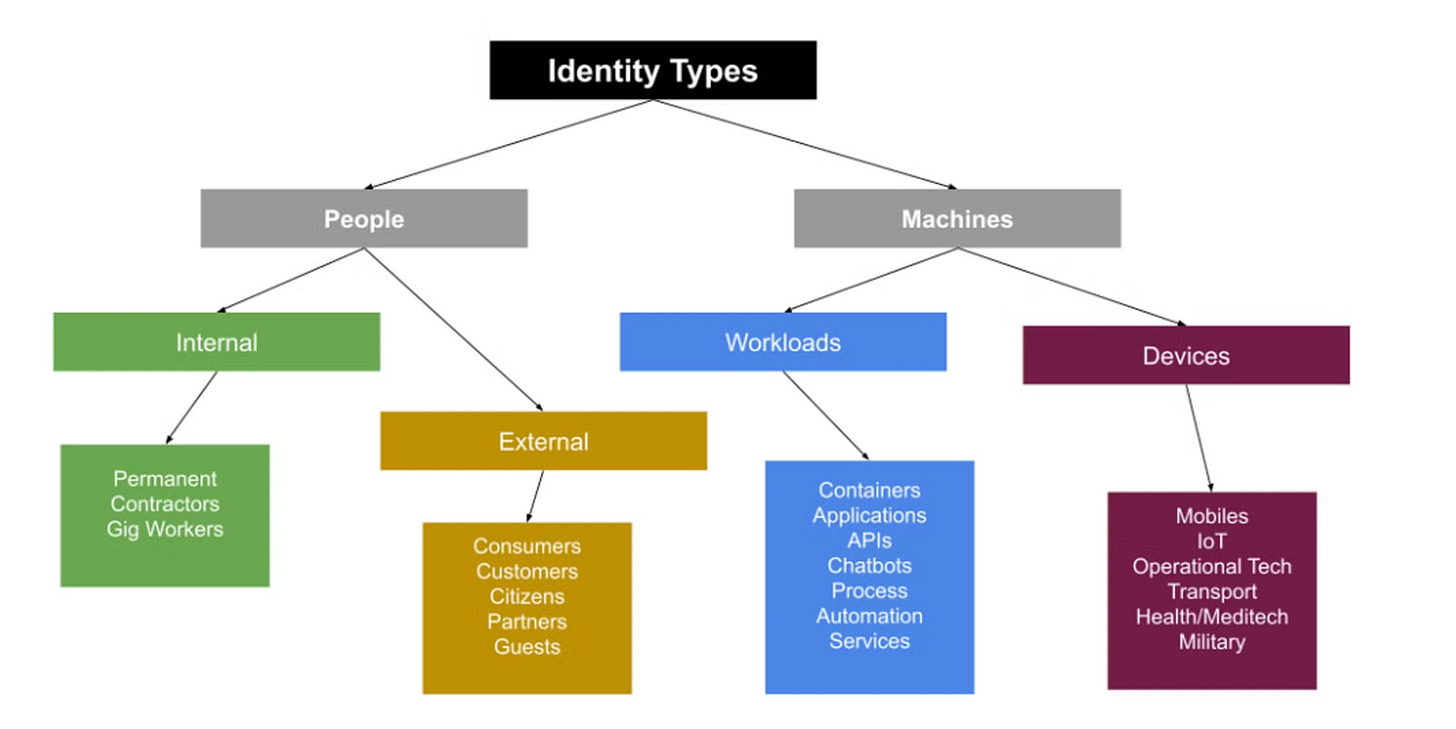
Historically, identity management focused on people i.e. managing human credentials through identity providers (IdPs) and access rights. However, the importance of managing non-human workloads and machines has grown significantly in recent years.
An Explosion of NHI is almost certain.
With the shift to cloud-native architectures, microservices, and DevOps practices, non-human identities are multiplying by the day. They now significantly outnumber human identities, and this trend is expected to grow fifty-fold by 2025. Unlike human identities, which are centralized and managed through Identity Governance and Administration (IGA) systems, non-human identities are often distributed across cloud environments, SaaS applications, on-prem environments and service-to-service communications. This creates a complex web of identities that lack oversight, making them an attractive target for attackers.
Defining NHIs (Non-Human Identities)
Non-human identities (NHIs) are digital identities tied to entities like applications, services, and machines within an enterprise technology stack. These include bots, API keys, service accounts, OAuth tokens, cloud services, and other credentials that allow machines or software to authenticate, access resources, and communicate within a system.
Where Are They Located?
NHIs are widespread and diverse, including service accounts, system accounts, secrets, webhooks, SSH keys, IoT devices, bots, machine identities, containers, microservices, RPAs, LLMs, automated scripts, and cloud resources.
This diversity and fragmented nature add to the complexity of managing NHIs, increasing the need for automation. Non-human identities are ubiquitous in organizations, found in:
Cloud-based and on-premises environments
Business platforms like Google Workspace, Salesforce, and Slack
Engineering environments such as GitHub, AWS, and GCP
Service accounts that exist in solutions like Snowflake
Service Accounts
Service accounts are special types of non-human identities used by applications, services, or systems to authenticate and interact with other resources within an IT environment. These accounts are typically used for automated processes, application-to-application communication, or to grant access to specific resources without requiring human intervention.
Key characteristics of service accounts include:
They are not tied to any specific individual user
They often have elevated privileges to perform specific tasks
They usually do not require interactive login
Service accounts can be found in various environments like Active Directory, cloud platforms, and databases. It has been seen that Active Directory service accounts (used for machine-to-machine communication within Microsoft’s Active Directory’s environments) are the most prevalent and vulnerable NHIs, within the large pool of NHI types. These identities are just as vulnerable to potential compromise and abuse as human ones. In fact, due to historic lack of visibility and protection, they might even be at graver risk. Typically, they have privileged access to sensitive machines, effectively making them admin accounts.
Silverfort, a leading ITDR vendor, has research that uncovers the scope of Active Directory service accounts, their exposure to compromise, and the confidence of security teams in discovering and protecting them By default, attackers frequently will target these service accounts for lateral movement due to their high-access privileges, low visibility, and protection challenges. Moreover , in many cases, service accounts fly under the radar of security and identity teams because they aren’t even aware they exist.
Why This Is A Large Attack Vector For Enterprises
The architecture is highly fragmented. Organizations face a massive challenge in trying to bring together this mesh in one architecture. More importantly, NHIs pose significant risks for large enterprises because they are:
Integral in connecting various systems, thereby allowing for many backdoors
Overly permissive by nature and they are often set without expiration
Inadequately monitored and difficult to detect during unauthorized activities
Capable of massive lateral movement, which increases the blast radius of attacks
Lack of MFA for NHIs: Unlike human identities, which are typically secured with multi-factor authentication (MFA), non-human identities often rely solely on static secrets (API keys, tokens). If these secrets are compromised, attackers can bypass most traditional security measures
Long Lifespans: Many non-human identities are created without an expiration date or have keys that remain active for years without rotation, further increasing the risk for exploitation
Like human IAM, non-human entities (such as bots, APIs, and IoT devices) suffer more from issues like excessive permissions, outdated credentials, and lack of monitoring.
