Public Cybersecurity Market Review & Commentary for H1 2024
Important updates for Crowdstrike, Palo Alto Networks, Zscaler, Okta, Datadog and Cloudflare.
Actionable Summary:
Happy Fourth of July to my American friends! At the beginning of the year, I made some predictions (Cybersecurity in 2024 from CISOs) for the cybersecurity industry. As the first half of the year just wrapped up, this is the perfect time to reflect on the state of the industry as leaders look to the back half of 2024. I published several reports on App Sec, Software supply chain, Identity, Next-Gen SIEMs and SOC Automation on some of the highest priority categories for cyber leaders.
There’s no better way to assess the industry's health than to examine the largest cybersecurity public companies. In this piece, I’ll summarize key technology and strategy updates for these companies as a barometer for what to expect in the next half of 2024. I hosted a cybersecurity webinar with top security leaders to explore some of the top themes that security leaders are focused on for the rest of 2024 - register here to view it. For today’s update, we’ll cover the latest developments across these companies:
Crowdstrike: Its path to $100B
Palo Alto Networks: The platformization dilemma
Zscaler: The new growth verticals
Okta: The growth re-acceleration
Cloudflare: Their expansion to edge AI & security
Datadog: Exploring their new cloud security businesses
I’ll summarize their quarterly results, discuss key takeaways from their recently concluded conferences and examine what is next for these businesses. In summary, the cybersecurity market is still growing decently. A key technological trend amongst all these companies is the battle for security data (next-gen SIEM—I have a report coming out on this topic next). Secondly, many of these companies are placing importance on building out their data security businesses as more companies set the foundations for deploying more AI/LLM applications. Much more below in the report.
🚨 NEW: Summer Cybersecurity Bootcamp for Founders & Investors (8-Spots Left)
I’m pleased to share that I have some open spots for my 4th Cybersecurity Bootcamp featuring cybersecurity leaders. (The deadline has been extended from June 30). This is a 3-week boot camp that goes in-depth and explains all the major areas of cybersecurity. Whether you’re a founder or cyber leader, the bootcamp will give you introductory cybersecurity frameworks to understand all the major industries - from cloud, endpoint, network security, data security and vulnerability management. The objective is to provide participants with a good grasp of cybersecurity using simple frameworks.
Learn & Network: This is an opportunity to engage with Cybersecurity leaders on how they view the industry and its future trends. We also provide networking opportunities with top-tier participants from investment and technology companies.
Meet top-tier leaders within different fields of cybersecurity: In the past, we’ve had CISOs like the leader of Google’s Deepmind, the CISO of Datadog, the $45B observability leader, and many others.
Full details here→ Cybersecurity Bootcamp. Whether you’re someone who wants to learn as a beginner or you’re an expert who wants to broaden your cyber knowledge (like I wrote in this deep-dive), this bootcamp is right for you.
**(NOTE: There are only five days left to register for the final 8 spots in this cohort).
Public Cybersecurity Companies Commentary
Crowdstrike: Its path to $100B
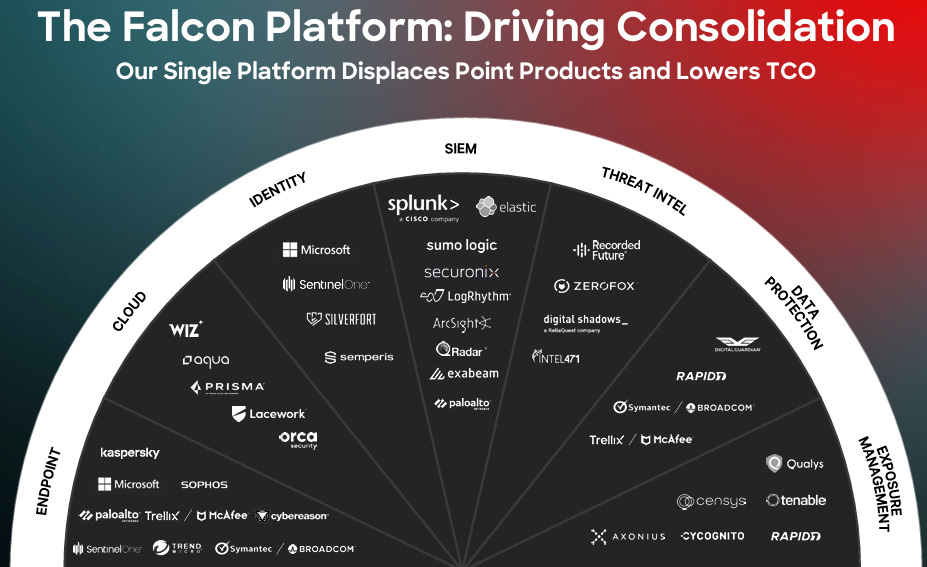
Crowdstrike is on its way to becoming the next $100B cybersecurity company in the next few months. The company has continued to execute brilliantly over the past two quarters, surpassing many expectations within the industry. Crowdstrike has successfully become a true multi-platform company as it has gone past being just an endpoint security company and has become a pivotal player across new markets, including cloud security, identity, and next-gen SIEM. These businesses have surpassed $100M in revenue, growing over 100% YoY. They continue to take significant market share from the major players within their core endpoint business.
Key discussion & highlights:
Financial update: In its recent quarter, CrowdStrike led the cybersecurity market with a 33% growth rate, generating $921M in its recent quarter, almost a billion-dollar quarter, which is impressive! They generated over $3.65B in ARR, and their net new ARR grew 22% YoY to $212M, surpassing Wall Street expectations. Their FCF reached a record $322M with a 35% FCF margin. Impressive for its scale.
