Runtime Security In 2025: How Wiz Defend Signals The Future of Cloud Security Operations
With Google’s Acquisition Looming: What Wiz’s Latest Launch Signals for Cloud Security and SOC Convergence, one of the biggest themes in 2025!
Readers,
Just over a year ago, I published The Wiz Playbook, detailing how Wiz outexecuted its cloud security competitors to become not only the fastest-growing cybersecurity company in the world, but one of the fastest-growing tech companies ever. That story ended with a twist no one expected (so soon): a $32 billion acquisition by Google—one of the largest cybersecurity deals in history. See my full analysis here.
But what happens after the fairy tale ending (pending its FCC approval)?
Now begins the harder chapter, in my opinion: transformation from category creator to a major platform. Wiz is no longer just trying to win cloud visibility (CSPM), it’s coming straight for one of the most defensible markets in security: endpoint detection and response (EDR), which has produced a $100B company like Crowdstrike!
But in typical Wiz fashion, they’re not targeting traditional endpoints. Instead, they’ve launched Wiz Defend, a new product designed to bring “EDR-level threat detection” to cloud workloads, containers, and ephemeral infrastructure. In short: it’s EDR, reimagined for cloud runtime. Let’s be clear: this is nothing completely new, as I have already conducted a complete analysis of Palo Alto’s Cortex Cloud in a previous report.
Wiz’s play is a direct challenge to incumbents like CrowdStrike and Microsoft, but targeted at cloud. It’s also a strategic bet that the future of detection and response won’t live on laptops, but it will live in cloud-native infrastructure. The stakes are massive because as we know the biggest CISO budget’s lie within the SOC (Go and ask a CISO how much they spend on their SIEM + EDR tools). See my latest SOC report on the evolution of SIEMs to get a glimpse, but this is why we know whoever dominates runtime visibility and threat response in the cloud will define the next decade of SOC operations.
Why This Report
After speaking with several of the Wiz co-founders and many senior executives over the past month, this report marks Part 2 of a two-part series exploring the evolution of cloud runtime security (see first one). While the first part analyzed the industry’s shift from agentless to hybrid detection strategies, this second part focuses on Wiz’s newly launched runtime product, Wiz Defend. It explores what makes Wiz Defend different and critically examines its strengths and weaknesses to assess whether Wiz can replicate its CSPM success in the far more competitive world of cloud runtime security.
Key Insights & Report Summary
The Emergence of Cloud Detection and Response (CDR): As we’ve discussed, cloud security has matured beyond static misconfiguration scanning. Cloud Detection and Response (CDR) introduces real-time alerting and behavioral correlation across identities, workloads, configurations, and network activity. This fusion enables security teams to detect, investigate, and remediate threats faster and with far less noise. Wiz Defend exemplifies this shift by integrating runtime detection into its broader CNAPP platform. Wiz has had agentless CDR to detect and respond since 2022, Wiz Defend, launched in 2024 expanding on the platform with the team from Gem Security, is now a complete suite for capabilities for Cloud SecOps including incident readiness, detection, investigation, response & forensic collection, and threat-hunting & cloud native threat intelligence.
Wiz Defend: A Hybrid Detection Breakthrough: Wiz Defend, launched after Wiz's acquisition of Gem Security, builds on its agentless CSPM foundation by introducing a hybrid detection approach. Lightweight eBPF-based sensors capture deep runtime signals, while the Wiz Security Graph correlates them with control-plane and identity activity. This enables behavior-based detections without sacrificing deployment agility, which remains a clear differentiator in the cloud runtime market.
Real-world impact: The report highlights real-world attacks like SeleniumGreed and IngressNightmare, showing how Wiz Defend detected and blocked malicious activities like credential theft, reverse shells, and RCE exploits — all while maintaining low CPU overhead.
Wiz + Google = Cloud SOC: Wiz’s GA release of Defend comes on the heels of its acquisition by Google. This opens the door for deep integration with Google SCC, Chronicle SIEM, and Mandiant IR. Together, these components could reshape the future of security operations by delivering an end-to-end Cloud SOC platform. The vision is to rival Microsoft Defender by merging posture, runtime, and threat intelligence into a unified command center.
Strengths and Opportunity Areas with Wiz Defend: Based on my review of the solution, Wiz Defend’s strengths lie in its unified platform, hybrid detection flexibility, and cross-cloud correlation capabilities. Its biggest opportunity areas are expanding runtime support for Windows environments (currently in preview) and deepening direct integrations with SIEM, XDR, and SOAR platforms.