Why NHIs Matter This Year?
This has been the biggest question from observers of this category. Most of these NHIs are nothing new within the enterprise. However, their importance and awareness have grown for several reasons:
Recent NHI Targets: Major breaches like the SolarWinds attack, AWS breach and many of the breaches which I discuss in the upcoming sections have exposed enterprise weakness in managing NHIs, making them a primary target for cyber attackers. Service accounts, tokens, and API keys often have elevated privileges and access to critical infrastructure, making them highly valuable for lateral movement or exfiltrating data once compromised. This is not just an issue about managing NHI risks within an organization's infrastructure; they are also heavily exposed to 3rd Party Supply Chain risks (a medium-sized organization typically has over 300 3rd party SaaS integrations)
Cloud Proliferation & Hybrid Cloud: The migration to cloud platforms (AWS, Azure, GCP) and integration with SaaS services has exponentially increased the use of non-human identities (known as Secrets Sprawl). Services in the cloud are interconnected through APIs, and these integrations require machine-to-machine communication using tokens, API keys, service accounts, and other forms of NHIs
Explosion in microservices architecture: Microservices rely heavily on non-human identities (NHIs) for internal communication. Each service typically has its own API keys, tokens, or credentials to interact with other services. This dramatically increases the number of NHIs, as modern applications are composed of hundreds or even thousands of microservices. The shift towards microservices has, in turn, sparked a wave of API security, often based on OAuth2. This need is further compounded by the requirement for automated management and data movement across diverse pipelines and trust boundaries, involving service accounts, chatbots, and now AI systems
AI Agents and Automation: AI agents, often designed to automate tasks, analyze data, make decisions, and or even interact with other systems autonomously, are classified as non-human identities. With the recent advancements in AI, there are predictions that suggest AI agents will drive growth across the board, meaning, the more companies that have AI agents and automated processes, the more we will have more NHI proliferation sprawl.
Investor funding and founders emerging: In the past three years, many companies have emerged to address the NHI challenge, and many investors are fueling growth in this niche.
Current Issues With NHIs Across Enterprises
NHIs typically have very weak identity lifecycle processes, in most cases they remain unmanaged, leading to significant security exposures. During my engagements with Lalit Choda, he shared the following around the top issues and challenges:
Plain-Text / Unencrypted Credentials - Organisations will often find that many NHIs have been hard-coded into source-code repositories (and other places) and therefore can be easily discovered by both External and Internal Threat Actors. Addressing these issues is a major undertaking for most organizations today.
Full Inventory of Accounts - Obtaining an inventory of all NHIs is very challenging, as there could be many platforms, end-points, directory services, cloud integrations where these NHIs exist.
Stale / Inactive Accounts - Due to weak lifecycle processes and a lack of visibility of account usage information, many NHIs end up inactive, which increases the attack surface area.
Lack of Account Ownership - NHIs in most organizations lack ownership information - it is critical to identify an owner for each NHI, to help drive hygiene/remediation activities.
Humans Using Non-Human Accounts - Humans using NHIs has always been a problem. It is very easy for users to by-pass human access controls and use a NHI account instead. This leads to repudiation issues and in many cases, the activities go undetected.
Lack of Credential Cycling/Rotation - Cycling / Rotating NHIs is very challenging for a number of reasons e.g. lack of password change information, unknown dependencies that could cause operational impact, changes required to application code/configuration, lack of secret vaulting capabilities and a lack of endpoint cycling capabilities.
Lack of Environment Segregation - In many cases, the same NHI gets used in production and non-production environments, or the same logical NHI has the same password across each environment, increasing the risk of lateral movement.
Sharing of Credentials - Sharing of NHIs across applications is a major issue, breaking the principles of need-to-have and least-privilege. This makes things like password cycling much more complex, as you don’t know all the dependencies of where a credential is being used.
Deep Dive Into Recent NHI Attacks
The growing number of machines and services introduces new attack vectors for cybercriminals. Instead of targeting humans with sophisticated security measures (e.g., FIDO2), attackers might exploit poorly monitored APIs with hardcoded credentials. There have been four notable attacks related to Non-Human Identities (NHI).
Diving into each of them:
Cloudflare - Exploiting inventory gaps
The Cloudflare Thanksgiving 2023 security incident involved a threat actor gaining access to internal systems by exploiting gaps in their inventory of non-human identities. Using credentials compromised in a previous Okta breach, the attacker accessed Cloudflare's Atlassian environment, including 5,000 rotated keys and 4 missed ones. This oversight in managing credentials and permissions created a vulnerability for attackers to exploit.
AWS - Exploiting misconfigured environment variables
A recent cyberattack targeting Amazon Web Services (AWS) exploited misconfigured environment variable files (.env files). These files commonly store sensitive information, such as access keys and API credentials. The attackers scanned over 110,000 domains, extracting over 90,000 unique credentials, including AWS IAM access keys.
Snowflake - Credential theft via malware
This breach primarily involved credentials obtained through infostealer malware on vulnerable servers or unprotected employee laptops. These credentials, often linked to service accounts lacking multi-factor authentication (MFA), were used to access Snowflake instances and exfiltrate large amounts of data. The threat actors demanded ransoms from breached organizations and, when unsuccessful, sold the data and credentials on dark web forums. This incident highlighted that Snowflake environments are rich in service accounts, which are not protected by MFA by default, increasing their vulnerability to exploits. It emphasizes the need for comprehensive inventory management and runtime anomaly detection capabilities for these accounts.
Hugging Face - Unauthorized access to tokens:
In mid-2024, Hugging Face's Spaces platform suffered a significant breach. Attackers gained unauthorized access to API tokens and secrets used by users to manage their AI applications and datasets. This incident underscores the critical importance of properly managing API tokens and secrets, particularly on platforms hosting sensitive AI models and data.
The next logical question is how organizations can mitigate these incidents…
Solution: NHI’s Lifecycle Management
Based on all my research, these are the foundational procedures for handling and solving the issue around NHIs. They are steps for organizations either staffing or looking to hire a vendor. As discussed, there hasn’t been a holistic solution that solves the problem. The way many vendors and enterprises are solving the problem involves a lifecycle for NHIs. It consists of several crucial steps that align with best practices in identity and access management (IAM). The most important of these steps are:
1. Visibility: Discovery and Inventory
The first critical step many organizations need is to identify all NHIs (e.g., service accounts, API keys, machine identities) in use across the organization, both on-prem and in cloud environments. Enterprises must then build and maintain a dynamic inventory of all NHIs, categorizing each by type (e.g., service accounts, tokens) and use case (e.g., cloud services, DevOps pipelines).