Key growth areas for CrowdStrike - rapid adoption of emerging products: A big part of Crowdstrike’s recent success comes down to their rapid growth in their next-gen businesses. As of the recent quarter, Crowdstrike’s deals involving Cloud and Identity doubled YoY - let’s explore each:
Next-gen SIEM product: Crowdstrike already had its Falcon Next-Gen SIEM, powered by Logscale (through the acquisition of Humio), a business that has surpassed $100M ARR, the product wasn’t fully scalable to provide the sophistication required for a full-scale SIEM like Splunk. It was always a data management and log aggregation product. However, at RSAC, CrowdStrike announced its full next-gen SIEM announcement in May. The business is starting to gain some traction, but admittedly, it is still very early. Their competitive advantage over other SIEM vendors is that a high majority of data that flows into an SIEM comes from the endpoint and Crowdstrike in most cases, especially since their existing customer base already holds most of this data. It will be interesting to see if this leads to customers displacing Splunk for them. Crowdstrike’s fusion SOAR product is now used by 47% of CrowdStrike's top 5K customers. I will share more on this in a future report.
Cloud Security Wins: We know Crowdstrike is the 3rd largest player in cloud security (behind Palo Alto Networks & Wiz). The business has seen momentum with its AWS partnership, consolidating several cloud point products with Falcon Cloud Security, now deployed in 62 Fortune 100 organizations. However, it is still clear that Wiz is a major market leader in this category, but this business holds tremendous potential because of Crowdstrike’s strong agent solution and how it works in runtime environments. I will share more on this in a future report.
Charlotte AI: The company has a longer-term opportunity to grow its Charlotte AI business. This AI chatbot is designed to optimize the work of SOC analysts to manage incident response, triage, and automation use cases through integration with CrowdStrike’s workflows and Falcon Fusion. Charlotte has potential, but it will take quite some time to see a significant ramp.
GTM for SMBs & moving down-market: The next big growth area is selling most of their solutions in the lower segment of the market since Crowdstrike’s early success has been predicated around selling top-down. One of their key moves here was hiring Dan Bernard from SentinelOne and striking key partnerships with Mandiant and AWS, and federal wins. CrowdStrike continues to invest in its ability to attack the still significant opportunity within the small and medium business (SMB) segment, where organizations remain tied to legacy AV and other outdated approaches to security. How they execute her will be critical for their next phase of growth.
Adoption of Multi-Module: Crowdstrike is seeing more platform traction as customers with deals with 8 or more modules grew 95% YoY - with 65% customers adopting 5 or more modules, 44% adopted 6 or more modules and 28% adopting 7 or more modules.
Falcon Flex Driving Large Platform Deals: Crowdstrike announced Falcon Flex, a new contract option, which has driven over $500M in deals. Its structure allows adding new products with no penalty and "right-sizing" endpoint licenses. Its contract structure is more similar to hyperscaler terms, which include a designated credit and “burn down” approach - customers have the ability to “right-size” an environment from an endpoint license perspective and repurpose those credits elsewhere.
Palo Alto Networks: The platformization dilemma
Palo Alto Networks continues to execute, albeit with a big overhang with investors around its platformization strategy will work over the long-term. In their recent quarter, Palo Alto Networks (PANW) reported revenue of $1.98B, up 15% year-over-year. This growth was supported by a 47% growth in the next-generation security (NGS) ARR - the cloud/subscription part of the business. They just had their sixth consecutive quarter of Secure Access Service Edge (SASE) growth exceeding 50% year-over-year. Their core firewall product revenue saw a 1% growth. It was a subdued quarter with business as normal (beyond the billings growth slowdown), but it is generally known that PANW has a slightly muted 3rd quarter before bouncing with a strong fourth quarter, so expect stronger expectations for the next quarter.
Platformization
The thesis around Palo Alto’s current story is how well its platformization strategy will work. This strategy is centred on getting more of PANW’s existing customers to adopt its full platform across SASE/Network security, SOC (Security operations), and Cloud.
During this recent quarter, they gave us a glimpse into their vision for this platform strategy. The goal is to grow the number of customers with multiple platforms from ~900 to 3,000 over the next few years, i.e ensuring these 3,000 adopt their network security, cloud, and SOC platforms (where they have 19+ products embedded).
Currently, 13% of their top 5,000 customers use three platforms, and 51% use at least two platforms. If they are successful in converting close to 2500-3000, this could potentially drive a $15B NGS ARR company. While this strategy sounds impressive, the bigger hiccup for investors to accept in the interim is the financial impact on the business over the short- to medium term.
PANW has PANFS (Palo Alto Networks Financial Services), which acts as a billing accelerator by offering deal structures tailored to customer budgets. In its recent quarter, billings slowed down, but PANW has told investors to pay less attention to billings since they are focused on winning long-term contracts (hence, investors need to focus more on RPO growth). The impact of this platformization strategy will be fully measured once it has lasted one full year since it announced the program, by which investors will see if the strategy is working.
PANW Business Updates
Cortex Business
PANW & IBM Partnership: During the quarter, Palo Alto announced one of its most impactful acquisitions (not monetary, but in terms of its impact on its data/SIEM strategy): PANW will acquire some key assets from IBM’s cybersecurity.
IBM Partnership: The latest update from PANW is that the partnership with IBM is already driving strong inbound interest from IBM customers looking to migrate to PANW's Cortex. The acquisition of IBM QRadar’s SaaS asset positions PANW as a top 3 vendor in SIEM/Security Analytics, a market expected to exceed $20B by 2026. Based on the QRadar migration, PANW estimates a >$2B total contract value opportunity from migrating IBM’s existing QRadar customer base over the next few years.