The Future of Wiz Platform Playbook: Cloud → Code → Runtime: Wiz’s long-term platform vision extends far beyond cloud posture management. With Wiz Defend, the company is bridging the gap between Wiz Cloud (its CSPM foundation) and the deeper layers of runtime and application security. Wiz Defend reflects a pivotal shift in the cloud security landscape: from posture to protection, from visibility to response, and from isolated alerts to collaborative remediation. As SOC teams embrace real-time detection and behavioral analytics, platforms like Wiz Defend are helping guide the transition. However, it’s important to be clear: this journey will take time. Achieving true convergence across posture, runtime, and response will not happen overnight.
What is Cloud Detection & Response?
For my SOC readers, or those not primarily focused on the cloud, CDR is defined as the process of identifying and mitigating security threats or incidents within cloud environments. It involves real-time monitoring, investigation, and both automated and manual response actions. CDR tools provide real-time alerts and embed cloud-specific context to help security operations teams prioritize remediation efforts. These tools can also automate responses, such as quarantining workloads or creating isolation zones.
I also wrote a primer on how CDR works in a recent LinkedIn post. However, I highly recommend if you want to learn how this industry — from:
The language of what is cloud runtime?
The unique challenges of threat detection and response in a cloud environment?
Preparing for cloud attacks and how to detect attacks in real time?
Investigating cloud incidents and how to get the best outcome in your SOC or cloud team?
How cloud runtime detection and response works?
There was a great webinar, but to learn how Wiz Defend works, please visit and easily download this guide. It’s the best explanation for any SOC team, engineering or DevOps team.
How Wiz Reshaped Agentless Cloud Security’s Operating Model
As I discussed in Part 1, cloud security initially relied on traditional agent-based tools that were noisy, clunky, and generated excessive alerts. While Orca is often considered as the first agentless solution, Wiz introduced a far more operationally effective agentless CSPM approach for many enterprises. It scanned cloud infrastructure externally to identify risks, such as open AWS buckets or misconfigured Azure firewalls, within minutes, without disrupting operations. These highly prioritized findings fed into a risk map that gave security teams a clear view of their environment and enabled them to address issues before attacks, emphasizing prevention over reaction. Overall, this advantage Wiz gained came from democratizing security by bringing dev and sec teams together and truly understanding the cloud. See more in my original research on Wiz [Linked here].
Why Cloud Runtime Security Has Become Increasingly Important
By 2024, 95% of enterprises relied on cloud computing, with 44% experiencing a cloud breach in 2024, often due to preventable gaps. Over 70% of enterprises on cloud now use containers for application management. Traditional tools like Security Information and Event Management (SIEM) systems falter under multi-cloud data floods, while Endpoint Detection and Response (EDR) solutions are limited in their ability to track dynamic workloads (e.g., containers, serverless functions). This gap heightens risks of financial losses, regulatory penalties, and reputational harm, leaving SOCs outmatched.
As a result, we’ve seen new examples of recent attacks:
In 2024, APAC saw a 127% surge in cryptojacking incidents, where attackers hijack cloud resources to mine cryptocurrency, often targeting serverless functions.
EMEA experienced an 89% rise in identity-based attacks exploiting stolen credentials.
Google’s Mandiant reported that 70% of 138 disclosed vulnerabilities in 2024 were first exploited as zero-days, up from previous years.
By mid-2023, container attacks had surged by 50%, highlighting a runtime security gap that allowed attackers to infiltrate live workloads.
Overall, these incidents highlight the limitations of preventive measures alone, as many threats, notably zero-days, emerge only at runtime. Unlike CSPM or CWPP, CDR detects and responds to live threats, for e.g: stopping a malicious Lambda function in 8 seconds for an APAC retailer, maintaining 99.8% uptime, or provides forensic telemetry to trace attack origins, supporting compliance and reducing damage when prevention fails. For example, Wiz Defend can map an attack from a compromised container to an S3 bucket, offering full situational context.
The Evolution of Cloud Runtime Security & Wiz Is Aligning Its Product
In recent years, we’ve seen the tide turn. In my last report, I detailed how cloud security has evolved over the last few years as seen in the diagram below.
For more deeper context into this evolution of how cloud runtime, there is more detail around this traditional evolution to this new market [See in-depth report]. However, I can try to summarize some key points.