Organizations will leverage this to a) build a thorough registry and conduct an inventory to map out all NHIs, including their purposes, owners, and associated permissions. Document and then look at their risks. c) work across different stakeholders to understand this landscape. This will involve engineering, DevOps, identity, and cloud teams.
2. Provisioning, Assignment & Classification
This second component handles the creation and assignment of unique credentials to NHIs securely when they are first deployed. This ensures they are given the correct access rights from the beginning with appropriate privileges and governance. This includes defining their scope of access and ensuring correct classifications for ongoing monitoring. There are a few components to this process:
Classification and secure Provisioning: NHIs should be tagged by criticality, privilege level, and access type (e.g., privileged, sensitive data access, separation of duties), with metadata capturing ownership and the service or system they are tied to. After that, NHIs should be created through controlled, automated processes that align with security policies.
Role-Based Assignment: Each NHI must be assigned to specific roles, services, or systems, with clear definitions of what data or actions it can access (e.g., AWS Lambda functions or Azure service accounts).
Classification of Privileges: NHIs must be classified based on their access levels (privileged, sensitive data) and context (e.g., whether they are used for internal service-to-service communication or third-party integrations).
3. Posture management & monitoring
Posture management involves the continuous assessment of NHIs to ensure their security configurations align with the organization's policies and standards. Monitoring focuses on the ongoing evaluation of NHIs for anomalous or risky behavior, ensuring that any deviations from secure practices are detected in real time.
Security Posture Evaluation: Vendors must continuously evaluate each NHI for security weaknesses, such as excessive privileges, outdated credentials, or misconfigurations (e.g., API keys with overly broad access scopes).
Behavior Monitoring: Implementing monitoring tools that track the behavior of NHIs, ensuring that activities align with baseline patterns (e.g., an API key should not access unauthorized services or communicate with unknown endpoints). NHI vendors should leverage this baseline analysis to detect suspicious behavior that could indicate compromise (e.g., an API key being used at unusual hours or from unauthorized locations).
There is another major component here that involves adapting Just-In-Time access to NHIs. This helps to reduce standing privileges by granting access only when necessary. This ensures NHIs only have access when needed, minimizing risks and aligning with zero-trust security principles.
4. NHI Detection and response
This phase focuses on detecting compromised or anomalous NHIs in real time and responding to potential incidents quickly to minimize damage. It involves setting up detection mechanisms and defining incident response processes tailored to non-human identities.
NHI vendors should establish automated alerting mechanisms that notify security teams of potential NHI compromises or policy violations. They should also establish predefined incident response playbooks specifically for NHI-related threats to ensure swift action.
5. Rotation and Secrets Vaulting
A key way to secure NHIs is by ensuring that all secrets and vaults within an enterprise are periodically updated or credentials are revoked at appropriate times to reduce the risk of credential leakage. This involves managing the secure storage, rotation, and lifecycle of NHI secrets, such as API keys, tokens, certificates, and passwords, to minimize the risk of unauthorized access.
Secrets Rotation: Every NHI vendor must ensure they can implement automated policies for regular rotation of NHI secrets (e.g., API keys, tokens) to limit the lifespan of credentials and reduce the window of opportunity for attackers. Best practices include rotating secrets every 30, 60, or 90 days.
Secure Vaulting: Companies should store all NHI secrets in a centralized, encrypted secrets management solution or vault. Ensure access to the vault is tightly controlled and monitored, with role-based permissions to prevent unauthorized access. Secrets management tools like HashiCorp Vault or AWS Secrets Manager can assist with this.
Audit and Tracking: Maintain detailed audit logs of all access, changes, and rotations of NHI secrets. This ensures accountability and provides an audit trail for compliance and security investigations
Failure to rotate credentials in a timely manner increases the chance of compromised credentials being used maliciously.
6. Deprovisioning and Decommission
The final stage involves the secure deprovisioning and decommissioning of NHIs that are no longer needed, ensuring they do not pose an ongoing security risk. Deprovisioning and decommissioning of Non-Human Identities (NHIs) is crucial for maintaining strong NHI security. This process involves several key steps to ensure that inactive or unnecessary NHIs are safely removed from the system, preventing potential security risks.
Automated workflows play a vital role in this process. These workflows identify and decommission NHIs that are no longer active or necessary, removing all associated credentials, privileges, and access rights. To complement this, organizations should establish expiration policies that set specific dates for NHIs and their credentials, ensuring that inactive or outdated identities are automatically decommissioned, minimizing the risk of stale NHIs being exploited by attackers.
Regular verification and validation are essential components of the deprovisioning process. This involves checking that deprovisioned NHIs have been fully removed from all systems, including cloud platforms, on-premise environments, and third-party integrations. Periodic audits should be conducted to ensure no "zombie" identities persist in the system. This thorough approach to deprovisioning is necessary because NHIs that are not properly removed can become dormant security risks, especially if their credentials remain valid.
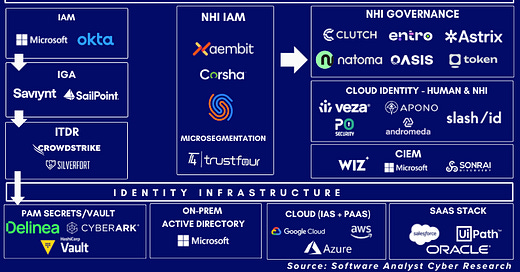
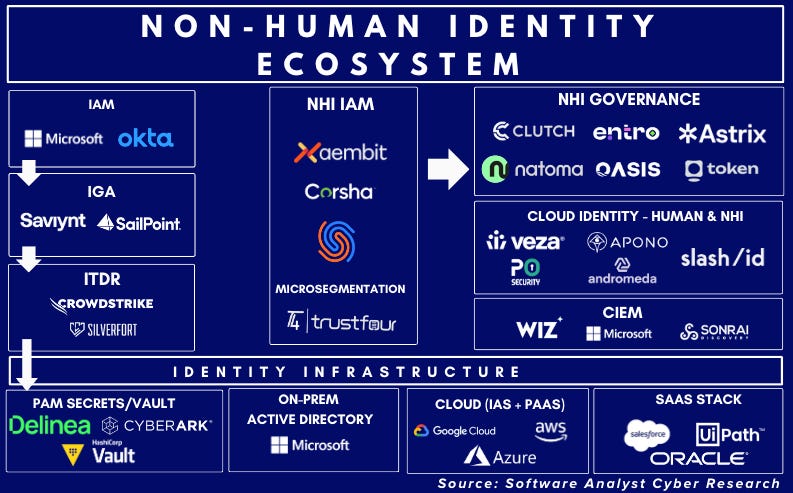
NHI Vendor Landscape & Adjacent Categories
Today, there are several types of vendors across the Non-Human Identity (NHI) ecosystem:
NHI Vendors
Authentication vendors
Authorization and governance vendors
NHI Authentication Platforms
Aembit: The Okta for Non-Human Identities
Aembit is a Non-Human Identity (NHI) and access management platform designed to handle secure machine-to-machine interactions across multi-cloud, SaaS, and on-premise environments. Often referred to as “Okta for Non-Human Identities”, Aembit streamlines the enforcement of machine identities and their access rights, ensuring secure and automated access without requiring manual intervention from developers or IT teams.