IBM Partnership Accelerates PANW’s GTM Impacts: I believe this is a big win for PANW in two ways. It’s less about the tech because PANW had a better data lake and SIEM product with XSIAM. 1) The bigger benefit is more around the GTM engine and customers coming from QRadar, which hugely benefits PANW within this deal. 2) A bigger benefit for PANW is that IBM will train over 1,000 security consultants on PANW products, marking the first time IBM will actively sell another vendor's security offerings. (I will be writing more on this topic in my next substack post)
SASE (Prisma SASE)
SASE is a big growth driver: The SASE business drives a large momentum (around >$1.5B ARR now) and will determine how big the company can continue to grow in the near future. The SASE business growth is largely driven by Secure Service Edge (SSE), which contributed to 50% growth. SSE (cloud-based deployments) accounted for 85-90% of the SASE business growth, while SD-WAN contributed 10-15%. The enterprise browser feature continues to unlock new use cases, enhancing product capabilities.
Firewall customers migrating to SASE: It was interesting to note that some firewall customers who are choosing not to refresh their on-prem firewalls are considering moving into SASE and Cloud. From a research note from CitiBank, PANW could see around 60% of their customer base going through a refresh, moving to SASE or cloud, with the potential for better average selling prices (ASPs) as SASE deals are typically 2.5x the total contract value of firewall (FW) deals over five years.
Market dynamics: The SASE market has shifted more and more to VPN displacement, with PANW well-positioned to capture this momentum. I wrote about this momentum similarly for Zscaler. PANW’s approach contrasts with competitors like Fortinet, who focus more on SD-WAN and branch office solutions.
Prisma Cloud Security
Comprehensive, but not well integrated: PANW has the most comprehensive product suite in cloud security. However, the bigger challenge is that it is not well-stitched together like other parts of the business. It is not as native to their platform as Crowdstrike or Wiz own their agent/agentless solutions. This is what I’ve heard from my network on the ground. This is likely the weakest part of PANW’s product lines. From all my conversations with security leaders and market research, Wiz and Crowdstrike are the leading names in cloud security.
Strong product in data security: The Cloud Security Posture Management (CSPM) market is becoming commoditized due to aggressive pricing and smaller vendors entering the space. PANW appears to be doubling down on its strong capabilities within data security posture management (DSPM), thanks to the acquisition of Dig security, which has become more important since AI/LLM adoption has grown. Together with more privacy regulations, this has become a critical piece for customers to understand their data stores in the cloud.
Zscaler: The new growth verticals
Zscaler’s success over the past few years has been predicated on its success as a first mover within SASE. However, as more players have moved into the SASE market and the company approaches a new scale (>$2B this year), it needs to expand into new verticals for the next growth phase as a platform.
ZScaler’s core SASE business (ZIA & ZPA) continues to grow, taking market share from on-prem MPLS, VPN, and SD-WAN systems. Revenue grew to $553M, up 32% year-over-year in its recent quarter, billings grew 30% year over year, and operating margin at 22%.
The company’s core focus is shifting towards new growth opportunities outside of its core SASE networking business into new verticals, including a new focus on data security, AI security and deeper network segmentation capabilities. The new ZS business platform offering includes the following:
ZS Product Categories:
As a refresher, here are ZS’s product suites and breakdown:
Zscaler for Users - ZPA, ZIA, ZDX:
Zscaler Internet Access (ZIA) is the company’s flagship product and sits between a customer’s users and the internet, inspecting traffic to protect against threats. Normally, user traffic flows through Zscaler’s cloud platform before flowing to and from internet applications, websites, etc., providing protection for employees connecting remotely.
Zscaler Private Access (ZPA) leverages Zscaler’s existing cloud data center footprint to provide secure remote access to internal applications. Unlike VPN approaches designed to provide remote access to the entire corporate network, ZPA utilizes policy-based controls to provide remote access on a per-application basis without exposing the internal network.
Zscaler for Workloads
Workload Communication and Network Segmentation (Airgap)
Zero Trust (Branch)
Zero-Trust SD-WAN for branch offices (new focus area)
Zero Trust Segmentation
Zscaler Zero Trust Networking for IoT/OT Security
Zscaler for B2B
ZScaler AI Cloud: Risk360, Business Insights (BI) and Vulnerability management
There is a new focus on the data fabric and, more importantly, on data security: DLP, DSPM, Email DLP, Gen-AI, and SaaS Security.
Zscaler aims to develop a comprehensive platform (powered by its Zero Trust Exchange) by leveraging its position as a proxy between applications and end users. The goal is to have a security product that secures users, workloads, branch offices, and physical devices (IoT/OT) and centralizes all these with a Zscaler data fabric for driving business insights. The company estimates its TAM has grown since it went public in 2018 from ~$20B to approximately $96B, currently split between User Protection ($61B), Workload Protection ($23B), and IoT/OT ($12B).
Key Points
Go-To-Market (GTM) Sales Attrition & Transition: The loss of Dali Rajic to Wiz, the former CRO who led ZS’ success through the pandemic, appears to have led to some major attrition within ZScaler’s team. They have a new CRO, Mike Rich, who is currently rebuilding their sales org, rebuilding their partner ecosystem, and aligning with GSIs (Global System Integrators) like Accenture, Deloitte, and EY. The new GTM is focused on an account-centric model. They aim to start new accounts from ZIA to ZPA to ZDX, Workload Protection to Data Protection. The whole sales attrition and rebuilding of their GTM will continue to be an overhang for the company.