The evolution of runtime security in the cloud has been fascinating, beginning with Endpoint Detection and Response (EDR), expanding into Cloud Workload Protection (CWP), and now being redefined by new platforms like Wiz Defend.
In the early cloud days, organizations attempted to bring legacy security into the cloud by deploying EDR tools such as CrowdStrike or Palo Alto Cortex into cloud environments. These agent-based tools were designed for traditional endpoints like laptops and on-prem servers. While they provided basic runtime visibility, they were never built for the ephemeral, distributed, and identity-driven nature of the cloud. EDRs struggle with limited visibility into cloud-native services, containerized infrastructure, serverless functions, and control plane activities. They also fail to contextualize alerts with posture or data exposure, which leads to operational blind spots and noisy alerts that don’t help SOC teams prioritize or understand the full extent of an emerging threat.
To address this, cloud security vendors introduced Cloud Workload Protection Platforms (CWPPs). CWP represented an incremental improvement: it extended security into virtual machines and containerized workloads and introduced some cloud-specific integrations. However, these tools remained narrowly focused on individual workload protection, often requiring agents. Over time, we’ve seen new startups build eBPF technologies that are able to provide a similar level of depth of analysis with lesser operational overhead.
Wiz Platform Strategy
Wiz already had plans to expand their platform from Wiz Cloud to application and developer security, and then into security operations. Some of the work came when Wiz introduced CWPP and deployed an eBPF sensor, a Linux kernel technology that monitored system calls with low overhead (under 2% CPU) and tracked containers, virtual machines (VMs), and serverless functions in real time.
It caught anomalies, like unauthorized scans or file tampering, with an 11-millisecond alert latency (according to the Wiz blog). The sensor also provided Kubernetes-specific features like file integrity monitoring and drift detection. This hybrid model is strong and performed well against traditional EDR, though SOC teams noted needs for customizable rules and faster containment to better align with their workflows.
By early 2024, to address this customer need, Wiz acquired Gem for $350 million, a firm with deep expertise in cloud incident response and anomaly detection. Wiz launched the public preview of Wiz Defend in December 2024, integrating CDR into its CNAPP framework. CDR focused on live threat mitigation, complementing Wiz’s complete visibility across cloud, workload, Kubernetes layers, and developer activity. With Gem’s anomaly detection, this unified platform correlates suspicious activities, like unusual Virtual Private Cloud (VPC) flow patterns or Identity and Access Management (IAM) role escalations, with workload telemetry to detect threats such as cryptojacking, ransomware, and container escapes. It prioritized remediation based on real-time threat signals rather than static CVE scores, ensuring critical vulnerabilities are addressed first.
Wiz Defend
Today, Wiz Defend is Wiz's offering for cloud detection and response designed for cloud environments, aiming to redefine how organizations approach security operations in the cloud by unifying cross-layer context with runtime signals and bringing SecOps, cloud security, and developers together in the same platform for shared understanding and better collaboration.
The foundation for Wiz Defend came from the team behind the Gem Security acquisition. Gem Security, prior to acquisition, was one of the few startups taking cloud anomaly detection seriously, moving beyond simple log parsing and building actual heuristics around identity behavior, flow data, and policy drift. This means things like unusual VPC flow alerts that don’t rely on static rules or cross-cloud correlation, such as Okta to AWS IAM misuse.
It provides a unified approach to cloud security operations, applying all the capabilities and code-to-cloud context of Wiz’s cloud-native agentless detection with analysis of CSP telemetry, real-time threat intelligence from the Wiz Security Research Team, and runtime signals from an eBPF sensor for complete runtime protection and faster, more efficient detection and response in the cloud. It is positioned as the solution that will replace legacy paradigms around EDR or primary agents that focused on point-in-time signals. The goal with Wiz Defend, as I understand it, is that it leverages a hybrid detection model, combining agentless cloud telemetry (from CSPs, IAM logs, posture scans, and data flows) with optional runtime sensors for deeper detection across Kubernetes, Linux, and Windows (currently in preview).
What I found most interesting about Wiz Defend is its end-to-end integration with the Wiz Security Graph, which correlates runtime behavior, configuration drift, vulnerabilities, and sensitive data exposure into a single contextual view. It is context-first, identity-aware, workload-agnostic, and driven by AI-powered insights.
The core principle behind this model centers on three key pillars:
Preventive security, which establishes strong baselines during code development;
Proactive security, which focuses on mitigating critical risks before they can be exploited; and
Blocking security, which rapidly identifies and responds to emerging threats.