Aembit cryptographically verifies the identities of workloads using “trust providers,” leveraging secretless identity tokens from platforms like AWS, GCP, or on-prem systems. Further, enforcing policies set by the administrator, Aembit grants access and then injects a short-lived credential directly into the access request. This shift from long-lived credentials to dynamic, short-term tokens with just-in-time delivery enables organizations to automate credential management, and eliminate the need for workload NHIs to store credentials. This significantly enhances security and operational efficiency. Aembit’s conditional access policies ensure that workloads access resources only under predefined circumstances, such as meeting compliance & security posture requirements defined by, for example, Crowdstrike or Wiz.
Differences between Aembit vs other NHI Vendors
Authentication vs Authorization Layer
I’ve observed a misconception around Aembit. They are different in that they broker access based on real-time policy enforcement and conditional access. They have a secretless authentication methodology for short-lived access credentials. Meanwhile, other vendors discussed are focused on NHI discovery, visibility and lifecycle management and remediation. I provide a detailed discussion in the next part of this report.
Use Cases
Aembit’s solutions are used in securing sensitive databases (e.g., Snowflake), CI/CD systems, AI agents and LLMs, and enabling zero-trust access for machine workloads. Its approach eliminates secrets in CI/CD pipelines and prevents credential reuse, addressing a critical challenge for organizations managing multi-cloud infrastructures. It also prevents humans from touching and managing privileged machine credentials through no-code auth. The platform’s flexibility allows companies to focus on specific pain points, whether that’s sensitive data protection, secure CI/CD processes, or multi-cloud federation.
Aembit’s Competitive Advantage
Aembit’s approach combines identity federation with policy-based access control, securing the rapidly expanding web of non-human identities (e.g., service accounts, API keys, and microservices). This platform offers clear advantages over traditional cloud IAM systems and secrets managers like HashiCorp Vault, which often lack the ability to manage conditional access and centralized policies for machine-to-machine interactions.
Federating Identities Across Environments: Aembit can federate identities across any infrastructure—AWS, GCP, Azure, on-premise, or SaaS applications—providing real-time, cryptographically verified identities. This "secret-less" access model reduces the security risks associated with long-lived credentials.
Automated Credential Management: Aembit’s automation capabilities streamline the credential management process, removing manual handling and mitigating human error. This helps companies eliminate the complexities of credential injection, significantly improving security posture.
Developer-Friendly, No-Code Integration: Aembit’s no-code implementation allows developers to continue their workflows without modifications, as the platform manages credentials and policies behind the scenes. This flexibility enables organizations to adopt Aembit without disrupting existing development processes, and use Aembit when organizations are running software from third party providers.
Seamless Integration with Existing Vaults: Aembit integrates with legacy systems like CyberArk and provides the ability to mint on-demand, short-term tokens. This capability ensures smooth policy enforcement without forcing companies to rip and replace their existing infrastructure.
Discussion on some approaches used and how Aembit differs
It is popularly known that some companies might use some form of Cloud IAM and secrets managers (e.g., HashiCorp Vault), but they have their limitations in managing modern, distributed infrastructures. These tools are often designed to manage static credentials within specific environments (such as AWS or GCP), but they struggle to handle the cross-environment communication required in multi-cloud or hybrid infrastructures. For instance, Cloud IAM systems are inward-looking, meaning they work well within their native environments but create gaps when trying to connect to external systems, SaaS applications, or other cloud providers. Similarly, secrets managers like CyberArk and HashiCorp are built to store secrets securely but lack the conditional access, real-time policy enforcement, and identity federation required for non-human identity (NHI) security in distributed environments.
Aembit addresses these shortcomings by offering automation and federation across multi-cloud distributed environments. Unlike secrets managers, Aembit can retrieve credentials from multiple environments while also acting as a policy engine to ensure that every access request is validated in real-time using conditional access checks. As discussed, Aembit emphasizes a secret-less architecture, where short-lived tokens replace long-lived credentials, reducing the risk of breaches. It’s important to note that Aembit integrates smoothly with existing vaults like CyberArk and HashiCorp, allowing companies to retain their infrastructure while benefiting from Aembit’s advanced policy control and automation features. This allows organizations to transition to a secret-less model without ripping out their current systems.
Based on my discussions, Aembit’s vision is to lead the shift towards secret-less architectures, where credentials are dynamically minted on demand, reducing the need for legacy vaults. As more organizations embrace multi-cloud and hybrid infrastructures, Aembit can solve the NHI security access management, offering a unified solution for companies struggling with both legacy systems and cloud-native deployments.
There are other competitors in the market, such as Corsha and Trustfour.
Corsha’s platform is centred around machine identity verification and API security. They aim to be an identity provider and authenticator of machine identities.
On the other hand, Trustfour is a workload-centric and am NHI zero-trust solution that focuses on securing both internal and external communication between workloads, APIs and bots.
NHI Authorization Platforms
There are many other vendors within NHI, but this section delves into discussing the vendors alphabetically:
Astrix security
Clutch security
Entro security
Natoma security
Slash ID
There are many others in the market who deserve a mention that are worth diving into, such as Token and Oasis. However, this report sheds a spotlight on a number of key vendors.
Astrix Security
Astrix was one of the earliest companies offering an NHI security platform. They can be credited as the first to coin the term “Non-Human Identity,” going back to the RSA Innovation Sandbox competition in May 2023. Coining the term “NHI” came after a number of positioning iterations, such as 3rd-party integration access controls and App-to-App security (not to be confused with SaaS-to-SaaS) as Astrix began its journey all the way back in 2021 with a focus on core environments spanning across IaaS, PaaS and SaaS.
The company quickly recognized the importance of behavior anomaly detection for the usage of these identities. One of the core competencies of Astrix is having years of training on real world API traffic to detect anomalies in near-real time. The same engine that actually detected a 0-day vulnerability in Google GCP back in 2022, more on that later.