Federal business: A huge part of ZScaler’s success in recent years that isn’t discussed much is its reliance on its federal business. This past quarter saw another increase in demand driven by federal government directives on VPN vulnerabilities and replacements, which benefited ZScaler. Also, nearly 50% of new customers are adopting Zscaler's Zero Trust security platform (ZIA, ZPA, ZDX), which positions the company well for expanding into data protection and cloud security.
Large enterprises continue to drive Zscaler’s growth: Beyond the strong Federal business, Zscaler continues to be the platform for some of the largest enterprises and organizations in the world. They added 26 new enterprises over $1M ARR in the quarter, bringing the total of >$1M ARR customers to 523, up 31% YoY, and 2,922 customers >$100k, up 20% YoY. ZS also now has >50 $5M ARR customers, up from around 35 in the prior year quarter and around 10+ customers spending more than $10M annually.
New product category for Zscaler:
Emerging products, including ZDX and Workloads, are growing faster than the overall business and are estimated to represent >20% of total revenues by the end of FY24. Additionally, Zscaler is including new GenAI-driven features in its advanced plus bundles, which are priced at a 20% uplift.
Data security commentary: Many of their new announcements at the Zenith live conference focused on how Zscaler has scaled its data security capabilities over the past few years. However, it’s important to note that other competitors like Netskope have had strong data security features. While Zscaler's advancements are closing the gap, particularly in DLP and data security, Netskope still has a longer track record of more data security features at the application level.
The ZScaler and Avalor acquisition commentary: The acquisition of Avalor’s data fabric augments Zscaler’s data and network security capabilities. My friend, Darwin, explains everything in more depth here in his Cybersecurity Pulse newsletter.
What’s the purpose of a security data fabric?
A security data fabric is the infrastructure and processes that create an integrated layer across many nodes (or data sources). Data fabrics often leverage advanced analytics and machine learning to identify relationships and patterns among disparate data sources, enabling real-time, data-driven decision-making. Avalor describes itself as a Data Fabric for Security with it's use case being vulnerability management. What this means is that Avalor extracts data from a customer's security solutions, normalizes and cross-pollinates findings from those solutions in order to surface highest-risk issues and then presents them to the customer. Avalor also has remediation assistance workflows so its not like they're solely surfacing vulns, but also helping with remediation. Aside from having a robust correlation engine that factors in the context (i.e., environment, reachability, exploitability, resource tags) that influence potential vulnerability impact, they also seem to have highly performant data infrastructure that enables the above, at scale. Avalor also has 150+ 3rd party integrations which include some of Zscaler's competitors. Simply put, the acquisition makes sense because it enables Zscaler to accelerate the implementation of AI into their products and it provides the infrastructure needed to correlate massive volumes of data across their offerings. Avalor can cleanse, normalize, and enrich data from Zscaler's various products to create a unified data asset that can be used for both training AI models and correlating security findings. This cross-correlation of data allows Zscaler to surface higher fidelity and prioritized findings to their customers, providing a level of precision and context that they weren’t previously able to.
ZScaler can now sell this product to their existing customer base and provide a “SIEM like product“ to centralize all the data from their existing tools into one product in which its output can drive SOC or business insights. Further, the Avalor acquisition also enhances ZScaler’s Risk360, allowing it to address inherent and residual risks. This makes it valuable for discovering misconfigurations and gaps in customer security postures. In the end, this is a drive from Zscaler to aggregate data. I will be writing more on this topic in my next report.
Okta
Okta was one of my top picks coming into the year based on its ability to rebound and bounce back, but it hasn’t successfully done that. They reported revenue growth of approximately 19% year over year. The company saw a 14.6% increase in Current Remaining Performance Obligation (CRPO) growth, below the anticipated 16%. It barely met investor expectations, but it still saw a decent quarter. Okta continues to recover from the setback of recent breaches, which has slowed its growth. The key highlights from the business in the recent quarter include:
Federal business driving growth opportunities: Okta’s traction was notable, with the largest ever public sector deal and significant deals with a large DoD agency consolidating over 75 identity tools using Okta. They had an average net new customer addition of 150, which matched the previous quarter but was below the TTM average of 340, reflecting macroeconomic headwinds and a shift towards greater upsell versus new business.
The core business - Workforce Identity and Access Management (WIAM): Okta started as a core IAM solution for enterprises. This was built around their workforce authentication platform. In this recent quarter, the WIAM business showed resilience, with 30% growth supported by upsell opportunities. A big part of their business success relies on winning more market share among existing on-prem customers with legacy on-prem authentication solutions. Okta’s workforce identity cloud benefits customers with large cloud and SaaS environments, giving them more room to capture this market.
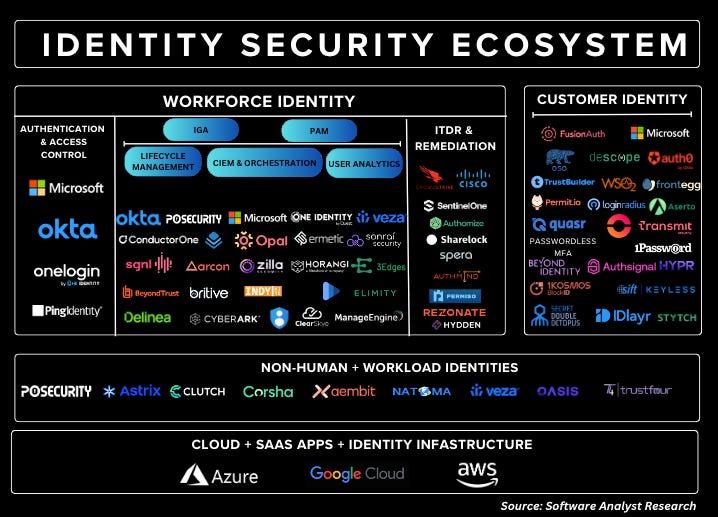
New product/growth areas: Okta’s next growth vertical focuses on expanding the pie within workforce identity (see IGA & PAM below) and entering new markets within customer identity solutions. As for Workforce Identity Expansion, the new areas for growth within the workforce are moving from the authentication to the authorization layer (as I’ve laid down in this market map below).