Example of Recent Attacks With Wiz Defend
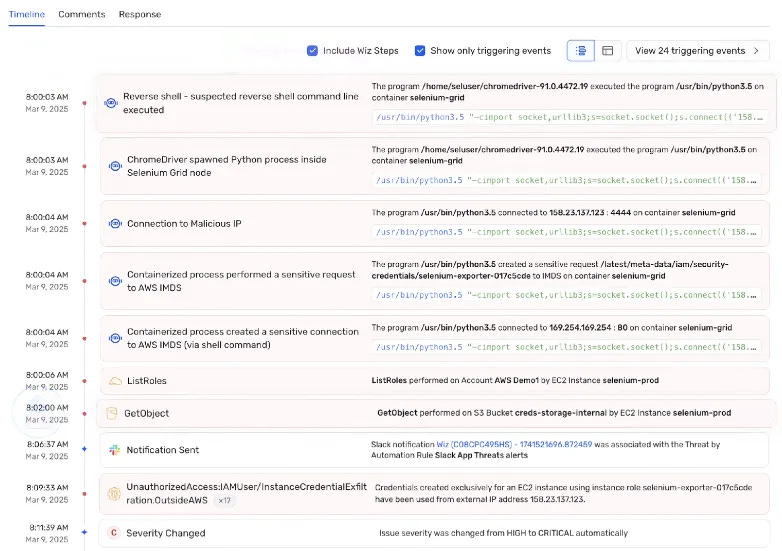
Wiz Defend: Selenium Greed Threat Example
Wiz Defend eliminates noise using a powerful combination of behavioral analytics, thousands of built-in detections for cloud-specific TTPs, real-time threat intelligence, and code-to-cloud context for a clear and prioritized view of threats.
Wiz includes thousands of built-in detection rules that are continually updated by the Wiz Research Team. One feature customers consistently highlight is the ability to add custom detection rules tailored to organizational needs and upload them for multi-cloud coverage and detection.
Imagine an attacker targeting a Selenium service running in an AWS Kubernetes environment. The attacker exploits the Selenium service to open a reverse shell and establish a foothold on the compromised host.
Most solutions would have gaps in identity and data risk visibility or would require analysts to pivot between multiple platforms to gather this data. In Wiz, however, all context is clearly presented through an AI-assisted Storyline, the Wiz Security Graph, and an Incident Timeline. These are further enhanced by an interactive, queryable AI chatbot, enabling even less experienced analysts to investigate container threats by asking natural language questions.
The Runtime Sensor deployed on the node detects the reverse shell immediately and raises an alert to the security operations team. If running in blocking mode, the sensor would terminate the malicious process instantly to stop the attack. If blocking is not enabled for reverse shells and the attack progresses, Wiz continues to detect each subsequent phase.
As the attack unfolds, Wiz identifies threats at each stage of the attack lifecycle, allowing teams to contain the threat actor step by step. If the attacker continues and exfiltrates AWS credentials from the host, they could move laterally to the control plane and eventually exfiltrate data from a sensitive AWS S3 bucket.
As the attacker shifts to the control plane, Wiz correlates the compromised keys used in the exfiltration attempt with the compute node targeted in the initial attack. It then presents Incident Responders and SOC teams with multiple, actionable recommendations for containment: kill the malicious process, rotate the compromised credentials, block public access to the S3 bucket, or remediate the misconfigured Selenium service.
Wiz Defend automatically correlates suspicious process executions detected by the Wiz Sensor (indicated by the blue Runtime Sensor logo beside alerts) and organizes them by principals.
One of the key strengths of Wiz Defend is its cloud-native response playbooks and automation capabilities. It facilitates organic collaboration within the platform between SecOps, Cloud Security, and Development teams. It offers built-in, one click containment actions and allows teams to create custom response actions using Python. These can be linked to either built-in or custom detection rules.
In addition to real-time response, Wiz enables proactive collaboration between SecOps and development teams to improve cyber resilience. For example, after detecting the compromise of a Selenium Grid container, Wiz can trace the issue back to the original Dockerfile used to build the image. It then provides developers with actionable guidance and a one-click pull request to remediate the vulnerability, retest, and redeploy the updated container.