The platform’s key capabilities include:
NHI Discovery and Inventory: Identifying and cataloging NHIs across various environments like AWS, Github, Slack, and Active Directory.
Posture Management: Ensuring NHIs adhere to least-privilege principles and are properly configured to minimize attack surfaces.
Lifecycle Management: Orchestrating the lifecycle of NHIs, including secret rotation, NHI retirement, and reassignment.
Anomaly Detection and Threat Remediation: Analyzing NHIs for unusual behavior or configuration anomalies and remediating issues directly in workflows
A few notable elements of their platform’s capabilities include:
Behavioural analysis: They have an AI-based threat engine that detects abuse of NHIs based on anomaly indicators such as unusual IP, user agent, and activity.
Vendor supply chain attacks: They map every associated NHI, allowing a company to see everything an NHI is connected to in their tech stack and what it’s used for, so in the case of an incident involving a third party, a company can either rotate or remove an NHI quickly. Since they comply with SEC disclosure guidelines, they can expedite incident response when a company’s external vendor is compromised.
Policy deviations: They prevent NHI abuse by enforcing organizational policies on NHIs. They use existing tools to mitigate policy deviations such as access from forbidden geos, number of API calls and more. Beyond Astrix’ strong NHITDR play, their aim is to secure these identities across different environments, particularly SaaS, on-prem and cloud-native environments, which form the backbone of most modern enterprises. Astrix’s platform focuses on managing the lifecycle and security posture of non-human identities.
A key component of Astrix’s solution is its risk engine. This engine assesses the risk level of every NHI by analyzing its permissions, potential for compromise, and how it interacts with external suppliers or internal systems. This allows Astrix’s customers to prioritize the most critical threats and take action on high-risk NHIs. Customers can use Astrix’s remediation workflows to fix issues such as over-permissioned accounts or compromised secrets.
The company has a broad platform, but its strengths relative to competitors lies with its ability to detect cross-environment threats, built-in remediation engine and real-time threat detection . While Astrix is primarily cloud-native, the company is actively developing capabilities to manage NHIs within on-prem environments. Key on-prem focus areas include Active Directory service accounts and on-prem databases, as well as SaaS tools deployed on-prem, such as GitHub Enterprise. Astrix is applying the lessons learned from cloud environments to ensure that on-prem NHIs are managed with the same level of sophistication.
Astrix Security manages the human-user lifecycle and its intersection with non-human identities (NHIs) by providing a seamless approach of tying human users to the NHIs they create and manage. This critical feature ensures that each NHI, such as service accounts or API keys, is associated with an accountable owner, allowing organizations to track and manage these identities throughout their lifecycle. For instance, when a human user is off-boarded, Astrix's platform ensures that any associated NHIs are also revoked or retired, preventing security gaps caused by lingering, unmanaged identities. Additionally, during access reviews, the platform helps ensure that both human-user access and the permissions granted to NHIs are evaluated together, reducing the risk of orphaned or overly privileged NHIs. This owner assignment mechanism offers an additional layer of security, enabling organizations to quickly identify and remediate issues by knowing exactly which user is responsible for each NHI. This capability is foundational to Astrix's strategy of providing comprehensive lifecycle management and ensuring security across all identity types.
Another strength of the Astrix platform is the Astrix research group, which specializes in NHI behaviors, risks, and vulnerabilities. These insights enrich the platform continuously. The Astrix research group is famous for the discovery of the Ghost token zero-day in GCP, which was actually patched by Google.
Astrix provides a unified platform that addresses NHIs by offering extensive coverage across multiple environments, including cloud-native, and SaaS. This approach is vital for enterprises with complex, hybrid infrastructures that require consistent NHI visibility and control across different layers of their stack. Astrix’s ability to monitor and secure AWS, CICD tools, SaaS platforms, and on-prem solutions like Active Directory gives it a significant advantage, providing customers with a holistic view of their NHI ecosystem.
At the core of Astrix’s offering is its powerful risk engine, specifically designed to assess the risk levels of NHIs. The risk engine evaluates the permissions, configurations, and usage of each NHI. It assigns risk scores based on these factors, helping organizations prioritize threats and focus remediation efforts on the most critical NHIs. The company’s deep understanding of how NHIs function within SaaS platforms allows it to offer more targeted and effective security solutions for enterprises that rely heavily on tools like Slack, AWS, and other SaaS applications. Astrix partnered with the Cloud Security Alliance to survey over 800+ security leaders, the report unveils the state of Non-Human Identity Security – from top challenges and risks to tooling, programs, and budget allocation - The State of Non-Human Identity Security. I highly recommend checking it out.
Clutch
Clutch Security is a non-human identity vendor that was launched early in 2024 and came out of stealth in July. Clutch is approaching this problem from a unique angle based on what is called Identity Lineage and using a zero-trust approach to solve this problem.
The Clutch Lineage is a capability that provides a comprehensive framework for understanding the full lifecycle and interactions of non-human identities—such as service accounts, API keys, tokens, and secrets—within an organization's infrastructure.
The Identity Lineage is built around a model which maps out the ecosystem in which each NHI operates. Clutch identifies five key elements that encompass the lifecycle of NHIs:
Origin (where it was created): This is the source of the identity, such as a system that generates API keys or secrets.
People (who owns, created or used it): These are the human actors within the organization who create or have access to these non-human identities. By linking NHIs to specific individuals, Clutch provides accountability and a clear attribution trail
Storage (where it resides): NHIs are often stored in various locations, such as secret managers (e.g., AWS Secrets Manager, Azure Key Vault), password managers (e.g., 1Password, LastPass) or hard coded in application code. Clutch tracks where these identities are stored, providing visibility into whether those storage mechanisms are secure.
Consumers (which systems are using it): These are systems that programmatically use the NHIs to perform operations. By identifying which systems consume these identities, Clutch helps organizations monitor and control which processes or applications have access to sensitive information.
Resources (what those identities access): These are the assets or data that NHIs have access to. By mapping out what resources each NHI can interact with, Clutch ensures that organizations can see if their identities are over-privileged or vulnerable.
Clutch does capture all the areas of NHIs - visibility, governance over lifecycle management, posture and risk management, and detection and response. By mapping out the complete lifecycle of each NHI, Clutch gives companies not just visibility into where their identities are, but a full contextual understanding of how these identities interact with their environments. At its core, Clutch’s product addresses the problem of compromised identities in real-time. Through an intuitive platform that correlates data from a wide range of integrations, Clutch provides security teams with a visual and comprehensive understanding of their NHIs' ecosystem. This isn't just about finding risks; it’s about contextualizing those risks within the organization's infrastructure.