Customer Identity Suite: They have invested significantly in CIAM (Customer identity & access management) due to regulatory pronouncements and consumer-facing app proliferation. Okta has been heavily pushing to CIAM due to regulatory pronouncements and consumer-facing app proliferation (business). However, the prospects for this market to grow considerably has slowed down in recent months and the company hasn’t seen as much traction in this niche due to the headwinds for SMBs who generally rely on this product.
Workforce expansion: Okta is focused on expanding into the governance layer - primarily focused on Identity Governance and Administration (IGA) and Privileged Access Management (PAM). These solutions are designed for more modern cloud environments and are primarily DevOps-catered and less for on-prem environments. Their biggest challenge will be winning mindshare since Sailpoint, CyberArk, and a few private companies have a larger market share / name presence within the governance area than Okta does.
Okta Identity Governance, Okta Identity Threat Protection, and Okta Identity Security Posture Management (ISPM) are other categories of focus for the company. These solutions proactively assess identity posture, identify critical misconfigurations and prioritize remediation efforts. Although there has been early traction within PAM, the monetization opportunities have been much slower.
Fatima Boolani at Citi had some interesting takeaways from meeting with Okta’s CEO - Todd McKinnon that I believe are worth sharing here:
On the governance (IGA) front, OKTA reiterated that many of its wins are greenfield and that there has been a surprisingly high degree of, so-far, amiable co-existence with legacy products than was originally expected (ie. customer using Sailpoint for SAP, but using Okta Identity Governance around it for Cloud, related governance). Full IGA replacements are rare but do happen (though OKTA is not at all relying on this), but overall growth will continue to come from the aforementioned greenfield (mid-enterprise) / co-exist (large enterprises) dynamic.
Mythbusting on competition, passwordless advancements: Regarding MSFT, OKTA expressed that Entra is not a comprehensive solution, with drawbacks/white spaces in supporting non-MSFT tech (relatively weaker authentication, low-phishing resistant controls on Mac, Android, iPhone; less sophisticated workflows), and limited tech intricacy beyond basic single-sign-on – all areas OKTA has a differentiated leg-up as it continues to deepen its investments around cross platform support, compatibility across systems and vendors, richer access management scope, along with better governance, workflow, integration for the entire ID lifecycle.
The commentary was comparable regarding the threat/opportunities around biometric and passwordless authentication uptake – particularly considering MSFT in many cases owns the device or machine. That said, CEO observed that the universality of Windows devices/OSs has peaked – in that MSFT’s 90%+ share in the 1990s has pared down significantly today along with its Active Directory dominance– where OKTA brings benefits as a neutral vendor that can support diverse form factors and OS’s, while also bringing policy consistency across these heterogenous ID/OS/device points.
The 411 on ID Threat Protection (upsell), ID Security Posture Management (new SKU cross-sell): We appreciate the simplified breakdown of what IDTP adds to WIC. Powered by Okta AI, IDTP is being positioned as the next-gen of multi-factor authentication (MFA) and 10x more secure than predecessor eras of SSO, MFA, and adaptive MFA – due to its features around advanced risk monitoring, universal logouts, and signal sharing. The sophistication with which it interacts to “pings” with the rest of the cyber tools ecosystem (live, deep integrations with CRWD , ZS, PANW) elucidates a fuller array of alerts to help add better context to and solve ID attacks. Monetization will largely be realized via upsell on aMFA and should ride the upsell coattails of Zero Trust/SASE architectural mandates, but we did not get a sense of the uplift magnitude on a base SSO, SSO+MFA, or SSO+aMFA seat.
On the IDSPM front (intellectual property acquired via the Spera deal), while this is part of the entire equation of up-leveling the WIC IAM stack towards proactivity, it is being called out and carved out independently as a new separate SKU (still early access, but GA not far off). IDSPM deeply scanning and inspecting IDs in systems hooked into OKTA to break down multiple silos and flag issues is novel but natural, in that while OKTA has always stood “in front” of apps, data sources to validate logins going in, IDSPM now closes the loop by sitting behind/into these systems too. Having been deployed internally (dog-fooded), CEO identified this has helped markedly improve the company’s overall security posture, which we think should serve as an important reference to prospects. That said, revs ramp on this solution will naturally be dependent on system integration breadth/depth (which shouldn’t take long and is likely to encapsulate OKTA’s existing 7K integrations at large, over time).
Okta has the potential to reaccelerate growth (north of >25%) if it can capitalize on some of its new identity products above. Despite many recent challenges, it remains a market leader along with Microsoft within the authentication market category. Many competitors have struggled to disrupt them yet. However, that competitive advantage can only last so long. They need to restore their brand publicly, begin to make some traction on their new product categories, and gain new logos to provide any strong upside in the near term.