Strong Capabilities of Wiz Defend
Based on the demo I’ve received and all the analysis I’ve done, these are a few strong capabilities that the Wiz Defend product offers:
Agent & Agentless Flexibility
Wiz Defend's hybrid detection approach provides immediate, low friction visibility into cloud configurations, identities, data flows, and control plane activities across multi-cloud environments by combining agentless telemetry with optional runtime sensors. The agentless layer enables rapid onboarding and broad coverage without deployment overhead. The runtime sensor (e.g., eBPF-based for Linux, with Windows in preview) adds deep, process-level telemetry and behavioral detection capabilities for high-fidelity threat identification. The hybrid model allows Wiz Defend to correlate static posture with dynamic runtime activity, enabling contextual alerting, better triage, and real-time threat detection. This offers customers the flexibility to scale coverage progressively, based on risk, architecture, and operational maturity. Enterprises with both legacy VM-based workloads and modern containers or Kubernetes can use Wiz agentlessly and deploy agents where needed, providing flexibility from a single vendor.
Leveraging the Power of the Wiz Graph
One of the areas I like includes how they are able to leverage the Wiz Graph to better enrich context. The security graph processes 1.2 billion asset relationships daily, ties these insights together, mapping relationships across cloud assets to trace attack paths and potential blast radius (e.g., from a compromised container to an S3 bucket, via GraphQL queries like “Which production workloads expose public APIs?”). Most of this is enhanced by Gem’s real-time log analysis and Wiz’s original eBPF sensor’s runtime monitoring. One of the most important factors when companies want to deploy agents is being aware of its capacity constraints and operational overhead. Based on my understanding, the eBPF sensor uses kprobes, tracks system calls with an 11ms alert latency (outpacing Sysdig’s 47ms according to the CNCF Benchmark, 2024), detects ransomware or unauthorized access with precision, and maintains overhead below 2%.
Wiz Behavioural Baselining Is Strong
One of the interesting features I found later is that Wiz Defend ingests cross-layer telemetry (control-plane events, identity logs, network flows, data-plane activity, and ebpf-driven runtime signals) into the Wiz Security Graph - discussed above and statistically derives “normal” patterns unique to each customer’s cloud footprint. As new resources spin up or usage patterns shift, those baselines automatically recalibrate—ensuring anomalies reflect true deviations rather than stale thresholds.
Built around its graph, Wiz applies a blend of statistical anomaly-detection algorithms (to catch deviations from established baselines) and thousands of TTP-based, rules-driven detections authored by its research team. Every alert is enriched with real-time threat intelligence and code-to-cloud context, so anomalies aren’t just flagged—they’re scored for severity, mapped to MITRE ATT&CK, and prioritized by potential blast radius. This is a very cool capability to reduce the number of false positives that plague SOC teams.
Out-of-the-box detection rules
One of the biggest hurdles for traditional SOC teams face is their lack of understanding of writing detection rules for cloud workloads since this isn’t their DNA. However, Wiz has prioritized this capability. Wiz aggregates thousands of curated rules (3,000+), custom runtime policies and their threat research. This out-of-the-box capability allows Wiz Defend to ship thousands of high-fidelity, research-curated detection rules spanning misconfigurations, IAM anomalies, data-access irregularities, behavioural IOCs, and more. Additionally, customers can author bespoke runtime rules evaluated in real time by the eBPF sensor to catch environment-specific threat vectors (e.g., proprietary services, sector-unique risks, or VCS-to-cloud workflows). This dual approach allow for both broad, cloud-native coverage and deep, customer-tailored detection.
Workload-to-Cloud Detection Correlation
Due to Wiz’s cloud-native DNA, they have developed a way to connect cloud workloads to the cloud control plane in a unified manner. Most tools alert either at the workload level (e.g., suspicious process in a container) or at the cloud control plane level (e.g., S3 access from a suspicious IP). Few can tie the two together, and even fewer do it in a contextually correct way.
Wiz Defend introduces an investigation graph that correlates these signals across different environments, from a runtime process in a container all the way up to cloud activity like an S3 read. That cross-layer visibility is what real-world SOC teams need to understand the full kill chain of a cloud-native attack. While this correlation isn’t as tight as direct causality, it is inferred based on asset relationships. Even these inferred relationships between processes, users, and cloud assets put Wiz ahead of most legacy CNAPPs and EDRs.