Contextual Risk Mapping
Clutch’s Identity Lineage model is not just about mapping relationships; it layers risk into the model. Every risk, whether it's related to an overprivileged NHI, an NHI that has been leaked or compromised, or an NHI being used inappropriately by a consumer, is contextualized within this lineage. This contextualization of risk gives security teams clear visibility into how to prioritize threats. For example, if an API key is stored insecurely in a public repository but is only used by a low-risk internal system, the risk might be lower than a key that is accessible from an external system. By using the lineage model, Clutch can help organizations make more informed decisions about where to focus their security efforts.
Clutch’s competitive advantage lies in the extensive integration capabilities and automation features built into its platform. With over 30 integrations across various systems (and growing), Clutch ensures that it can correlate data from diverse environments, including cloud platforms, secret management systems, and CI/CD pipelines. This wide-ranging integration ensures that Clutch's lineage model remains accurate and comprehensive across an organization’s entire tech stack.
Eliminating Secret Rotation, Layering On A Zero-Trust Approach
One of the unique aspects of Clutch is its elimination of secret rotation in favour of ephemeral, secretless identities. These credentials expire automatically, reducing the attack surface by minimizing exposure. This shift from traditional methods ensures that compromised secrets are less exploitable, especially in cloud-native environments where static secrets are vulnerable to rapid exploitation. Clutch proactively guides organizations toward adopting these modern, ephemeral alternatives, providing a more secure and scalable solution.
Clutch adopts a phased approach to implementing ephemeral and secretless identities. It starts with Virtual Shielding, allowing teams to monitor and detect anomalies in NHIs without immediate disruptions. As organizations advance, they can fortify these identities by adding stronger protections, gradually minimizing the need for R&D or IT involvement. In the final phase, Clutch enables the transition to ephemeral identities, where credentials are automatically short-lived and self-expiring. This progression ensures a seamless move from traditional credential management to a fully secure, zero-trust model with minimal operational impact.
In general, Clutch identity lineage and zero-trust model sets it apart by providing an integrated and holistic view of the entire NHI ecosystem. Its combination of contextual risk mapping and a move towards secretless, ephemeral identities places it ahead of competitors in addressing modern NHI security challenges. Clutch offers a next-generation solution that adapts to the growing needs of organizations heavily reliant on non-human identities, making it a formidable player in the market.
Entro Security
Entro Security is a platform focused on securing and managing the lifecycle of non-human identities (NHI), such as service accounts, API keys, and secrets, which are often created, permissioned, and used by developers and DevOps teams without proper security oversight. These identities can be scattered across different environments (e.g., Kubernetes, GitHub, Slack, Vaults, etc.), and are often poorly managed, leaving organizations vulnerable to security breaches.
Entro Security started with a focus on secrets and then NHI security, aiming to address the challenges of managing and securing sensitive tokens, API keys, and other programmatic credentials used by applications and automated systems. Entro was the first company to launch a platform (using a wayback machine to 2022), but primarily focused on providing security solutions that revolved around securing machine secrets and improving governance over these credentials.
Today, Entro provides end-to-end lifecycle management of NHIs and secrets, from discovery and classification to the decommissioning of unused or unnecessary identities. This holistic approach allows companies to identify and manage their non-human identities more efficiently. Some of Entro’s competitive advantage include:
Identifying Exposure Locations & Enrichment
Entro excels at identifying and discovering all NHIs and secrets, in their creation locations, storage locations(Vaults), and /or exposure locations where sensitive tokens, secrets, or credentials may be at risk. This includes scanning across a wide range of environments such as: Jira tickets, SharePoint pages, or Kubernetes clusters, GitHub repositories, and Vaults.
Entro detects exposure locations of NHIs, which are critical for identifying potential vulnerabilities. This capability is unique in comparison to competitors who often focus only on discovery without providing insights into where identities were created, stored, or exposed.
The enrichment process adds critical context to these NHIs and secrets by classifying and enriching them with business context, effectively creating a lineage map of which application is using what NHI to access what resource and more context that enables the security team to understand the blast radius of each NHI and secret. Entro's detailed insights into the lifecycle of tokens—such as distinguishing between idle and active tokens—sets it apart from competitors. Additionally, Entro can detect sensitive NHIs or secrets improperly stored across multiple platforms, cloud, or on-prem environments, making it particularly effective in managing the sprawl of NHIs across hybrid systems. Entro adds metadata and context to each identity, such as permissions, creation details, and usage patterns, making it easier for organizations to assess risks and take action. This detailed classification process helps organizations gain better visibility and control over their NHIs
NHI Role Identifier
A major strength of Entro is its ability to identify who created a token and trace its storage locations, vaults, and secrets. This role identifier functionality helps organizations quickly pinpoint who is responsible for critical non-human identities, which can streamline the management and accountability of NHIs. By tracking not only the token's lifecycle but also its creators and users, Entro enables better visibility and security, allowing security teams to identify and address potential risks more efficiently.
NHIDR (Non-Human Identity Detection & Response)
Entro’s threat detection and response capabilities go beyond simple monitoring. The platform can identify anomalous behaviours, such as:
Unauthorized access attempts: For example, if someone from China is attempting to download secrets from a vault, Entro can immediately flag the activity and initiate an automated response.
Decommissioned accounts: It identifies accounts that should no longer have access and automatically prevents their tokens from being used.
This proactive approach ensures that security incidents are addressed in real-time, reducing potential breaches before they occur. Entro also automates the remediation process by rotating or revoking compromised tokens, thus minimizing the manual effort needed to secure environments.
Natoma: Breadth and Depth for NHI security
Natoma came out of stealth in July 30, 2024. Natoma is a comprehensive NHI platform for securing and controlling non-human identities. They provide visibility across cloud, SaaS and on-prem. They manage the lifecycle of NHIs as discussed earlier in this report. The founders have extensive experience within the Identity ecosystem and want to use their knowledge to solve the NHI problem.
Natoma wants to go beyond breadth of visibility, but go deeper into depth of these NHIs across vaults. Natoma provides more than just a surface-level view of NHIs. They emphasize giving deep contextual graph to understand the relationship between all your NHIs, including:
Who owns the NHI: Identifying the human owner or team responsible for each NHI.
Where the NHI is being used: Mapping NHIs to their usage within cloud workloads to ensure that lifecycle actions (e.g., rotation, decommissioning) don’t disrupt critical services.
What the NHI is capable of: ensuring NHIs follow the principle of least privileged access and are only granted permissions that they need (and use)
Natoma’s approach to Non-Human Identity (NHI) management follows a lifecycle process that begins with gaining full visibility and inventory of all NHIs across cloud environments. Next, they map dependencies to understand where NHIs are used, ensuring any lifecycle changes don’t disrupt services. They then attribute ownership of NHIs to responsible individuals or teams, dynamically updating this as roles change. Natoma also automates secret rotation, ensuring credentials are regularly updated and secure, while orchestrating provisioning for new NHIs with the right permissions. They handle offboarding and deprovisioning by safely deactivating unused NHIs and ensure smooth ownership transitions when users leave or change roles. For NHIs that need scope adjustments, Natoma facilitates change of permissions based on actual usage. All of this is done through non-intrusive collection, integrating with existing security systems to minimize friction.