Cloudflare
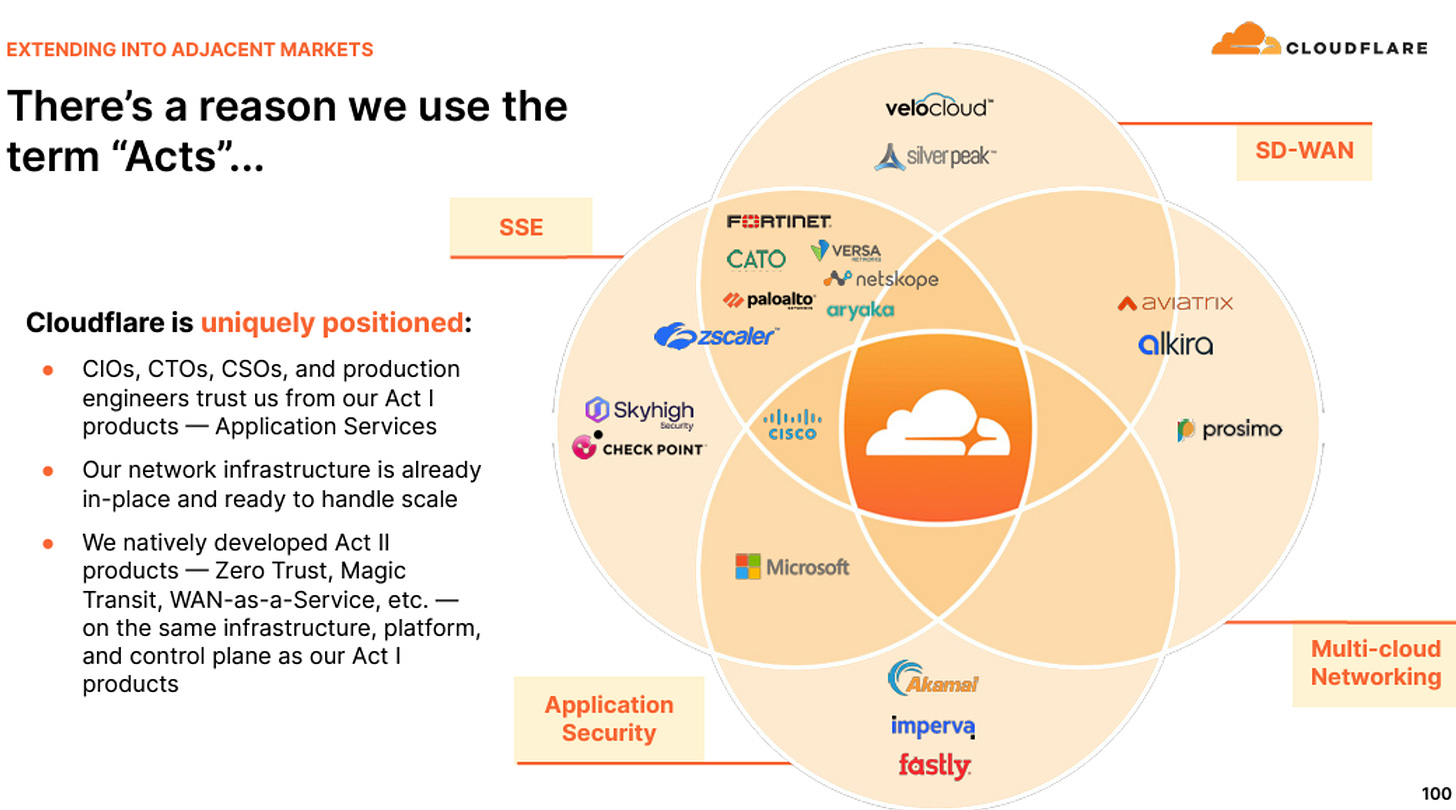
Cloudflare started the year modestly with revenue of $379M, growing 30% year over year. In my earlier reports, I outlined the Cloudflare thesis around its three acts, which is its strategy around building an ultimate platform solution.
Act 1: Application Services (Where the company began)
Act 2: Network Services Security Services (SASE/SSE)
Act 3: Developer & AI Services
See the full piece below
Almost a year later since I wrote that report, the company has been executing on their strategy modestly. Since this is a security newsletter, I will focus on their security efforts within Act 2. Here are some of the key updates:
The expansion into SASE (Competitive to ZS & Netskope): Cloudflare's expansion into the SASE market through the launch of Cloudflare ONE positions the company as a significant player in zero-trust and network services. Cloudflare’s history as a CDN player has enabled their network security solution to be much faster than key competitors Netskope and Zscaler. This provides a critical advantage, serving as both a global sensory system and threat intelligence engine. This network strength is a pivotal component of their growth strategy. Cloudflare has suggested its network is ~75%/50% faster than competitors like Netskope and Zscaler, respectively, while Cloudflare Access was also ~40% faster than ZPA. See evidence and data here and here. This network advantage also acts as a global sensory system and threat intelligence engine that helps them. However, they still have many areas to catch up to become a fully respected SASE player like Zscaler and Netskope. The business results from SASE doesn’t seem to be showing any massive traction yet. Here are some updates from the recent quarter.
During the quarter, Cloudflare acquired a Zero-Trust company, BastionZero, to enhance its SASE vision with zero-trust infrastructure access controls, simplifying the stack and reducing costs by eliminating the need for bastion hosts and complex PAM solutions. This move extends Cloudflare's VPN replacement capabilities, providing robust security for infrastructure resources.
Cloudflare’s SASE Advantage
Cloudflare’s advantage is how they all their native features tightly integrated into one stack and all built up from ground-up. Many other competitors either have to borrow some of their SASE features either by leveraging SD-WAN networking appliances from Velocloud/Silverpeak (if its a cloud-player with no networking history) or the networking guys have to acquire their way to get the SSE part.
The company has a unique advantage and the technology required to win the SASE and MPLS replacement market. They can leverage the shift from centralized to decentralized network infrastructure in networking to consolidate a number of network security solutions (CASB, SD-WAN, WAF, ZTNA) into their platform. Their extensive presence and optimized traffic paths position them favourably for cloud-based infrastructure adoption amid a growing threat landscape.