Hybrid Detection (Agentless + Sensor)
It allows some baseline visibility even without full Windows runtime. The solution emphasizes reducing manual workloads and eliminating noise, enabling quick collaboration between security and development teams through automation and root-cause analysis. Wiz claims significant improvements, including an increase in cloud workload visibility, an acceleration in threat detection and response times, immediate visibility into zero-day threats, and a tenfold reduction in investigation and remediation efforts.
Cloud Response Remediation
Over time, Wiz needs to have a cloud-native AI-SOAR remediation capability capable of allowing SOC teams to take response actions directly from a cloud alert without waiting on human intervention or an external automation platform. These actions, especially IAM role de-escalation and session terminations, are directly aligned with the identity-centric attacks that dominate cloud breaches. While other competitors have similar actions, having this capability natively within Wiz will be key for speed and effective containment. Wiz will also continue to further enhance its research organization. While Wiz Defend can generate alerts, SOC teams typically rely on SIEM or XDR platforms for in-depth investigation and response workflows. Wiz will have to find the balance between being deeply integrated with SOC platforms while keeping its strong cloud DNA.
Future Areas To Watch, Improvements & Roadmap
Windows Runtime Environments (vs. Linux)
Wiz currently demonstrates strong capabilities in Linux and Kubernetes-native environments, offering deep runtime visibility and comprehensive sensor-based coverage for Linux workloads in VMs, containers running on Kubernetes, and serverless functions based on Linux OS.
Windows runtime coverage is currently in preview, indicating ongoing testing with select enterprise customers. It is not yet at feature parity with the Linux capabilities. The long-term vision is to support Windows-based cloud workloads equally, but the rollout is being carefully staged. While the runtime sensor model, leveraging technologies like eBPF for Linux, is being extended, inherent OS differences (such as the absence of eBPF in Windows) necessitate a phased and research-informed approach by the Wiz team for Windows support.
Many large enterprises, particularly in sectors like banking, government, retail, and manufacturing, operate in hybrid cloud environments with a mix of Linux and Windows workloads. Competing vendors such as CrowdStrike and Palo Alto Networks (with mature EDR for Windows) currently offer broader runtime capabilities for Windows environments. The speed of engineering development is often underestimated in security tooling, where feature rollouts can take significant time. Wiz’s rapid progress in integrating Gem’s detections, developing runtime visualizations and dashboards, and releasing a Windows agent preview demonstrates strong organizational alignment and investment, signaling to both customers and competitors that Wiz’s ambitions extend beyond cloud visibility to becoming a significant player in the SOC landscape.
Detection Correlations
Wiz has developed a strong correlation investigation graph that outperforms many competitors, but it is important to be mindful that while correlation in detection is powerful, inaccurate correlations can be detrimental. If a SOC analyst mistakenly assumes a link between unrelated events, it can lead to wasted time investigating false leads and potentially overlooking genuine threats. The fact that Wiz currently displays correlated events based on asset relationships, rather than direct activity chains, may limit the level of trust analysts can place in these alerts.
Wiz needs to watch for competitive pressure from both traditional vendors and emerging startups
While Wiz Defend represents a compelling shift toward unified cloud-native runtime security, it enters a competitive landscape marked by both entrenched incumbents and agile upstarts. Traditional endpoint security vendors with very strong on-prem presence and SOC Threat Intel backgrounds like CrowdStrike, Microsoft Defender for Cloud and Palo Alto Networks, exist as we discussed above with mature agent-based EDR solutions that offer deep containment and policy enforcement for on-prem workloads. However, more pressing might be the presence of emerging startups like Upwind, Armo built for this specialization.
However, Wiz main advantage is that it has a cloud-native DNA better than many competitors and many companies begin their cloud spend with posture/compliance/vul scanning before expanding to covering runtime security.
However, as the runtime security category expands, Wiz will need to navigate this dual pressure: defending against incumbents with broader platform integration and proven endpoint controls, while also differentiating itself from niche vendors that are increasingly innovating around identity-aware detections, application-layer telemetry, or post-exploit remediation automation.
Long Road Ahead for SOC-Cloud Convergence
Despite Wiz’s clear effort to unify security operations and cloud engineering through Wiz Defend, true convergence between SOC and cloud teams remains a long-term vision. Organizational silos, differing toolsets, and mismatched response workflows continue to create friction between infrastructure teams responsible for cloud posture and SOC analysts focused on threat detection and incident response. Even as Wiz provides shared context via the Security Graph and collaborative tooling such as Fix PRs and Playbooks, many enterprises still treat cloud misconfigurations, runtime alerts, and IAM exposures as separate workflows handled by distinct teams. Furthermore, legacy SOC infrastructure (SIEMs, SOAR platforms, and incident escalation processes) often lacks the agility and context-awareness needed to ingest and act on real-time cloud-native detections. In practice, while early adopters may pilot this convergence through cross-functional incident response or shared dashboards, mainstream adoption across enterprise environments is likely to evolve gradually. This dynamic reinforces the need for tools like Wiz Defend to remain modular, interoperable with traditional SOC ecosystems, and flexible enough to support a phased integration between posture, runtime, and response operations.