Non-invasive approach
A highlight from my discussions is Natoma’s non-Intrusive approach. Natoma collects data from various systems to build a detailed picture of NHI activity and automatically inventory all NHIs present in the cloud environment. This includes service accounts, API keys, OAuth tokens, and other non-human credentials. This approach allows them to provide insights without requiring deep integration into each system, making their solution relatively low friction for customers.
Natoma ingests and fingerprints data that includes actions taken by NHIs, such as API calls, service account activity, and interactions with cloud workloads. This data is ideal for understanding NHIs because they capture detailed information about who (or what) is accessing specific resources and when the access occurred. For example:
Where an NHI is being used (e.g., within which cloud service or workload).
What actions the NHI is performing (e.g., accessing sensitive databases, making API calls).
When and how frequently the NHI is active (e.g., identifying stale NHIs that have not been used recently).
What actions were performed (e.g., API usage, file modifications).
Which permissions were invoked or used
Natoma can identify anomalous behaviors associated with NHIs. For instance, if a service account that is typically used during office hours suddenly starts making API calls at 3 AM, this could indicate a compromised identity. They give Natoma the ability to see both real-time and historical data, which is critical for lifecycle management including the meta-data for attributing ownership and accountability.
Downstream Dependencies
One of the most challenging aspects of NHI governance is understanding where an identity is used across an organization’s infrastructure. Natoma maps these dependencies by tracking which systems interact with which NHIs. This information is crucial when making lifecycle decisions, such as rotating credentials or deprovisioning an account, as it prevents accidentally breaking workflows or services. It can also identify abuse of non-human identity such as when a new, unexpected client or system attempts to use an NHI, or there is interactive activity associated with an account reserved for programmatic use.
Natoma’s analysis is a key capability for managing NHIs because it allows for deep visibility, comprehensive lifecycle management, and proactive security measures. Natoma’s approach to Non-Human Identity (NHI) management is distinguished by its ability to provide both breadth and depth in managing the lifecycle of NHIs, across a wide range of systems, such as SaaS, PaaS, on-prem infrastructure, and more. Natoma is focused on scaling their solution to support very large enterprises, including those in highly regulated industries like finance and critical infrastructure (e.g., oil and gas).
SlashID
SlashID offers a comprehensive view of identities, enabling informed decisions on identity hygiene, attack detection, and response. Contrary to other vendors, SlashID extends to human identities and credentials across both managed and unmanaged environments. SlashID’s approach to managing non-human identities (NHI) is built on three pillars:
Visibility: They cover cloud providers and SaaS applications. They provide visibility for Kubernetes clusters and network traffic through a deployable agent (similar to a sidecar model).
Detection: They provide both posture and anomaly detection. They can identify misconfigurations (eg weak MFA), but also extend that by performing behavioral analysis to detect compromised identities.
Remediation: They offer both manual and automated actions like suspending identities, revoking permissions, and deleting or rotating credentials. They equally integrate with workflow tools (e.g., Jira) to automate responses.
SlashID ingests identity and log data through agentless connectors for managed environments, and sidecars are used specifically for unmanaged environments like Kubernetes. This data builds a cross-provider “trust tree” for each identity, detailing permissions, roles, privileges, and historical activity. The trust tree simplifies lifecycle management and enforces least-privilege policies by identifying unused permissions and tracing NHI ownership and usage.
The detection engine identifies misconfigurations (e.g., unused permissions) and active threats. It includes an attack graph that aids SOC investigations and assesses the blast radius of breaches or misconfigurations. A key strength is cross-platform, cross-identity threat detection, such as lateral movement between human and non-human identities.
SlashID offers both manual and automated remediation, allowing organizations to enforce least-privilege policies and speed up incident response. The platform can quarantine identities, revoke sessions, integrate with ticketing and SOAR systems, and rotate and tokenize credentials as needed. I see SlashID as a solid platform that provides enterprises with a robust solution that intersects several key identity categories such as NHI, ITDR and identity attack surface management (IASM).
Oasis
Oasis Security is a management and security solution for non-human identities (NHIs). It similarly addresses NHI challenges in visibility, security, and governance of NHIs across hybrid cloud environments.
Oasis has a three-phase approach (outlined here) built around their posture and remediation intelligence (PRI) engine that continuously analyzes an enterprise environment to discover all NHIs (new and legacy), create a comprehensive inventory of all NHIs providing rich contextual information on who owns it, consumes it, what resources it grants access to and how privileged it is then subsequently generates tailored remediation plans that can be executed semi-automatically or fully automated. The PRI engine also has a big emphasis on identifying any security posture vulnerabilities leveraging context from its integration with other identity solutions and then classifying them by severity.
Additionally, Oasis leverages advanced AI-based analytics to automatically discover NHIs, assess their risk, and identify their owners throughout the environment. With its integrated, policy-driven governance capabilities, it orchestrates the entire lifecycle of NHIs, including remediation and compliance management, all within a single solution.
Cloud Identity Governance Providers: Human & Non-Human Context
These providers already have robust Identity next-gen governance and Cloud infrastructure entitlements management (CIEM) solutions. I had the opportunity to do a product demo with several of the adjacent cloud identity and governance solutions.
Veza
Veza has an identity graph that visually maps out the relationships between identities (both human and non-human) and the resources they access. They have good capabilities around NHI discovery, key visibility/rotation, owner certifications, and the NHI lifecycle, with strong strengths in Access requests and CIEM capabilities.
Since through their IGA solution, they already have access to the human users, Veza’s platform is able to emphasize automated discovery, allowing customers to locate NHIs, especially those that might be hidden behind reused human identity accounts or legacy systems. Veza has a single pane of glass that makes it easy for the user to assign human owners to NHIs. This ownership is crucial because it ensures that someone is responsible for monitoring and managing the lifecycle of NHIs. Without human ownership, tasks like key rotation or deprovisioning are prone to errors and oversight.
P0 Security
P0 Security is a vendor in the identity security space that offers a universal cloud-access governance platform. Their solution focuses on enhancing cloud security across all identities, both human and machine while integrating into developer workflows. P0 Security can provide a thorough inventory and visibility of all non-human identities - specifically within cloud environments. They particularly focus on cloud environments crucial for developers, such as AWS, GCP, Snowflake, and Kubernetes, since they believe a large volume of NHIs reside within the core infrastructure.