However, everything comes down to their execution on the GTM front and winning the top-down personas at large enterprises required when selling these products. If they can’t execute on this front, it’s going to be difficult to make any meaningful headways.
Other security updates:
Cloudflare's AI security features: they launched a firewall for AI and AI observability tools, offering comprehensive protection and better visibility on AI investment ROI. This positions Cloudflare as a one-stop shop for AI inferencing security, enhancing its platform's attractiveness to AI-focused enterprises.
Cloudflare's malware content scanner enhances security by protecting files in transit, providing robust defence against threats during file uploads. This feature strengthens the overall security of Cloudflare’s platform, particularly for AI applications.
Partnership with Crowdstrike: Although separate from SASE, they announced the expansion of their strategic partnership with CrowdStrike which connects the two platforms to deliver full device-to-network security capabilities. This combined offering enhances the visibility necessary for SOC teams to detect and respond to attacks. This expanded partnership should continue to help Cloudflare get closer to larger enterprise accounts, which is critical in selling many of their Act 2 products.
Beyond the security opportunities outlined above on SASE, Cloudflare also has an opportunity that lies in its edge network capability to provide an optimal solution for AI inferencing workloads for GenAI. They estimate that over 78% of the top 50GenAI customers are already leveraging them.
Datadog
I got an opportunity to speak to a few Datadog security leaders about their product roadmap in cybersecurity, including getting some updates from their recently concluded DASH conference. Before diving into that data, let’s briefly discuss the business highlights and where Datadog is today. Some updates:
Datadog reported a 27% YoY increase in 1Q24 revenues, driven by strong momentum across its product lines, particularly the three pillars of observability: infrastructure monitoring, APM (Application Performance Monitoring), and log management. Datadog's robust growth is fueled by its diversified product lines and advancements in security and observability.
Products outside their three core pillars have exceeded $200M ARR in the quarter, with 12 products launched between 2020 and 2022 now representing ~11% of ARR and eight products each generating over $10M in ARR. While there has been some initial resistance due to different buyers and departments, these products are becoming anchors in Datadog’s security portfolio.
Datadog’s revenue growth and product momentum are driven by a big part of its multi-product module adoption across large customer cohorts. For example, they’ve seen tremendous expansion here:
2+ products or more (growing 82% YoY)
4+ products or more (growing 47% YoY)
6+ products or more (growing 23% YoY)
8+ modules or more (growing 10% YoY)
Datadog’s Security Portfolio
Datadog has been building a large portfolio over the past two years. Below, I wanted to share some updates on it. Their security offerings now have 6,000 customers. They are all built around the fact that Datadog runs in most cloud production environments through the Datadog agent on cloud accounts, and they have a deeper understanding of these environments than many competitors. Their security portfolio can be divided into three areas (AppSec, Cloud, and SIEM).
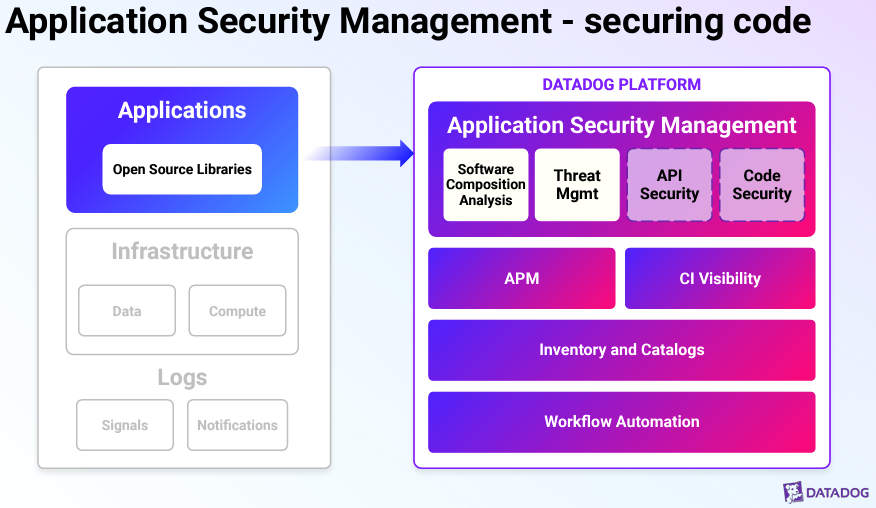
Application Security Management
Cloud Security Management
Cloud SIEM
I’m going to cover these product categories in simplistic terms below, but I plan to write something more in-depth in the near future. Breaking down these categories, they all line up into the following here:
Application security management
Datadog’s ASM helps secure application code by focusing on the code developers write, including any libraries and external sources they use. Their tools can detect active attacks from bad actors and find vulnerabilities in the code before it goes live. They have their Software Composition Analysis (SCA) tool that scans code for vulnerabilities detected in OSS libraries, which helps ease the process of managing 3rd party dependencies as cloud-native apps often include a large proportion of open-source code. This means developers can pinpoint and fix issues before they cause problems. Datadog also works on securing APIs and other parts of the code. By building on their existing products within APM and CI Visibility, they make these security tools available to all developers.
They are specifically focused on providing a broad suite of application security testing (AST) tooling for customers: SAST, IAST, ATO, software composition analysis, code security (new), and API protection. The more interesting product that they will release soon is Code Security (in beta), which is an IAST solution that can detect and prioritize code-level vulnerabilities in production environments and suggest remediation steps to include in lines of code. To understand all the terminologies here, please read my deep dive into the cloud and app security ecosystem.