How The Future of Wiz Defend Ties Into Google’s SecOps Ambitions
The potential integration of Wiz’s cloud-native detection platform with Google Cloud’s Security Command Center (SCC) and Mandiant’s incident response and threat intelligence capabilities could signal a major step forward in building the next generation of runtime security and cloud-native SOC infrastructure. Wiz Defend brings deep telemetry from cloud environments through its hybrid agentless and runtime sensor model, unified by the Wiz Security Graph. This allows for real-time detection, posture correlation, and contextual alerting across workloads, identities, and misconfigurations. This type of integration addresses gaps that have historically been fragmented across multiple tools.
Google’s SCC is a foundational control plane visibility layer for GCP customers, but it has lacked full-spectrum runtime threat detection across multi-cloud environments. Wiz can close this gap by bringing real-time, workload-level insight and investigation tooling, paired with full cloud context, into SCC. This effectively transforms it from a posture-focused dashboard to a cloud detection and response (CDR) command center. Wiz’s ability to surface high-fidelity runtime detections, enriched with vulnerabilities and data exposure, could drastically enhance SCC’s signal-to-noise ratio and accelerate security outcomes.
From a strategic standpoint, this combination also addresses Google’s key weakness. Google has long been strong in defensive infrastructure and zero trust tooling but has struggled to build a fully cohesive cloud security platform that is multi-cloud, context-rich, and SOC-usable. Wiz brings the product maturity, usability, and multi-cloud coverage. Google brings the infrastructure, AI and ML resources, and the reach of Mandiant’s global incident response practice. This merger could produce a platform that rivals Microsoft’s Defender, Sentinel, and GitHub combination, but specifically optimized for cloud-native SOC teams who want deep runtime coverage, strong context, fast investigation workflows, and native GCP tie-ins.
Conclusion: Wiz Defend and the Long Game in Cloud Runtime Security
For Security Operations Centers (SOCs) grappling with the complexity of cloud-centric, real-time threats, Wiz Defend represents an important step forward. By integrating runtime detection with posture, identity, and workload context, all stitched together via the Wiz Security Graph, the platform offers a powerful foundation for reducing noise, accelerating response, and driving collaboration between security, cloud, and development teams.
Wiz is not simply launching a feature. It is redefining the architecture of cloud security operations. The traditional approach, built around siloed tools for posture scanning, workload protection, and incident response, is being replaced by a model where context-rich detections, real-time analytics, and developer-centric remediation converge into one platform. Wiz Defend exemplifies this shift by blending agentless cloud telemetry with lightweight runtime sensors, correlating infrastructure misconfigurations with live attack paths, and enabling SOC analysts to trace incidents all the way back to the code commit that introduced the risk.
However, the road ahead is not without challenges. The convergence of SOC and cloud security functions will take time, and organizational adoption will vary. Wiz must also contend with both legacy vendors offering mature Windows runtime capabilities and emerging startups driving innovation in areas such as identity-aware detection, runtime policy enforcement, and automated remediation. Feature gaps remain, but the strategic intent is clear. Wiz aims to become the runtime engine of the cloud-native SOC.
In this light, Wiz Defend represents more than just a product expansion. It signals a broader industry evolution that is already underway. As cloud-native threats grow more sophisticated, the ability to correlate cloud misconfigurations, runtime activity, and developer intent in real time will define the leaders of the next generation of cybersecurity platforms.
Additional Readings:
If you’re a cloud, SOC, or operations practitioner, or anyone trying to better understand how this market is evolving toward convergence, I highly recommend checking out this market guide on Cloud Detection and Response (CDR).
A LinkedIn Live session was hosted earlier today; you can learn more by clicking here.
If you found this report valuable, I encourage you to subscribe and follow my ongoing research. I will continue tracking how runtime security evolves, how vendors differentiate, and how the cloud SOC matures: one release, one insight, and one breach at a time.