Andromeda
Similarly, Andromeda has a solution that can easily map between human and non-human identity flows. They have a risk and context-based identity security platform with the vision of aggregating - CIEM dynamics least-privilege, Just-In-Time Privilege management (PAM), Governance & Compliance using IGA and utilizing a risk-based ITDR to help detect threats.
CIEM Providers
Wiz
While Wiz isn’t a pureplay NHI vendors
Wiz’s approach to Cloud Infrastructure Entitlement Management (CIEM), particularly for Non-Human Identities (NHI), is designed to provide deep visibility and robust governance across cloud environments. The core of their solution revolves around the Non-Human Identities Dashboard, which is part of Wiz's larger CIEM offering. This dashboard helps organizations track and manage the growing number of non-human identities, such as service accounts, serverless functions, and machine identities, which are essential in cloud environments but often pose significant security risks if not properly managed.
Apono
Apono is another vendor that provides security and engineering teams with a modern access management platform, quickly helping them get privileged accounts in check and making it easy to deploy advanced controls like granular just-in-time access, context based approvals, anomaly detection and AI-based least privilege recommendations. With the growth of cloud adoption, permissions management and access control have become huge problems for organizations, and I expect this theme to evolve over the next few months.
The Future: How NHIs Could Evolve / Things To Watch
The determining factor for success
A key factor for success will be the breadth of integrations with a company's SaaS, IaaS, and on-premises environments. Here's why:
Effective NHI lifecycle management is crucial, but it's complicated by the need for visibility into where NHIs are used. For example, if an NHI is tied to a critical service, rotating or offboarding that NHI without full visibility into its dependencies can cause system failures. While visibility is the starting point, more mature customers seek deeper governance features. They want solutions that can help with orchestration of NHI management—for instance, automating secrets rotation across various environments while ensuring that dependencies remain intact.
The ability to closely integrate with highly entrenched enterprise products like Access Management/IDPs, IGA, and PAM solutions is vital. These three products have strong staying power within the enterprise. This integration ultimately allows a company to gain full context into both human and non-human identities across their entire enterprise stack.
Feature or Platform Convergence Debate
Many CISOs recognize this as a significant security blind spot, and some are allocating budgets to address this issue. For some organizations, however, it remains a priority for 2025, as current budgets are focused on more immediate security concerns. Through my extensive discussion and readings, it is very clear that this problem needs to be addressed distinctly before it becomes part of a larger platform.
Integration with Larger Platforms through acquisitions or standalone
There will be winners in the NHI space, and some will do well, while some will be acquired. Some vendors may focus solely on visibility without offering actionable remediation, which could limit their long-term appeal. Customers increasingly demand platforms that not only detect problems but also offer solutions. Therefore, many of these vendors must expand their appeal across other areas of the stack.
DevOps teams might resist implementing disruptive NHI security solutions because they require changing existing scripts, processes, and tools, even if the solution is ultimately more secure. Some vendors offer less intrusive solutions, providing visibility without disrupting workflows, but these may only offer short-term benefits as a “feature” rather than a long-term comprehensive security solution.
Identity Governance & Access (IGA)
IGAs can integrate NHI discovery tools that scan cloud environments, SaaS applications, and on-prem systems for NHIs such as service accounts and tokens. These tools should be able to identify roles and permissions associated with each NHI, similar to how human identities are managed.
Once integrated into IGA, these identities need to be classified by risk levels, similar to how IGA systems manage human roles (e.g., admin, user, guest). This classification allows for more targeted governance policies.
Governance workflows can be adapted to include NHIs, such as scheduling access reviews for all NHIs in the same way that human identity access reviews are conducted, ensuring that permissions are still relevant and not over-privileged.
Privileged Access Management (PAM)
PAM systems can extend their capabilities to manage the credentials of NHIs such as API keys and service accounts by using vaulting solutions to store and rotate these credentials securely. PAM systems/vendors could acquire NHI vendors, as PAM tools already manage human and privileged access. This synergy could provide a complete solution for both human and non-human identities, especially for vendors lacking strong SaaS and cloud footholds.
PAM systems can extend their vaulting solutions to securely store and rotate NHI credentials. By providing a unified view of both human and non-human identities, these platforms enable organizations to keep track of every account that interacts with sensitive systems.
CNAPP / CIEM Providers
Wiz has a CIEM solution for monitoring and managing entitlements across cloud environments. For NHI security to work effectively, cloud security and identity security systems must collaborate seamlessly. Both are responsible for managing access and protecting sensitive resources, and NHIs blur the line between these two domains. A potential NHI solution with Wiz would leverage its strong cloud-native security capabilities, particularly in the CNAPP space, to ensure that non-human identities (NHIs)—like API keys, service accounts, and bots—are governed, monitored, and secured in real-time across cloud environments. Wiz could automatically detect NHIs across cloud infrastructures, including multi-cloud and hybrid environments, identifying all instances where service accounts, API keys, or machine identities have access to cloud resources. Currently, similar solutions are being developed by Andromeda, Veza, and P0 security.
Need for specialist NHI-focused programs and products.
To conclude, based on the current fragmented ecosystem of the identity ecosystem where no one solution solves the problem, it is clear that the industry requires a comprehensive solution that solves the problem. Recently the NHI Mgmt Group did a big industry survey involving close to 330 security practitioners on whether non-human identity products and human identity products should be kept separate or converge. Whilst the result was close, 55% to 45% in favor of keeping non-human identity products separate from human identity products, the reality is, some of the folks who voted for converge, want this to be an ideal end-state view, but clearly see there is a valid case for keeping the focus on NHI risks separate for now.
The challenges and approaches to addressing non-human identity risks vs human identity risks are very different e.g. addressing hardcoded passwords in source-code, require discovery through scanning tools, and then remediation requires shift-left DevSecOps CI/CD processes integrated into a secrets vault etc.
Whilst there may be overlapping identity lifecycle processes for non-human and human identities, there is a clear need to manage NHI identity risk programs separately from human identity risk programs and specialized NHI products that are more vertically focused on discovering and managing NHI risks.
Longer term, as the industry moves towards a zero-trust model and we move away from static secrets to more of a JIT model, then we may see more convergence, as it then becomes a more generic problem of identity management and security.
******
Thank you for reading.
Thank you to the software analyst's partners, such as Astrix, Entro, Natoma, Clutch, SlashID and Aembit, for helping to bring this research project together.
Thank you to Lalit Choda for sharing feedback and adding commentary to the report. Lalit is the founder of the NHI Mgmt Group. Lalit has a group, NHI Mgmt LinkedIn Group, that provides the latest news and developments around NHIs. He equally has the NHI Mgmt Group Portal, a knowledge hub on NHIs as well as details for supporting organizations who need to manage NHI risks.
***
Please share your feedback and thoughts by replying back to this email on the market.

















Very comprehensive. Excellent work on uncharted technology to many.