Their goal is to help developers and security teams work together seamlessly in a DevSecOps model, preventing the accidental deployment of insecure code.
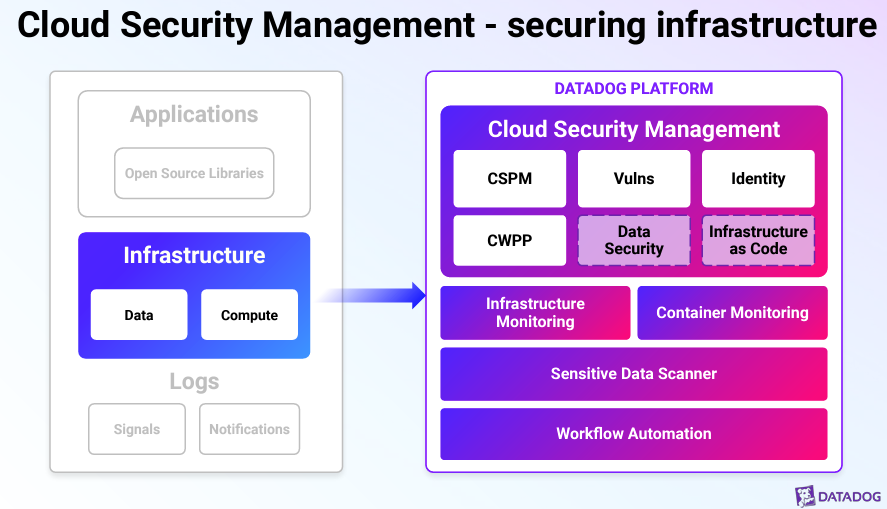
Cloud Security Management
Datadog’s Cloud Security Management (CSM) has fully made all their cloud products GA. Their CSM solution secures cloud infrastructure by spotting misconfigurations and vulnerabilities in production environments. The product identifies issues in containers and hosts, while the Cloud Security Posture Management (CSPM), CIEM, KSPM, VM, CWPP, and FIM tool manages these risks. They also have an identity risk management tool to find users with too many permissions. If a bad actor gets in, their workload protection detects malicious activities like suspicious files or network actions. They scan infrastructure code to ensure it’s secure and integrate all these tools into the existing Datadog platform, making them easy to use for both security and DevOps teams. Their service management approach helps close the loop on security issues quickly.
Most importantly, they recently announced a new agentless scanning solution (a common feature in cloud security), which allows customers to scan for vulnerabilities without needing to install the Datadog agent, facilitating a smoother vulnerability management and detection experience.
Cloud SIEM
Datadog's Cloud SIEM collects logs and data from different sources to detect threats based on patterns identified by their security team. Customers can choose specific content from third-party vendors, like Okta or Microsoft 365, and integrate it with Datadog for custom threat detection. They have cloud audit logs, security log ingestion, real-time threat detection, and graph-based investigators.
The most interesting thing about Datadog’s SIEM approach (compared to many competitors) is that they have an identity-focused SIEM to detect threats. They focus on understanding user behaviour and identity analytics to spot and score risky behaviour when an identity behaves beyond baseline. They have a workflow automation component that allows SOC teams to take quick action on detected threats. Built on Datadog’s log management capabilities, this tool is accessible to all team members, making it easy to respond to threats. The focus is on turning threat detections into actionable steps, enhancing collaboration and reducing friction between teams.
In summary, Datadog has the right vision for cybersecurity. At the core of Datadog is its unified agent, which builds upon its strong competitive advantage within cloud environments—observability—and leveraging that same agent to build around all its other security products. Many of their security efforts are focused on expanding their product suite. Datadog's future growth will be anchored by a strong and expanding product portfolio that addresses critical customer needs in observability and security powered by their Datadog security research. The company's ability to innovate and adapt to market demands positions it for continued success. Key drivers include the successful adoption of security products, sustained revenue growth, and the ability to capture a significant share of the observability market.
Concluding Words
Today, I’ve provided a high-level overview of the key cybersecurity companies. In general, I find public security companies always provide a glimpse of where the market is heading since they all have a large install base of customers. From the first half of the year, it has been clear that Crowdstrike is ahead of everyone (not just in cybersecurity but also in the broader technology software industry). They have executed against some high investor expectations. I expect the business to slow down at some point, but I don’t expect any major collapse. Palo Alto Networks has two more quarters to prove its strategy. The story with them is when a full year elapses on their platformization story; it will be important for them to show some results. Okta has a hurdle of rebuilding its customer trust and, importantly, expanding into new growth verticals. Cloudflare and Datadog are building important cybersecurity businesses that industry observers should monitor.
To get a full update on everything happening within the Cybersecurity industry, I recommend readers visit Altitude Cyber (Everything on the major deals across the cybersecurity industry from January - June). If you want to research private cybersecurity companies, please visit my favourite research platform on joincypher.com
🖥️ Cybersecurity Bootcamp Goes Deeper 🖥️
My cybersecurity bootcamp gives you an introduction and a deeper dive into the seven major cybersecurity industries. This cybersecurity primer report is a sneak peek into the reports I teach during our upcoming cybersecurity bootcamp.
The cybersecurity program delves deeper into each of these foundational components, providing an easy framework for you to grasp the cyber landscape and key players within each category - whether you’re an operator, investor, or someone who wants to expand your knowledge of cybersecurity. I cover all of the leading cybersecurity companies discussed above in depth. (Few more days left!).
Thank you for reading!













I'd be interested in checking out the webinar, looks like it needs a passcode?
Excellent piece of work